How to Build an Effective Cloud Security and Cryptography Audit Checklist
 Logeshwaran N
Logeshwaran N
As organizations continue to adopt cloud services, ensuring data security and privacy becomes critical. Auditing cloud environments is essential for verifying that sensitive data is protected and managed effectively. Two key domains that require focused attention are Cryptography and Key Management and Data Security & Privacy Lifecycle Management. This article presents a detailed auditing checklist for these domains to help organizations maintain compliance, minimize risks, and secure sensitive data in cloud infrastructures.
1. Cryptography and Key Management
Effective cryptography and key management ensure that sensitive data is encrypted and that encryption keys are stored, rotated, and destroyed securely. The following auditing checklist provides a detailed breakdown of the key aspects to review in this domain.
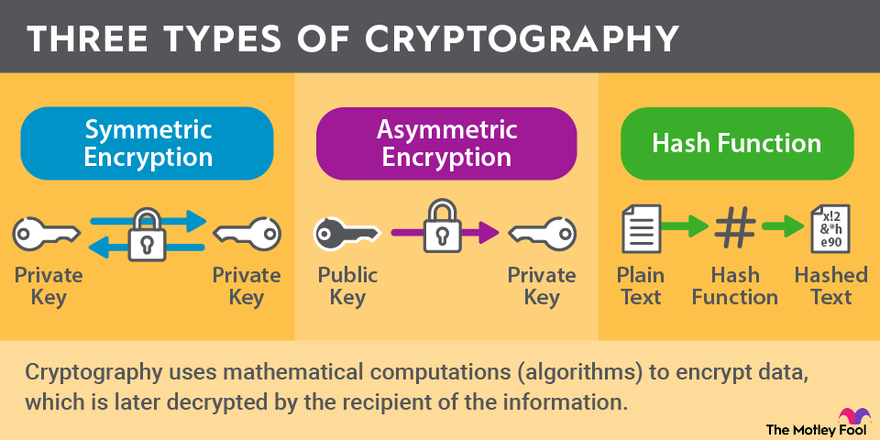
1.1 Encryption Algorithms and Strengths
Encryption Standard: Verify that data is encrypted using strong encryption algorithms such as AES-256 or RSA-2048, which are considered industry standards.
Encryption In-Transit: Ensure that data is encrypted during transmission over public networks using secure protocols like TLS (Transport Layer Security) or IPsec (Internet Protocol Security).
Encryption At-Rest: Confirm that data stored on cloud infrastructure is encrypted at rest, either at the disk or file level, using strong algorithms.
Review Legacy Encryption: Check if any legacy encryption algorithms like DES or MD5 are still in use and recommend upgrading to modern encryption standards.
1.2 Key Management Practices
Key Generation: Confirm that encryption keys are generated using secure and random processes, adhering to standards such as NIST SP 800-90A.
Key Rotation Policy: Verify that a well-defined key rotation policy exists, ensuring keys are regularly rotated and old keys are securely retired.
Key Storage: Review the methods used to store encryption keys. Ideally, keys should be stored in hardware security modules (HSMs) or secure key vaults, not in plain text or insecure environments.
Access Control for Keys: Ensure that access to encryption keys is tightly controlled, with only authorized personnel and systems able to retrieve or use the keys.
Key Revocation and Destruction: Confirm that a process is in place to revoke and securely destroy keys when no longer in use or when compromised.
Separation of Duties: Verify that the roles for managing cryptographic keys are separate from those who manage the systems that use them, ensuring that no single individual has full control over both the data and its keys.
1.3 Certificate Management
Certificate Validity: Review the organization’s management of digital certificates, ensuring that certificates are valid and not expired.
Certificate Authority (CA) Trust: Check that certificates are issued by a trusted Certificate Authority and not self-signed unless internal use is fully justified and controlled.
Certificate Revocation: Ensure a mechanism is in place for managing certificate revocation (e.g., CRL or OCSP) to promptly invalidate compromised or expired certificates.
1.4 Cryptographic Operations Auditing
Logging of Cryptographic Events: Review logging practices to ensure all cryptographic events, such as key generation, key rotation, and certificate issuance, are logged for audit purposes.
Regular Audits: Verify that cryptographic operations are audited regularly, checking for unauthorized access, outdated keys, and compliance with encryption policies.
Compliance with Regulations: Ensure cryptographic practices comply with relevant regulations and standards, such as GDPR, HIPAA, and PCI-DSS, particularly for data encryption and key management.
