WazirX Transaction Analysis
 Cryptomedication
Cryptomedication
Consider some of the following biographical information related to what we're looking at too:
The address of the logic contract / implementation is
0xd9db270c1b5e3bd161e8c8503c55ceabee709552. That contract was created at TX0x0b04589bdc11585fb98f270b1bfeff0fb3bbb3c56d35b104f62d8115d6f7c57fat block12504268`. This is a smart contract created by Gnosis Safe and used as an implementation proxy address for another smart contract that was exploited by the proxy storage address.The address for the proxy smart contract address that was compromised was
0x27fD43BABfbe83a81d14665b1a6fB8030A60C9b4and that was created by the transaction ID0x3c889ee7c1a19bb15d899f21c5c7d9da0af0c5a5f597f0e288b7309169b4dba5and deployed by0xD7Df5bf3B8d2bd159664dF54A30101d7FAF6cA26by making a call on the smart contract0x4e59b44847b379578588920cA78FbF26c0B4956Cto deploy the smart contract address which is labeled assingleton. The address responsible for deploying this contract is0xfA54B4085811aef6ACf47D51B05FdA188DEAe28bat block height16132578and it was deployed from the Gnosis Safe Factory contract located at0xfA54B4085811aef6ACf47D51B05FdA188DEAe28b.When the smart contract storage proxy address
0x27fD43BABfbe83a81d14665b1a6fB8030A60C9b4was created, it established 5 different owners. Those owners are0xaE648f68823bc164CA3ad1f5f5dC0057d9d515aD,0x10F16CdE93f1bC9C38a9e31C8DB0eEb89a744824,0xD83b89E261D02B0f2f9E384B44907f8d380E9AF0,0x9AF78003CecC2383d9D576A49c0C6b17fc34Ae34and0xfA54B4085811aef6ACf47D51B05FdA188DEAe28b. The threshold for this multi-signature address was established as3. The initializer was0x0000000000000000000000000000000000000000and the address for the smart contract designated as thefallbackHandlerwas0xf48f2B2d2a534e402487b3ee7C18c33Aec0Fe5e4. This transaction also designated0xd9Db270c1B5E3Bd161E8c8503c55cEABeE709552as thesingletonfor this address. The singleton is the logic proxy address that we're examining that serves as the main address.The transaction that ultimately compromised both smart contracts in question occurred at transaction ID:
0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d. The sender of the transaction was an EOA with the address0xd967113224c354600b3151e27aaba53e3034f372at block height20331565. The transaction involved a delegatecall being made to the singleton smart contract at0xd9db270c1b5e3bd161e8c8503c55ceabee709552(which is our flattened smart contract) before eventuallycalldatawas forwarded to a malicious smart contract address located at0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2. This EOA (0xd967113224c354600b3151e27aaba53e3034f372)was added as an owner to the0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4smart contract in February 2023 during transaction ID:0xfda0801c5f916fc17d042a8297af15ccdfa91bc12d530fda4708c159e992b19a. The multi-signature threshold was subsequently raised to4afterward.
The source code for all smart contracts involved in the creation of the two proxy smart contracts that I mentioned (0x27fD43BABfbe83a81d14665b1a6fB8030A60C9b4 and 0xd9db270c1b5e3bd161e8c8503c55ceabee709552) are verified on Etherscan already. Thus, if there is any additional information that is needed then that can be obtained from the blockchain directly.
It is known that none of the keys involved in the multi-signature orchestration were compromised at any point in time and this has been independently verified after the fact. Thus, the flaw, vulnerability or exploit must be laden within the smart contracts themselves. Since the logic within the main proxy (0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4) is nominal at best, we have decided to set our focus on dissecting the singleton contract that was associated with the deployed proxy from Gnosis Safe.
During the malicious transaction we observed that the storage data in slot 0 was updated for the main proxy. This update swapped out the legitimate singleton contract for a malicious one at 0xef279c2ab14960aa319008cbea384b9f8ac35fc6. The malicious contract that was responsible for returning data back to the main proxy, resulting in an update of that proxy's singleton address value in slot 0 is at the address 0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2. The bytecode for both malicious contracts is not verified or available on Etherscan. Therefore, any and all attempts to dissect the true nature of these smart contracts will be contingent on the efficacy of associated bytecode disassemblers.
That transaction can be found here. The transaction itself is highly complex and reveals a lot of potential issues in the Safe contract deployment (yes, those guys formerly known as Gnosis Safe).
Before we make anymore assertions about the nature of the hack, let's go ahead and take a look at the malicious transaction, starting with Etherscan's view.
