VPC Tutorial #3: How to set-up AWS VPC Endpoint a step-by-step guide
 Shivprasad Waghmare
Shivprasad Waghmare
Table of Contents -
Setup VPC and its components -
EC2 instance
S3 bucket
AWS CLI commands (aws configure)
IAM User
VPC Endpoints
Introduction -
- A VPC Endpoint lets you securely access services like S3 from a private subnet without using the internet. It's safer, faster, and cheaper.
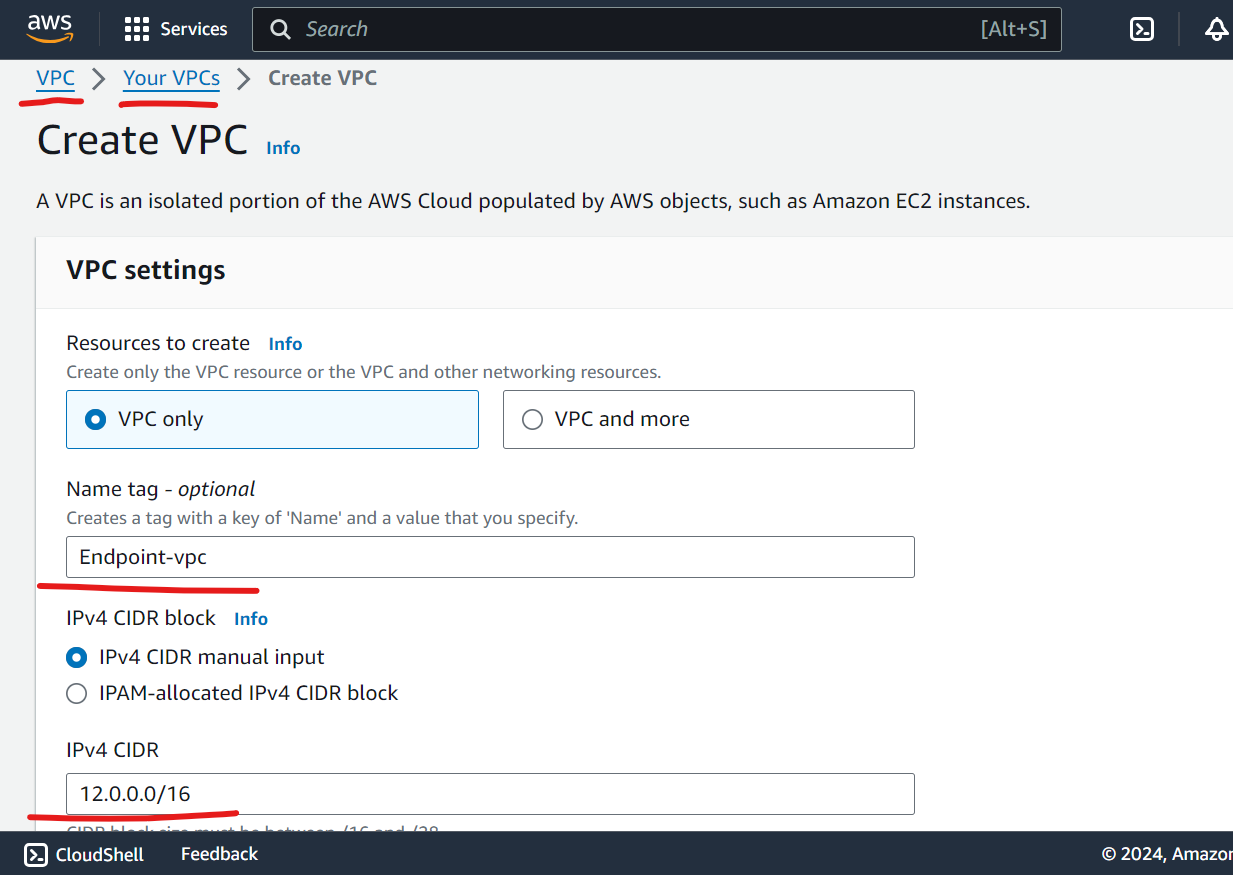
Step 1: Set Up a VPC and Its Components
Create a VPC: Follow step-by-step instructions for setting up a VPC.
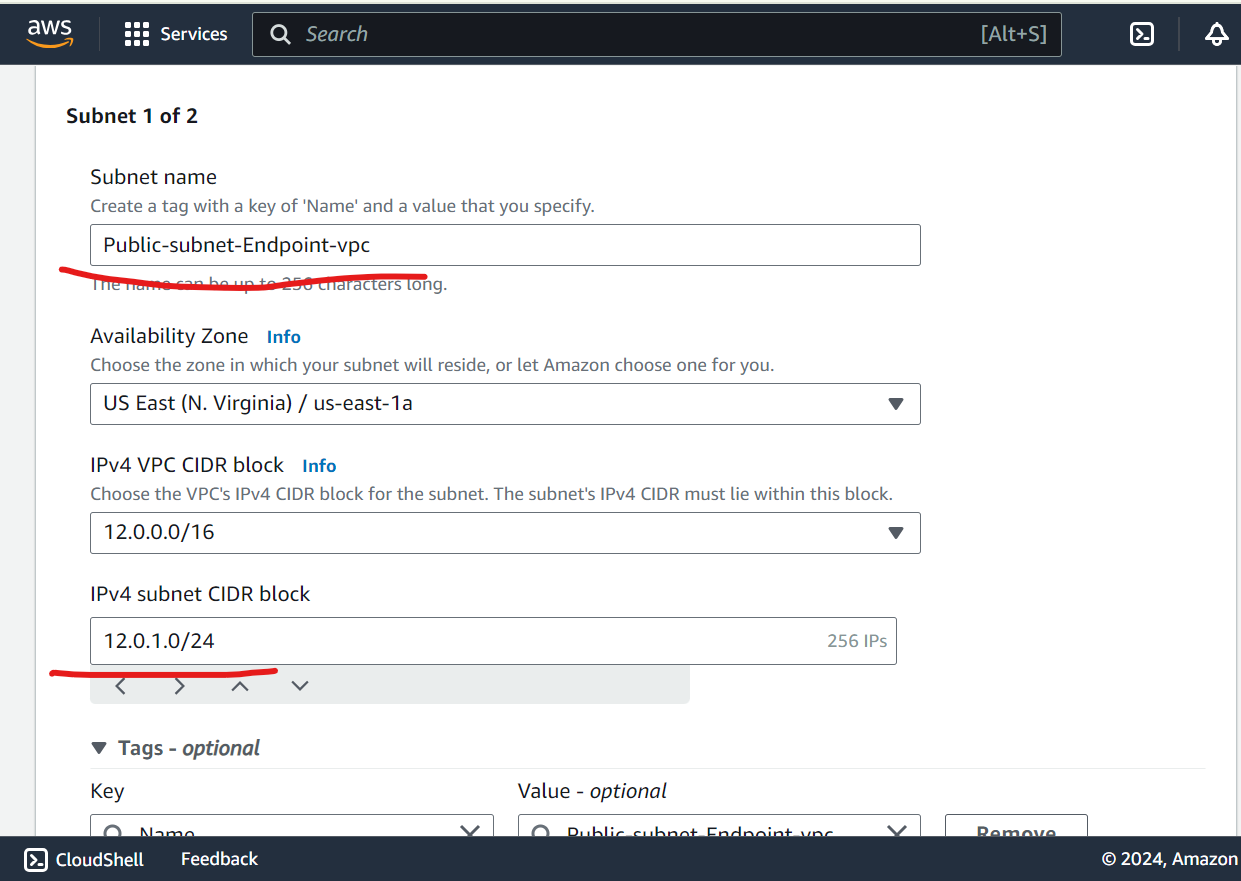
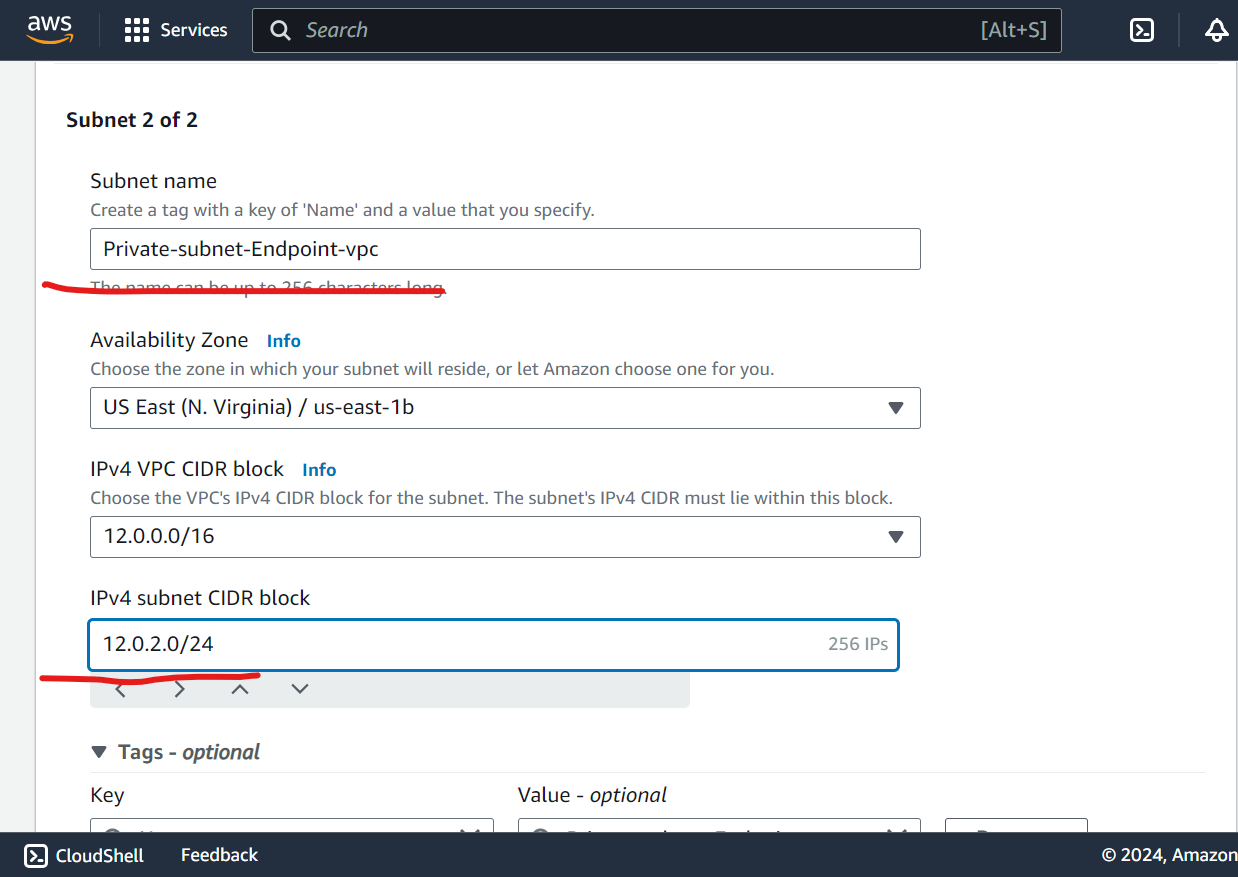
Create Subnets:
Add public and private subnets.
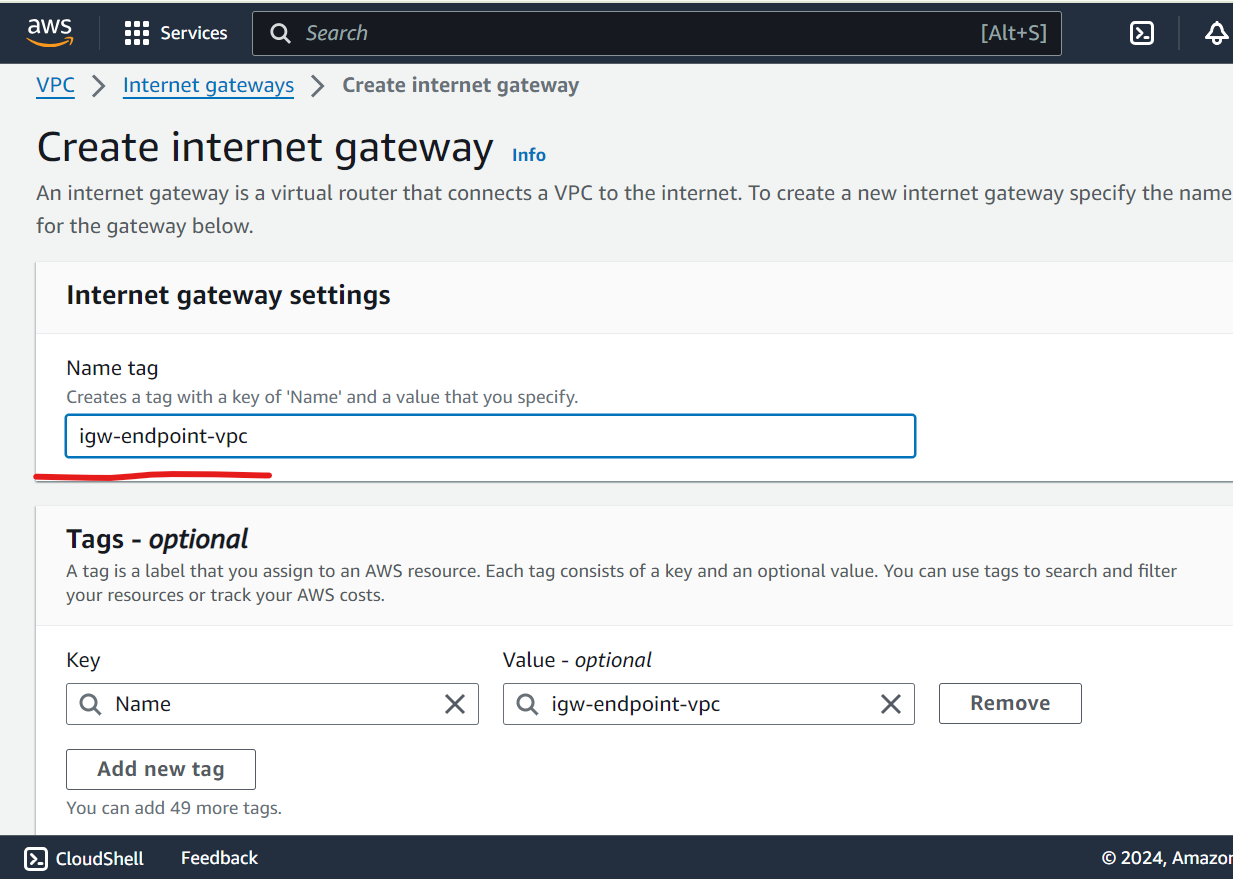
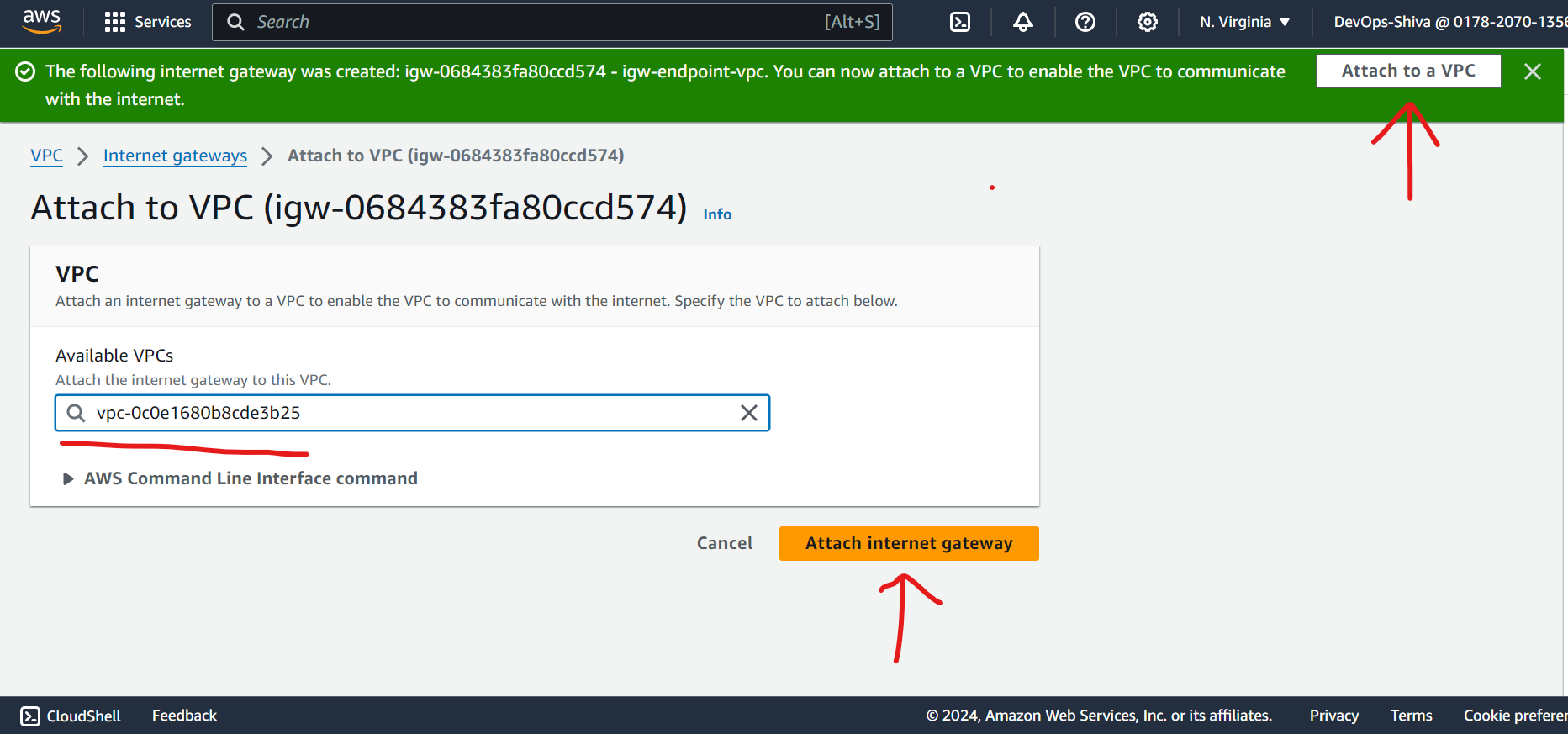
Configure Internet Gateway:
Attach an Internet Gateway to the VPC.
