Accessing Secrets Using Cross Account Role between Two AWS Accounts.
 Mahira Technology Private Limited
Mahira Technology Private Limited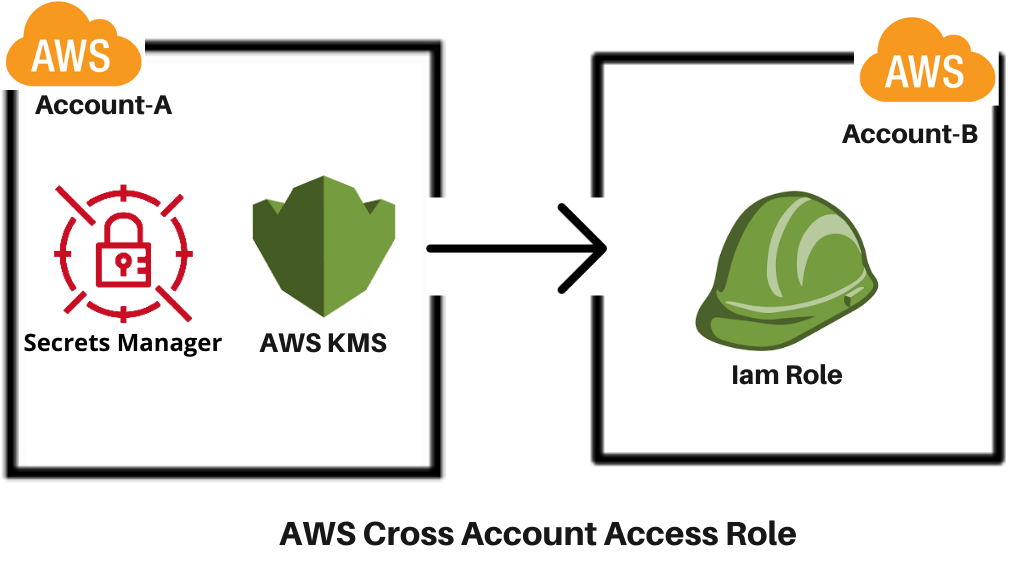
Introduction :-
In the world of cloud computing, managing secrets across different #AWS accounts can be a challenging task. However, by using cross-account roles, we can simplify this process and enhance security. This blog post will guide you through the steps of accessing secrets using a cross-account role, providing a secure and efficient method for managing sensitive information across multiple #AWS accounts.
Prerequisites :-
Before we dive into the procedure, make sure you have the following:
Two AWS account’s with the necessary permissions
#AWS CLI installed and configured
Basic understanding of #AWS Identity and Access Management (IAM)
Familiarity with #AWS Secrets Manager
Tip: If you’re new to AWS, consider reviewing the AWS documentation on IAM and Secrets Manager before proceeding.
Procedure :-
Step 1: Create a cross-account role in Account-B
Log in to the #AWS Management Console of the Account-B.
Navigate to the #IAM dashboard.
Click on “Roles” in the left sidebar, then “Create role”.
Choose “Custom trust policy” as the trusted entity type.
Add the below policy into the custom trust policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::AWS_Account-A_id:root"
},
"Action": "sts:AssumeRole"
}
]
}
Click on next and add the “SecretsManagerReadWrite” permissions policy.
Review and create the role, noting down the ARN of the new role.
Step-2:- Create #Kms key in the Account-A
Login to the #Aws Account-A and navigate to the key Management service.
Go to the customer managed keys and click on create a key.
choose the key type as symmetric and usage as encrypt & decrypt.
click on next and give an alias to the key, click on next.
select the administrator for the key and add the below key policy into the key.
{
"Sid": "Allow account administrators to manage the KMS key",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::${Account-A-id}:root"
},
"Action": [
"kms:*"
],
"Resource": "arn:aws:kms:${region}:${Account-A-id}:key/Your-KMS-Key-ID"
},
{
"Sid": "Enable cross account log decryption",
"Effect": "Allow",
"Action": "kms:Decrypt",
"Principal": {
"AWS": "arn:aws:iam::${Account-B-id}:role/cross-account-role-name"
},
"Resource": "arn:aws:kms:${region}:${Account-A-id}:key/Your-KMS-Key-ID",
"Condition": {
"StringEquals": {
"kms:ViaService": "secretsmanager.ca-central-1.amazonaws.com"
},
"StringLike": {
"kms:EncryptionContext:SecretARN": "arn:aws:secretsmanager:${region}:${Account-A-id}:secret:YOUR_SECRET_NAME"
}
}
}
Step-3:- Create Secret in the Account-A
Login to the #Aws Account-A and navigate to the secrets manager.
Create a secret with the below resource permissions.
Add the secret-key and values into the secret.
{
"Version" : "2012-10-17",
"Statement" : [ {
"Effect" : "Allow",
"Principal" : {
"AWS" : "arn:aws:iam::ACCOUNT-B-ID:role/CROSS_ACCOUNT_ROLE_NAME"
},
"Action" : "secretsmanager:GetSecretValue",
"Resource" : "*"
} ]
}
- Select the encryption key(#KMS key) in which u have been created in step-1.
Step 4: Assume the cross-account role
Open a command prompt window and configure your #AWS account-2 credentials(Access Keys). Using the #AWS CLI, assume the cross-account role:
aws sts assume-role --role-arn arn:aws:iam::AWS_ACCOUNT_2_ID:role/ROLE_NAME --role-session-name MySession
This command will return temporary security credentials.
Step 5: Configure #AWS CLI with temporary credentials
Set the following environment variables with the values from the previous step:
export AWS_ACCESS_KEY_ID=<AccessKeyId>
export AWS_SECRET_ACCESS_KEY=<SecretAccessKey>
export AWS_SESSION_TOKEN=<SessionToken>
Step 6: Access the secrets
Now you can use the #AWS CLI or SDK to access secrets in the other account:
aws secretsmanager get-secret-value --secret-id MySecret
Conclusion :-
Accessing secrets using a cross-account role provides a secure and manageable way to share sensitive information across #AWS accounts. By following this procedure, you can maintain the principle of least privilege while still allowing necessary access to secrets. Remember to regularly review and update your #IAM policies and roles to ensure ongoing security of your #AWS environment.
Subscribe to my newsletter
Read articles from Mahira Technology Private Limited directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mahira Technology Private Limited
Mahira Technology Private Limited
A leading tech consulting firm specializing in innovative solutions. Experts in cloud, DevOps, automation, data analytics & more. Trusted technology partner.