Cold System Forensics: A Comprehensive Guide to Data Acquisition and Preservation
 Harsimran Singh
Harsimran SinghTable of contents
- 1. Order of Volatility: Prioritizing Data Acquisition
- 2. Methods for Acquiring Data from Cold Systems
- 3. Secure Storage and Data Integrity
- 4. Chain of Custody: Ensuring Legal Admissibility
- 5. Essential Forensic Tools for Cold System Analysis
- 6. Techniques for Analyzing Disk Images and Memory Dumps
- 7. Avoiding Common Mistakes in Cold System Forensics
- Conclusion
- TryHackMe Room Solutions

Cold system forensics is a critical branch of digital forensics that focuses on analysing data from systems that are either dormant or powered off. In cases where a system is shut down or compromised, forensic investigators need to employ specialised techniques to retrieve and preserve vital evidence without altering the original data. From disk imaging to memory analysis, these methods help uncover crucial insights into potential cyberattacks or system breaches. This blog will delve into the essential concepts, tools, and techniques of cold system forensics, guiding you through best practices for data acquisition and preservation.
In addition, for those practicing their skills on platforms like TryHackMe, I’ve provided solutions to key questions related to cold system forensics at the end of the blog. These answers will help solidify your understanding as you progress through real-world scenarios.
1. Order of Volatility: Prioritizing Data Acquisition
When performing digital forensics on cold systems, the order of volatility helps prioritize data collection based on how quickly it can change or disappear. Some data is extremely short-lived, while other forms of data are more stable. Understanding this order is essential for forensic analysts to capture the most ephemeral evidence before it’s lost.
Here is a typical order of volatility from most to least volatile:
CPU Registers and Cache: This data is lost as soon as the system is powered down, making it the most volatile. It contains insights into the operations being executed at the moment of shutdown.
RAM (Random Access Memory): RAM data holds valuable information about running processes, network connections, and open files. It is highly volatile and must be captured quickly.
Temporary File Systems: Temporary files are frequently updated and cleared during system reboots. They can reveal recently accessed files or applications.
Hard Disk: While less volatile, disk data can still be modified or deleted. Imaging the disk ensures a complete snapshot of all stored information, including deleted file fragments.
Remote Logging and Monitoring Data: Logs stored on remote systems are relatively stable and can provide a detailed timeline of system and network activities.
Physical Configuration and Network Topology: Documentation of the network layout and system architecture helps provide context to the investigation.
Archival Media: Offline data storage, such as tapes and optical discs, tends to be the least volatile.
By following this order, forensic investigators can ensure they capture crucial data before it is altered or lost, preserving the integrity of the investigation.
2. Methods for Acquiring Data from Cold Systems
Acquiring data from cold systems is the first step in any forensic investigation. Whether dealing with physical hard drives, volatile memory, or network logs, forensic analysts use specific tools and methods to ensure that data is collected in a forensically sound manner.
2.1 Disk Imaging
Disk imaging involves creating an exact, bit-by-bit copy of a hard drive or storage device. This allows investigators to analyze the data without modifying the original evidence. Disk imaging tools such as dd, dc3dd, and FTK Imager are commonly used for this process.
To maintain the integrity of the evidence during disk imaging, write-blockers are used. These hardware or software devices prevent any changes to the original data, ensuring that nothing is altered during acquisition. Forensic logs should document the use of write-blockers, providing transparency throughout the process.
2.2 Physical Acquisition
When systems or drives are damaged, encrypted, or otherwise inaccessible, forensic investigators may need to perform physical acquisition techniques. Two methods often employed are:
Chip-off Forensics: This process involves physically removing the storage chip from the device and reading it with specialized equipment. It’s a delicate method, typically used when traditional data extraction methods fail.
JTAG Forensics: This method accesses data directly from embedded systems via the Joint Test Action Group (JTAG) interface, often useful for mobile devices or IoT (Internet of Things) systems.
3. Secure Storage and Data Integrity
Once data has been acquired, maintaining its integrity is crucial. Forensic data must be stored securely to prevent tampering or unauthorized access. Best practices include:
Encryption: Using strong encryption methods such as AES-256 ensures that even if data is accessed without authorization, it remains unreadable without the proper decryption keys.
Access Control: Limiting access to the forensic data to authorized personnel only helps prevent accidental or malicious tampering.
Environment Control: Physically secure storage locations, such as locked safes or controlled-access server rooms, provide additional protection against physical threats.
Regular Audits: Auditing storage environments and access logs can help detect potential breaches and ensure compliance with security policies.
4. Chain of Custody: Ensuring Legal Admissibility
One of the cornerstones of forensic investigation is maintaining a strict chain of custody. This process documents every individual who handles the evidence from its initial collection to its presentation in court or any other legal body. A well-maintained chain of custody ensures that the evidence has not been tampered with or altered.
Key steps to maintaining chain of custody include:
Detailed Documentation: Every step of the forensic process, including who handled the evidence, when, and why, must be logged meticulously.
Tamper-Proof Packaging: Physical evidence such as hard drives should be stored in tamper-evident packaging during transport.
