Enhance Security with DevSecOps Tools: StackStorm, Calico, AWS & Veracode Explained
 Deepak parashar
Deepak parashar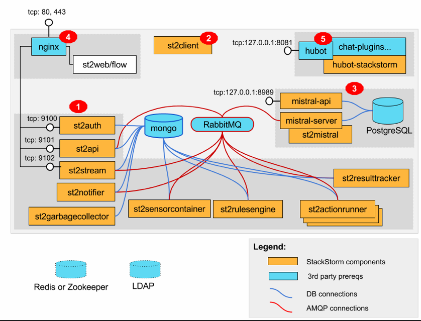
In the fast-paced world of software development, security has become one of the biggest priorities. While DevOps has revolutionized how we build and deploy applications by integrating development and operations, DevSecOps takes this further by integrating security into every stage of the software lifecycle. This approach emphasizes the need to think about security from the very beginning – from code development to deployment and monitoring in production environments.
DevSecOps relies on tools that enable seamless automation, monitoring, and enforcement of security protocols. In this guide, we’ll explore four powerful DevSecOps tools: StackStorm, Calico Open Source, AWS Security Services, and Veracode. Whether you're a software engineer, cloud architect, or DevOps enthusiast, these tools will help you incorporate security into your continuous integration/continuous deployment (CI/CD) pipelines.
Let’s dive in!
Step 1: StackStorm – Automate and Orchestrate Your Security Workflows
StackStorm is an open-source automation tool designed to help you automate security processes and workflows. It connects different systems and allows you to build automation workflows for security events, making it easier to detect and respond to threats.
1.1 Why Use StackStorm for DevSecOps?
StackStorm provides integration with many systems and services, making it an ideal tool for DevSecOps. With it, you can create security playbooks that automatically respond to suspicious activities like unauthorized access attempts or system vulnerabilities.
For example, if an anomaly is detected, StackStorm can trigger actions like notifying the security team, isolating affected resources, or even patching vulnerabilities in real time.
1.2 Setting Up StackStorm for Security Automation
To get started with StackStorm, follow these steps:
Install StackStorm on your local machine or server using the following commands for Linux systems:
bashCopy codecurl -sSL https://stackstorm.com/packages/install.sh | bash -s -- --user=st2admin --password=Ch@ngeMeCreate a security automation workflow by writing rules that define specific events and actions. These can include user authentication checks, access control validations, or incident response workflows.
Integrate with other tools: StackStorm works well with cloud services like AWS, monitoring tools like Prometheus, and security platforms like Splunk or Palo Alto firewalls.
Suggested Visual: A flowchart showing how StackStorm connects various systems and automates security event responses, with nodes representing different cloud services, security tools, and the workflows between them.
Step 2: Calico Open Source – Network Security and Microservices Protection
As microservices architecture becomes more common, securing containerized applications has never been more important. Calico Open Source is a container networking solution that provides network policy enforcement for Kubernetes clusters, offering protection to both services and workloads.
2.1 The Power of Network Policy in Kubernetes
Calico enforces network security policies that define how traffic can flow between different components in your Kubernetes cluster. For example, you can use Calico to isolate services and ensure that only authorized traffic flows between them.
2.2 Setting Up Calico for Kubernetes
Install Calico on your Kubernetes cluster by applying the necessary manifest:
bashCopy codekubectl apply -f https://docs.projectcalico.org/v3.20/manifests/calico.yamlDefine network policies that specify which services are allowed to communicate with each other. Here’s an example of a simple policy:
yamlCopy codeapiVersion: projectcalico.org/v3 kind: NetworkPolicy metadata: name: allow-frontend namespace: default spec: selector: app == "frontend" ingress: - action: Allow source: selector: app == "backend"Monitor traffic flows using Calico’s built-in monitoring tools, which can help identify any malicious activity or policy violations.
Suggested Visual: A diagram of a Kubernetes cluster, with visual representations of different services and how Calico enforces network policies between them.
Step 3: AWS Security Services – Security for Cloud-Native Applications
For cloud environments, AWS Security Services offers a suite of tools to help you safeguard your AWS resources. From identity management to threat detection and vulnerability scanning, AWS provides a robust set of features for DevSecOps.
3.1 Key AWS Security Services
AWS Identity and Access Management (IAM): Manage user permissions and roles to enforce least-privilege access. IAM ensures that users and applications have access only to the resources they need.
Amazon GuardDuty: An intelligent threat detection service that continuously monitors your AWS environment for suspicious activity. GuardDuty can alert you to malicious behavior like unauthorized access or data exfiltration attempts.
AWS WAF (Web Application Firewall): AWS WAF helps protect your web applications from common attack vectors like SQL injection and cross-site scripting (XSS) by allowing you to create custom security rules.
3.2 Implementing AWS Security Services
Create IAM policies: Use the AWS Management Console to create detailed access policies for users and roles.
Enable GuardDuty: From the AWS console, enable GuardDuty and integrate it with other AWS services like CloudTrail to gain insights into suspicious activity.
Set up AWS WAF: Define custom rules for your web applications using the AWS WAF console, protecting against common web exploits.
Suggested Visual: A tree diagram illustrating the various AWS security services, with branches representing IAM, GuardDuty, WAF, and other security offerings. Include descriptions of how each service integrates into a cloud infrastructure.
Step 4: Veracode – Application Security Testing
For organizations looking to build security into their development pipeline, Veracode provides a suite of tools for application security testing. Veracode integrates seamlessly with your CI/CD pipeline to automatically scan code for vulnerabilities.
4.1 Static Application Security Testing (SAST)
Veracode offers Static Application Security Testing (SAST), which scans your code during development to identify potential vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows. SAST provides detailed reports on security flaws and suggestions on how to fix them.
4.2 Dynamic Application Security Testing (DAST)
With Dynamic Application Security Testing (DAST), Veracode performs runtime analysis by interacting with the application in real-time. This helps identify vulnerabilities that only surface when the application is running.
4.3 Implementing Veracode in Your CI/CD Pipeline
Set up Veracode integration with your preferred CI/CD tool (e.g., GitLab, Jenkins). Here’s an example of how to integrate Veracode with Jenkins:
groovyCopy codepipeline { agent any stages { stage('Build') { steps { script { def response = veracodeApiWrapper.staticScan('app_id', 'build_id') echo response } } } } }Run automated security scans during each stage of your development pipeline. Veracode automatically sends alerts and reports to your team whenever it detects vulnerabilities.
Review vulnerability reports: Developers can use Veracode’s detailed reports to quickly address security issues in their codebase.
Suggested Visual: A graph showing how Veracode integrates into a CI/CD pipeline, with stages for code scanning, report generation, and vulnerability remediation.
Conclusion
By integrating tools like StackStorm, Calico Open Source, AWS Security Services, and Veracode into your DevSecOps strategy, you can automate security processes, enforce security policies, and proactively identify vulnerabilities. These tools help build a security-first mindset into your development workflow, ensuring that your applications are not only functional but also secure.
Whether you're automating security workflows with StackStorm, securing your microservices with Calico, managing cloud security with AWS, or scanning for vulnerabilities with Veracode, these tools are essential for modern DevSecOps practices.
Have you used any of these tools in your DevSecOps journey? What challenges have you faced while integrating security into your CI/CD pipeline? Drop a comment below – I’d love to hear your thoughts!
Subscribe to my newsletter
Read articles from Deepak parashar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