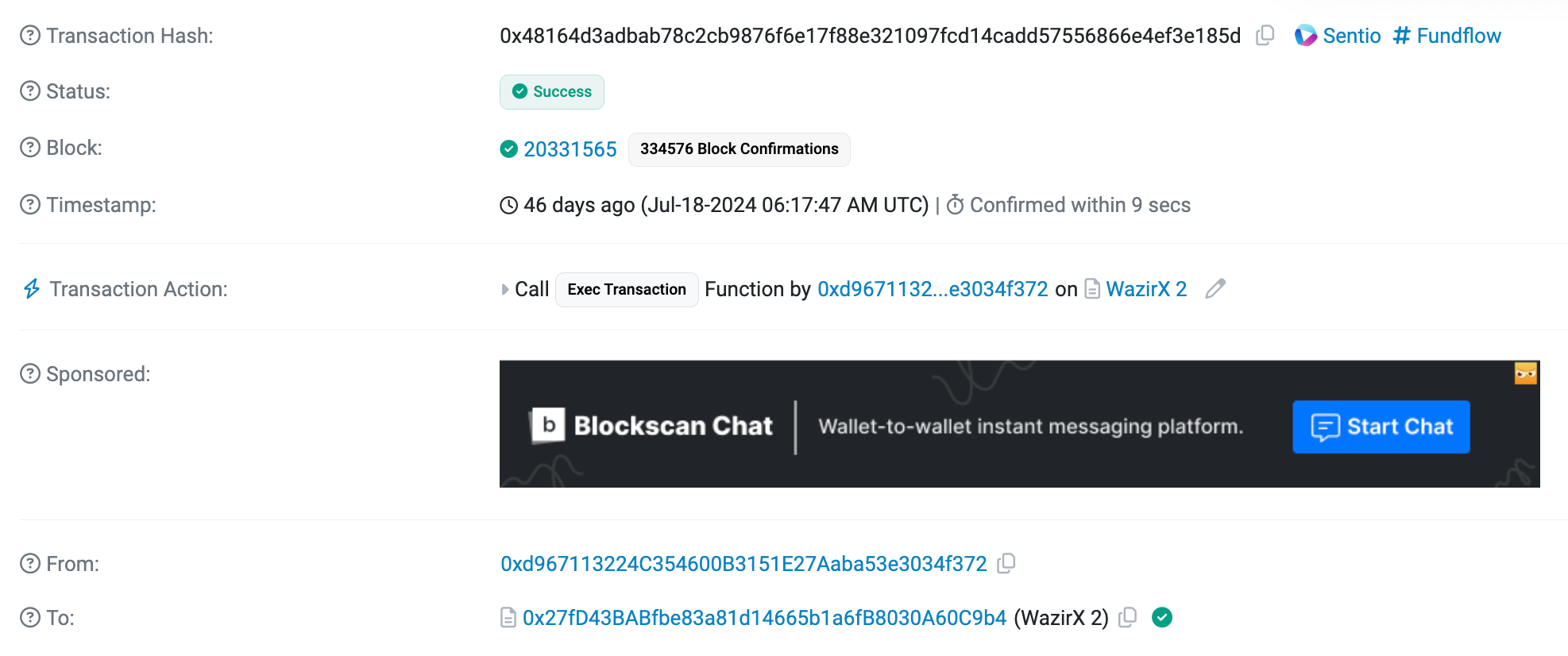
As we can see, it appears that the transaction was initiated by the 0xd967 address - which we've already established as belonging to the team.
The transaction was sent directly to the 0x27fD address, which is the WazirX team's main proxy. As we've discussed in a (separate guide), the specific proxy upgradable orchestration that WazirX used involves deploying a unique proxy from a "factory contract" (which served as the 'template' for their proxy).
However, the other associated contracts (i.e., their implementation/singleton & fallback handler) are Gnosis Safe deployments. They were never deployed or owned by the team. Thus, any compromise arising out of the functionality of those contracts should also be attributed to the Safe team (more specifically for their failure to make it a widespread imperative for users to upgrade to better constructed implementations).
Getting back to the malicious transaction, let's take a look at the internal transaction trace that the malicious transaction created:
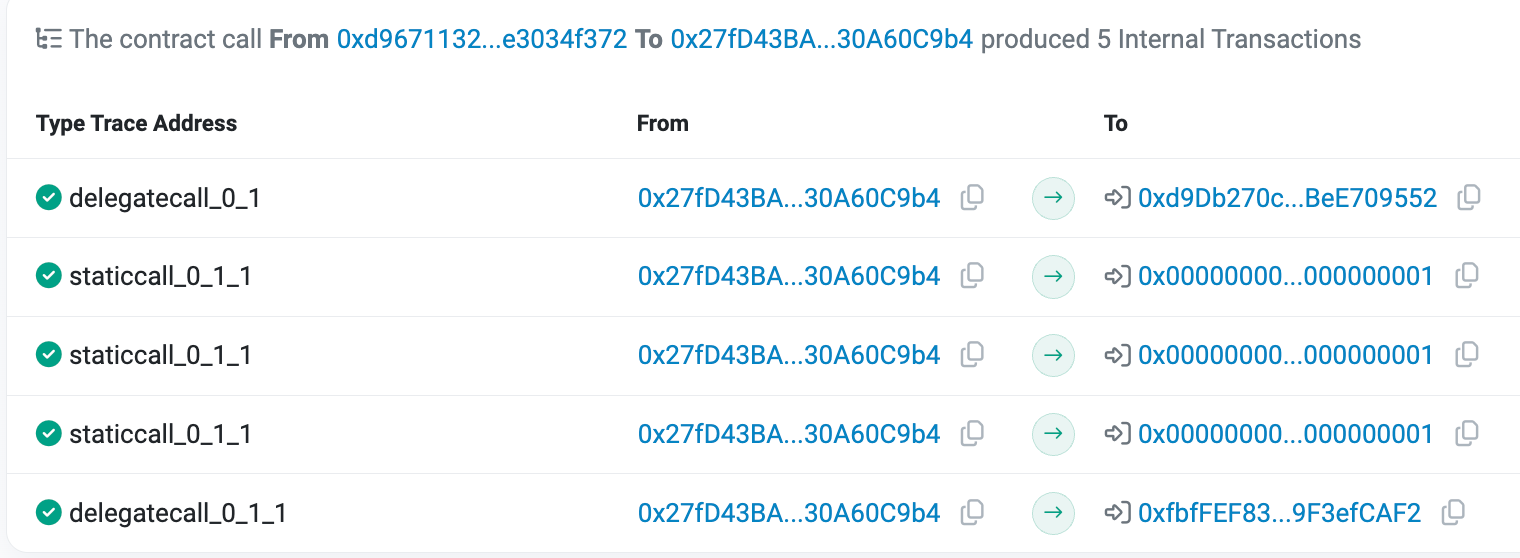
As we can see abvoe, the entry point was the team's proxy contract with a function call that triggered the contract's
fallbackfunction, ultimately leading to a call being delegated to a malicious proxy contract (0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2)
Moving forward, let's see if we can't glean more information about the nature of this attack by looking at a simple stack execution trace of the actual compromise.
