Mastering IAM Roles in AWS: The Key to Secure, Temporary Access
 Pooja Manellore
Pooja Manellore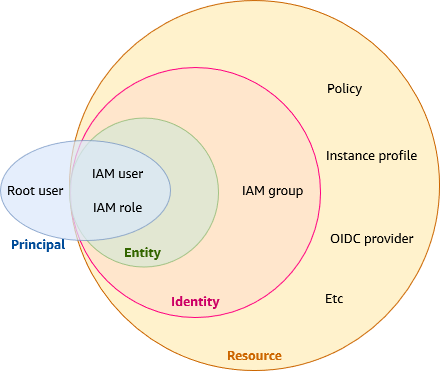
Welcome to today's session on IAM Roles in AWS. We're diving into a topic that often raises questions—What exactly is an IAM Role? How is it different from an IAM User? Why should we use roles, and what makes them so special? Today, we’ll answer these questions, explore the core advantages of IAM roles, and understand the many things we can accomplish using them.
Roles are essential when you want to allow someone or something (like an AWS service) to perform specific actions without providing permanent credentials. With roles, there's no need to expose your access keys or secret keys, making your environment more secure.
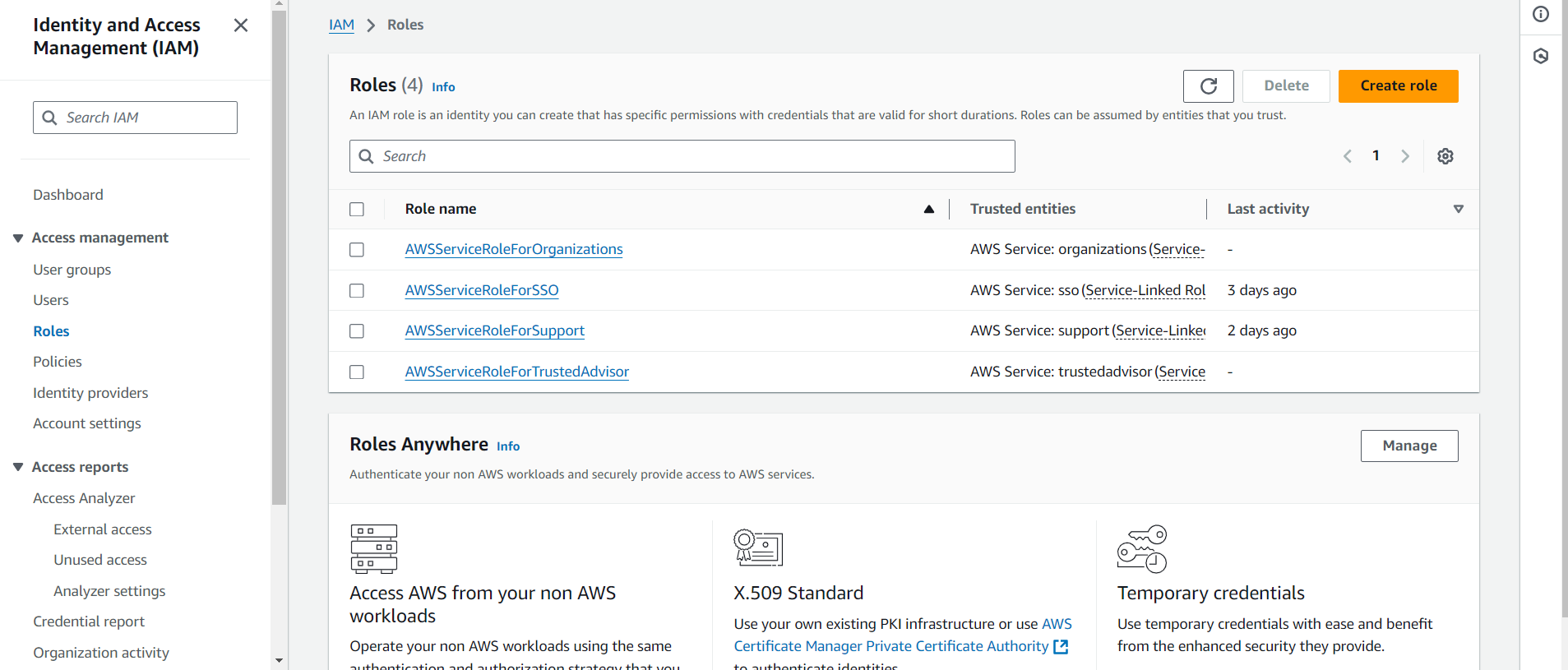
Step 1: Creating a Role for an AWS Service
To start, let’s learn how to create a role for an AWS service, and as we go, we’ll discuss the importance of roles.
