Setting up VPC Peering in AWS within the same region
 Ankita Lunawat
Ankita Lunawat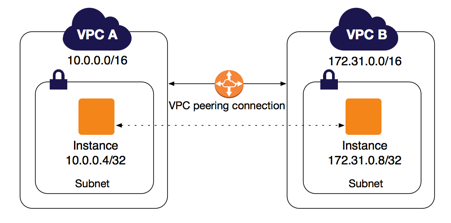
VPC Peering in AWS is a networking connection that allows you to route traffic between two Virtual Private Clouds (VPCs) using private IP addresses. VPC Peering enables the resources in one VPC to communicate with resources in another VPC as if they are within the same network.
Key Features of VPC Peering
Private Communication: Traffic between peered VPCs stays within the AWS network and does not traverse the public internet, ensuring security and performance.
Same or Different AWS Accounts: VPC peering can be established between VPCs in the same AWS account or across different AWS accounts.
Same or Different Regions: Peering connections can be set up between VPCs in the same region (intra-region) or in different regions (inter-region).
No Overlapping CIDR Blocks: The VPCs being peered must have unique, non-overlapping IP address ranges (CIDR blocks).
Benefits of VPC Peering
Low Latency and High Bandwidth: Traffic between peered VPCs uses the AWS backbone, which provides low-latency and high-bandwidth connections.
No Single Point of Failure: VPC peering is a fully distributed and redundant connection.
Cost-Effective: Unlike VPNs, VPC Peering doesn’t require the setup of gateways or connection appliances, and there’s no data transfer cost for traffic within the same region (intra-region peering).
Secure: VPC peering uses private IP addresses, so all traffic is encrypted within AWS and no public IPs are exposed.
Common Use Cases
Multi-VPC Architecture: Connect multiple VPCs within the same AWS account for efficient and secure communication between them.
Cross-Account VPC Communication: Share resources between VPCs in different AWS accounts.
Hybrid Cloud Architecture: Extend on-premises resources to AWS using VPC peering to connect multiple VPCs.
Application Segmentation: Isolate parts of a larger application into different VPCs (e.g., web servers in one VPC, databases in another) and connect them using VPC peering.
Key Components of VPC Peering
Peering Connection: The actual connection established between two VPCs.
Route Tables: You need to update the route tables in both VPCs to allow traffic to route through the peering connection.
Security Groups/Network ACLs: Both VPCs need to configure security group and network ACL rules to allow communication.
Steps for Creating a VPC Peering Connection
Create or identify two VPCs with non-overlapping CIDR blocks.
Establish a VPC peering connection.
Accept the peering request from the other VPC.
Update route tables in both VPCs to allow traffic through the peering connection.
Modify security group and network ACL rules to permit communication between the VPCs.
Step1: Create two Custom VPCs in your AWS account within the same region.
Create the two Custom VPC.
Create 2 subnets.
Make the subnet public by modifying the auto-assign IP settings for both subnets. Navigate to the Action dropdown menu, click on Edit subnet settings, and enable auto-assign public IPv4 address by checking the box.
Create two Internet Gateways and attach them to created VPCs respectively.
Same we have to perform for IGW02 .
4.Create and Add Route entries (0.0.0.0/0 for IGWs) to two Route Tables. Same we have to perform for RT02.
Step2: Create a VPC Peering Connection :
Go to dashboard → search for Peering Connections.
Select the following parameters
Peering connection name tag = pc-01
VPC (Requester) = 01 Select My Account and the Same Region
VPC (Accepter) = 02
In order to confirm this you are required to select “Actions” → “Accept Request”.
Add two Routing Entries to both the Route Tables of each VPC Click on Modify my route table now as shown in the above pop-up
For custom-vpc-01, add the following entry
Destination = 10.2.0.0/16
Target = <Select the Peering Connection> Click on the route table ID that is for VPC-01.
Step3 : Test Network Connectivity
Create two EC2 instances in each public subnets in each custom VPCs. SSH into both the public subnets (in both VPCs) and and verify that they can communicate with one other using their private IP addresses.
Also add SSH (Port no. 22), HTTP (80), ICMP into your security group.
Ping and curl EC2-VPC-02 from EC2-VPC-01 to test network connectivity between two instances that are in different VPCs.
EC2-VPC 1 IP: 44.220.179.59
EC2 VPC 2 IP: 98.84.24.179
Here, we have successfully done with with VPC Peering within the same region.
Subscribe to my newsletter
Read articles from Ankita Lunawat directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ankita Lunawat
Ankita Lunawat
Hi there! I'm a passionate AWS DevOps Engineer with 2+ years of experience in building and managing scalable, reliable, and secure cloud infrastructure. I'm excited to share my knowledge and insights through this blog. Here, you'll find articles on: AWS Services: Deep dives into core AWS services like EC2, S3, Lambda, and more. DevOps Practices: Best practices for CI/CD, infrastructure as code, and automation. Security: Tips and tricks for securing your AWS environments. Serverless Computing: Building and deploying serverless applications. Troubleshooting: Common issues and solutions in AWS. I'm always eager to learn and grow, and I hope this blog can be a valuable resource for fellow DevOps enthusiasts. Feel free to connect with me on [LinkedIn/Twitter] or leave a comment below!