Day 6 Task: File Permissions and Access Control Lists
 Faizan Shaikh
Faizan Shaikh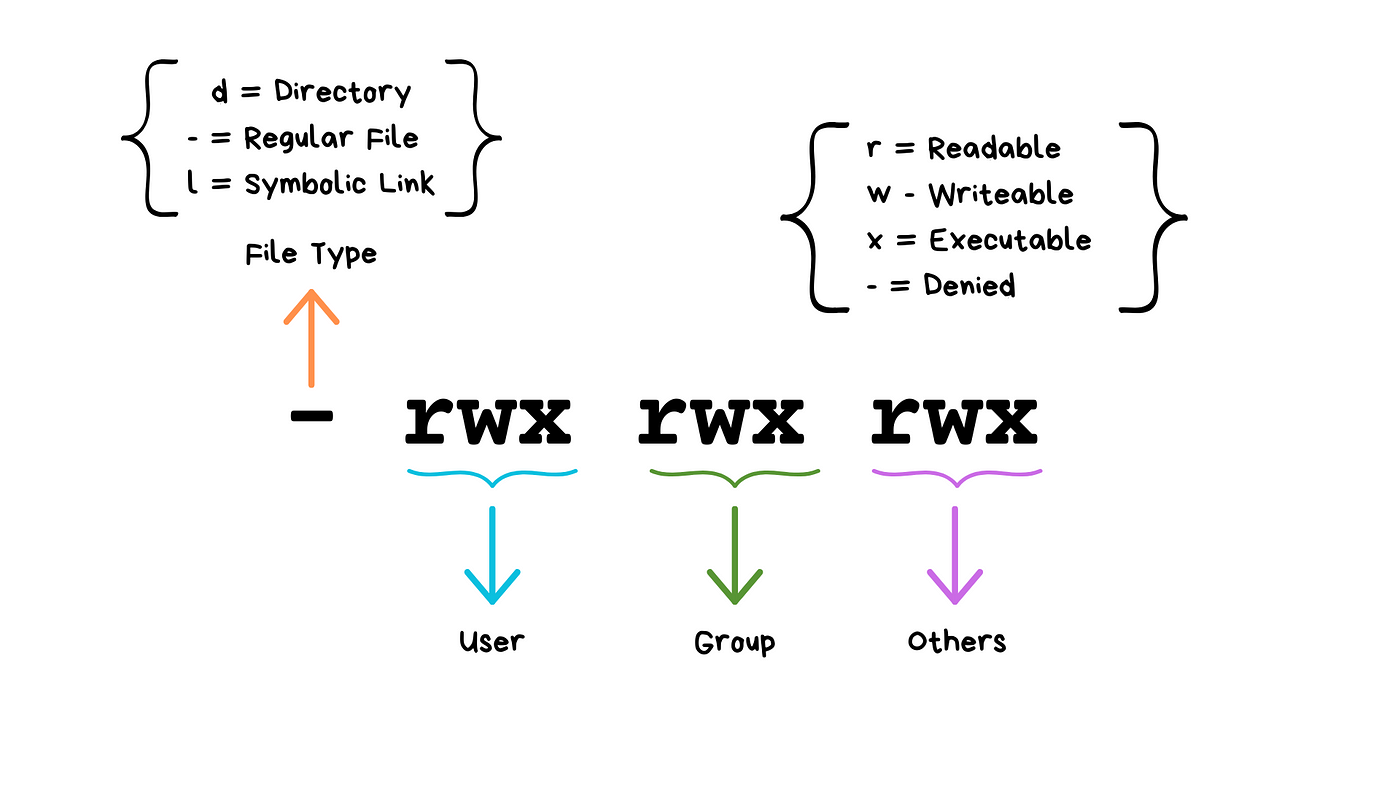
The concept of Linux file permission and ownership is important in Linux. Today, we will work on Linux permissions and ownership, and perform tasks related to both.
Task 1 : Understanding File Permissions
Create a simple file and run ls -ltr to see the details of the files.
