Vulnerability Scanning ( Nmap / Metasploitable 2 ) - Blue Team
 Isael Melendez
Isael Melendez
In this project, I’ll be working on completing a small lab about vulnerability management by scanning a vulnerable (VM) Virtual Machine - Metasploitable 2 - from Rapid7 using a Nmap scanning tool running on Kali Linux.
“Metasploitable 2 is an intentionally vulnerable virtual machine created by security company Rapid7. It is designed to be a test environment and playground for ethical hackers” - Blue Team
"Nmap" is an open-source network discovery and security auditing tool widely used by network administrators for many types of scanning.
By the end of this project, you'll have a good understanding of vulnerability management, vulnerability scanning, and vulnerability scanning tools.
We need to start gathering all necessary tools for this project:
Virtualization Software ( VMWare or VirtualBox)
Running Linux VM ( Kali-other)
Metasploitable 2 zip, Nmap
Steps:
Download the Metasploitable 2 VM files from https://sourceforge.net/projects/metasploitable/ and open it with the chosen virtualization software. To host this VM we’ll be using VMWare.
Consider login details as user: msfadmin pass: msfadmin
We’re going to open two virtual machines, one with the Metasploitable 2 and another with Kali Linux
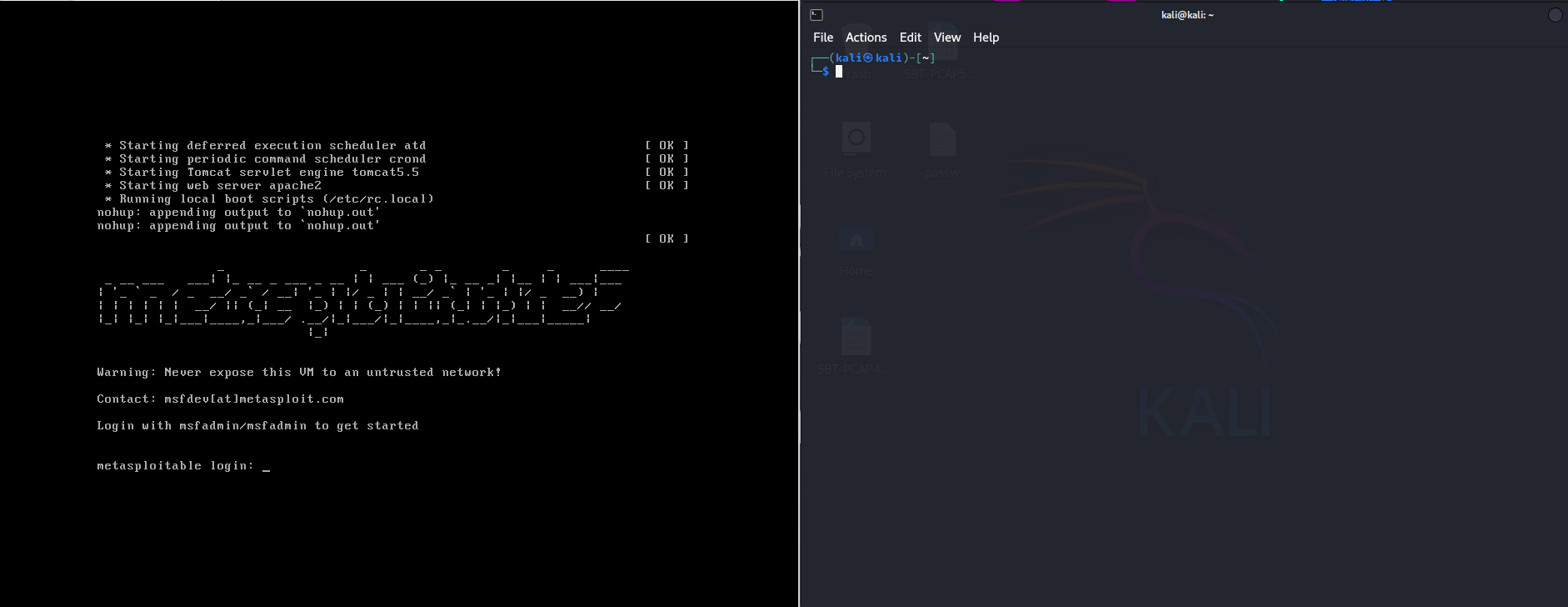
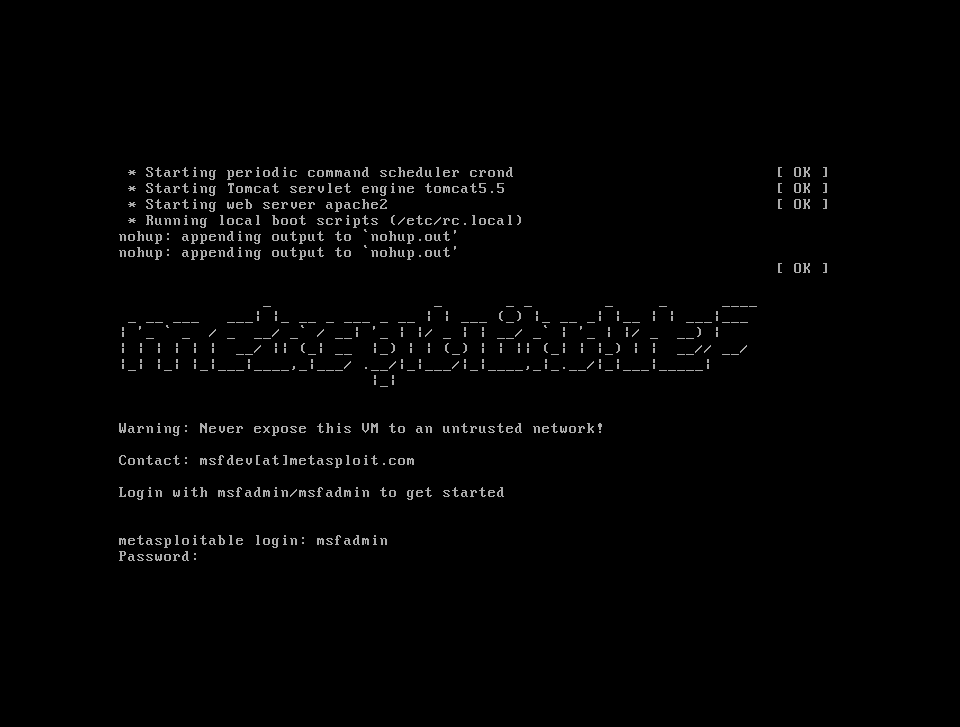
We’re going to confirm connectivity between VMs. First we’re going to logging using the credentials mentioned before.
