Understanding SELinux: A Comprehensive Guide
 Dinesh Kumar K
Dinesh Kumar K
What is SELinux?
Security-Enhanced Linux (SELinux) is a powerful security module integrated into the Linux kernel that provides a robust mechanism for enforcing access control policies. Developed by the National Security Agency (NSA), SELinux enhances the security of the Linux operating system by allowing administrators to define granular access controls for processes, files, and resources. By implementing mandatory access control (MAC), SELinux restricts how processes interact with each other and the files they access, significantly minimizing the risk of unauthorized access or exploitation.
SELinux Values and Types
SELinux operates based on a set of values and types that define how objects and subjects (processes) can interact. The key values include:
Enforcing: SELinux policy is enforced, and access is denied if the policy does not permit it.
Permissive: SELinux policy is not enforced, but denials are logged for monitoring and troubleshooting purposes.
Disabled: SELinux is turned off completely.
The types are associated with security contexts and define the role or permissions assigned to processes and files. Each object and subject has a security context, which includes the following components:
User: Identifies the user who owns the object or process.
Role: Defines the role assigned to the user or process.
Type: Specifies the type of the object or process and the permissions allowed.
Checking SELinux Status
To check the current status of SELinux on your system, you can use the following commands:
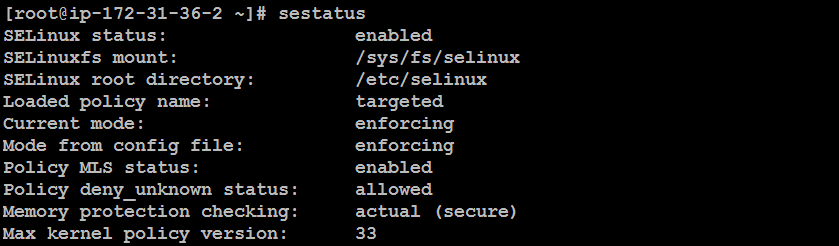
sestatus: This command provides detailed information on whether SELinux is enabled and the current mode (enforcing, permissive, or disabled).
sestatus
getenforce: This command provides a quick view of the current SELinux mode. It outputs one of three values: Enforcing, Permissive, or Disabled.
getenforce
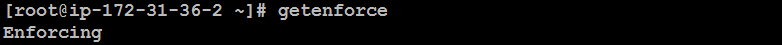
Using either of these commands will help you understand the SELinux configuration on your system.
Viewing Security Contexts
To view the security contexts of files and processes, you can use the following commands:
- To view the security context of a file:
ls -lZ /path/to/file
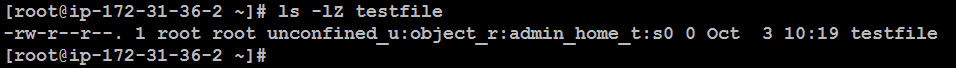
Breakdown of the security context unconfined_u:object_r:admin_home_t:s0 for the file testfile:
User (
unconfined_u):- Represents a user without SELinux restrictions.
Role (
object_r):- Indicates that this context is associated with an object (like a file).
Type (
admin_home_t):- Specifies that the file is located in an administrator's home directory and is treated accordingly by SELinux.
Level (
s0):- Denotes a low sensitivity level, indicating general accessibility.
Modifying SELinux Contexts
If you need to modify the SELinux context of files or directories, you can use the chcon command. For example, to change the context of a file, you would run:
chcon -t etc_t /path/to/file
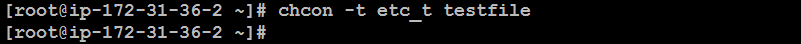
Explanation:
chcon: This command is used to change the SELinux security context of a file.-t etc_t: The-toption specifies that you are changing the type of the file toetc_t. Theetc_ttype is typically used for files in the/etcdirectory.testfile: This is the name of the file whose context you want to modify.