Each of the three permissions are assigned to three defined categories of users. The categories are:
Owner: The owner of the file or application. Use chown to change the ownership permission of a file or directory.
Group: The group that owns the file or application. Use chgrp to change the group permission of a file or directory.
Others: All users with access to the system (outside the users in a group). Use chmod to change the other users' permissions of a file or directory.
Task: Change the user permissions of the file and note the changes after running ls -ltr.
Solution:
To understand file permissions in Linux, let's break down the steps for creating a file, viewing its permissions using ls -ltr, and modifying the permissions using chown, chgrp, and chmod.
- Create a Simple File: You can create a file using the touch command:
touch example.txt
This will create an empty file named example.txt.
- Check File Permissions: To view the file's details and permissions, run:
ls -ltr
Here’s an example of the output:
-rw-rw-r-- 1 ubuntu ubuntu 0 Oct 10 11:32 example.txt
Let's break this down:
-rw-r--r--are the permissions.The first
-refers to a file (can bedfor directory).rw-means the owner has read and write permissions.r--means the group has read permission.r--means others have read permission.
Change Ownership (Owner):
Use the chown command to change the ownership of the file:
sudo chown new_owner example.txt
Replace new_owner with the desired username. You can verify the change by running ls -ltr again. The owner of the file will now be the new user.
Change Group (Group):
To change the group ownership, use chgrp:
sudo chgrp new_group example.txt
Replace new_group with the desired group name. Run ls -ltr to check the new group assignment.
Change Permissions (Others)
Use the chmod command to change permissions for others.
For example, to remove read permissions for others:
chmod o-r example.txt
This removes read permission for "others." Run ls -ltr again to see the changes. The permission part should now look like:
-rw-r-----
Task Example: Change Permissions and Note Changes
Create a file:
touch sample.txtView initial permissions:
ls -ltrLet's assume the output is:
-rw-r--r-- 1 user group 0 Oct 10 10:30 sample.txtThis means:
The owner (
user) has read (r) and write (w) permissions.The group has only read permission.
Others also have read permission.
Change owner:
sudo chown newuser sample.txtRun
ls -ltrto verify:-rw-r--r-- 1 newuser group 0 Oct 10 10:30 sample.txtChange group:
sudo chgrp newgroup sample.txtRun
ls -ltrto verify:-rw-r--r-- 1 newuser newgroup 0 Oct 10 10:30 sample.txtChange permissions for others:
chmod o-wr sample.txtRun
ls -ltrto verify:-rw-r----- 1 newuser newgroup 0 Oct 10 10:30 sample.txtNow, others have no permission (
---).
Conclusion
By using chown, chgrp, and chmod, you can modify the file ownership and permissions. The ls -ltr command helps you verify these changes and understand the current permissions.
Task 2 : Writing an Article:
Write an article about file permissions based on your understanding from the notes.
Understanding File Permissions in Linux: A Comprehensive Guide
File permissions are a fundamental aspect of the Linux operating system that ensure security, proper access control, and system integrity. They define what actions users can perform on files and directories, allowing administrators to manage access for different users and groups. In this article, we’ll dive deep into file permissions, how they are structured, and how they can be modified using commands like chown, chgrp, and chmod.
What Are File Permissions?
In Linux, every file and directory has permissions that specify who can read, write, or execute the file. These permissions are crucial for controlling access, preventing unauthorized changes, and ensuring that sensitive files are protected from being altered or viewed by others.
Each file or directory is associated with three types of users:
Owner: The user who owns the file.
Group: A set of users that can share the same access rights.
Others: All other users on the system who are neither the owner nor part of the file's group.
The permissions system is split into three categories of actions that can be performed:
Read (r): Permission to view the contents of the file or list the contents of a directory.
Write (w): Permission to modify or delete the file or directory.
Execute (x): Permission to run a file as a program or to navigate into a directory.
