Understanding AWS VPC and VPC Peering
 Muhammad Irfan
Muhammad IrfanTable of contents
Mastering AWS VPC and VPC Peering
In the world of cloud computing, understanding network architecture is key to building scalable, secure, and efficient systems. One of the most important concepts in Amazon Web Services (AWS) networking is the Virtual Private Cloud (VPC). Along with VPC Peering, these components empower DevOps and Cloud Engineers to design and maintain robust cloud infrastructures.
In this article, I’ll explore AWS VPC, its components, and how VPC Peering enables secure cross-VPC communication for businesses looking to scale across regions or accounts. Let’s dive in!
What is AWS VPC?
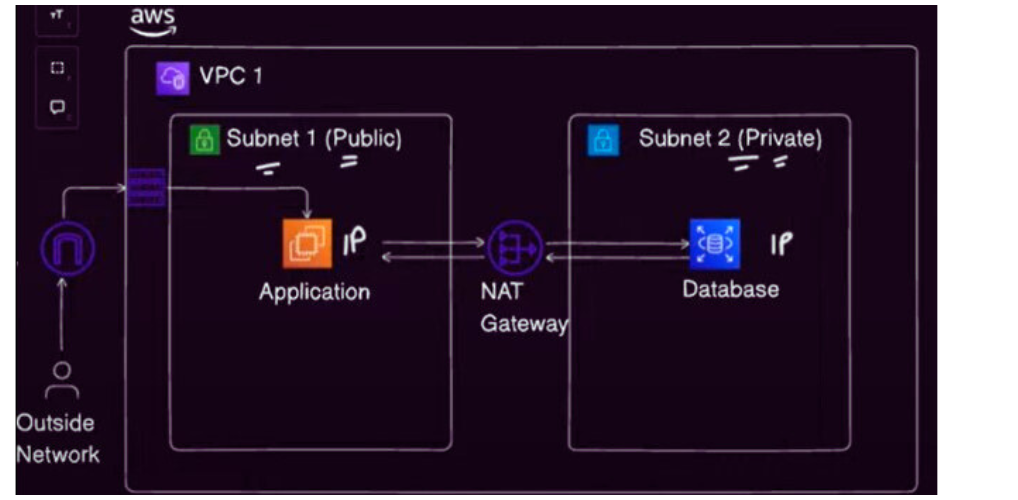
At its core, an Amazon Virtual Private Cloud (VPC) is a logically isolated network within AWS. It allows us to define own network configuration, similar to a traditional data center but with all the advantages of AWS.
Key Features of AWS VPC:
Subnets:
These are smaller subdivisions of the VPC, allowing you to group resources by their purpose or security needs.
Route Tables:
Define how traffic is routed within the VPC and beyond (like to the internet or other VPCs).
Internet Gateways (IGW):
Enable communication between your VPC and the internet.
NAT Gateways:
Allow instances in private subnets to connect to the internet without exposing them to incoming traffic.
Security Groups & Network ACLs:
Act as firewalls, controlling inbound and outbound traffic at the instance and subnet levels.
Elastic IP:
Static IP addresses that allow for consistent, public-facing IP configurations.
With a VPC, cloud architectures have full control over IP address ranges, subnets, routing, and security policies, making it an essential building block for cloud architecture.
What is VPC Peering?
VPC Peering is a powerful feature that allows two VPCs to communicate directly with each other, as if they were part of the same network. This is especially useful in scenarios where need to connect VPCs across different AWS regions, accounts, or departments while maintaining isolation and security.
Key Benefits of VPC Peering:
Private Communication:
Traffic between VPCs remains within AWS's private network, offering high security.
No Bandwidth Bottlenecks:
VPC Peering utilizes AWS’s backbone network, meaning there's no performance hit for communication.
Cost-Efficient:
No need for VPNs or dedicated lines, reducing operational costs.
Cross-Region and Cross-Account:
VPC peering can be established between VPCs in different AWS regions or accounts.
VPC Peering Project Example: Connecting Two VPCs
Let’s walk through a project that sets up VPC Peering between two VPCs in same-zone communication. Same concept can be applicable for businesses that operate across multiple geographies and need their infrastructure to be globally connected.
Project Goals:
Create two VPCs: VPC-1 in US-East-1 and VPC-2 in US-East-1.