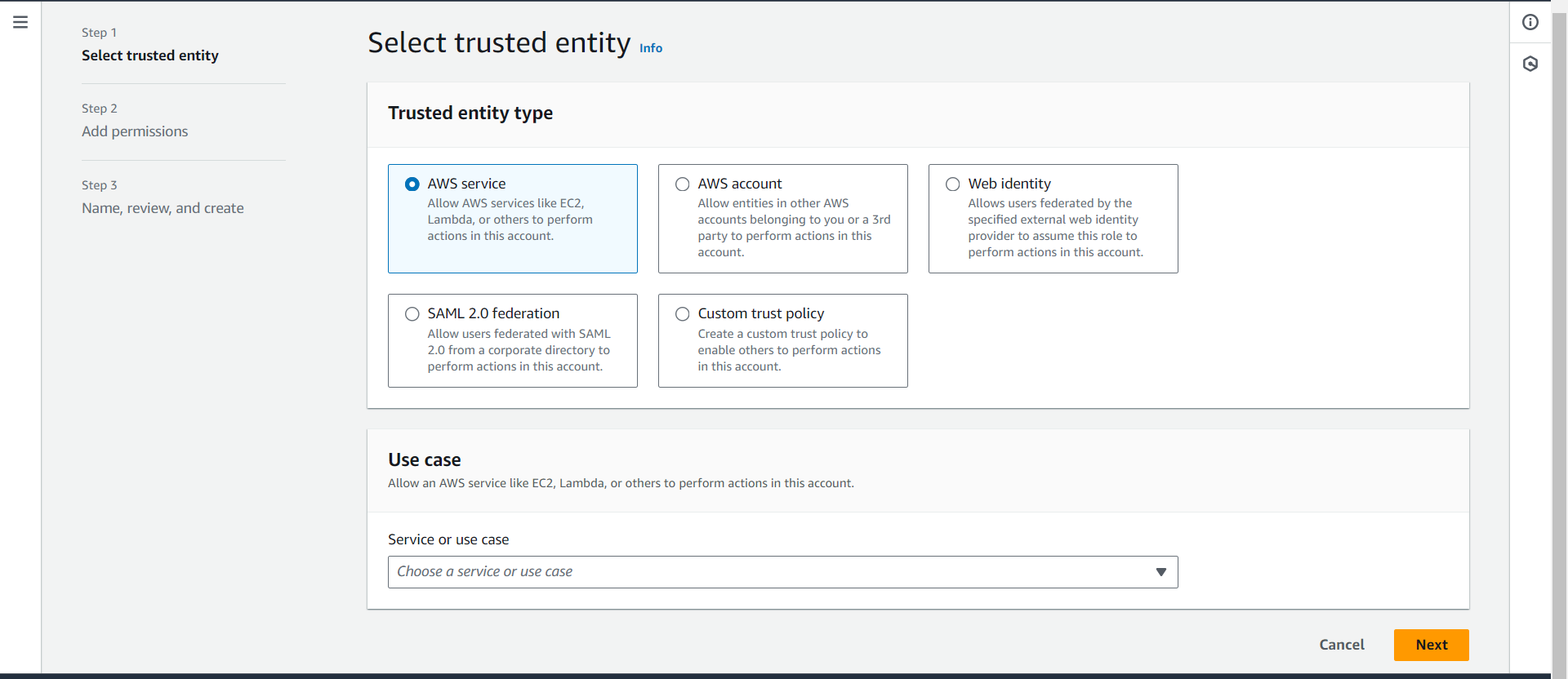
On the left-hand side of the AWS Console, navigate to Roles. Once there, click the Create Role button on the right. This brings up the Create Role dashboard, where you’ll see options for creating roles for various use cases:
AWS Service
AWS Account
Web Identity
SAML 2.0 Federation
Custom Trust Policy
Each option tailors the role creation to your specific needs. Let’s break down what each one does:
AWS Service Role:
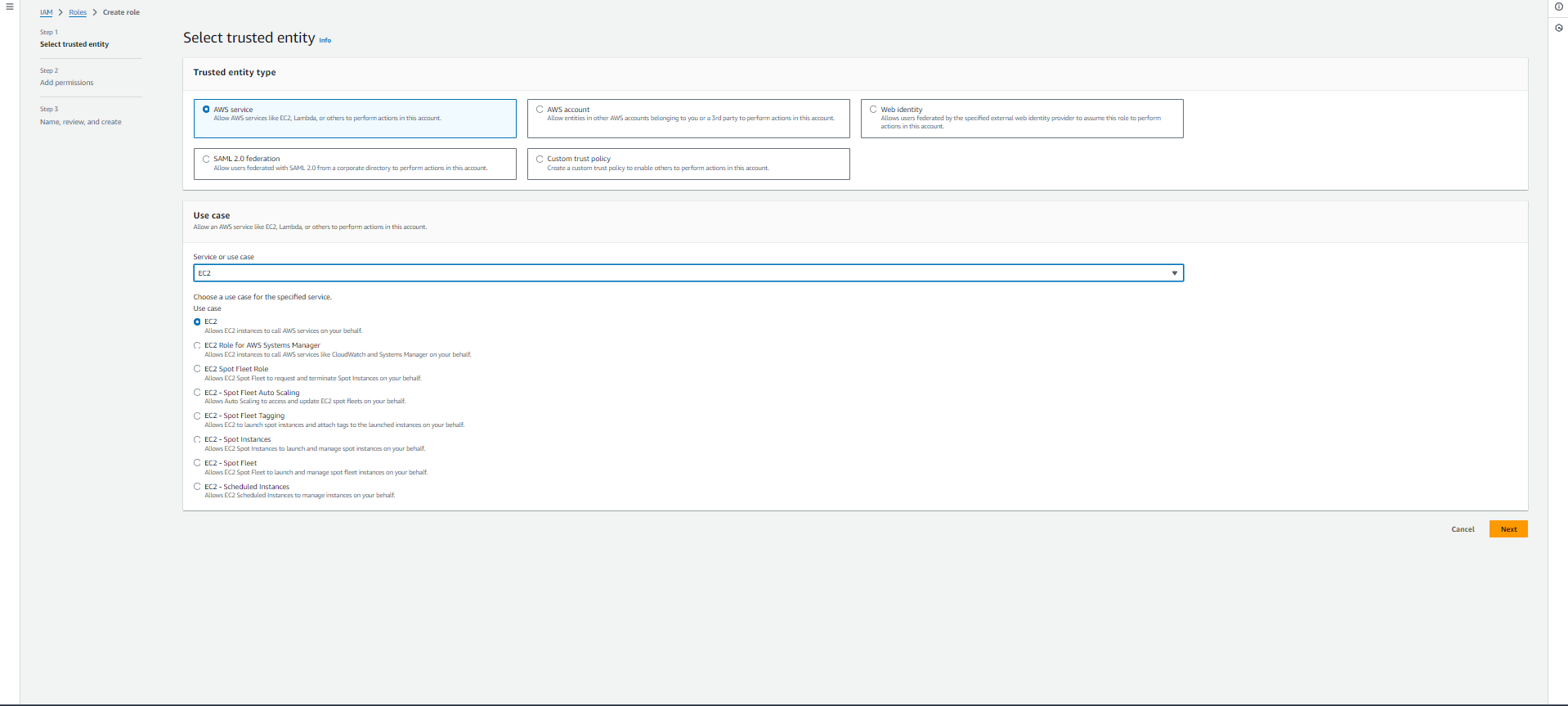
Use this when you want one AWS service to interact with another on your behalf. For example, if you’re launching an application on an EC2 instance and need it to access an S3 bucket, you can create a role that allows EC2 to perform read/write actions on the S3 bucket. In essence, the role lets EC2 assume temporary permissions to act on your behalf, without the need for permanent credentials. This process is called service-to-service role assumption.
AWS Account:
This type of role is perfect for cross-account access. It allows resources or users in one AWS account to access resources in another AWS account. For example, if a client or partner needs access to your account, you can create a cross-account role, granting them the specific permissions they need, without sharing credentials. You can also use it for third-party access, giving external entities controlled access to your AWS resources.
Web Identity:
Web Identity roles are used for application-level access. Suppose you’re developing an app where users need to upload photos to an S3 bucket. Instead of creating IAM users for each app user, you can allow them to access the bucket using temporary credentials provided by an external identity provider like Google, Facebook, or Amazon Cognito. This way, users can perform actions securely for a limited time (like 15 minutes) before the session expires.