Hashing: Cryptographic hashes, such as MD5 or SHA-1, can create unique fingerprints for data, ensuring that the data remains unchanged from its initial acquisition.
5. Essential Forensic Tools for Cold System Analysis
Successful cold system forensics relies on using the right tools. Here are some must-know tools that should be in every forensic investigator's toolbox:
Disk Imaging Tools: Tools like dd, dc3dd, and FTK Imager allow for creating exact replicas of disk drives while preserving data integrity.
Memory Forensic Tools: Volatility is a powerful framework for analyzing memory dumps, extracting running processes, network connections, and system states that might be lost during cold system analysis.
Disk Image Analysis Tools: The Sleuth Kit (TSK) and Autopsy allow investigators to explore disk images, recover deleted files, and perform advanced forensic analysis. EnCase offers a professional-grade solution for deep data recovery and investigation.
6. Techniques for Analyzing Disk Images and Memory Dumps
Once the data has been acquired, forensic analysts must analyze disk images and memory dumps to uncover evidence. Key techniques include:
Mounting and Exploring Disk Images: Creating a virtual representation of a disk image allows analysts to interact with the data as though it were a physical drive. Careful use of write-blockers is essential during this step to prevent any accidental modification.
Extracting Artefacts: Artefacts such as files, registry entries, emails, and logs must be carefully extracted for investigation. Techniques like file signature analysis and web history extraction help uncover vital evidence.
Recovering Deleted Data: Even when files are deleted, traces remain. Forensic analysts use techniques like file carving and unallocated space analysis to recover hidden or deleted data.
Memory Dump Analysis: Memory dumps capture the state of a system’s RAM, offering insights into running processes and network connections. This data is often critical for understanding the actions occurring at the time of an incident.
7. Avoiding Common Mistakes in Cold System Forensics
Lastly, cold system forensics carries risks that need to be managed carefully. Some common mistakes include:
Data Integrity Issues: Failing to use proper write-blockers or not verifying data with hash functions can compromise the integrity of evidence.
Misinterpretation of Data: Forensic findings must be cross-verified with other data sources to ensure accuracy and avoid incorrect conclusions.
Inadequate Documentation: Poor documentation can make it difficult to prove the authenticity and reliability of evidence in legal proceedings. Keeping a detailed log of all activities is vital for maintaining credibility.
Conclusion
Cold system forensics is an intricate but essential process in investigating offline systems. By following best practices for data acquisition and preservation, maintaining the integrity of evidence, and using the right tools, forensic analysts can uncover critical insights and ensure the credibility of their findings. Whether in legal proceedings or internal investigations, the ability to properly handle cold systems is crucial for any forensic investigator.
TryHackMe Room Solutions
In this section, I provide the solutions to the questions from the TryHackMe room to aid in understanding cold system forensics concepts.
Q1. Under what two system states are cold system forensics mainly applied?
A: Dormant or Powered-off
Q2. What type of attack provided a research basis for cold system forensics?
A: Cold boot attack
Q3. The making of a bit-by-bit copy of forensic data is known as?
A: Disk imaging
Q4. What restricts access to sensitive data?
A: Access control
Q5. Which sources of evidence are part of the most volatile on a host?
A: CPU registers and cache
Q6. Using hash functions seeks to minimise risks associated with what element?
A: Data integrity
Q7. What is the name of the documentation responsible for listing the forensic evidence and its accompanying responsibilities?
A: Chain of custody
Q8. Get the first flag with the correct order of volatility:
Registers
Routing table
Process table
Memory RAM
Temporary files
Disk
Remote logs
Network topology
Archival media
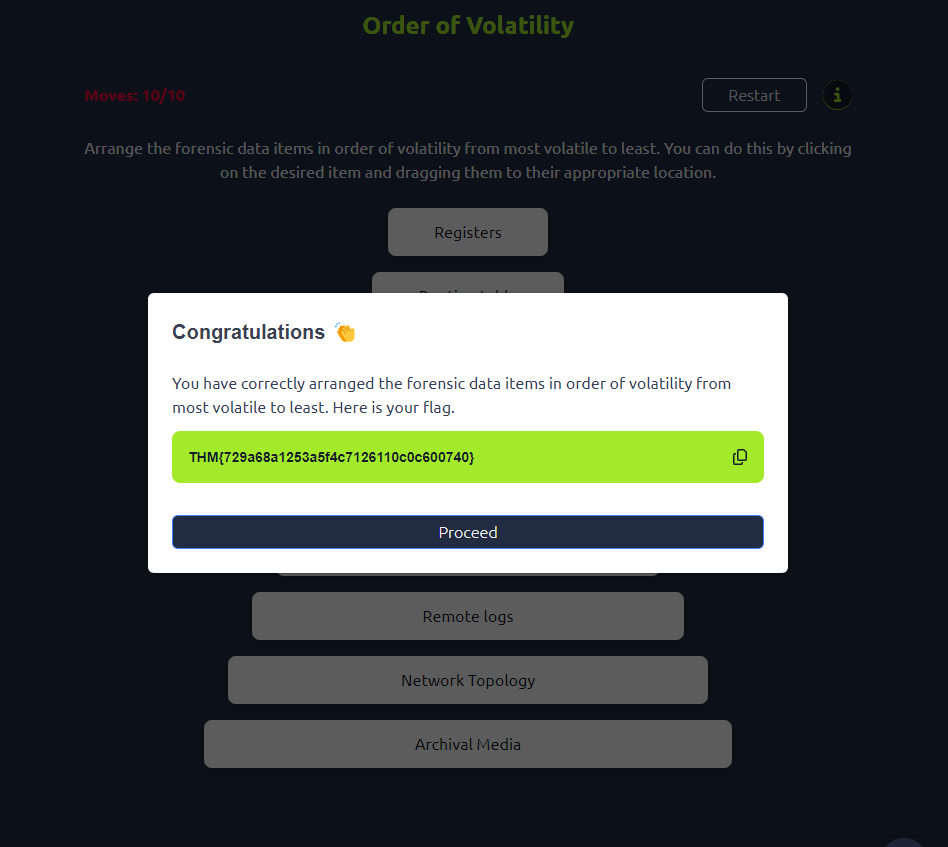
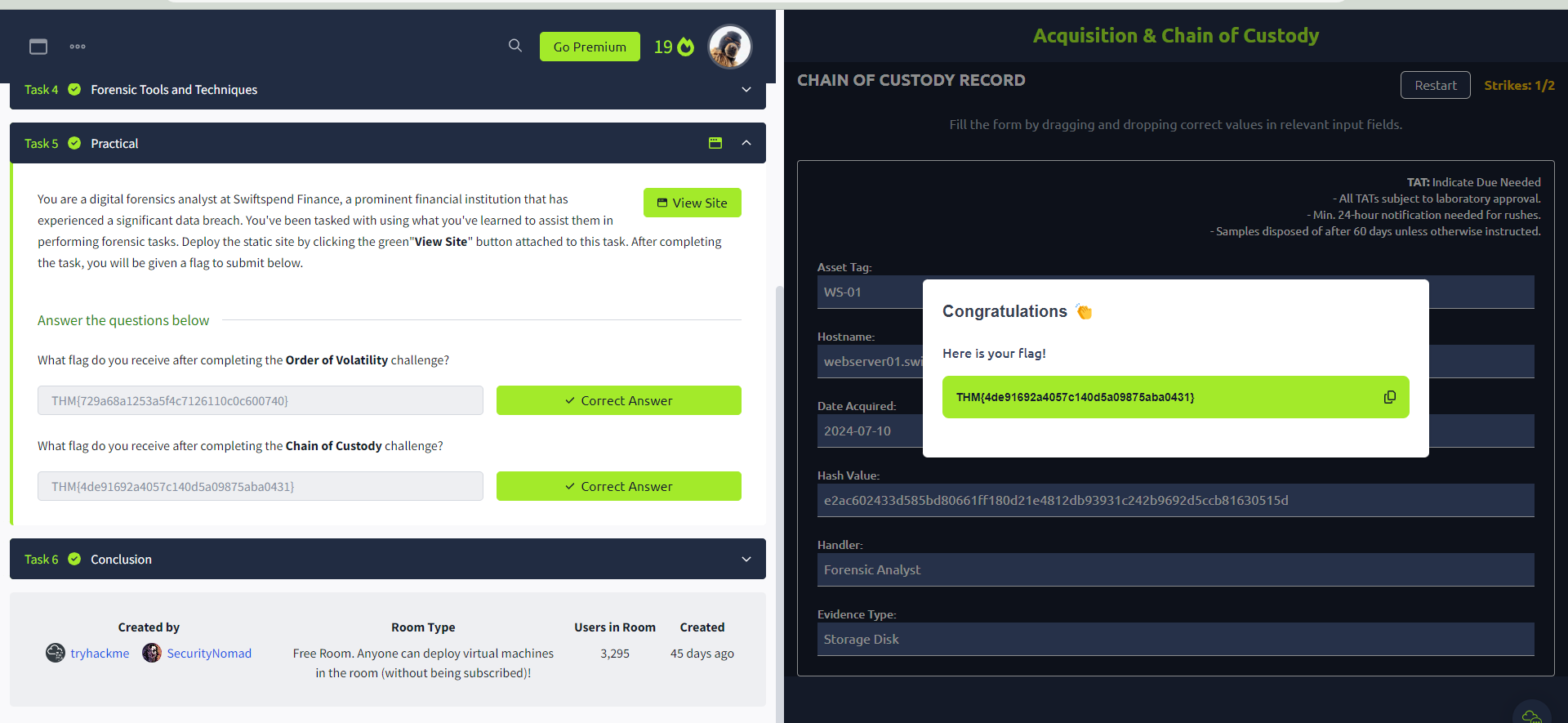
Q9. Get the second flag with the correct values (refer to the picture provided in the room).
Subscribe to my newsletter
Read articles from Harsimran Singh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