Understanding Permission Structure
Permissions are usually represented in a string of 10 characters, as shown in the following example:
-rw-r--r--
Here’s how to interpret this:
The first character: Indicates the file type. A dash
-represents a regular file, while adindicates a directory.The next three characters (
rw-): Represent the owner’s permissions (read, write, no execute).The following three characters (
r--): Represent the group’s permissions (read-only).The last three characters (
r--): Represent the permissions for others (read-only).
In this example, the file is readable and writable by the owner, readable by the group, and readable by others.
Viewing File Permissions
You can view file permissions by using the ls -ltr command:
ls -ltr
The output will display the permissions, owner, group, and other details such as the file size and modification date.
Changing File Permissions
Linux provides several commands to modify file permissions and ownership. Let’s explore how to use these commands effectively.
1. Changing Ownership with chown
The chown command changes the ownership of a file or directory. By default, the owner of a file is the user who created it, but ownership can be transferred to another user if necessary.
sudo chown new_owner filename
For example:
sudo chown alice example.txt
This changes the owner of example.txt to the user alice. After running ls -ltr, the new owner will be reflected in the file details.
2. Changing Group Ownership with chgrp
The chgrp command is used to change the group ownership of a file or directory. By default, a file is assigned to the primary group of the user who created it.
sudo chgrp new_group filename
For instance:
sudo chgrp developers example.txt
This assigns the file example.txt to the group developers. When you check the file’s details, you’ll see that the group has changed.
3. Modifying Permissions with chmod
The chmod command changes the permissions for the owner, group, or others. Permissions can be modified in several ways, including adding or removing specific permissions (read, write, execute).
To remove read and write permissions for "others," for example, you can use:
chmod o-rw example.txt
This removes both read and write permissions for anyone outside the file's owner and group.
You can also use numeric values to set permissions. Each permission (read, write, execute) is assigned a number:
Read = 4
Write = 2
Execute = 1
To assign permissions, you add these numbers together. For example, chmod 755 would result in the following permissions:
Owner: Read (4) + Write (2) + Execute (1) = 7
Group: Read (4) + Execute (1) = 5
Others: Read (4) + Execute (1) = 5
Thus, 755 would give the owner full control (read, write, execute), and the group and others read and execute access only.
Practical Example
Here’s a step-by-step practical example that walks through modifying file permissions:
Create a File:
touch sample.txtThis creates a file named
sample.txt.View Current Permissions: Run the following command to see the file’s current permissions:
ls -ltr sample.txtOutput:
-rw-r--r-- 1 user group 0 Oct 10 10:30 sample.txtThis shows that the file owner has read and write permissions, while the group and others have read-only access.
Change Ownership: To change the ownership to another user (
alice):sudo chown alice sample.txtChange Group: To assign the file to the
developersgroup:sudo chgrp developers sample.txtModify Permissions: To remove read permissions for others:
chmod o-r sample.txtVerify Changes: After making changes, run
ls -ltragain:-rw-r----- 1 alice developers 0 Oct 10 10:30 sample.txtNow, only the owner has read and write permissions, the group has read access, and others have no access.
Conclusion
Managing file permissions is crucial for maintaining security in any Linux environment. The commands chown, chgrp, and chmod allow you to control who can access or modify files and directories. By understanding the structure of file permissions and knowing how to modify them, you can protect sensitive data and ensure that only authorized users have the necessary access.
Mastering file permissions is an essential skill for system administrators, developers, and anyone working in a Linux environment. It ensures that files are shared safely and securely, protecting your system from unauthorized access.
Task 3 : Access Control Lists (ACL):
Read about ACL and try out the commands
getfaclandsetfacl.Task: Create a directory and set specific ACL permissions for different users and groups. Verify the permissions using
getfacl.
Access Control Lists (ACL) in Linux
What is ACL?
Access Control Lists (ACL) provide more fine-grained permissions for files and directories than the traditional file permissions in Linux. While regular permissions control access for the file owner, group, and others, ACL allows you to specify permissions for individual users or groups in addition to the standard set.