Check out the parity stack trace below (you can find this on Etherscan too):
{
"action": {
"from": "0xd967113224c354600b3151e27aaba53e3034f372",
"callType": "call",
"gas": "0x2c9f8",
"input": "0x6a761202000000000000000000000000fbffef83b1c172fe3bc86c1ccb036ab9f3efcaf20000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000014000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001a00000000000000000000000000000000000000000000000000000000000000024804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc60000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001043da7c6bd7c130430cf662de3d9af067c4a0629f849e29003c40ad3979cd670720c3ceb3a61e38fb7166353e3262eb6554c3f6571807cf22f9bdc4a83a56441661f8e64a89386af2f223b8433a1df65db8f0ff60544b2f02c56ec02b640d6fb15a11f7dffda5b99b0292b5e02d0cc44508d7d8f994515358e9da3016d8098b2258820000000000000000000000000d967113224c354600b3151e27aaba53e3034f37200000000000000000000000000000000000000000000000000000000000000000140082eba0f71627a3451d47132b8f4c266bc9be2bebe4424848757d10f13e76963af0b543a2357765d9f290410e919301ad065f0f2efa1233eb8634c93111f0e2000000000000000000000000000000000000000000000000000000000",
"to": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"value": "0x0"
},
"blockHash": "0xf0716718399afb665776df3378a2bc7c1ff02c03a40af8d6471193b1611b873b",
"blockNumber": 20331565,
"result": {
"gasUsed": "0xb4eb",
"output": "0x0000000000000000000000000000000000000000000000000000000000000001"
},
"subtraces": 1,
"traceAddress": [],
"transactionHash": "0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d",
"transactionPosition": 21,
"type": "call"
},
{
"action": {
"from": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"callType": "delegatecall",
"gas": "0x2abe6",
"input": "0x6a761202000000000000000000000000fbffef83b1c172fe3bc86c1ccb036ab9f3efcaf20000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000014000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001a00000000000000000000000000000000000000000000000000000000000000024804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc60000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001043da7c6bd7c130430cf662de3d9af067c4a0629f849e29003c40ad3979cd670720c3ceb3a61e38fb7166353e3262eb6554c3f6571807cf22f9bdc4a83a56441661f8e64a89386af2f223b8433a1df65db8f0ff60544b2f02c56ec02b640d6fb15a11f7dffda5b99b0292b5e02d0cc44508d7d8f994515358e9da3016d8098b2258820000000000000000000000000d967113224c354600b3151e27aaba53e3034f37200000000000000000000000000000000000000000000000000000000000000000140082eba0f71627a3451d47132b8f4c266bc9be2bebe4424848757d10f13e76963af0b543a2357765d9f290410e919301ad065f0f2efa1233eb8634c93111f0e2000000000000000000000000000000000000000000000000000000000",
"to": "0xd9db270c1b5e3bd161e8c8503c55ceabee709552",
"value": "0x0"
},
"blockHash": "0xf0716718399afb665776df3378a2bc7c1ff02c03a40af8d6471193b1611b873b",
"blockNumber": 20331565,
"result": {
"gasUsed": "0xa187",
"output": "0x0000000000000000000000000000000000000000000000000000000000000001"
},
"subtraces": 1,
"traceAddress": [
0
],
"transactionHash": "0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d",
"transactionPosition": 21,
"type": "call"
},
{
"action": {
"from": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"callType": "delegatecall",
"gas": "0x214ec",
"input": "0x804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6",
"to": "0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2",
"value": "0x0"
},
"blockHash": "0xf0716718399afb665776df3378a2bc7c1ff02c03a40af8d6471193b1611b873b",
"blockNumber": 20331565,
"result": {
"gasUsed": "0xc2e",
"output": "0x"
},
"subtraces": 0,
"traceAddress": [
0,
0
],
"transactionHash": "0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d",
"transactionPosition": 21,
"type": "call"
}
Later on, we’re going to go ahead and dissect the bytecode that was sent to the malicious contract and walk through how the opcodes operated on said calldata, step by step to get a better understanding of how this compromise took place.
While this raw trace (parity) is far from complete in terms of what it does for us, it does provide us with some preliminary information that can begin to give us an understanding of how this hack took place:
The initial 'action' (i.e., function call) is noted as coming from the
0xd967address (more on what this means later and how the hackers could have possibly done this).That call - which was made to the WazirX main proxy (
0x27fd4), triggered the proxy's fallback function, which will always be adelegatecallby default (that's how proxies are designed). For those new to the world of smart contract hacks, compromises, rugpulls etc., this opcode is one of the most problematic ones in the entire EVM system.The first 4 bytes of the
calldatatell us what function was being called. If you look back at thejsonstack execution trace that's printed above, you can identify thecalldataas that large hexadecimal value next to the topic called "input". If you found it, then you'll notice the first 8 characters (4 bytes) after the0xprefix are6a761202. This hexadecimal value corresponds with the function that was called by the hacker. A quick lookup in a database like4bytesorevm.codesreveals that this hexadecimal value corresponds with the function signatureexecTransaction(address,uint256,bytes,uint8,uint256,uint256uint256,address,address,bytes).The
calldatathat was ultimately sent to the malicious proxy was0x804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6. There have been some attempts to dissect the meaning of this calldata already in the general public. But thus far, most analyses fall woefully short of breaking down the potency of this short, yet simply craftedcalldatavalue.
