A new aspect to security: Homomorphic Encryption
 Dhwanil Shah
Dhwanil Shah
The Conventional Encryption Techniques
The primary objective of standard contemporary encryption techniques is to safeguard the privacy of data, whether it is stored or being transmitted. Effective encryption should guarantee that even if someone gains unauthorized access to the encrypted data, they will be unable to comprehend or make sense of it. But this method of standard encryption doesn't allow any computation to be performed on the encrypted data.
The Need Of New Techniques of Encryption
There are many situations where the data has to be secret and certain computations are required to get meaningful insights from data for example Financial transactions, account details, and other sensitive financial data must be protected to prevent fraud and unauthorized access. At the same time, banks and financial institutions need to perform various computations on this data, such as fraud detection, credit risk analysis, and personalized financial recommendations.
What is Homomorphic Encryption ?
Homomorphic encryption is a form of encryption that allows computations to be performed on encrypted data without first having to decrypt it. The resulting computations are left in an encrypted form which, when decrypted, result in an output that is identical to that produced had the operations been performed on the unencrypted data.
Homomorphic encryption is revolutionary because it allows users to utilize services that analyze their data without exposing their personal information. For instance, if someone wants to use a service that identifies genetic disease risk factors based on their genome, they wouldn't have to share their DNA and medical history with a third party. Instead, homomorphic encryption could ensure that the service can process the data without ever seeing the actual genetic sequence, maintaining the user's privacy and security.
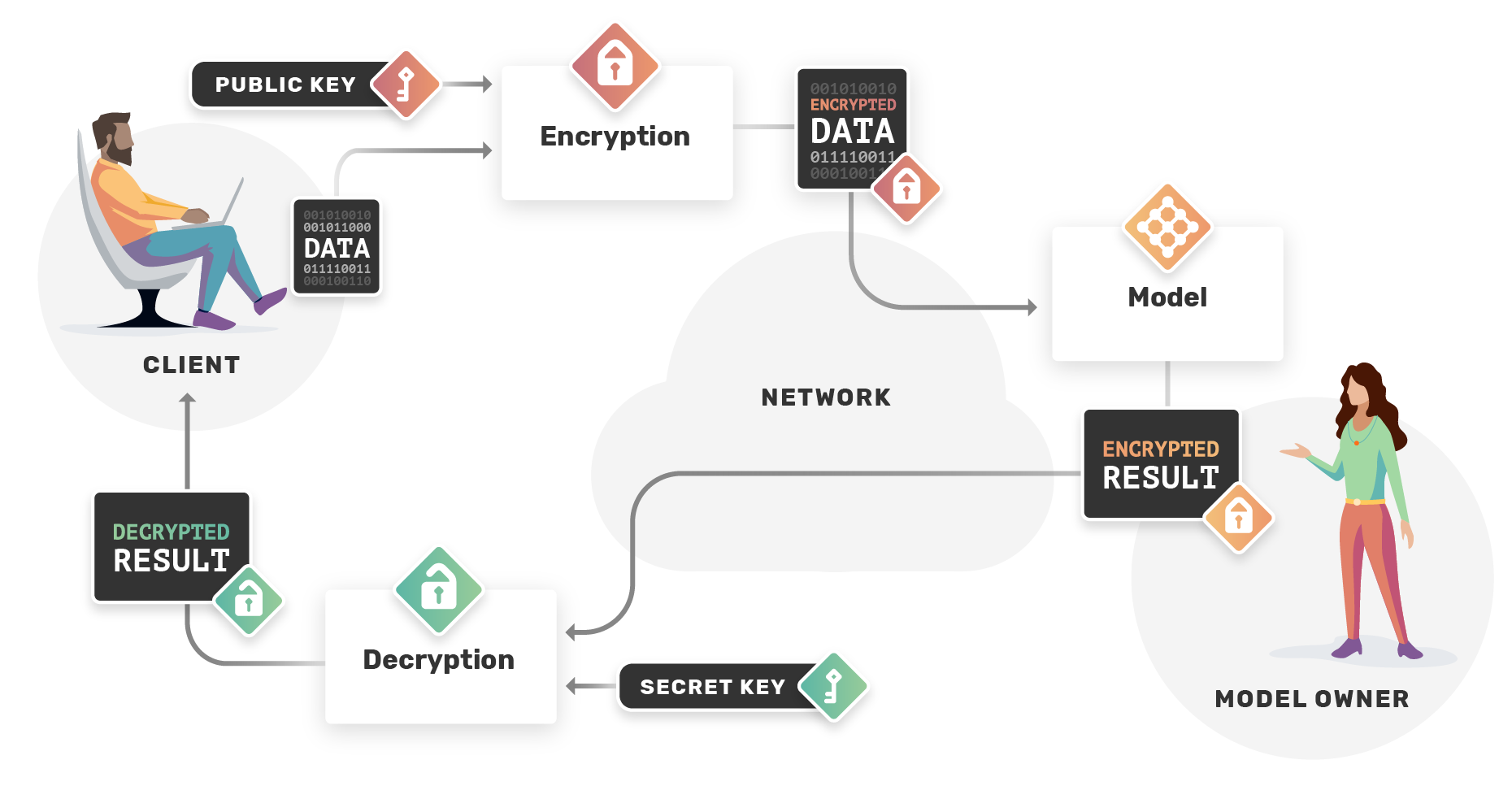
Homomorphic Encryption Schemes
Homomorphic encryption schemes are cryptographic constructions that enable Homomorphic Encryption .