ACLs are particularly useful when you need to grant different levels of access to multiple users or groups without changing the file’s ownership or group.
Key ACL Commands
getfacl: Displays the ACL of a file or directory.setfacl: Used to set or modify the ACL of a file or directory.
Step-by-Step Guide: Using ACL
1. Enable ACL Support
Most Linux systems have ACL enabled by default. If it’s not enabled, you might need to mount the file system with ACL support. You can check ACL support with:
mount | grep acl
2. Create a Directory
Start by creating a directory where you’ll apply ACL permissions:
mkdir acl_example
3. Set ACL for Specific Users or Groups
Use the setfacl command to assign specific permissions to individual users or groups.
Syntax:
setfacl -m u:username:permission directory_or_file
u:username: Specifies the user.permission: Permissions (r, w, x).
Example: Give user alice read and write access to acl_example:
setfacl -m u:alice:rw acl_example
Similarly, you can set permissions for a group:
setfacl -m g:developers:rx acl_example
4. Verify ACL Permissions with getfacl
To view the ACLs set on the directory or file, use the getfacl command:
getfacl acl_example
The output will look something like this:
# file: acl_example
# owner: user
# group: group
user::rwx
user:alice:rw-
group::r-x
group:developers:r-x
mask::rwx
other::r-x
This shows the standard file permissions along with the additional ACL entries for alice and the developers group.
5. Remove ACL Entries
To remove an ACL entry, use the setfacl command with the -x option:
setfacl -x u:alice acl_example
You can also remove all ACL entries using:
setfacl -b acl_example
Task: Setting and Verifying ACL Permissions
1. Create a Directory
mkdir project_dir
2. Assign ACL to Different Users
Assign read, write, and execute permissions to user john:
setfacl -m u:john:rwx project_dir
Assign read and execute permissions to group team:
setfacl -m g:team:rx project_dir
3. Verify Permissions Using getfacl
Run the following to check the ACL permissions on project_dir:
getfacl project_dir
Sample output:
# file: project_dir
# owner: user
# group: group
user::rwx
user:john:rwx
group::r-x
group:team:r-x
mask::rwx
other::r-x
Conclusion
Access Control Lists (ACL) allow you to set detailed permissions beyond the traditional owner-group-other model. With commands like getfacl and setfacl, you can easily manage and verify file and directory access for different users and groups, providing flexibility in managing permissions in a multi-user environment.
Task 4 : Additional Tasks:
Task A: Script to Change Permissions of Multiple Files in a Directory Based on User Input
This script will prompt the user to input the directory name and the permissions they want to set. It will then apply the specified permissions to all files in that directory.
#!/bin/bash # Function to change permissions of files in a directory change_permissions() { echo "Enter the directory name:" read dir # Check if directory exists if [ ! -d "$dir" ]; then echo "Directory does not exist!" exit 1 fi echo "Enter the permission (e.g., 755 for rwxr-xr-x):" read permission # Change permissions of all files in the directory for file in "$dir"/*; do if [ -f "$file" ]; then # Check if it's a file (not a directory) chmod "$permission" "$file" echo "Changed permissions of $file to $permission" fi done } # Run the function change_permissionsHow it works:
The script prompts for the directory and permission mode (e.g.,
755for full permissions for the owner and read/execute for others).It iterates over all files in the specified directory and applies the permissions.
It ensures only regular files (not directories) are modified.
Task b : Script to Set ACL Permissions for a User on a Given File Based on User Input
This script will allow the user to input a file, a username, and desired permissions. It will then set the specified ACL permissions for that user on the given file.
#!/bin/bash # Function to set ACL permissions for a user on a file set_acl_permission() { echo "Enter the filename:" read file # Check if file exists if [ ! -f "$file" ]; then echo "File does not exist!" exit 1 fi echo "Enter the username:" read username echo "Enter the permission for the user (e.g., rwx for full permissions):" read permission # Set ACL permission for the user setfacl -m u:"$username":"$permission" "$file" echo "Set ACL permissions for user $username to $permission on file $file" } # Run the function set_acl_permissionHow it works:
The script asks the user to provide the file name, the username, and the permissions (e.g.,
rwxfor full access).It checks if the file exists, then uses
setfaclto apply the specified ACL permissions to the user.After applying the permissions, it confirms the action.