What makes this hack so intriguing is its complexity. Despite all we've covered thus far, we've still barely scratched the surface in terms of how exactly the threat actor was able to compromise WazirX. But without any further deliberation, let's move forward here. A better breakdown of this transaction is going to require us decompiling the bytecode behind the calldata or piping the transaction itself into a high-quality debugger.
Before we do that, we’re going to need to get a more detailed view of the stack execution trace. This is going to require us going through a debugger similar - either via the terminal or through the use of an online tool that we can use like ‘Tenderly’, ‘Sentio’ or ‘Phalcon’. The latter two of those three online tools are entirely free while Tenderly requires that we at least sign up to obtain a trial subscription (14 days) before payment is necessary. All of them come with their own specific benefits. For those that are not as comfortable with using the terminal, we’re going to go ahead and see
Fortunately, there are plenty of tools in the Ethereum ecosystem that will allow us to do either. And those tools cater to both developers and folks that aren't as comfortable with navigating a terminal. Let's start with the 'terminal' approach.
Before we do that, we’re going to need to get a more detailed view of the stack execution trace. This is going to require us going through a debugger similar - either via the terminal or through the use of an online tool that we can use like ‘Tenderly’, ‘Sentio’ or ‘Phalcon’. The latter two of those three online tools are entirely free while Tenderly requires that we at least sign up to obtain a trial subscription (14 days) before payment is necessary. All of them come with their own specific benefits. Since most users are not quite as well-versed with the terminal, we’re going to go ahead and look at those latter two visual debuggers.
Disclaimer: To be clear, the best debugger (in the author's opinion), would be Tenderly since it tends to give us the most accurate decoding of the stack execution trace, step by step. Misinterpretations of some of the steps as well as the sub-steps are what lead to differing outputs as far as the debuggers are concerned.
Sentio Debugger
For those that have never visited this site, you can find its main interface here: https://app.sentio.xyz.
They may ask you to signup on the main website. If you want to bypass this step, just go ahead and visit this link here: https://app.sentio.xyz/tx/1/0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d?t=1&block=0x131fe81 ; this will take you directly to the malicious transaction in question without being forced to sign-up or login to the website.
Once you arrive at the panel for the malicious transaction, you should see the following:
From here, we're going to take a look at some of the panels at the bottom, which go by the names of Call Trace, Call Graph and Gas Profiler (we're not quite as interested in the last tab, but we may take a breeze through it for good measure).
Call Trace Panel
If you're not used to looking at transaction traces, this may be a bit overwhelming at first, but don't worry - we'll make ourselves familiar with the context shortly
Upon firs visiting the Call Trace panel on the Sentio site for the malicious transaction, we should see the following at the bottom half of the page.
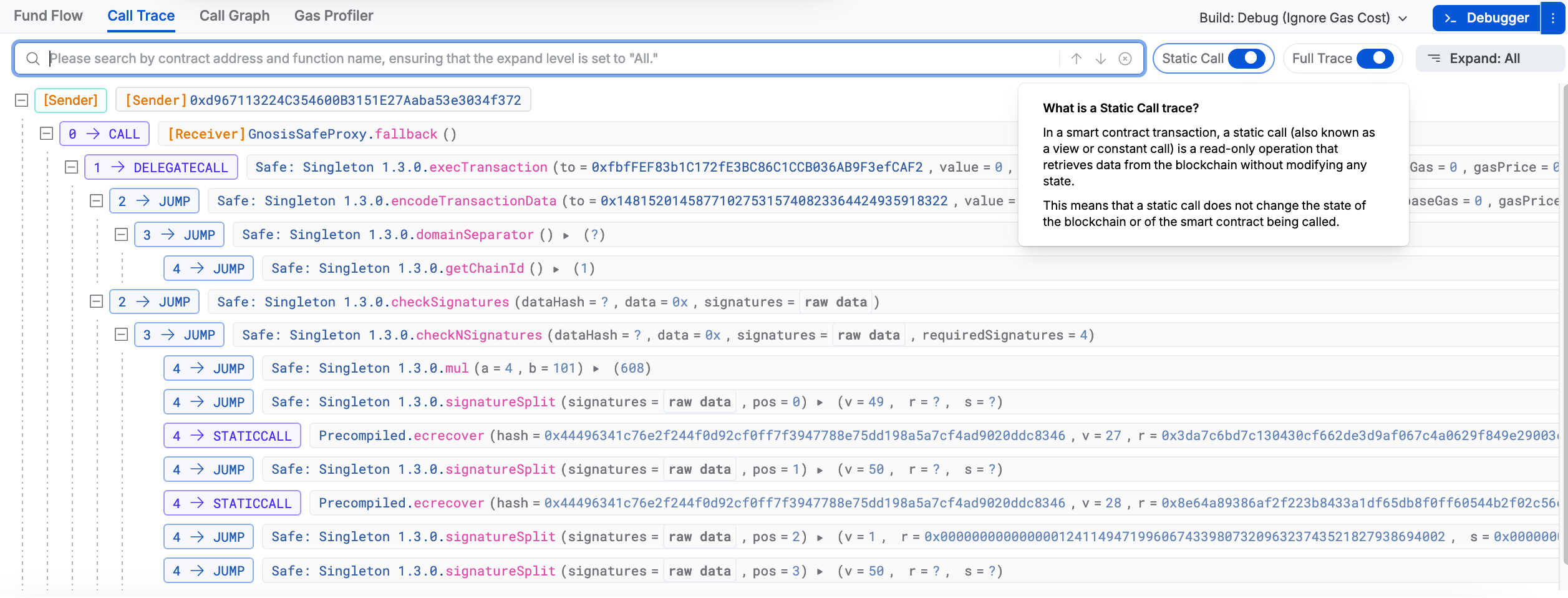
Its worth noting that definition for a 'Stack Call Trace' given in the top right corner of our screenshot above. Specifically, it states, "In a smart contract transaction, a static call (also known as a view or constant call) is a read-only operation that retrieves data from the blockchain without modifying any state. This means that a static call does not change the state of the blockchain or of the smart contract being called."
