Understanding Cybersecurity Threats: In-Depth Incident Response Lifecycle Guide
 Logeshwaran N
Logeshwaran N
In the world of cybersecurity, the rise in the sophistication and frequency of cyberattacks has made incident response a crucial aspect of any organization’s defense strategy. Whether you're a small business or a multinational corporation, the ability to detect, mitigate, and recover from cyber incidents effectively can mean the difference between a minor disruption and a full-scale crisis. At the core of every successful cybersecurity program lies the Incident Response (IR) Lifecycle—a well-defined process designed to address and manage security breaches in a systematic manner. This article will guide you through each phase of the Incident Response Lifecycle and provide a real-world scenario to demonstrate its importance.
What is the Incident Response Lifecycle?
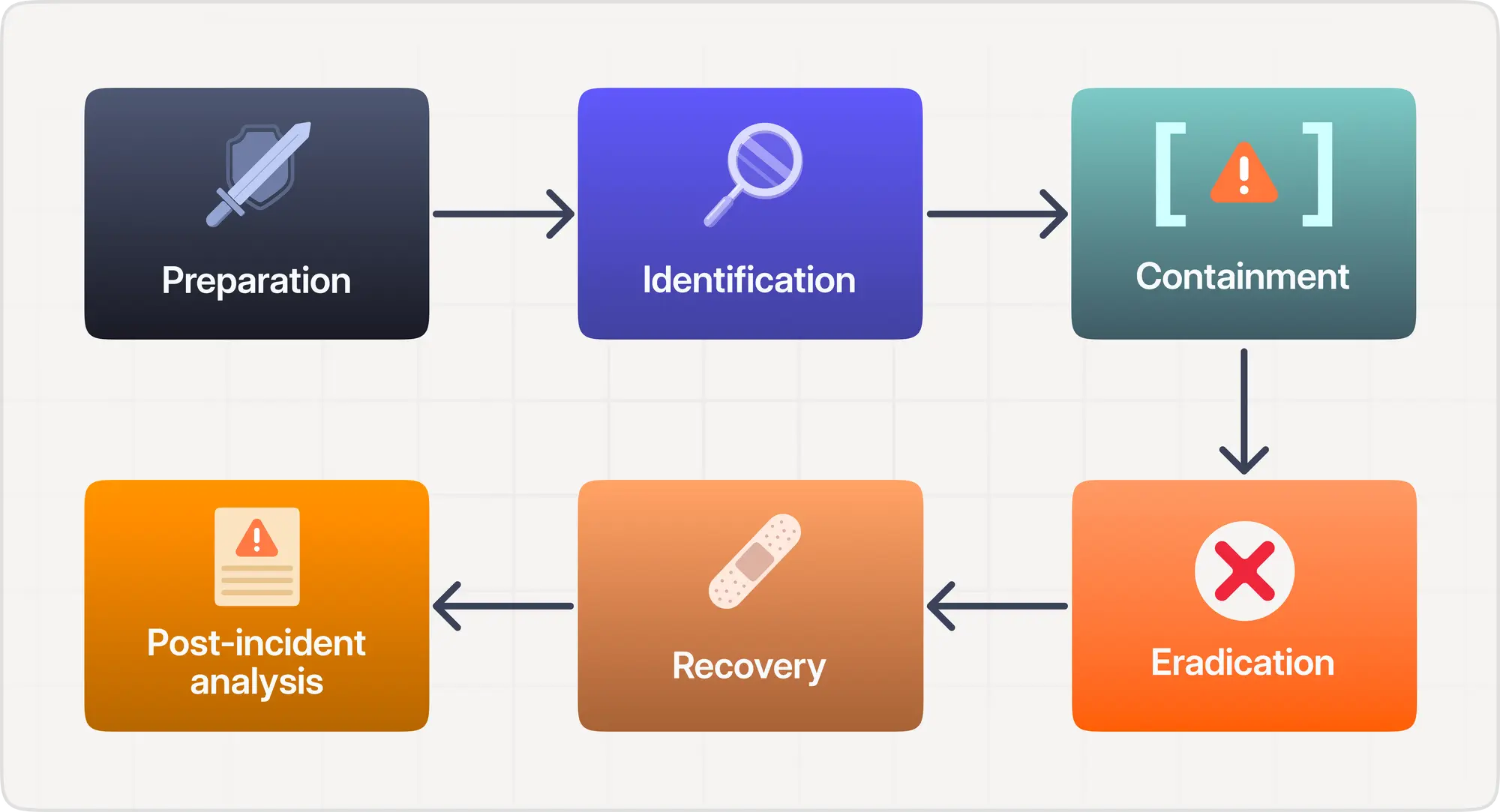
The Incident Response Lifecycle is a structured approach that helps organizations prepare for, detect, contain, and recover from cybersecurity incidents. A well-established Incident Response Lifecycle consists of the following phases:
Preparation
Detection & Analysis
Containment, Eradication, Recovery
Post-Mortem (Lessons Learned)
Each phase plays a crucial role in minimizing damage, reducing recovery time, and preventing future incidents. Now, let's explore these phases in detail, along with an illustrative real-world scenario that will help you better understand how these phases are applied in practice.
Phase 1: Preparation
The first and most important phase of the Incident Response Lifecycle is Preparation. It involves proactive measures to establish a robust incident response plan and ensure your team has the skills, tools, and processes needed to respond swiftly when an incident occurs. Preparation also includes implementing strong security measures, conducting regular training, and simulating potential incidents through tabletop exercises.
During this phase, organizations typically:
Establish an incident response policy and team.
Define roles and responsibilities.
Ensure relevant stakeholders are informed.
Develop communication plans for internal and external parties.
Deploy appropriate detection and monitoring systems.
Ensure all systems and data are backed up regularly.
Being well-prepared significantly reduces response time and can prevent an incident from spiraling into a crisis. It’s essential to have clear guidelines and procedures in place to tackle security breaches effectively. Additionally, running incident response drills simulates real-world scenarios, ensuring the team knows how to handle a crisis.
