Understanding SELinux: A Guide to Configuration and Setup
 Aditya Gadhave
Aditya Gadhave
What is SELinux?
SELinux is a special security system built into Linux computers.
It helps keep your computer safe and secure.
With SELinux, different programs and users on the computer have limited permissions.
This means each program or user can only access certain files and do certain actions that they are allowed to do.
For example, The web browser can connect to the internet but it cannot read your private documents.
This prevents viruses and hackers from gaining full control over your system if they get into one program.
SELinux sets rules about what different programs and users are permit
SELinux Modes
SELinux operates in three main modes that control how security policies are enforced:
Enforcing: SELinux enforces its security policy, denying any access that is not explicitly allowed. This is the default mode on most distributions with SELinux enabled.
Permissive: SELinux logs policy violations but does not actually block access. This mode is useful for troubleshooting, testing, and developing new policies.
Disabled: SELinux is completely turned off, and no policies are enforced or logged.
To check the current mode:
getenforce
To change the mode:
sudo setenforce Enforcing # or Permissive
SELinux Contexts
SELinux assigns a security context to every process and file.
This context is a label that contains the security attributes used to make access control decisions.
A typical SELinux context is made up of four parts:
User – SELinux user (e.g., unconfined_u, system_u) that is used by the policy.The Linux user mapped to a SELinux user
Role – Defines what the user can do. Common roles include object_r for files and system_r for system processes.The user’s authorized role for that system
Type – The most important part of the context; defines the domain/type a process or object belongs to (e.g., httpd_sys_content_t for web server files).This determines the permissions that are enforced
Level (optional) – Used for Multi-Level Security (MLS) and Multi-Category Security (MCS) environments.A security clearance level
Example of a file's context:
ls -Z /var/www/html/index.html
Output:
unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/index.html
SELinux Policies
An SELinux policy defines the rules governing which subjects (users or processes) can access which objects (files, sockets, etc.) and under what conditions. There are two main types of policies:
Targeted Policy: The most commonly used policy type in modern distributions. It protects only specific system processes, leaving the rest of the system in an unconfined state. For example, targeted services like httpd, sshd, and mysqld are confined by SELinux, while other user processes run without restrictions.
MLS (Multi-Level Security) Policy: Provides strict security for highly sensitive environments (e.g., military systems). It uses a more granular access control model, including different security levels and categories.
To view the loaded policy, you can use:
sudo semanage policyversion
SELinux Booleans
SELinux booleans are toggle-able settings that allow administrators to modify specific parts of the security policy without rebuilding or reloading it entirely. Booleans make it easy to enable or disable certain features or behaviors.
Example: To list all SELinux booleans:
sudo getsebool -a
To change a boolean (e.g., allowing Apache to connect to the database):
sudo setsebool httpd_can_network_connect_db on
Types of Access Control in SELinux
Type Enforcement (TE): The most common form of access control in SELinux, where each process and object is assigned a type, and policies specify which types can access others. For example, the web server process (httpd_t) can access files of type httpd_sys_content_t.
Role-Based Access Control (RBAC): SELinux uses roles to define what types of operations can be performed by different users. Roles are used to group users into different categories based on the tasks they perform.
Multi-Level Security (MLS): MLS allows strict control of access to files based on their sensitivity level (e.g., Top Secret, Secret, etc.). This is typically used in environments that require strict compartmentalization of information, like government or military systems.
Common SELinux Commands
Check SELinux status:
sestatusChange SELinux mode (temporary):
sudo setenforce 0 # Permissive mode sudo setenforce 1 # Enforcing modeView file context:
ls -Z /path/to/fileRestore default file context:
sudo restorecon -v /path/to/file
How to Enable or Disable SELinux in Different Modes?