2. Data Security & Privacy Lifecycle Management
Data security and privacy management is vital throughout the data lifecycle, from creation to deletion. This domain ensures that data is protected at all stages, especially when it is sensitive or personally identifiable (PII). The checklist below outlines best practices for auditing this domain in a cloud environment.
2.1 Data Classification
Classification of Data: Confirm that data is properly classified according to its sensitivity (e.g., public, confidential, restricted) and that security controls are applied accordingly.
Automated Classification: Review whether data classification tools are employed to automatically categorize data, reducing human error and ensuring that sensitive data is flagged appropriately.
2.2 Data Retention and Disposal
Data Retention Policies: Ensure that well-documented data retention policies exist, specifying how long different types of data should be stored based on regulatory requirements and business needs.
Data Disposal Practices: Verify that proper procedures are in place for the secure disposal of data that is no longer needed, including the use of secure deletion methods like cryptographic erasure for cloud environments.
Data Archiving: Check that archival data is properly secured and encrypted, ensuring that old or infrequently accessed data is still protected.
2.3 Data Access Controls
Role-Based Access Control (RBAC): Confirm that access to data is granted on a need-to-know basis, using role-based access control mechanisms to enforce least privilege.
Identity and Access Management (IAM): Review IAM policies and configurations to ensure strong authentication and authorization controls are in place for data access in the cloud environment.
Access Auditing: Ensure that access to sensitive data is regularly audited, and any suspicious access patterns are flagged and investigated.
2.4 Data Masking and Anonymization
Data Masking: Verify that sensitive data is masked when displayed or processed in non-production environments (e.g., development or testing), protecting real user information.
Anonymization: Ensure that data anonymization techniques are used when sharing data for purposes like analytics, ensuring that PII or sensitive data cannot be traced back to individuals.
Compliance with Data Protection Regulations: Confirm that anonymization and masking practices meet the requirements of regulations like GDPR, CCPA, or HIPAA.
2.5 Data Transmission Security
Secure Transmission Protocols: Ensure that all data transmitted between systems is secured using protocols like TLS or SSH, especially when data is sent over public networks.
Data Integrity Checks: Verify that measures such as digital signatures or hash functions are used to check the integrity of data during transmission, ensuring that data has not been altered in transit.
2.6 Data Processing and Sharing
Third-Party Data Sharing Policies: Review the organization’s policies on sharing data with third parties, ensuring that appropriate contracts, including data processing agreements (DPAs), are in place.
Data Processing Agreements: Ensure that cloud service providers and third-party processors comply with data protection regulations and contractual obligations, particularly for processing sensitive data.
Data Flow Documentation: Confirm that the data flow across systems and between organizations is well documented, allowing auditors to track how data is used and shared throughout its lifecycle.
2.7 Data Breach Response
Incident Response Plan: Verify that a well-documented incident response plan exists to handle data breaches, including procedures for notifying affected parties and regulatory authorities.
Breach Detection and Reporting: Ensure that systems are in place to detect and report data breaches promptly, with appropriate logging and monitoring tools to capture security incidents.
Data Breach Simulations: Confirm that the organization conducts regular data breach simulations or tabletop exercises to prepare staff for real-life breach scenarios.
2.8 Data Backup and Recovery
Regular Data Backups: Verify that regular backups of critical data are performed, with backup data encrypted both in transit and at rest.
Backup Integrity Testing: Ensure that data recovery and backup integrity tests are regularly conducted to validate that data can be restored in the event of a loss or breach.
Disaster Recovery Plan: Confirm that a disaster recovery plan is in place, detailing procedures for restoring data and operations after a significant outage or incident.
Conclusion
The above auditing checklist covers two crucial control domains in a cloud environment: Cryptography and Key Management, and Data Security & Privacy Lifecycle Management. By systematically auditing these areas, organizations can ensure they are properly securing sensitive data, managing encryption keys effectively, and complying with industry regulations. Implementing this checklist will not only protect organizational assets but also build trust with clients and regulatory bodies by demonstrating robust security and privacy practices in the cloud.
Subscribe to my newsletter
Read articles from Logeshwaran N directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Logeshwaran N
Logeshwaran N
I’m a dedicated Cloud and Backend Developer with a strong passion for building scalable solutions in the cloud. With expertise in AWS, Docker, Terraform, and backend technologies, I focus on designing, deploying, and maintaining robust cloud infrastructure. I also enjoy developing backend systems, optimizing APIs, and ensuring high performance in distributed environments. I’m continuously expanding my knowledge in backend development and cloud security. Follow me for in-depth articles, hands-on tutorials, and tips on cloud architecture, backend development, and DevOps best practices.