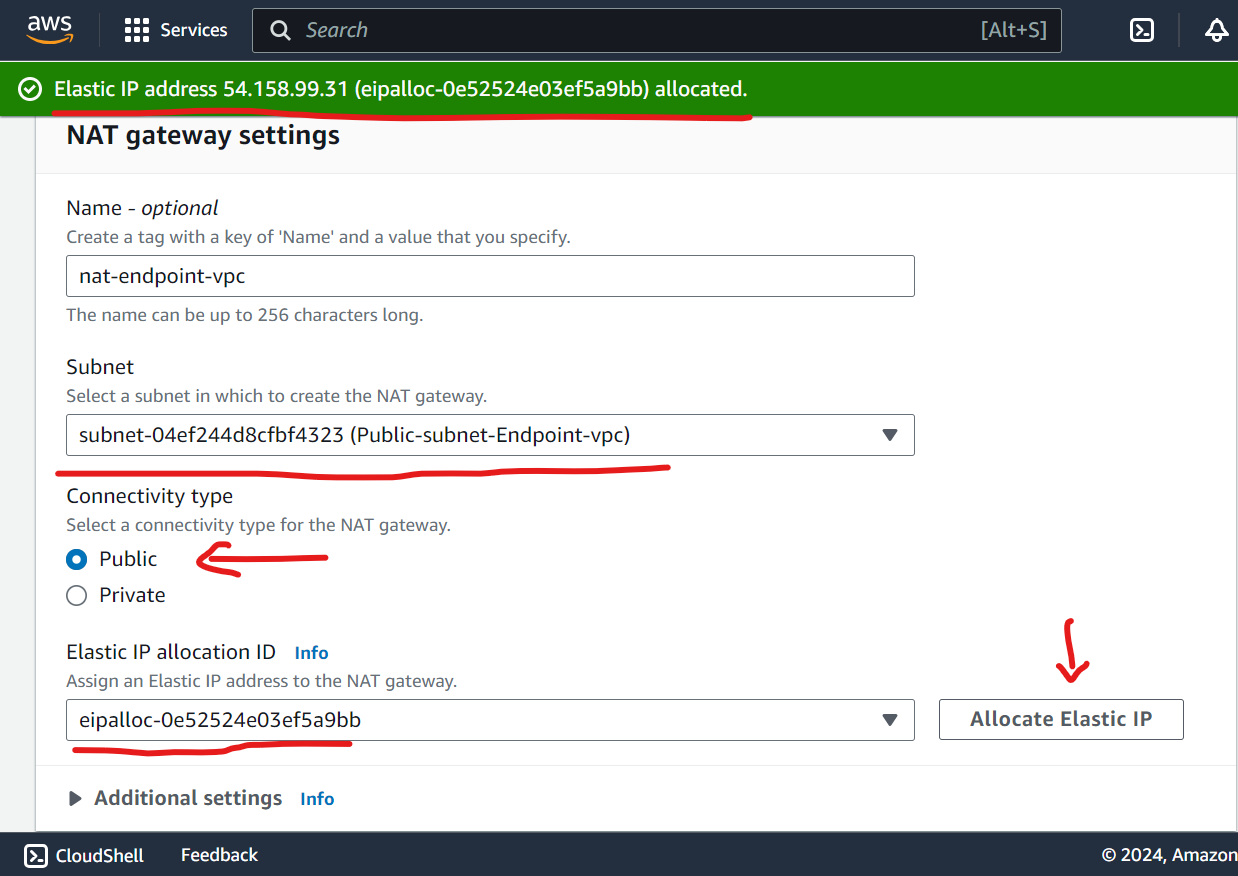
Configure NAT Gateway: ( Probably you asked me why? NAT? )
To install awscli in public EC2 instance, internet access needed and to facilitate internet in private subnet NAT gateway required.
Either allocate Elastic IP or choose from existing (if have).