There are four main types of homomorphic encryption schemes:
Partially Homomorphic Encryption (PHE): PHE allows for a specific type of mathematical operation, either addition or multiplication, to be performed on encrypted data while maintaining encryption. Examples of PHE schemes include the Paillier cryptosystems.
Somewhat Homomorphic Encryption (SHE): SHE schemes support both addition and multiplication computations on encrypted data but have a limitation on the number of operations that can be performed before compromising security. SHE strikes a balance between security and computational performance and is a crucial step towards achieving fully homomorphic encryption.
Leveled Fully Homomorphic Encryption(LFHE): LFHE can perform an arbitrary number of computations on encrypted data, as long as it has a pre-defined sequence of computations to be specified ahead of time.
Fully Homomorphic Encryption (FHE): FHE is the most powerful type of homomorphic encryption, allowing for both addition and multiplication operations on encrypted data, as well as more complex operations like Boolean operations. Examples of FHE schemes include the Gentry-BGV scheme and the Dijk-Gentry-Halevi-Vaikuntanathan (DGHV) scheme.
Some Known Applications of Homomorphic Encryption
Computing on Cloud:-
In the current scenario of booming cloud and edge computing it can be used to allow cloud servers to compute directly on encrypted data and return encrypted results to the owner of the data, who can then decrypt them locally thus maintaining security and privacy of user data.Refining closed AI/ML Models with proprietary Data:-
AI/ML algorithms can be fine tuned on sensitive data of company without the raw data ever being exposed. This helps to maintain privacy of company's data and also able get assistance from an more capable and mature AI which can make best decision for the company based on their own track record.Voting System:-
Voters can securely cast their votes without ever having to reveal who they voted for. This could make voting fairer and more transparent, and the enhanced privacy could encourage voter participation.
A simple Paillier encryption scheme could be used to add up votes in a way that keeps them secret and allows third parties to verify the accuracy of the vote count.
Hurdles in adopting Homomorphic Encryption
- Costs:- Homomorphic encryption comes with significant computational demands. In comparison to processing data in plaintext, it is notably slower, less efficient, and consumes more energy. The speed reduction can vary based on the specific technique employed.

- Not immune:-
Homomorphic encryption schemes are not immune to attacks. Similar to conventional encryption systems, they are vulnerable to side channel attacks that can extract plaintext during operation.
Some Implementations of Homomorphic Encryption
HeLib by IBM
Microsoft Seal by Microsoft
Concrete by Zama.ai
Conclusion
Homomorphic encryption presents a promising yet complex approach to data security and privacy. While it allows for computations on encrypted data without decryption, it faces challenges such as computational intensity, susceptibility to attacks, and limitations in practical applications like content scanning.
Partially homomorphic encryption offers better performance than fully homomorphic encryption but is constrained in its operations.
Fully homomorphic encryption, although theoretically groundbreaking, currently lacks practicality due to significant speed and efficiency issues.
Overall, while HME shows potential for secure data processing, its current limitations and challenges must be addressed before widespread adoption in real-world scenarios.
Future Reading References
Subscribe to my newsletter
Read articles from Dhwanil Shah directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
