Comprehensive Guide to IAM, VPC, and Route53: In-Depth Look at VPC
 Jyothsna
JyothsnaIAM is a service in AWS that helps you to securely access the AWS Services and resources.
Components of IAM:
Users: IAM users represent individual people or entities that interact with AWS resources. Each user has a unique name and security credentials used for authentication and access control.
Groups: IAM groups are collections of users with similar requirements. Instead of managing permissions of each user individually you can assign permissions to groups, making it easier to manage access control.
Roles: IAM roles are used to grant temporary access to AWS resources. Roles are typically used by applications or services that need to access AWS resources on behalf of users or other services.
Policies: JSON documents that define permissions. You can attach policies to users, groups, and roles. Policies specify which AWS actions are allowed or denied.
Virtual Private Cloud:
A VPC (Virtual Private Cloud) in AWS is a service that allows you to create an isolated network environment where you can launch AWS resources like EC2 instances. It provides full control over networking configurations, including subnets, IP addresses, routing, and security settings.
Components of VPC:
Subnets: It is subdivided into two smaller networks
Public Network: It is connected to internet via Internet Gateway
Private Network: it is isolated from the Internet
Internet Gateway: It is attached to the VPC to enable public access. It allows communication between the resources in the VPC and the internet.
NAT Gateway: It masks the public Ip of the instance present in the private subnet.
Route Tables: Define how traffic is routed within and outside the VPC. Every subnet is associated with a route table.
Security Groups: Act as a virtual firewall for your instances to control inbound and outbound traffic. It is used at instance level.
NACL(Network access control list): A Network Access Control List is a stateless firewall that controls inbound and outbound traffic at the subnet level. It operates at the IP address level and can allow or deny traffic based on rules that you define. NACLs provide an additional layer of network security for your VPC. To add security at subnet level, NACL is used.
Load Balancer: It helps distribute incoming traffic across multiple servers (or instances) to ensure reliability, scalability, and fault tolerance. It consists of a target group.
- Target Groups: Target Groups are an essential component of AWS Elastic Load Balancing (ELB) that allow load balancers to direct traffic to specific destinations, such as EC2 instances, IP addresses, or AWS Lambda functions.
Securing and Scaling Applications with AWS VPC in Production:
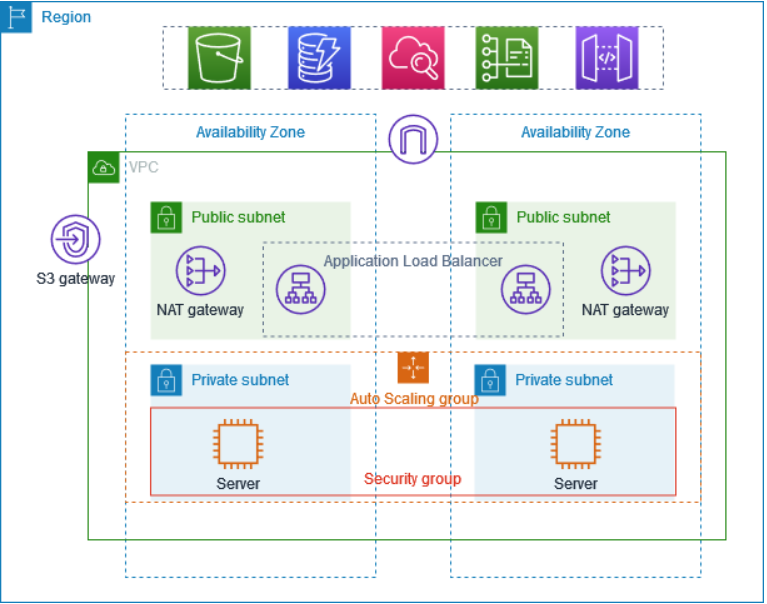
Create a VPC with two Availability Zones that consists of two public subnets and two private subnets , Route tables , a Internet Gateway and a NAT Gateway.
Created a Auto Scaling group that defines the increase or decrease of ec2 instance in response to traffic changes, also launch a template that consists of configuration settings for EC2 instances within a Auto Scaling Group.
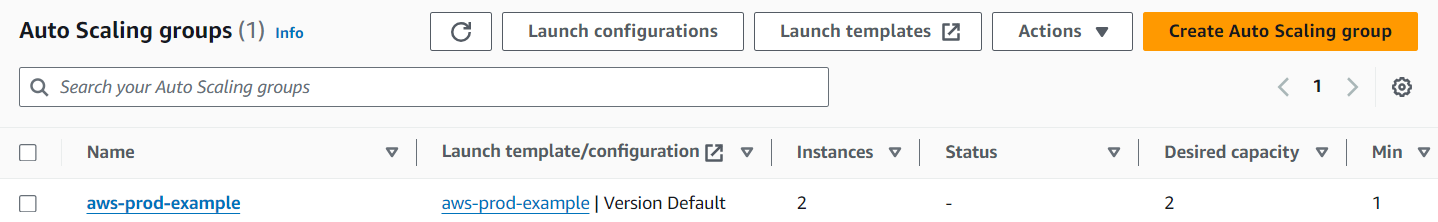
Now two instances are Created as we configured in the auto scaling groups. These instances doesn’t contain public IP address. So we cannot connect the instance.