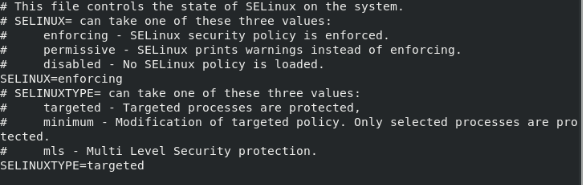
SELinux stands for Security-Enhanced Linux. SELinux is just like the Windows firewall, but it is more secure and private. It manages all the access control policies. We can control the status of SELinux security by using some direct commands or by actually going to the SELinux configuration file and editing the status. SELinux can have three values, enforcing, permissive and disabled. Enforcing means SELinux security policy is enforced. Permissive means SELinux is not enforcing but will print warnings. Disabled means it is not enforcing and also not print warning.
Check the Status
When SELinux is enforcing:
# getenforce
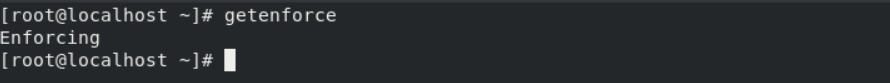
When SELinux is Permissive:
# getenforce
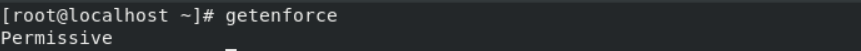
Two ways to Enable or Disable SELinux:
Through commands.
Edit SELinux config file.
Through Command:
#setenforce Enforcing
#getenforce
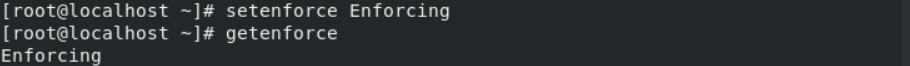
#setenforce Permissive
#getenforce
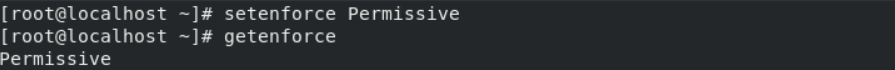
Instead of Enforcing and Permissive, you can also use 1 and 0 respectively. For example
#setenforce 0
#getenforce

Edit SELinux Configuration File:
Open SELinux configuration file in vi editor. It is located at /etc/selinux/config
#vi /etc/selinux/config
Advantages of SELinux:
Enhanced Security: Provides fine-grained access controls, preventing unauthorized users and processes from accessing sensitive files or services.
Protection from Exploits: Limits the damage that malicious software can do by confining it to specific roles and types.
Flexible Policy Management: Allows administrators to customize security policies and make quick changes using booleans.
Activity Auditing: Logs security-related events, making it easier to identify potential threats or policy violations.
Disadvantages of SELinux:
Complexity: SELinux has a steep learning curve, and configuring it for specific applications can be challenging.
Can Break Applications: Incorrect configurations or overly restrictive policies can block legitimate application behavior.
Performance Overhead: SELinux adds some overhead as it enforces security policies, though this is usually minimal on modern systems.
Difficult Troubleshooting: It can be hard to troubleshoot why certain actions are blocked, especially for beginners.
Linux vs. SELinux: What are the Differences?
1. The purpose : Linux is the operating system that manages the hardware and the software resources onto a computer. SELinux is a security part that protects the Linux from the bad software and the unauthorized access.
2. Access control enforcement : In normal Linux the users and apps can access the whole system if they have the right permissions. This is called the Discretionary Access Control (DAC). With SELinux admins set the exact permissions for each user, program, and resource. SELinux blocks any access attempts that admins do not allow through the security policies.
Conclusion:
SELinux is a powerful tool for improving Linux system security through Mandatory Access Control (MAC). By controlling access to files and processes based on predefined security policies, it can prevent unauthorized actions, even by users with root privileges. However, it can be complex to configure and manage, so it’s important to understand its key concepts and how it operates within Linux systems.
Subscribe to my newsletter
Read articles from Aditya Gadhave directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aditya Gadhave
Aditya Gadhave
👋 Hello! I'm Aditya Gadhave, an enthusiastic Computer Engineering Undergraduate Student. My passion for technology has led me on an exciting journey where I'm honing my skills and making meaningful contributions.