Establish VPC Peering between these VPCs.
Configure routing so that instances in VPC-1 can communicate with instances in VPC-2.
Ensure the setup is secure using Security Groups and Network ACLs.
Step-by-Step VPC Peering Setup
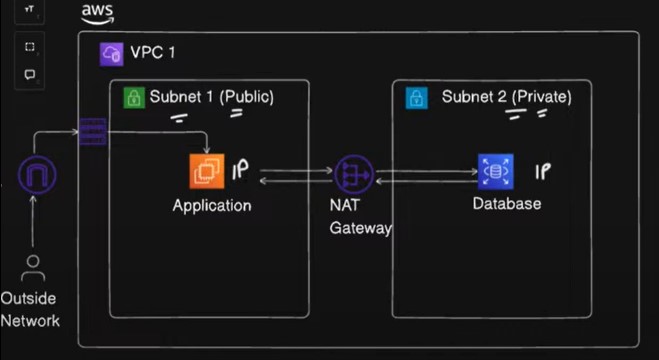
1️⃣ Create VPC-1 (US-East-1)
Login to AWS Management Console and navigate to the VPC Dashboard.
Click on Create VPC, and choose a CIDR block like
10.0.0.0/16.Create Subnets within this VPC (e.g., public subnet
10.0.1.0/24and private subnet10.0.2.0/24).Configure a Route Table to associate subnets with internet gateways, if needed.
Attach a Security Group to control the traffic rules for your instances.
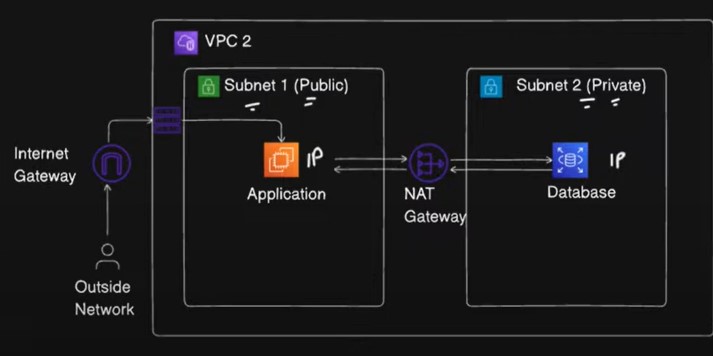
2️⃣ Create VPC-2 (US-East-1)
Repeat the same steps as above, but this time in the US-East-1 region.
Choose a different CIDR block for VPC-2, such as
10.1.0.0/16, to avoid conflicts with VPC-1.
3️⃣ Create the VPC Peering Connection
In the VPC Dashboard, go to Peering Connections and click Create Peering Connection.
Select VPC-1 as the requester and VPC-1 as the accepter. Make sure both CIDR blocks don’t overlap.
Once the request is made, go to the VPC-2's console and accept the Peering Connection.
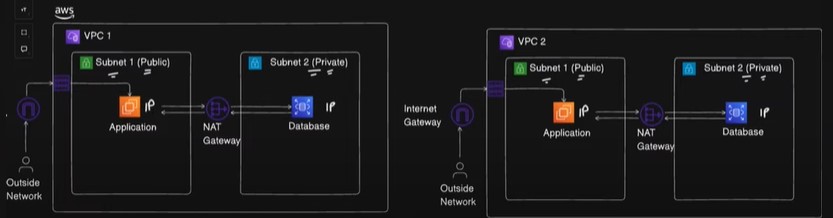
4️⃣ Configure Route Tables
- In VPC-1, update the Route Table to route traffic destined for
10.1.0.0/16(VPC-2) through the Peering Connection.
