AWS_Route53-Cert_bot Project
 Mohit Meshram
Mohit MeshramTable of contents
- # Outline for "AWS Route53-Cert_bot Project"
- **Introduction**
- Overview of the project's purpose and objectives
- Importance of automated certificate management
- Introduction to AWS Route 53 and its role in the project
- **Background**
- Common Challenges in DNS Management and SSL/TLS Certificate Deployment
- Current solutions and their limitations
- Why automation is beneficial for managing AWS infrastructure
- **Project Requirements**
- Steps to Set Up the Environment
# Outline for "AWS Route53-Cert_bot Project"
The AWS Route53-Cert_bot Project aims to solve this problem by automating the process of certificate creation, validation, and renewal using AWS services such as Route 53 for DNS management and Certbot for automated SSL/TLS certificates. The project’s primary objective is to streamline and automate certificate management, ensuring continuous availability of secure connections for your applications.
**Introduction**
In today's fast-paced digital world, security and scalability are crucial for web applications and services. One of the essential elements of online security is the implementation of SSL/TLS certificates to ensure secure data transmission. However, manually managing these certificates across multiple domains and services can be time-consuming and prone to errors.
Overview of the project's purpose and objectives
The AWS Route53-Cert_bot Project is designed to automate the management of SSL/TLS certificates for web applications and services, with a focus on using AWS Route 53 for DNS management and Certbot for certificate automation. The primary goals of the project are:
Automate SSL/TLS Certificate Provisioning and Renewal:
The project leverages Certbot to automatically request, validate, and renew certificates from Let's Encrypt. This eliminates the need for manual intervention, ensuring that certificates are always up-to-date without downtime due to expiration.Integrate AWS Route 53 for DNS Management:
By using AWS Route 53, the project automates the DNS validation process required for issuing SSL/TLS certificates. Route 53 ensures that the necessary DNS records are created, updated, and maintained seamlessly during certificate validation, making the entire process faster and error-free.Simplify Domain Management Across Multiple Services:
For applications that operate across multiple domains or subdomains, managing certificates manually becomes cumbersome. This project automates domain validation, enabling developers to manage a large number of domains with minimal effort.Ensure Secure and Continuous Availability:
The project’s automation ensures that SSL/TLS certificates are always valid, preventing any service outages or security vulnerabilities due to expired certificates. This guarantees secure, continuous availability of services for users.Improve Efficiency and Scalability:
Automating certificate and DNS management allows organizations to scale their infrastructure effortlessly. Whether hosting one website or hundreds of applications, the project ensures that certificates are automatically provisioned, validated, and renewed.
Importance of automated certificate management
SSL/TLS certificates are necessary for establishing secure communication between users and web servers. However, manually managing certificates across various domains can be a tedious task, especially when dealing with expiration and renewals. By automating certificate management with tools like Certbot, businesses can:
Eliminate the risk of expired certificates, which could lead to downtime or compromised security.
Save time by automating renewals and validations.
Ensure consistent and secure deployments, no matter the scale.
Introduction to AWS Route 53 and its role in the project
AWS Route 53 is a scalable and highly available Domain Name System (DNS) web service. It plays a critical role in this project by providing automated DNS management, which is vital for domain validation during the certificate creation process. Route 53 allows for the seamless creation and management of DNS records required for certificate validation, reducing manual intervention and improving efficiency.
**Background**
Common Challenges in DNS Management and SSL/TLS Certificate Deployment
Traditionally, managing DNS and SSL/TLS certificates comes with various challenges:
Manual DNS Record Management: Administrators must manually create and update DNS records, which is error-prone and time-consuming, especially when managing multiple domains.
Certificate Renewal: Certificates have expiration dates, and missing renewal deadlines can cause service outages and security vulnerabilities.
Domain Validation: SSL/TLS certificates require validation before being issued. This usually involves creating DNS records to prove domain ownership, which can be tedious without automation.
Current solutions and their limitations
There are several tools and services available for managing DNS and certificates, such as Let’s Encrypt and various third-party DNS management platforms. However, these solutions often require manual intervention, especially when integrating with cloud environments like AWS. Additionally, some DNS providers lack robust automation capabilities, further complicating the process.
Why automation is beneficial for managing AWS infrastructure
In a modern DevOps-driven environment, automation is critical for maintaining infrastructure at scale. Automating the DNS and SSL certificate management process in AWS brings several benefits:
Scalability: Automated certificate provisioning allows businesses to scale effortlessly across multiple domains without manual oversight.
Reliability: Automation reduces the risk of human error, ensuring that certificates are always valid and properly deployed.
Efficiency: By automating DNS record management through AWS Route 53 and certificate renewal through Certbot, companies save valuable time and resources.
The AWS Route53-Cert_bot Project leverages these automation capabilities to provide a robust solution for managing SSL/TLS certificates and DNS records, ensuring a streamlined, secure, and highly available infrastructure.
**Project Requirements**
Steps to Set Up the Environment
1. Launch an EC2 Instance with Ubuntu 20.04
Start by creating an AWS EC2 instance with the following configuration:
AMI: Ubuntu Server 20.04 LTS (ami-042e8287309f5df03)
Instance Type: t2.micro (or higher if necessary)
Security Group: Open port 80 (HTTP) and 443 (HTTPS) to allow web traffic.
After launching the instance, connect to it via SSH.