Real-world Scenario: Imagine a large financial institution, "FinCorp," that deals with thousands of sensitive customer transactions daily. As part of their preparation phase, FinCorp has a robust cybersecurity program in place, which includes multi-factor authentication (MFA), encryption, security awareness training for employees, and a comprehensive incident response plan. Regular security drills are conducted to ensure every employee knows their role in the event of an attack.
Phase 2: Detection & Analysis
The second phase, Detection & Analysis, focuses on identifying suspicious activity or potential security incidents and determining their scope and severity. Effective detection mechanisms are vital, as the faster a threat is identified, the quicker it can be addressed. Detection typically occurs through automated systems such as intrusion detection systems (IDS), Security Information and Event Management (SIEM) platforms, or manual reporting from employees or external partners.
This phase involves several key activities:
Identifying signs of potential incidents: This includes system alerts, abnormal traffic, login anomalies, or reports from employees who notice unusual activity.
Analyzing the threat: The incident response team must determine the nature of the attack, its scope, and its potential impact on the organization. They should classify the incident based on severity, which will guide the appropriate response.
Prioritizing incidents: Not all incidents require the same level of attention. By assessing the criticality of each incident, the team can allocate resources efficiently.
At this stage, collecting evidence is also crucial for further analysis and potential legal action, ensuring that logs, files, and data are secured to aid in future investigations.
Real-world Scenario: At FinCorp, a network anomaly triggers an alert in the SIEM system. A large volume of traffic is being sent from an external IP address to the internal network. The incident response team quickly reviews the logs and discovers that an employee's credentials may have been compromised. They initiate the detection and analysis phase, confirming that a phishing attack targeted the employee, leading to the unauthorized access attempt. Fortunately, MFA prevented the attacker from gaining full access, but the team continues to investigate whether any data was compromised.