That's how we're able to get that stack execution trace that we see below (keep in mind, this still isn't the debugged version of the transaction). Some of the data here won't be entirely accurate and there are also some parts of the data that we need to further decode in order to get the "decoded" version.
Tenderly Debugged Transaction
Tenderly is probably the best platform to use if you want to not only get a thorough transaction trace but a fully debugged, stepped re-simulation of the transaction itself as well
Assuming you've already signed up for an account on Tenderly (they provide a free trial for new users for 14 days before restricting some features), this will be our best source for debugging the full transaction trace.
We're going to proceed forth with a free account for the sake of brevity (sorry, Tenderly, we're on a budget - but if you'd like to throw a free membership, that would be greatly appreciated!).
Seriously though, if you got the chance, make sure you go ahead and grab a Tenderly subscription / membership if you need to do anything even peripherally related to these activities in the blockchain space.
Once we're at the dashboard, we can go setup a virtual testnet, which will be based on a fork of the target network (Ethereum) at its current height (at the time of writing), which is well beyond the time of the hack. Don't worry though, if we need to revert the state of the blockchain to an earlier point in time, we'll be able to do so without any issue (you'll understand why this was mentioned later on).
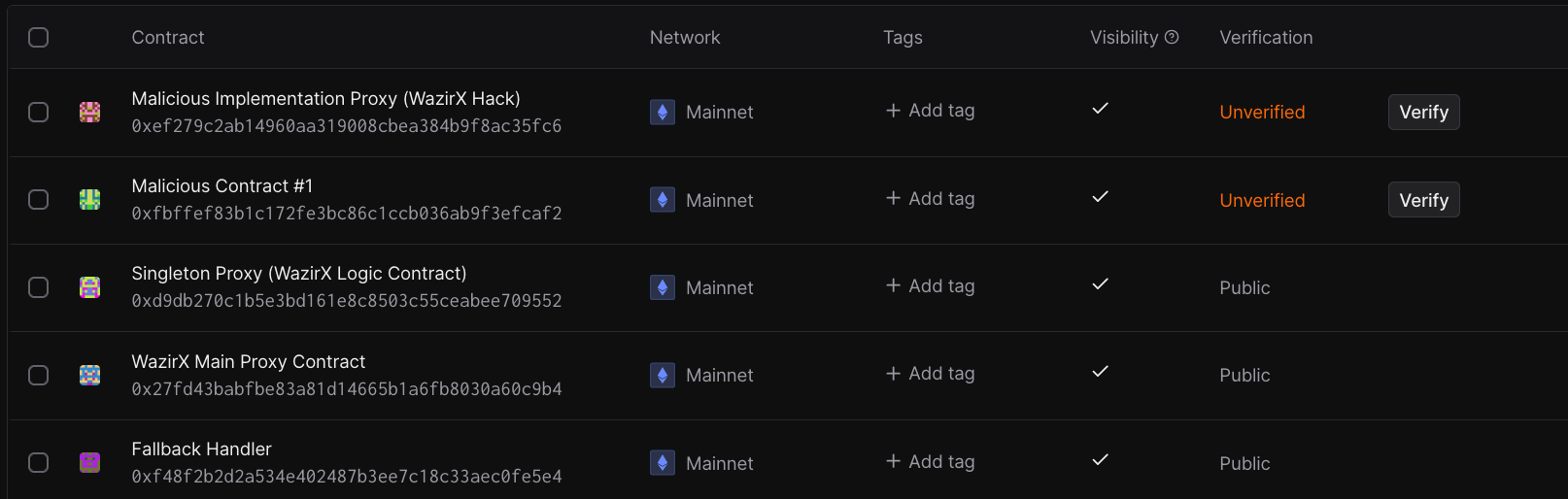
First, we're going to add some of the relevant contracts to our dashboard. See the truncated list of contracts we're going to provide below:
0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4(WazirX main proxy contract)0xd9Db270c1B5E3Bd161E8c8503c55cEABeE709552(Logic Contract/Singleton for the Main Proxy)0xf48f2B2d2a534e402487b3ee7C18c33Aec0Fe5e4(Fallback Handler for the Contract)0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2(this is the attacker contract that was involved in the OG malicious transaction that ultimately compromised the WazirX main proxy contract)
If you're feeling ambitious/productive, then you can go ahead and hunt down the factory contracts that some of the proxies were deployed from as well as the contracts responsible for the deployment (where this is applicable)
Now that we have the contracts added, let's take a renewed look at the stack execution trace for the main hack that occurred.