Make sure you select public subnet not private.
Once awscli configured, delete nat gateway you don’t need it again.
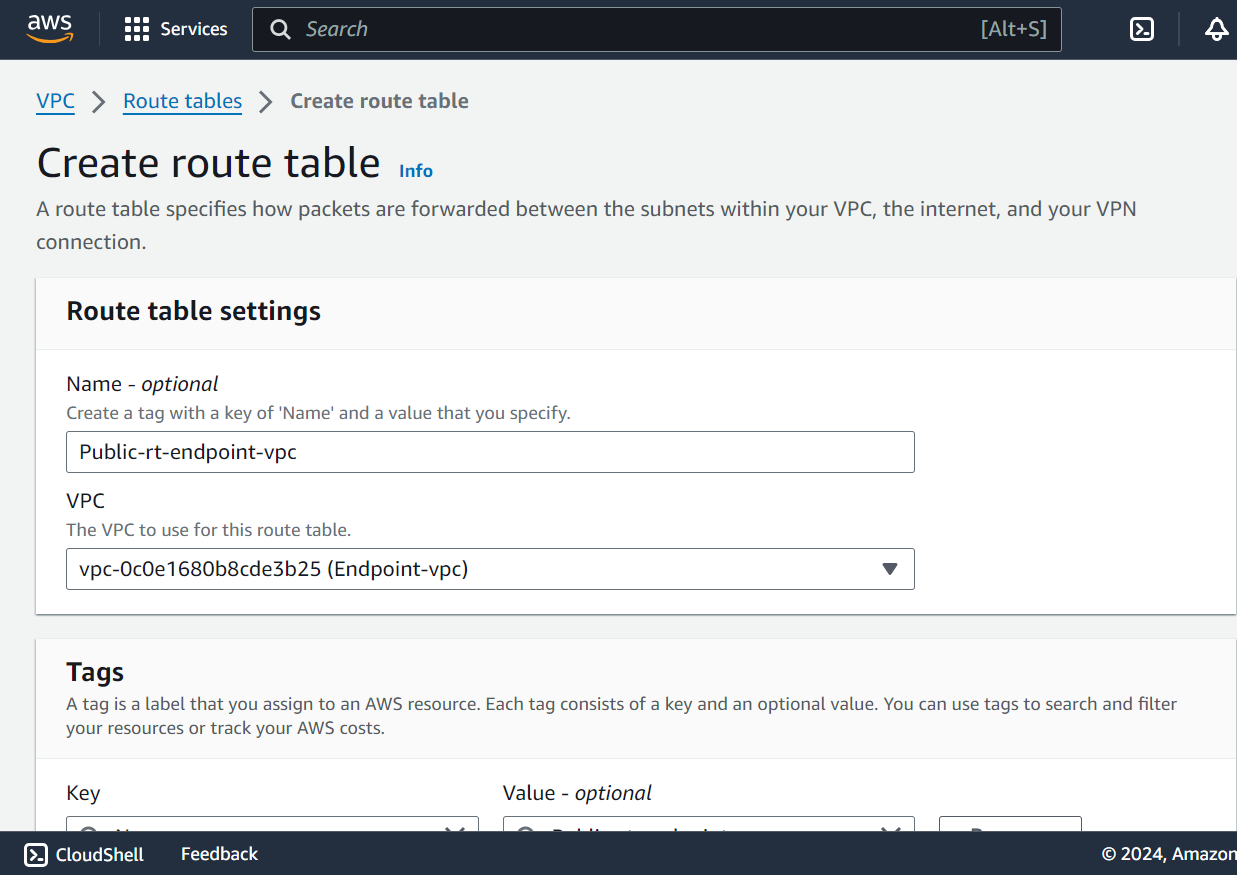
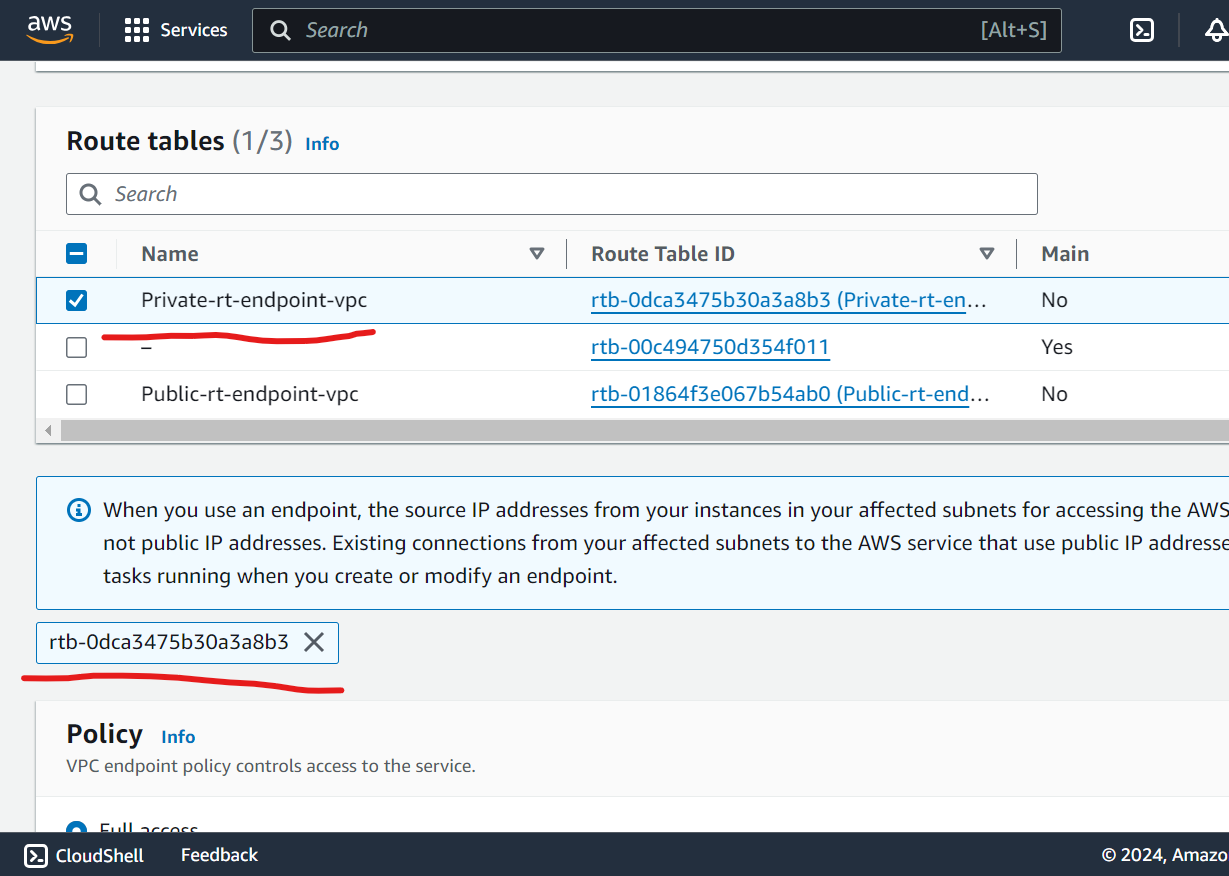
Set Up Route Tables:
Configure route tables for public subnet.