Phase 3: Containment, Eradication, and Recovery
Once an incident is confirmed, the next step is to limit the damage, eliminate the threat, and restore normal operations. This phase is broken down into three distinct sub-stages: Containment, Eradication, and Recovery.
Containment: The goal here is to prevent the threat from spreading further. This could involve isolating infected systems, blocking malicious IP addresses, or disconnecting affected devices from the network. Containment strategies are divided into short-term (quick, immediate actions to prevent the spread) and long-term (more comprehensive fixes that ensure the attack is fully under control).
Eradication: After the threat is contained, it’s essential to remove all traces of the malicious actor from the network. This involves cleaning or rebuilding infected systems, applying patches, and closing any vulnerabilities that may have been exploited.
Recovery: Once eradication is complete, the focus shifts to restoring normal operations. This means ensuring that all affected systems are securely reinstated, and any damaged files or data are restored. Testing and monitoring are essential during this stage to confirm that the threat has been completely eliminated and systems are functioning properly.
Real-world Scenario: In our FinCorp example, once the attack is identified, the team immediately contains the breach by disconnecting the compromised employee's account and device from the network. After investigating further, they find that the phishing email contained a malware payload designed to steal login credentials. The malware is removed, and affected systems are thoroughly scanned. The team also resets the employee’s credentials, applies necessary patches, and verifies that all compromised systems are functioning correctly. Finally, FinCorp monitors the network for several days to ensure no further malicious activity occurs.
Phase 4: Post Mortem (Lessons Learned)
The final phase of the Incident Response Lifecycle is Post Mortem, also known as the Lessons Learned phase. After the incident has been contained and normal operations have resumed, it’s essential to conduct a thorough review of the incident to determine what went wrong, what was done well, and how future incidents can be prevented or handled more effectively.
Key activities in this phase include:
Conducting a detailed post-incident review.
Identifying gaps in the incident response process.
Documenting lessons learned and sharing them with relevant stakeholders.
Updating the incident response plan and security measures accordingly.
This phase not only helps improve your organization's resilience but also ensures that the same incident does not occur again. Continuous improvement in your incident response process is critical in staying one step ahead of cybercriminals.
Real-world Scenario: After the incident is resolved, FinCorp's security team holds a post-mortem meeting to review the breach in detail. They discover that although MFA prevented the attacker from gaining full access, there was a delay in detecting the phishing email due to insufficient email filtering rules. As a result, FinCorp decides to strengthen their email security protocols, increase employee training on phishing detection, and update their incident response plan to include quicker detection mechanisms for similar attacks in the future.
Conclusion
The Incident Response Lifecycle provides a comprehensive framework for managing cybersecurity incidents. By following a structured approach to preparation, detection, containment, and recovery, organizations can effectively respond to incidents, mitigate damage, and reduce downtime. A well-executed post-mortem ensures continuous improvement, making your organization more resilient to future attacks.
In a constantly evolving threat landscape, having a robust incident response plan in place isn't just a best practice—it's a necessity. As demonstrated in the FinCorp scenario, a swift, effective incident response can make all the difference in protecting sensitive data and maintaining business continuity. Every organization, regardless of size, should invest in strengthening its incident response capabilities to stay ahead of potential threats.
Subscribe to my newsletter
Read articles from Logeshwaran N directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Logeshwaran N
Logeshwaran N
I’m a dedicated Cloud and Backend Developer with a strong passion for building scalable solutions in the cloud. With expertise in AWS, Docker, Terraform, and backend technologies, I focus on designing, deploying, and maintaining robust cloud infrastructure. I also enjoy developing backend systems, optimizing APIs, and ensuring high performance in distributed environments. I’m continuously expanding my knowledge in backend development and cloud security. Follow me for in-depth articles, hands-on tutorials, and tips on cloud architecture, backend development, and DevOps best practices.