This requires having an RPC endpoint that we can query to get the full trace of the transaction. Since we have Tenderly, that's not an issue. On the lefthand side on the panel menu, there's an option that reads, 'Node RPCs'.
If we select that option, then we'll see an option to Create Node. Once we click on that, we just navigate through the interface and then select the appropriate options.
Once a node is created, users are taken to the following 'home screen' for their personal node (RPC endpoint).
On the lefthand side of the panel, we can see an option called 'RPC Builder'. We're going to select that option and then pull up the following screen.
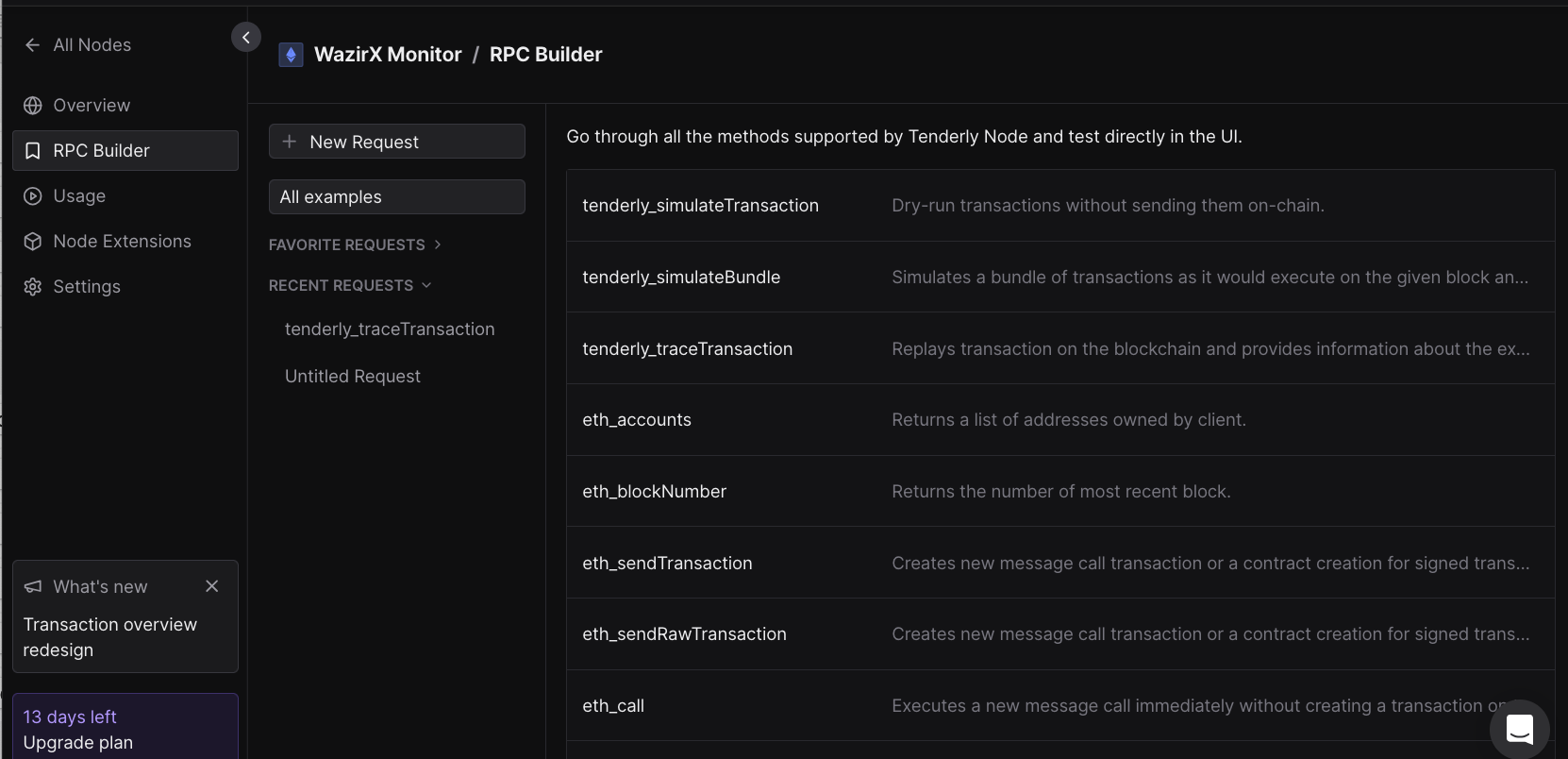
From here, we're going to select an RPC option called tenderly_traceTransaction. Its stated that this RPC call, "Replays transaction on the blockchain and provides information about the execution, such as status, logs, internal transactions, etc."
For those not as savvy with the terminal, all that one needs to do is edit the params key with the value of whatever transaction ID they're looking to receive a stack execution trace for (which in this case is 0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d).