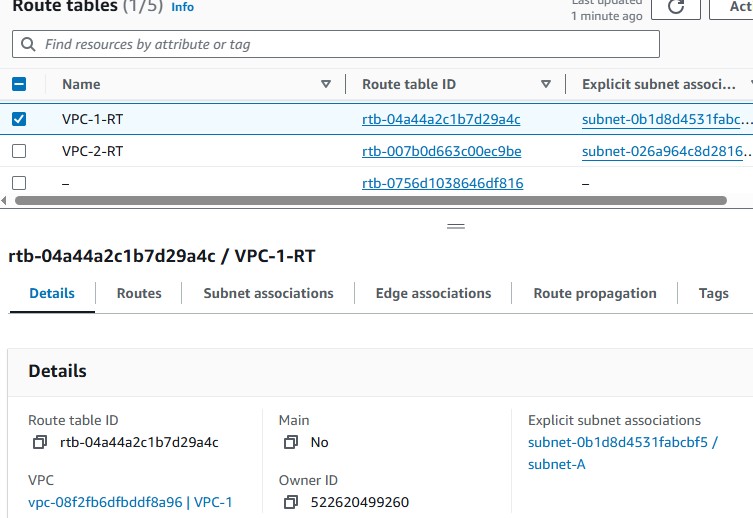
In VPC-2, update the Route Table to route traffic destined for
10.0.0.0/16(VPC-1) through the Peering Connection.Make the subnets involved have the appropriate route entries to communicate.
5️⃣ Configure Security Groups and Network ACLs
Update Security Groups to allow inbound and outbound traffic between the instances in VPC-1 and VPC-2.
- Example: Allow SSH (port 22) from the CIDR block
10.1.0.0/16in VPC-2 to instances in VPC-1.
- Example: Allow SSH (port 22) from the CIDR block
As per requirement, modify Network ACLs for additional layer of security at the subnet level.
Testing the VPC Peering Connection
Once set up completed of peering connection and routes, then launch and ping instances in both VPC-1 and VPC-2.
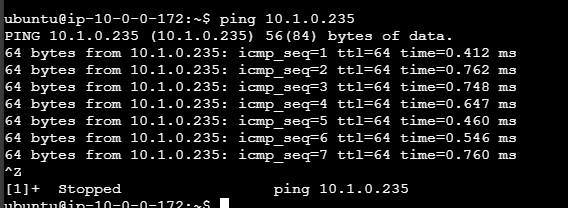
- Ping or SSH from an instance in VPC-1 to an instance in VPC-2 using its private IP.
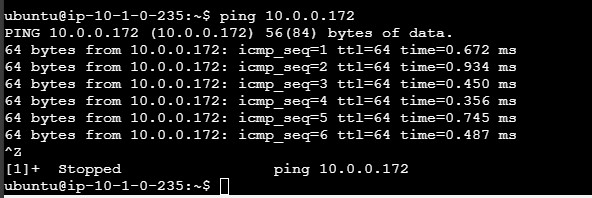
- This way connections are established in the zones without the traffic going over the public internet.
Best Practices for VPC Peering and Security
Avoid Overlapping CIDR Blocks:
Ensure the IP address ranges of peered VPCs do not overlap to avoid routing conflicts.
Limit Peering Connections:
Use Transit Gateways for complex architectures with many VPCs to simplify peering and reduce management overhead.
Secure VPC-to-VPC Traffic:
Implement strict Security Group and Network ACL rules to allow only necessary traffic between VPCs.
Scaling VPC Peering for Complex Architectures
As the infrastructure grows, managing multiple VPC Peering connections can become complex. For large-scale architectures, AWS Transit Gateway offers a solution by acting as a central hub for VPC-to-VPC communication. Instead of managing many peer connections, all VPCs connect to the Transit Gateway, simplifying the process.
Conclusion
Mastering AWS VPC and VPC Peering is essential for DevOps and Cloud Engineers who design scalable and secure cloud architectures. Whether connecting multiple VPCs within the same region or across regions, VPC Peering allows to seamlessly integrate your network infrastructure while maintaining security and performance.
With the right setup and adherence to best practices, VPCs can operate as an interconnected, private cloud network—enabling flexibility, security, and growth for organization.
Subscribe to my newsletter
Read articles from Muhammad Irfan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Muhammad Irfan
Muhammad Irfan
I am passionate about the transformative power of Linux, DevOps, and cloud technologies. With a background in system administration, I’m on a journey to master cloud infrastructure, automation, and containerization. On my GitHub, you’ll find projects where I explore automation, AWS, CI/CD, and scripting to solve real-world problems. 📚 Current Focus: Enhancing my expertise in Linux systems, AWS, and scripting. Here, I share insights and experiences from my hands-on projects to help and inspire fellow tech enthusiasts.