How to Use:
Make both scripts executable:
chmod +x change_permissions.sh chmod +x set_acl_permissions.shRun the scripts as needed:
./change_permissions.sh ./set_acl_permissions.sh
These scripts automate the process of changing traditional file permissions and setting ACLs, making them user-friendly tools for managing access control in Linux.
Task 5 : Understanding Sticky Bit, SUID, and SGID:
Read about sticky bit, SUID, and SGID.
Task: Create examples demonstrating the use of sticky bit, SUID, and SGID, and explain their significance.
Understanding Sticky Bit, SUID, and SGID in Linux
In Linux, the sticky bit, SUID (Set User ID), and SGID (Set Group ID) are special permissions that offer additional control over file access and execution.
1. Sticky Bit
What is the Sticky Bit?
The sticky bit is a permission that is primarily applied to directories. It restricts the deletion of files within that directory to only the file's owner or the root user, even if others have write permissions.
Use Case:
- It's often used in shared directories, like
/tmp, to prevent users from deleting each other's files while still allowing them to create and modify their own files.
Setting the Sticky Bit:
- To set the sticky bit on a directory, use the
chmodcommand with the+toption.
Example:
Create a directory
shared_dir:mkdir shared_dirSet write permissions for all users on this directory:
chmod 777 shared_dirSet the sticky bit:
chmod +t shared_dirCheck the permissions using
ls -ld:ls -ld shared_dirOutput:
drwxrwxrwt 2 user user 4096 Oct 10 12:00 shared_dirNotice the
tat the end of the permissions (drwxrwxrwt). This indicates the sticky bit is set.
Significance:
- In a directory with the sticky bit set, even though all users can write to the directory (permissions
777), only the file owner or root can delete files. This protects users' files from being deleted by others in shared environments.
2. SUID (Set User ID)
What is SUID?
The SUID (Set User ID) permission allows users to execute a file with the permissions of the file's owner. It is mostly applied to executable files. When SUID is set, the process spawned by executing the file runs with the privileges of the file owner rather than the privileges of the user who launched it.
Use Case:
- The
passwdcommand is a classic example where SUID is used. Thepasswdprogram allows users to change their passwords, which requires modifying the/etc/shadowfile, a file that regular users normally do not have permission to modify. SUID allows the program to run with the elevated privileges of its owner (typicallyroot) to modify the file safely.
Setting SUID:
- Use
chmodwithu+sto set the SUID bit on an executable file.
Example:
Create a simple script
test_suid.sh:echo "echo 'SUID test script executed!'" > test_suid.sh chmod 755 test_suid.shSet the SUID bit:
chmod u+s test_suid.shCheck the permissions:
ls -l test_suid.shOutput:
-rwsr-xr-x 1 user user 28 Oct 10 12:05 test_suid.shNotice the
sin the owner’s execute position (rws). This indicates that SUID is set.
Significance:
- With SUID, any user executing this script will run it with the file owner's privileges, potentially allowing them access to files or actions they normally wouldn't be allowed.
3. SGID (Set Group ID)
What is SGID?
The SGID (Set Group ID) permission has two main purposes, depending on whether it is applied to files or directories.
On Files: Similar to SUID, it allows users to execute a file with the group permissions of the file’s group owner.
On Directories: SGID ensures that files created within the directory inherit the group ownership of the directory rather than the group of the user who created the file.
Use Case:
- SGID on a directory is useful in collaborative environments where you want all files in a project directory to belong to the same group, regardless of who creates them.
Setting SGID:
- Use
chmodwithg+sto set the SGID bit.