If done correctly, your screen should look as follows:
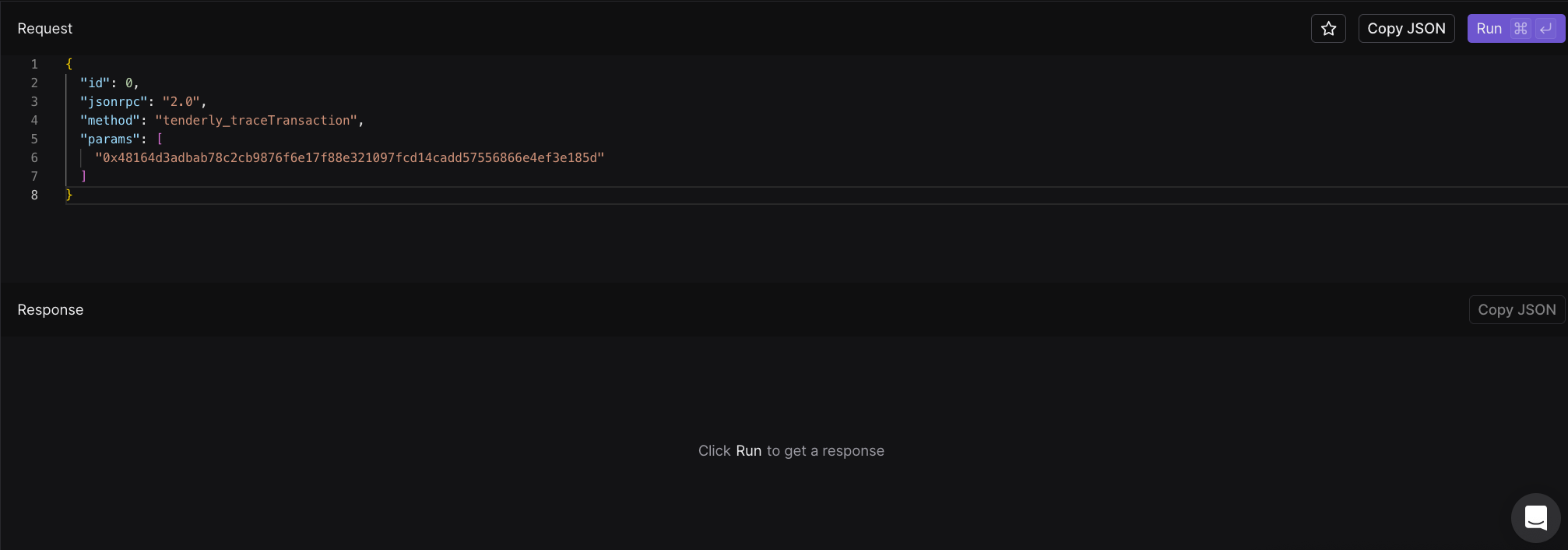
When we click the 'Run' button located at the top right, then we'll receive the full, detailed trace.
That trace should look like the following:
{
"id": 0,
"jsonrpc": "2.0",
"result": {
"status": true,
"gasUsed": "0x11f43",
"cumulativeGasUsed": "0x11f43",
"blockNumber": "0x1363c2d",
"type": "0x2",
"logsBloom": "0x00000000400000000000000000000000000000000000000000000000040000002000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004000000000000000000000000000000000000000000000000000000000000000000000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000",
"logs": [
{
"name": "ExecutionSuccess",
"anonymous": false,
"inputs": [
{
"value": "0x4e82121a3bc2fb62c0b06ab5fff5ca965ceab4f51cc949c6e50d85ed63e6aa70",
"type": "bytes32",
"name": "txHash",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "payment",
"indexed": false
}
],
"raw": {
"address": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"topics": [
"0x442e715f626346e8c54381002da614f62bee8d27386535b2521ec8540898556e"
],
"data": "0x4e82121a3bc2fb62c0b06ab5fff5ca965ceab4f51cc949c6e50d85ed63e6aa700000000000000000000000000000000000000000000000000000000000000000"
}
}
],
"trace": [
{
"type": "CALL",
"from": "0xd967113224c354600b3151e27aaba53e3034f372",
"to": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"gas": "0x2c9f8",
"gasUsed": "0xb4eb",
"value": "0x0",
"input": "0x6a761202000000000000000000000000fbffef83b1c172fe3bc86c1ccb036ab9f3efcaf20000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000014000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001a00000000000000000000000000000000000000000000000000000000000000024804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc60000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001043da7c6bd7c130430cf662de3d9af067c4a0629f849e29003c40ad3979cd670720c3ceb3a61e38fb7166353e3262eb6554c3f6571807cf22f9bdc4a83a56441661f8e64a89386af2f223b8433a1df65db8f0ff60544b2f02c56ec02b640d6fb15a11f7dffda5b99b0292b5e02d0cc44508d7d8f994515358e9da3016d8098b2258820000000000000000000000000d967113224c354600b3151e27aaba53e3034f37200000000000000000000000000000000000000000000000000000000000000000140082eba0f71627a3451d47132b8f4c266bc9be2bebe4424848757d10f13e76963af0b543a2357765d9f290410e919301ad065f0f2efa1233eb8634c93111f0e2000000000000000000000000000000000000000000000000000000000",
"decodedInput": [
{
"value": "0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2",
"type": "address",
"name": "to",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "value",
"indexed": false
},
{
"value": "0x804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6",
"type": "bytes",
"name": "data",
"indexed": false
},
{
"value": 1,
"type": "uint8",
"name": "operation",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "safeTxGas",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "baseGas",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "gasPrice",
"indexed": false
},
{
"value": "0x0000000000000000000000000000000000000000",
"type": "address",
"name": "gasToken",
"indexed": false
},
{
"value": "0x0000000000000000000000000000000000000000",
"type": "address",
"name": "refundReceiver",
"indexed": false
},
{
"value": "0x3da7c6bd7c130430cf662de3d9af067c4a0629f849e29003c40ad3979cd670720c3ceb3a61e38fb7166353e3262eb6554c3f6571807cf22f9bdc4a83a56441661f8e64a89386af2f223b8433a1df65db8f0ff60544b2f02c56ec02b640d6fb15a11f7dffda5b99b0292b5e02d0cc44508d7d8f994515358e9da3016d8098b2258820000000000000000000000000d967113224c354600b3151e27aaba53e3034f37200000000000000000000000000000000000000000000000000000000000000000140082eba0f71627a3451d47132b8f4c266bc9be2bebe4424848757d10f13e76963af0b543a2357765d9f290410e919301ad065f0f2efa1233eb8634c93111f0e20",
"type": "bytes",
"name": "signatures",
"indexed": false
}
],
"output": "0x0000000000000000000000000000000000000000000000000000000000000001",
"decodedOutput": [
{
"value": true,
"type": "bool",
"name": "success",
"indexed": false
}
],
"subtraces": 1,
"traceAddress": []
},
{
"type": "DELEGATECALL",
"from": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"to": "0xd9db270c1b5e3bd161e8c8503c55ceabee709552",
"gas": "0x2abe6",
"gasUsed": "0xa187",