After executing the command, you can verify the change by running:
ls -lZ testfile
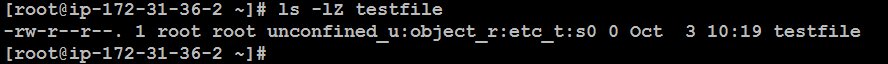
Changing SELinux Modes
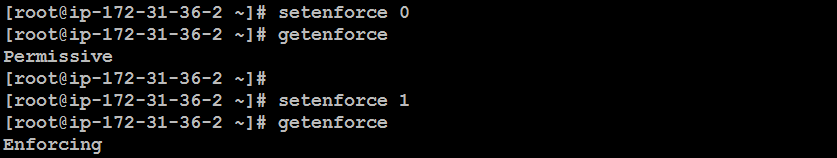
You can change SELinux modes temporarily or permanently. To change the mode temporarily, use the following command:
setenforce 0 # Set to permissive
setenforce 1 # Set to enforcing
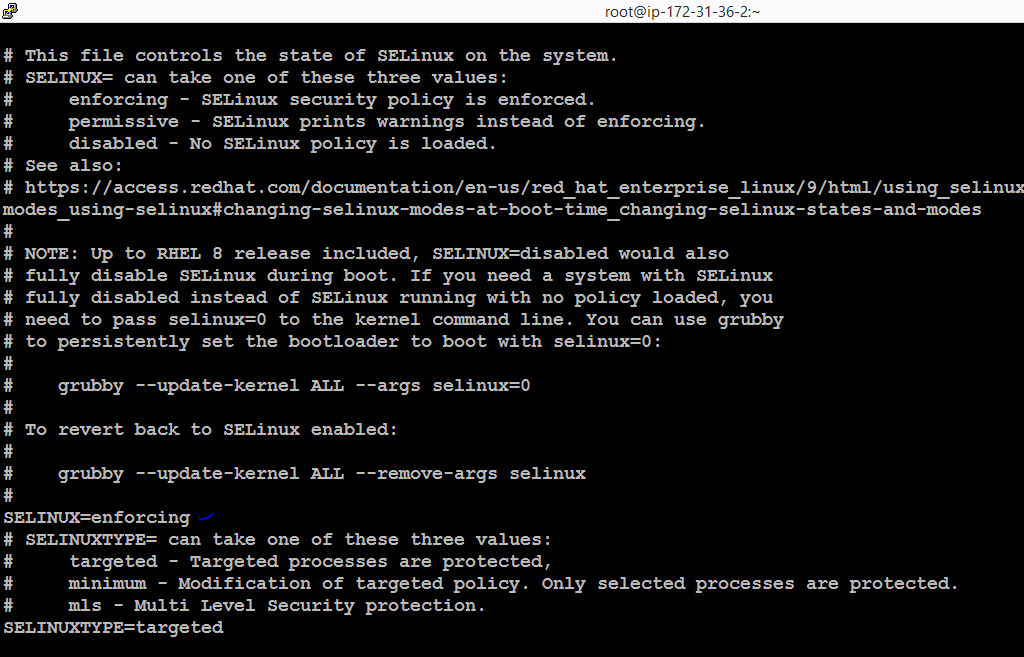
For permanent changes, you need to edit the SELinux configuration file, usually located at /etc/selinux/config. Modify the SELINUX directive to either enforcing, permissive, or disabled, and then restart your system.
Conclusion
SELinux is a powerful security feature in Linux that provides fine-grained control over how processes interact with each other and the system's resources. Understanding SELinux values and types, checking its status, viewing security contexts, changing modes, and modifying contexts are essential skills for any Linux administrator. By effectively leveraging SELinux, you can significantly enhance the security posture of your systems and mitigate potential threats.
Subscribe to my newsletter
Read articles from Dinesh Kumar K directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Dinesh Kumar K
Dinesh Kumar K
Hi there! I'm Dinesh, a passionate Cloud and DevOps enthusiast. I love to dive into the latest new technologies and sharing my journey through blog.