In order to connect to the instance we use a Bastion host or jump server. A Bastion Host (or jump server) is a special-purpose server used to securely access and administer servers in a private network, typically in a Virtual Private Cloud (VPC). It acts as a bridge between the public internet and private instances, allowing SSH or RDP connections
Now use the bastion host to ssh into other servers and Create a Simple html file and run the Following Command.
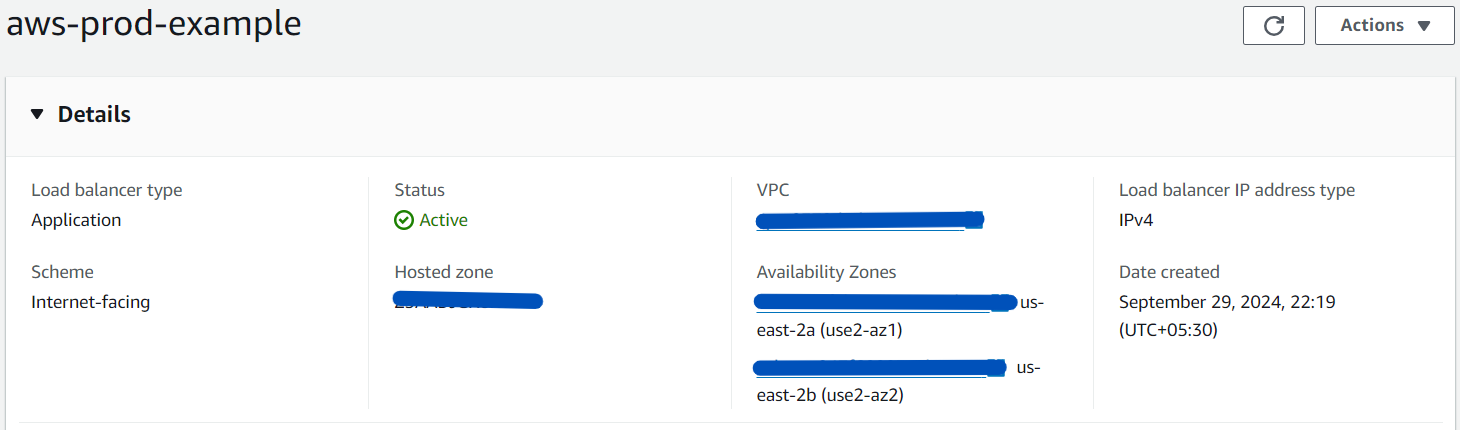
python3 -m http.server 8000python3: Invokes Python 3 interpreter.-m http.server: Runs the HTTP server module included with Python. This module creates a basic web server that serves the files in the directory it is run from.8000: Specifies the port on which the server will listen for incoming requests. In this case, it's port 8000.Create a Load Balancer and it should be in Public subnet and configure the VPC and Security Groups and create a target Group and give necessary permission to it
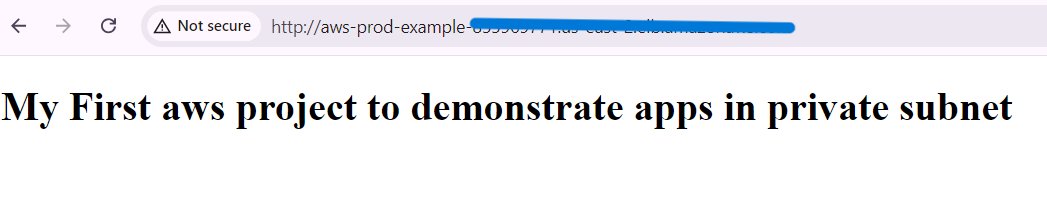
- Copy the DNS name and browse it
What is ROUTE53?
Route53 is a managed DNS(domain name system) service where DNS is a collection of rules and records intended to help clients/users understand how to reach any server by its domain name.
ROUTE53 hosted zones is a collection of records for a specified domain that can be managed together. There are two types of zones:
Private Hosted Zone - Determines how traffic is routed within VPC.
Public Hosted Zone - Determines how traffic is routed on the Internet.
Subscribe to my newsletter
Read articles from Jyothsna directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by