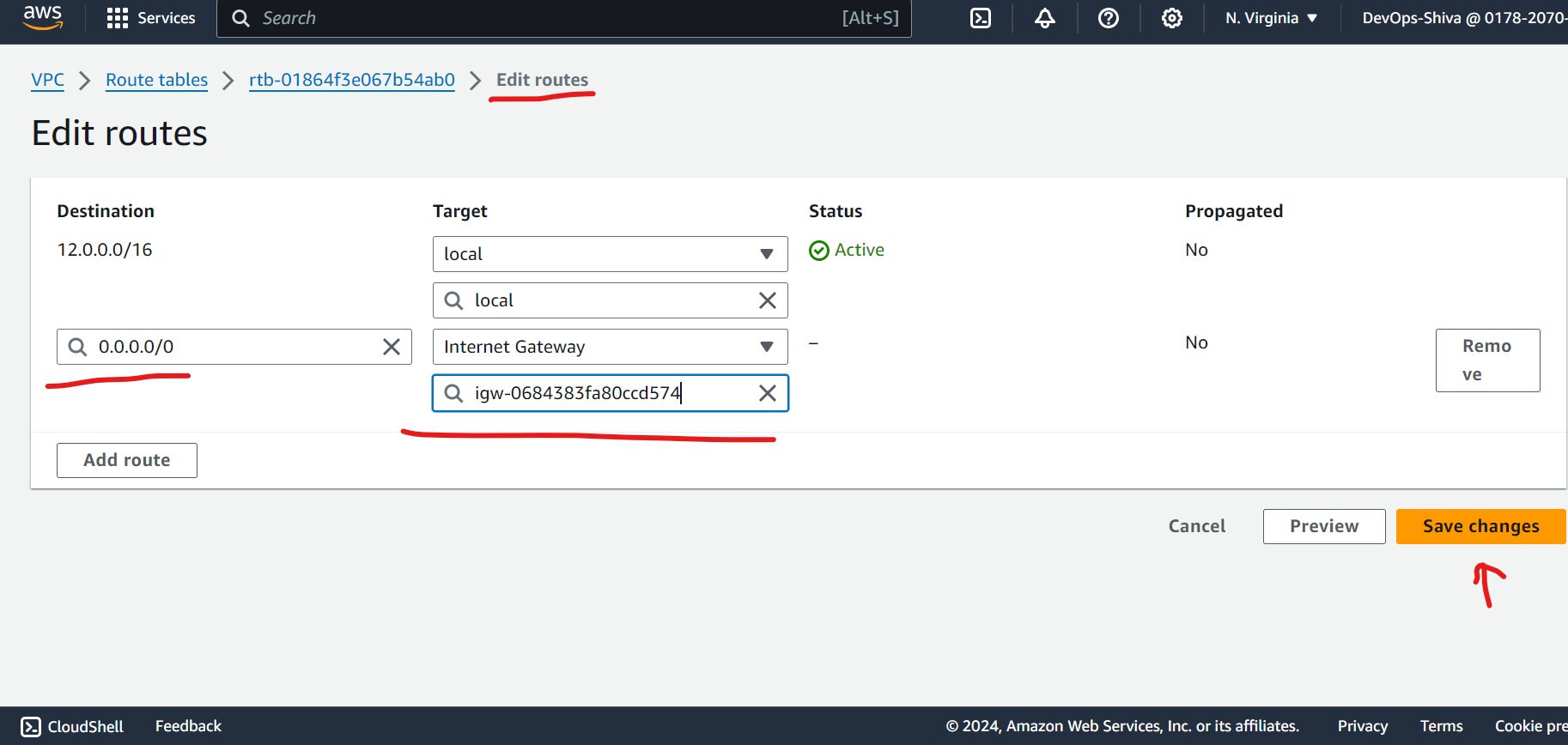
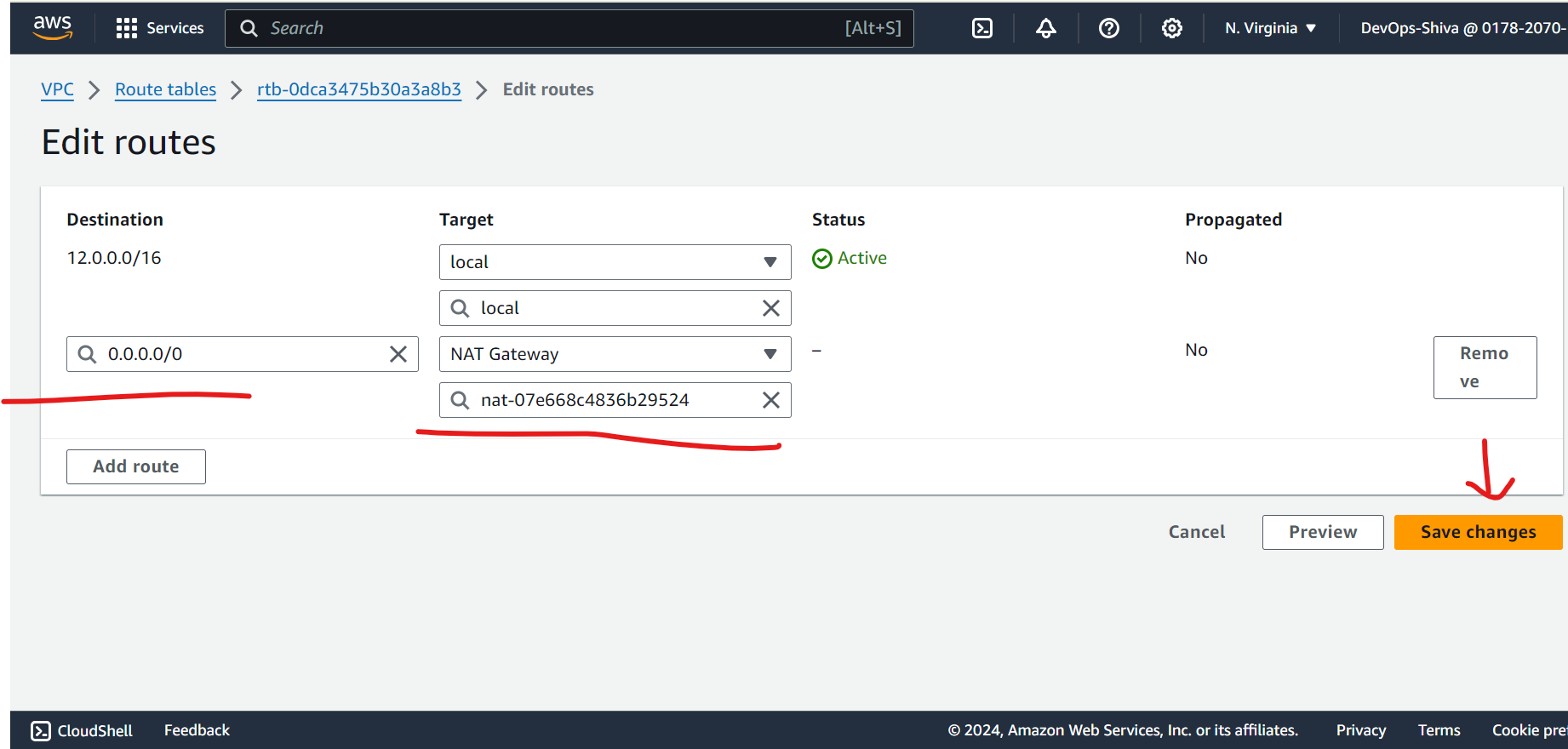
Edit routes (add igw)
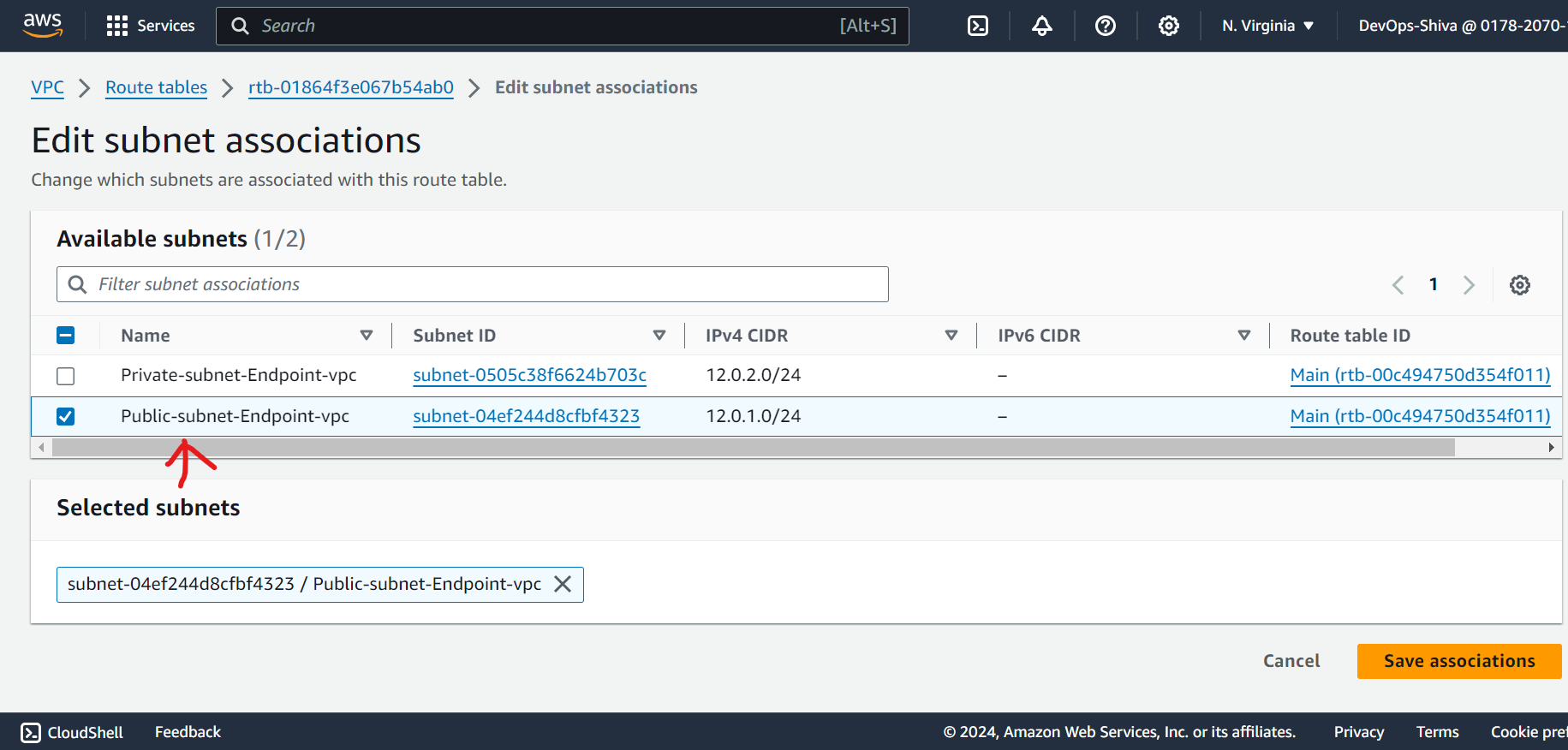
Subnet association
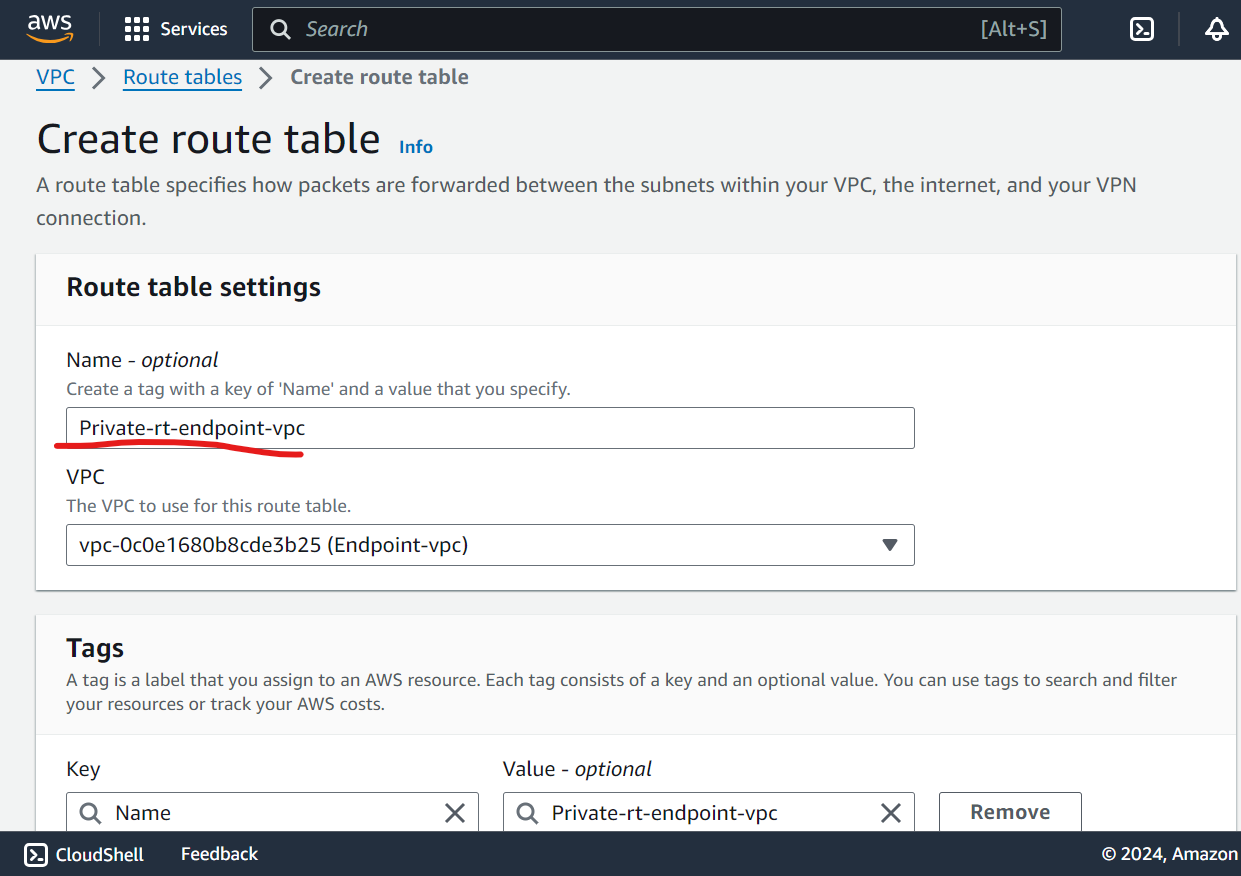
Configure route table for private subnet.