msfadmin / mfsadmin
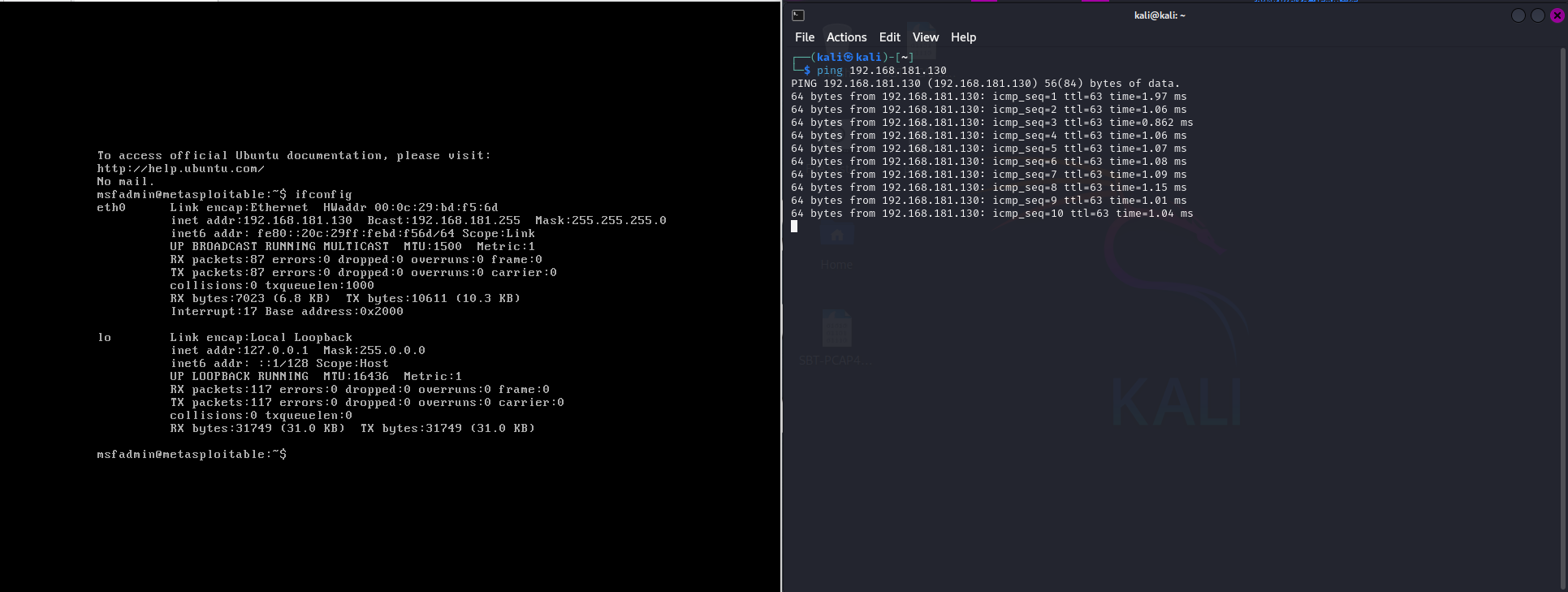
Now, to check connectivity we run the command ifconfig in MS2 and do a ping on Kali Linux.
Scan Metasploitable 2 Vm from Linux VM using Nmap:
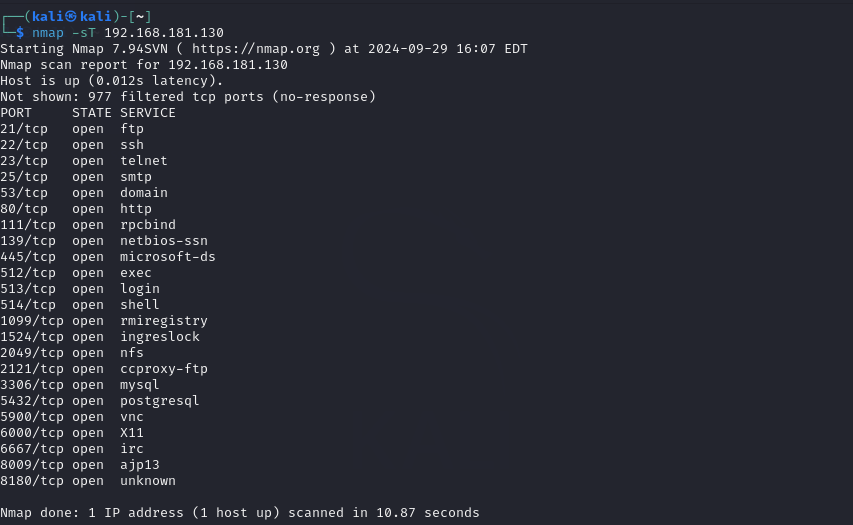
To know how many TCP ports are open on MS2 we should run Nmap using the -sT flag.
- To know how many UDP ports are open on MS2 we should run Nmap using the -sU flag.