2. Install and Configure Nginx
Update the package list and install Nginx:
sudo apt update && sudo apt install -y nginx
3. Install Certbot and Certbot Nginx Plugin
Certbot is the client for Let's Encrypt, and it automates the issuance of SSL/TLS certificates. Install Certbot along with the Nginx plugin:
sudo apt update && sudo apt install certbot python3-certbot-nginx
4. Create Website Files and Set Proper Permissions
Step 1: Create the Website Directory
You’ll need to create the necessary directories for your domain and assign proper permissions:
sudo mkdir -p /var/www/mohitmeshram.shop/html
sudo chown -R $USER:$USER /var/www/mohitmeshram.shop/html
sudo chmod -R 755 /var/www/mohitmeshram.shop
Step 2: Create the Website's HTML File
Next, create an index.html file for the website:
sudo vim /var/www/mohitmeshram.shop/html/index.html
Copy the following HTML into the file:
<html>
<head>
<title>Welcome to mohitmeshram.shop!</title>
</head>
<body>
<h1>Success! The mohitmeshram.shop server block is working!</h1>
</body>
</html>
5. Configure Nginx for the Website
Step 1: Create the Nginx Site Availability File
Create a new Nginx configuration file for your domain:
sudo vim /etc/nginx/sites-available/mohitmeshram.shop
Paste the following configuration:
server {
listen 80;
listen [::]:80;
root /var/www/mohitmeshram.shop/html;
index index.html index.htm index.nginx-debian.html;
server_name mohitmeshram.shop www.mohitmeshram.shop;
location / {
try_files $uri $uri/ =404;
}
}
Step 2: Enable the Site
Create a symbolic link to enable the site:
sudo ln -s /etc/nginx/sites-available/mohitmeshram.shop /etc/nginx/sites-enabled/
Step 3: Test and Restart Nginx
Test the configuration for syntax errors:
sudo nginx -t
Restart Nginx to apply the changes:
sudo systemctl restart nginx
6. Install Certbot for SSL/TLS Certificate Automation
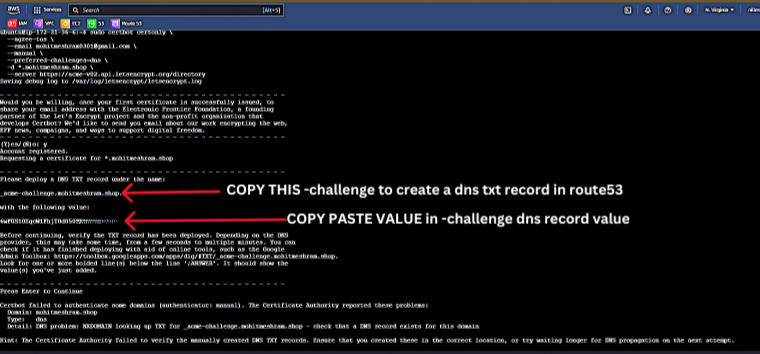
To request an SSL/TLS certificate for your domain, run the following Certbot command. This will initiate the process to obtain a wildcard certificate, using DNS validation:
sudo certbot certonly \
--agree-tos \
--email mohitmeshram0301@gmail.com \
--manual \
--preferred-challenges=dns \
-d *.mohitmeshram.shop \
--server https://acme-v02.api.letsencrypt.org/directory
During the process, Certbot will prompt you to create a DNS TXT record
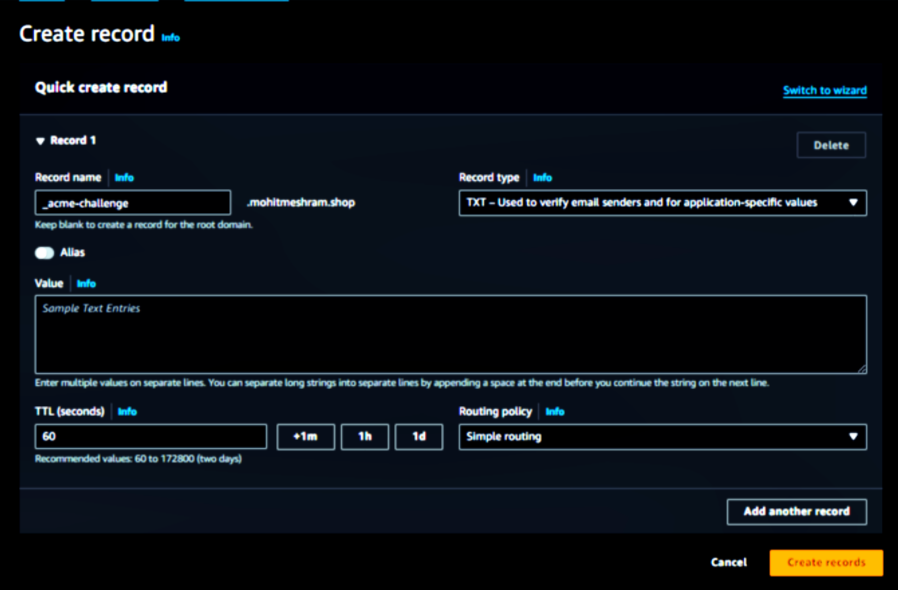
copy the DNS TXT and create a new record in AWS Route 53 to verify domain ownership.
Create a new record as a record name _acme-challenge and record type TXT
Paste the value Appears in the terminal in VALUE BOX of record
After creating the record, Certbot will automatically obtain the certificate.
Subscribe to my newsletter
Read articles from Mohit Meshram directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