Edit routes
Subnet association

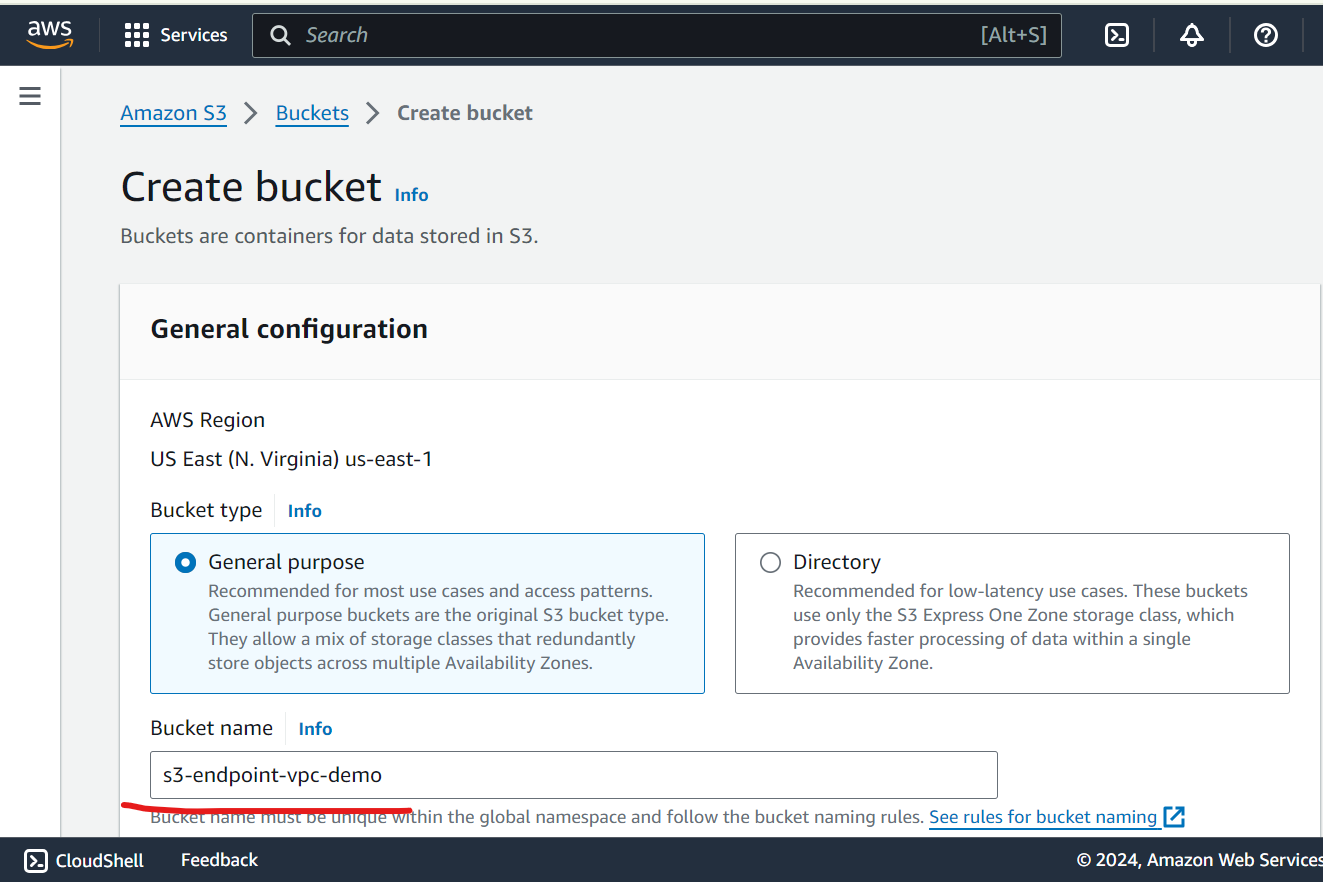
Step 2: Create an S3 Bucket
Create S3 bucket with default settings.