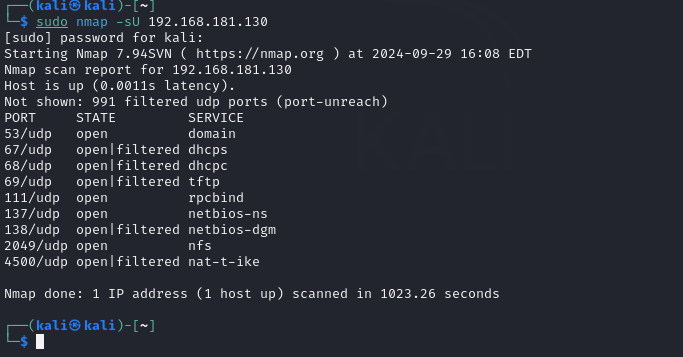
You may see, only are open those who don’t say FILTERED
In this option, you should find a Version Detection, what port is running a Metasploitable Root Shell using the -sV flag in Nmap.
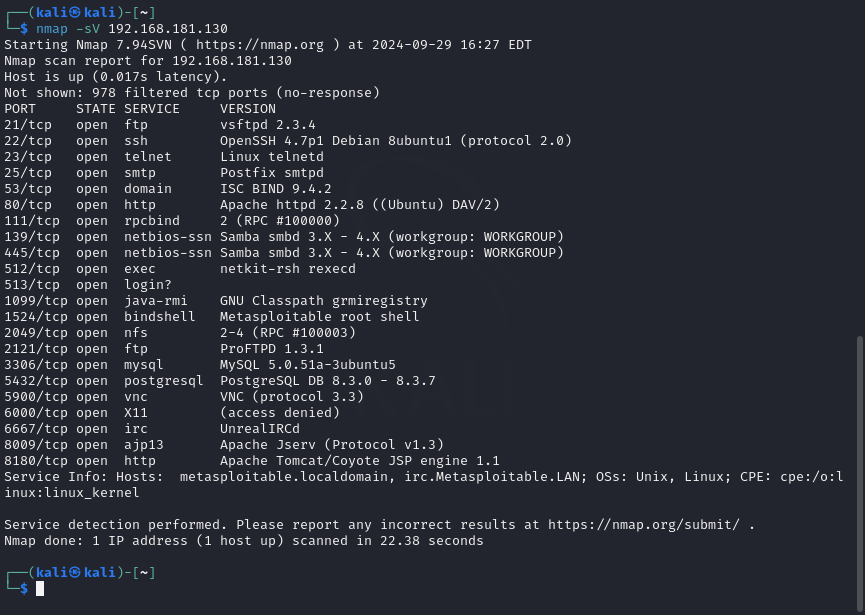
When asking which non-standard port is FTP running on MS2, (n NOT port 21) we should use the -sT flag in Nmap and look for the exact port.

Now, if you need to know what version on the non-standard port found, we use the -sV flag to find the version always focusing on that -p flag port.
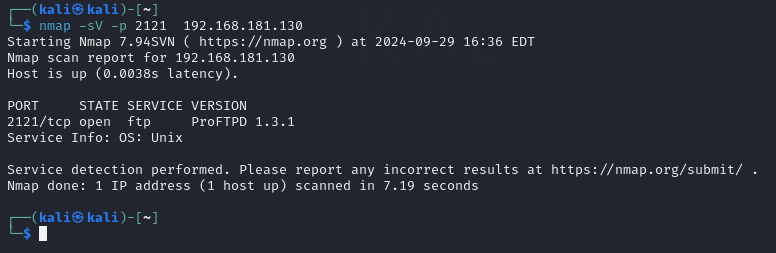
Here you complete the small lab using Nmap and Metasploitable2.
If you need any help or clarification, I’ll be reading the comments section.
Congrats!!!!!!
Subscribe to my newsletter
Read articles from Isael Melendez directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Isael Melendez
Isael Melendez
Tech enthusiast , always learning IT field. ♦Cybersecurity Analyst and Cloud Computing student @ MDC | Banking Specialist ♦CodePath Intermediate Intern.