"input": "0x6a761202000000000000000000000000fbffef83b1c172fe3bc86c1ccb036ab9f3efcaf20000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000014000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001a00000000000000000000000000000000000000000000000000000000000000024804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc60000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001043da7c6bd7c130430cf662de3d9af067c4a0629f849e29003c40ad3979cd670720c3ceb3a61e38fb7166353e3262eb6554c3f6571807cf22f9bdc4a83a56441661f8e64a89386af2f223b8433a1df65db8f0ff60544b2f02c56ec02b640d6fb15a11f7dffda5b99b0292b5e02d0cc44508d7d8f994515358e9da3016d8098b2258820000000000000000000000000d967113224c354600b3151e27aaba53e3034f37200000000000000000000000000000000000000000000000000000000000000000140082eba0f71627a3451d47132b8f4c266bc9be2bebe4424848757d10f13e76963af0b543a2357765d9f290410e919301ad065f0f2efa1233eb8634c93111f0e2000000000000000000000000000000000000000000000000000000000",
"decodedInput": [
{
"value": "0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2",
"type": "address",
"name": "to",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "value",
"indexed": false
},
{
"value": "0x804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6",
"type": "bytes",
"name": "data",
"indexed": false
},
{
"value": 1,
"type": "uint8",
"name": "operation",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "safeTxGas",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "baseGas",
"indexed": false
},
{
"value": "0",
"type": "uint256",
"name": "gasPrice",
"indexed": false
},
{
"value": "0x0000000000000000000000000000000000000000",
"type": "address",
"name": "gasToken",
"indexed": false
},
{
"value": "0x0000000000000000000000000000000000000000",
"type": "address",
"name": "refundReceiver",
"indexed": false
},
{
"value": "0x3da7c6bd7c130430cf662de3d9af067c4a0629f849e29003c40ad3979cd670720c3ceb3a61e38fb7166353e3262eb6554c3f6571807cf22f9bdc4a83a56441661f8e64a89386af2f223b8433a1df65db8f0ff60544b2f02c56ec02b640d6fb15a11f7dffda5b99b0292b5e02d0cc44508d7d8f994515358e9da3016d8098b2258820000000000000000000000000d967113224c354600b3151e27aaba53e3034f37200000000000000000000000000000000000000000000000000000000000000000140082eba0f71627a3451d47132b8f4c266bc9be2bebe4424848757d10f13e76963af0b543a2357765d9f290410e919301ad065f0f2efa1233eb8634c93111f0e20",
"type": "bytes",
"name": "signatures",
"indexed": false
}
],
"method": "execTransaction",
"output": "0x0000000000000000000000000000000000000000000000000000000000000001",
"decodedOutput": [
{
"value": true,
"type": "bool",
"name": "success",
"indexed": false
}
],
"subtraces": 1,
"traceAddress": [
0
]
},
{
"type": "DELEGATECALL",
"from": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"to": "0xfbffef83b1c172fe3bc86c1ccb036ab9f3efcaf2",
"gas": "0x214ec",
"gasUsed": "0xc2e",
"input": "0x804e1f0a000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6",
"output": "0x",
"subtraces": 0,
"traceAddress": [
0,
0
]
}
],
"stateChanges": [
{
"address": "0x27fd43babfbe83a81d14665b1a6fb8030a60c9b4",
"storage": [
{
"slot": "0x0000000000000000000000000000000000000000000000000000000000000000",
"previousValue": "0x000000000000000000000000d9db270c1b5e3bd161e8c8503c55ceabee709552",
"newValue": "0x000000000000000000000000ef279c2ab14960aa319008cbea384b9f8ac35fc6"
},
{
"slot": "0x0000000000000000000000000000000000000000000000000000000000000005",
"previousValue": "0x00000000000000000000000000000000000000000000000000000000000006b6",
"newValue": "0x00000000000000000000000000000000000000000000000000000000000006b7"
}
]
},
{
"address": "0x95222290dd7278aa3ddd389cc1e1d165cc4bafe5",
"balance": {
"previousValue": "0xfd1064e88789a744",
"newValue": "0xfd11419f913eea44"
}
},
{
"address": "0xd967113224c354600b3151e27aaba53e3034f372",
"nonce": {
"previousValue": "0xb9c",
"newValue": "0xb9d"
},
"balance": {
"previousValue": "0xab9e0a1fde78eca",
"newValue": "0xab777e165b284d3"
}
}
]
}
}
Now that we have this full stack execution trace, we can properly assess what exactly happened here on a more thorough basis.
Subscribe to my newsletter
Read articles from Cryptomedication directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Cryptomedication
Cryptomedication
#Blockchain #BlockSec #OSINT #CyberSec #Darkweb | Isaiah 54:17 Fingerpint: 54EADD6FCBCF520E37A003E04D3ECE027AEFA381