Step 3: Launch an EC2 Instance
Public Instance -
Choose an AMI: Ubuntu 22.04
Select Instance Type: t2.micro for demo
Key pair - Create Key pair or choose from existing
Network settings - Choose Endpoint-vpc and public subnet
Auto assign Public IP - enable
Configure Security Group:
Allow inbound SSH (port-22)
Private Instance -
Choose an AMI: Ubuntu 22.04
Select Instance Type: t2.micro for demo
Key pair - Create Key pair (use same key for demo purpose)
Network settings - Choose Endpoint-vpc and private subnet
Auto assign Public IP - disable
Configure Security Group:
- Allow inbound SSH (port-22)
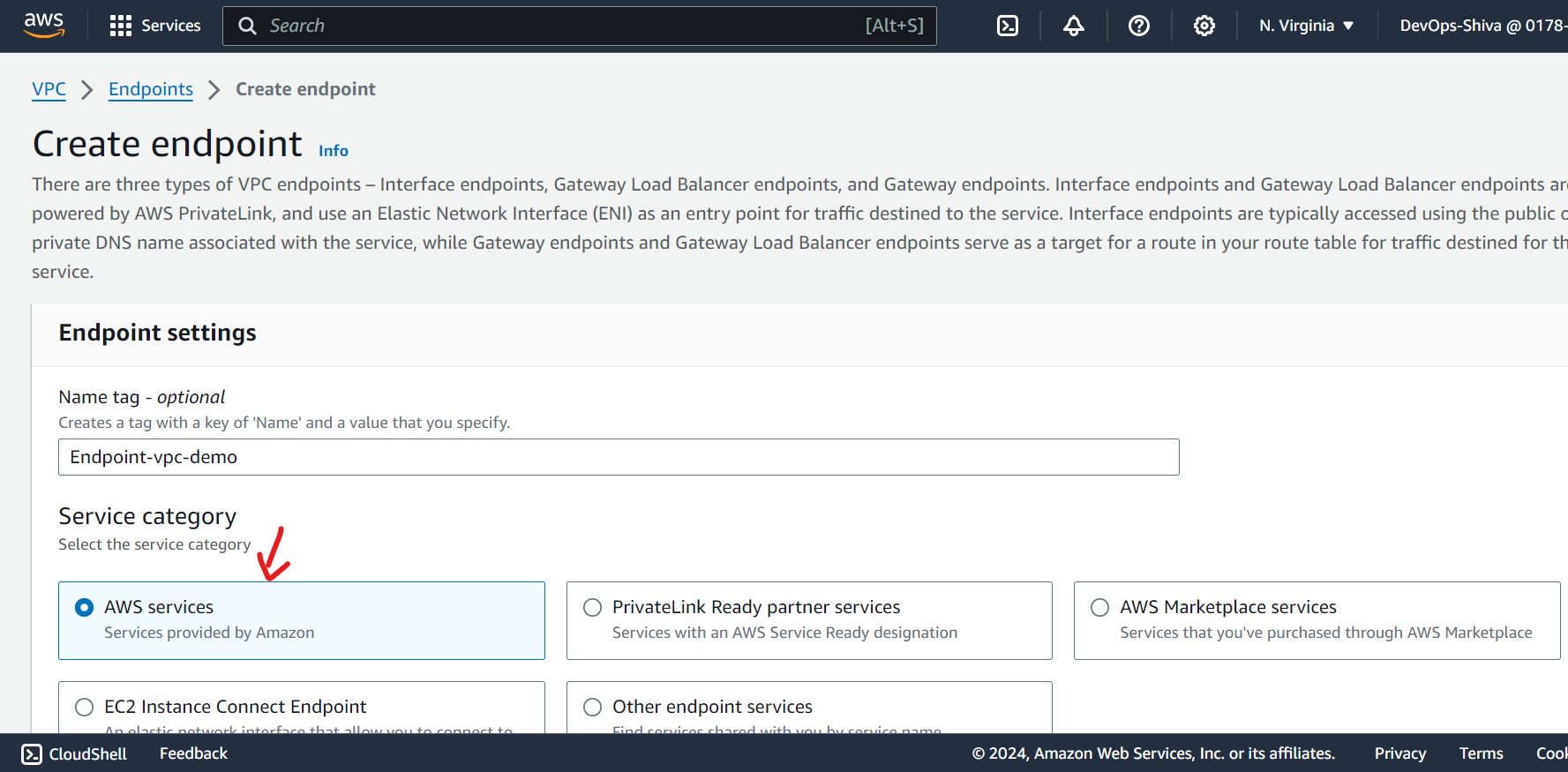
Step 4: Create VPC Endpoints
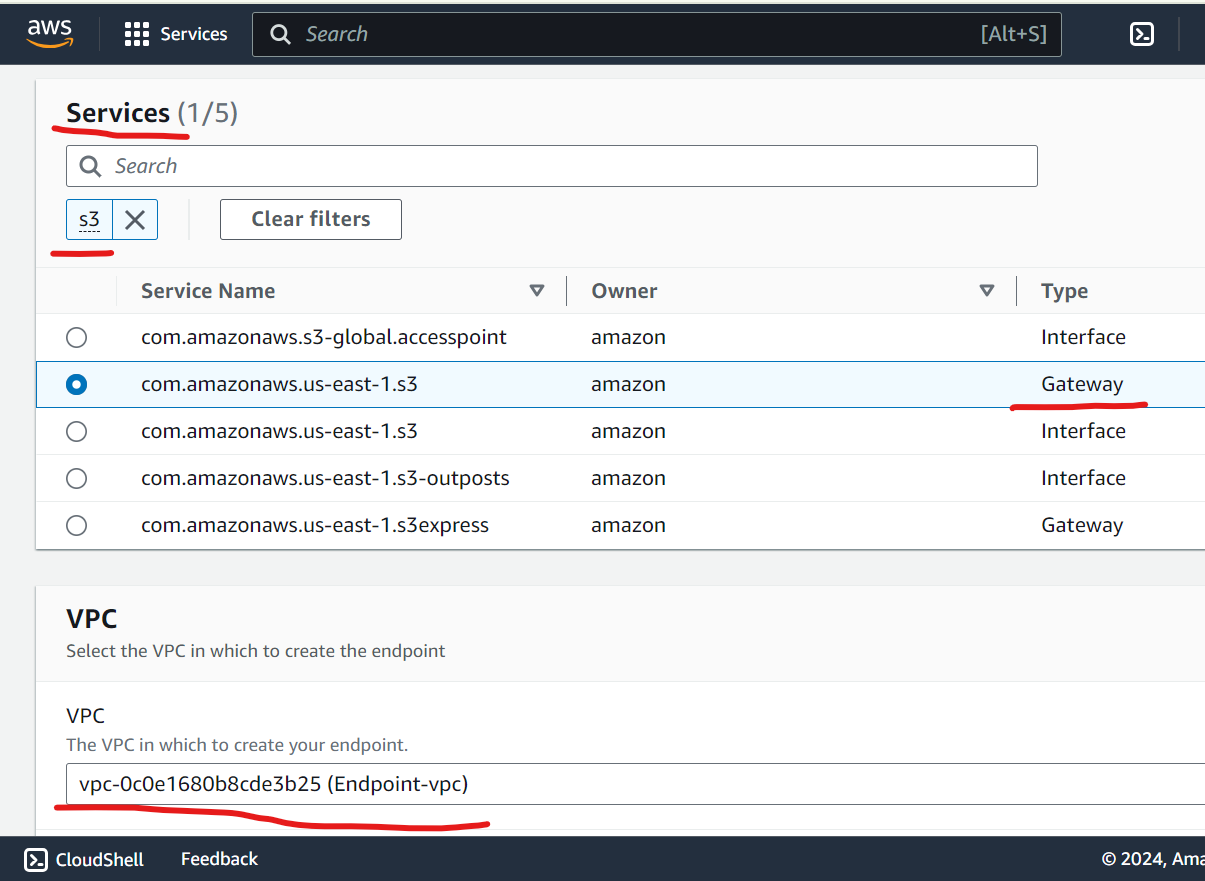
Create an S3 VPC Endpoint:
Navigate to the VPC dashboard select Endpoint.
Select the correct VPC, select public route table and choose the S3 service (gateway).
keep remaining default and heat create endpoint.
Step 5: Test the VPC Endpoint
First ssh into public instance:
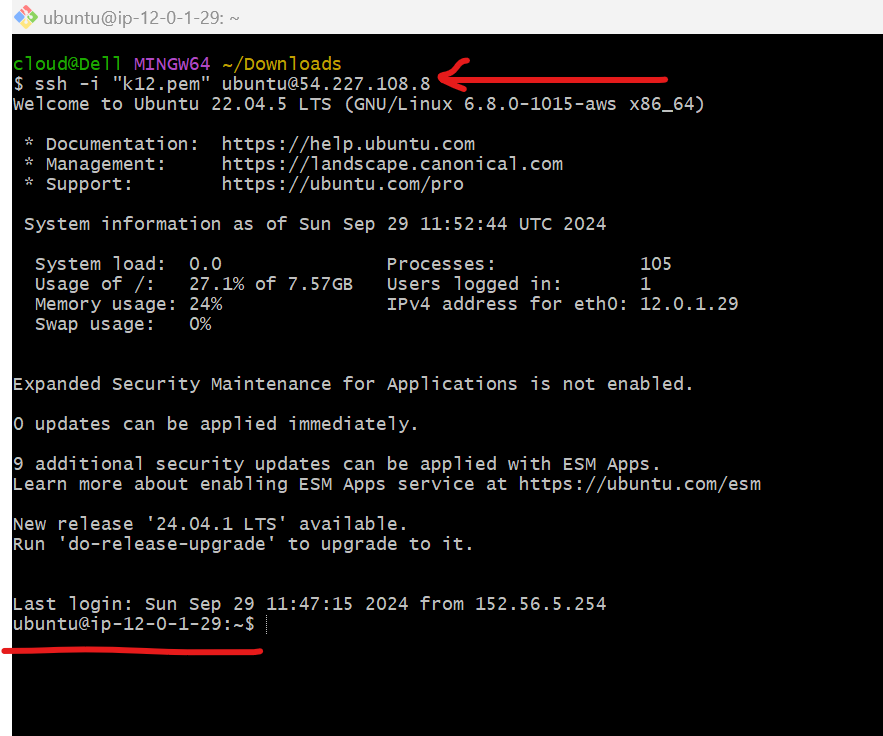
Copy key and paste it. - I have already made it So you can do
vi key_name.pemgive permission -
chmod 400"key_name.pemyou can find it on connect page.ssh to private instance
ssh -i"key_name.pem".....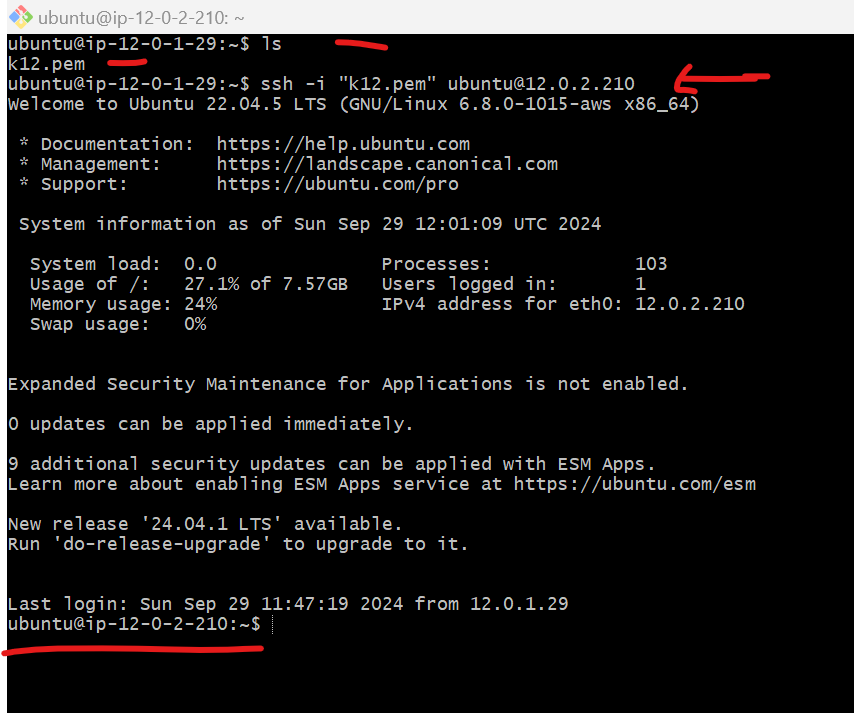
aws configure - here you will asked access key and secret access key
You can find keys from IAM console, you can create user and add admin access.