Example for Directories:
Create a directory
project_dir:mkdir project_dirChange the group ownership to a specific group, e.g.,
developers:sudo chgrp developers project_dirSet SGID on the directory:
chmod g+s project_dirCheck the permissions:
ls -ld project_dirOutput:
drwxrwsr-x 2 user developers 4096 Oct 10 12:10 project_dirThe
sin the group permissions (rws) indicates SGID is set.
Significance:
On Files: When applied to an executable, SGID allows users to run the file with the permissions of the file’s group owner.
On Directories: It ensures that any file created inside
project_dirwill automatically inherit the groupdevelopers, ensuring consistent group permissions for collaboration.
Summary Table:
| Permission | Command to Set | Usage | Example |
| Sticky Bit | chmod +t | Restricts file deletion in shared directories | Applied to /tmp and shared folders |
| SUID | chmod u+s | Executes a file with the owner's privileges | passwd command to change passwords |
| SGID | chmod g+s | Executes a file with group privileges or ensures files inherit directory's group | Applied to project directories for collaborative environments |
These special permissions add flexibility and control to how files and directories are accessed and modified, particularly in multi-user systems where collaboration and security are important.
Task 5 : Backup and Restore Permissions:
Task A : Script to Backup Permissions of Files in a Directory
This script will save the current permissions of all files in a specified directory to a backup file.
#!/bin/bash
# Script to backup file permissions
backup_permissions() {
echo "Enter the directory you want to backup permissions for:"
read dir
# Check if directory exists
if [ ! -d "$dir" ]; then
echo "Directory does not exist!"
exit 1
fi
echo "Enter the name of the backup file:"
read backup_file
# Backup permissions using stat command
> "$backup_file" # Clear the backup file if it exists
for file in "$dir"/*; do
if [ -f "$file" ]; then
permissions=$(stat -c "%a %n" "$file") # Get permissions and file name
echo "$permissions" >> "$backup_file" # Write to backup file
fi
done
echo "Permissions backed up to $backup_file"
}
# Run the backup function
backup_permissions
How It Works:
The script prompts for a directory and the name of a backup file.
It uses the
statcommand to get the numeric permissions (like755) and file names.It stores this information in the specified backup file, clearing the file first if it already exists.
Task b : Script to Restore Permissions from a Backup File
This script will read the backup file and restore the saved permissions to the respective files.
#!/bin/bash
# Script to restore file permissions from a backup file
restore_permissions() {
echo "Enter the name of the backup file:"
read backup_file
# Check if the backup file exists
if [ ! -f "$backup_file" ]; then
echo "Backup file does not exist!"
exit 1
fi
# Restore permissions from the backup file
while read line; do
permission=$(echo "$line" | cut -d ' ' -f 1) # Extract permission
file=$(echo "$line" | cut -d ' ' -f 2) # Extract file name
# Check if the file exists before restoring permissions
if [ -f "$file" ]; then
chmod "$permission" "$file" # Restore permission
echo "Restored $file to $permission"
else
echo "File $file not found, skipping."
fi
done < "$backup_file"
echo "Permissions restored from $backup_file"
}
# Run the restore function
restore_permissions
How It Works:
The script prompts for the name of the backup file.
It reads each line in the backup file, extracting the permission and the corresponding file name.
It applies the saved permissions to the files using
chmod, checking if each file exists before doing so.
How to Use:
Make the scripts executable:
chmod +x backup_permissions.sh chmod +x restore_permissions.shRun the backup script:
./backup_permissions.shFollow the prompts to specify the directory and the backup file name.
Run the restore script:
./restore_permissions.shFollow the prompts to specify the backup file.
Example Workflow:
Backup the permissions:
./backup_permissions.sh # Enter the directory: ./mydir # Enter the name of the backup file: permissions_backup.txtRestore the permissions:
./restore_permissions.sh # Enter the name of the backup file: permissions_backup.txt
This ensures that you can back up and restore file permissions easily, preserving your system’s security and file access settings during maintenance or migration tasks.
Subscribe to my newsletter
Read articles from Faizan Shaikh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