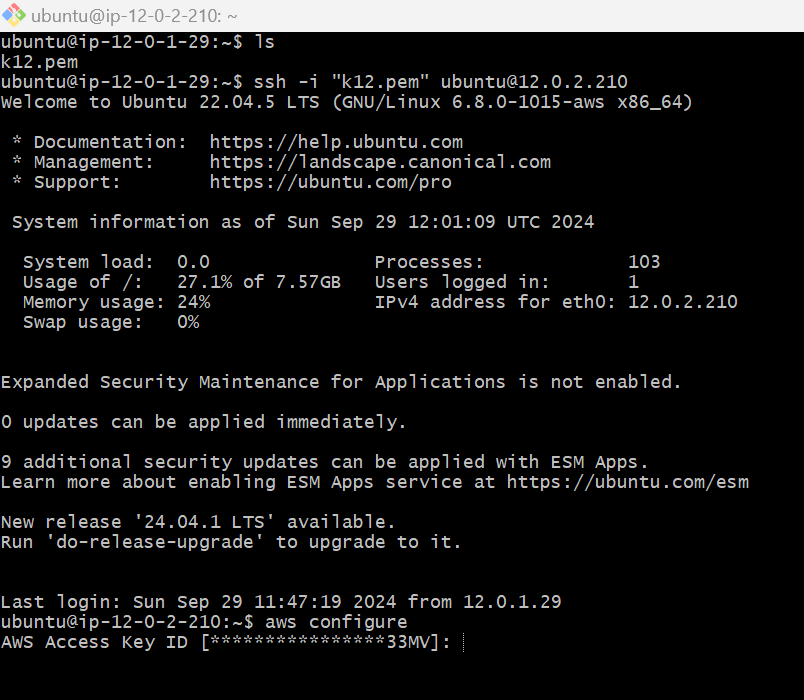
then test s3 -
aws s3 ls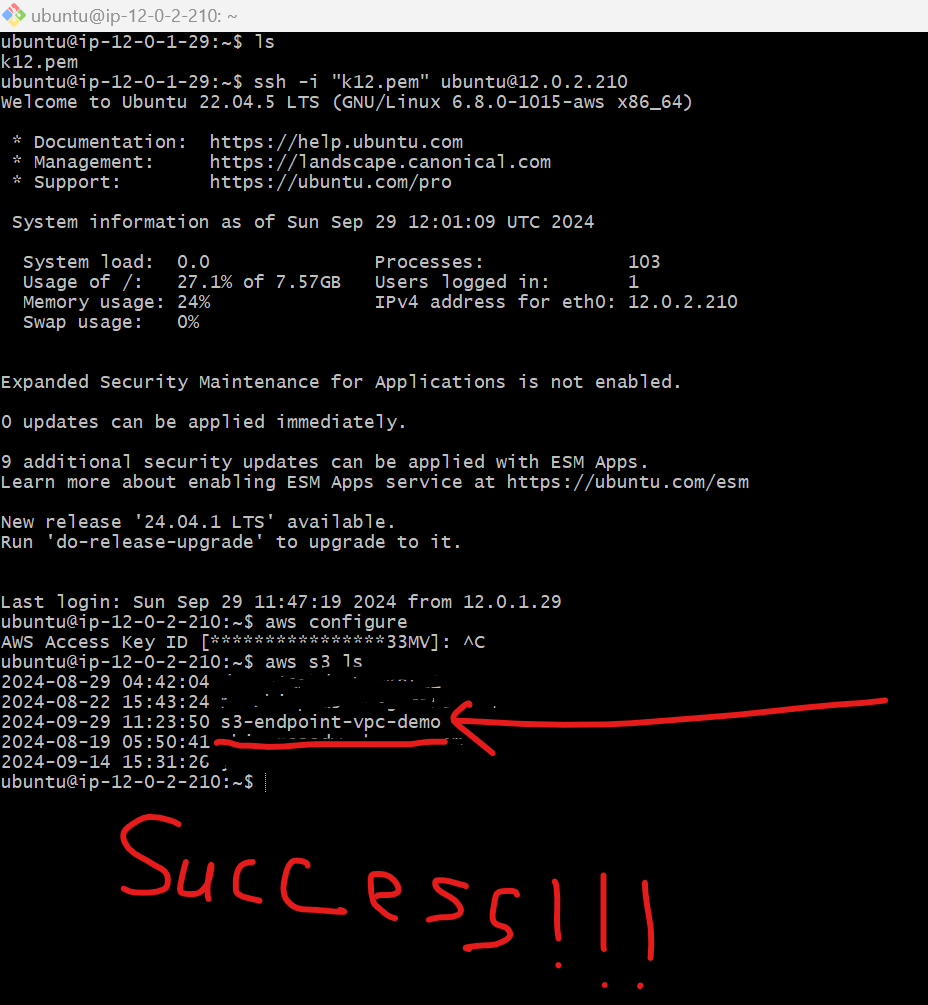
Mission Successful !!! We can able to access s3 from VPC Endpoints securely not through internet.
Cleanup
Delete EC2 instances
Delete Endpoint
Delete NAT gateway and release Elastic IP
Delete VPC’s
You might charge couple of cents !!
Note -
In production scenario :- You will need NAT gateway to install awscli in private instance only, later delete it. Otherwise if you ssh from private instance to public instance and then “test s3 ls” you can able to see s3 buckets as well.
Why Can a Private Instance Access S3 via a VPC Endpoint or NAT Gateway?
VPC Endpoint: AWS allows services like S3 to be accessed internally via VPC Endpoints, which provide a secure and fast connection within AWS’s infrastructure. Since the traffic does not leave the AWS network, it's safer and more efficient than routing through the public internet.
NAT Gateway: The NAT Gateway allows instances without public IPs to reach the internet. Since S3 is a public AWS service, traffic from the private subnet can reach it via the NAT Gateway by sending requests through the internet.
Key TakeAways:
VPC Endpoints let you access S3 securely from private subnets.
No internet needed, so it’s safer and cheaper.
Easy to set up and use within your VPC.
Subscribe to my newsletter
Read articles from Shivprasad Waghmare directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shivprasad Waghmare
Shivprasad Waghmare
"Accidental AWS/DevOps Engineer | AWS Community Builder | 7+ Years of Experience | Exploring AWS, Kubernetes, Terraform, Docker, Jenkins | Passionate about automating cloud infrastructure | Let’s explore the world of DevOps together!"