SAML 2.0 Federation:
SAML Federation roles are used for enterprise-level single sign-on (SSO), integrating with identity providers like Active Directory or Okta. This method uses the SAML protocol to authenticate users, allowing them to access AWS resources through their existing corporate credentials. It’s ideal for large organizations that need to manage many users while maintaining high security.
Custom Trust Policy:
With a Custom Trust Policy, you can define specific trust relationships. Whether it's granting access to a particular service, role, IAM user, or even another AWS account, you can tailor these policies to meet your exact security needs.
Step 2: Assigning Permissions
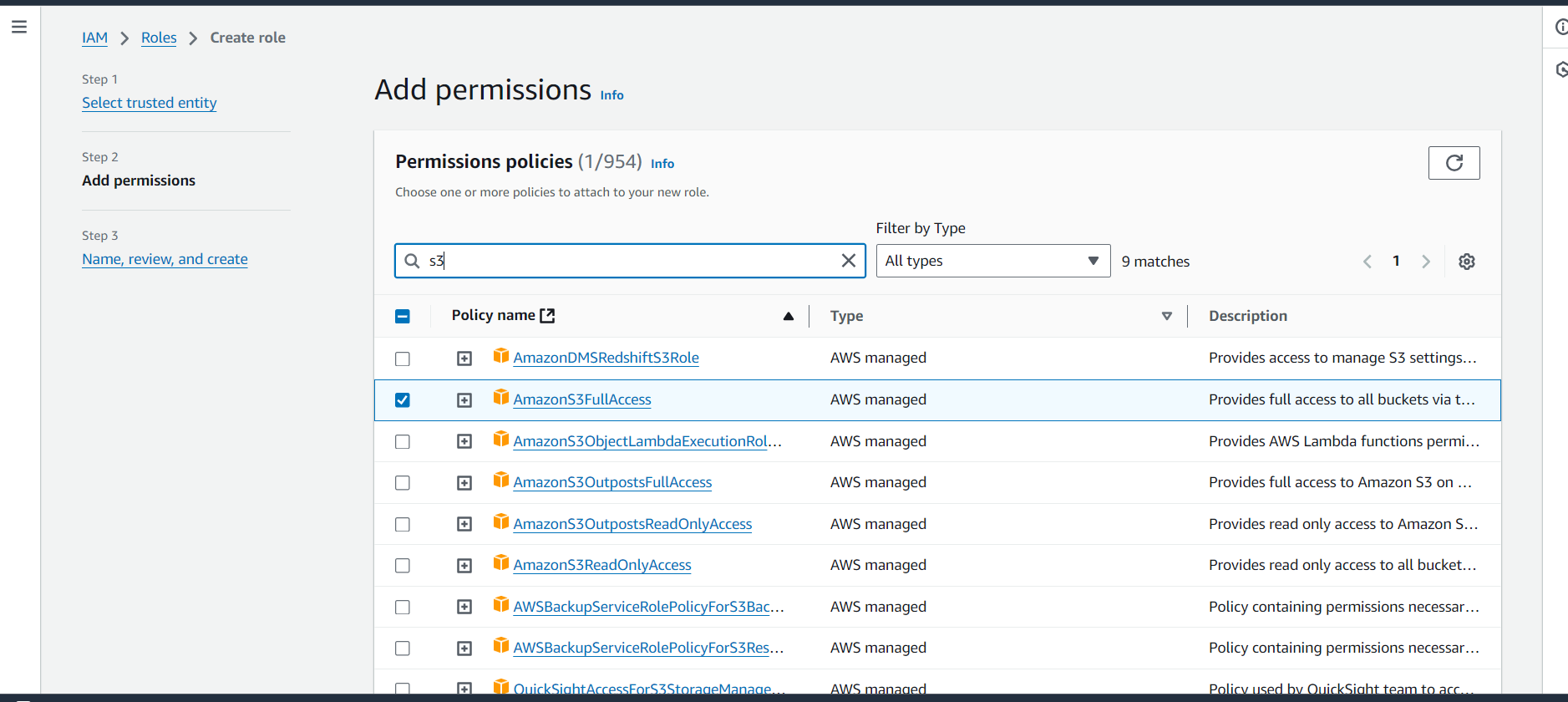
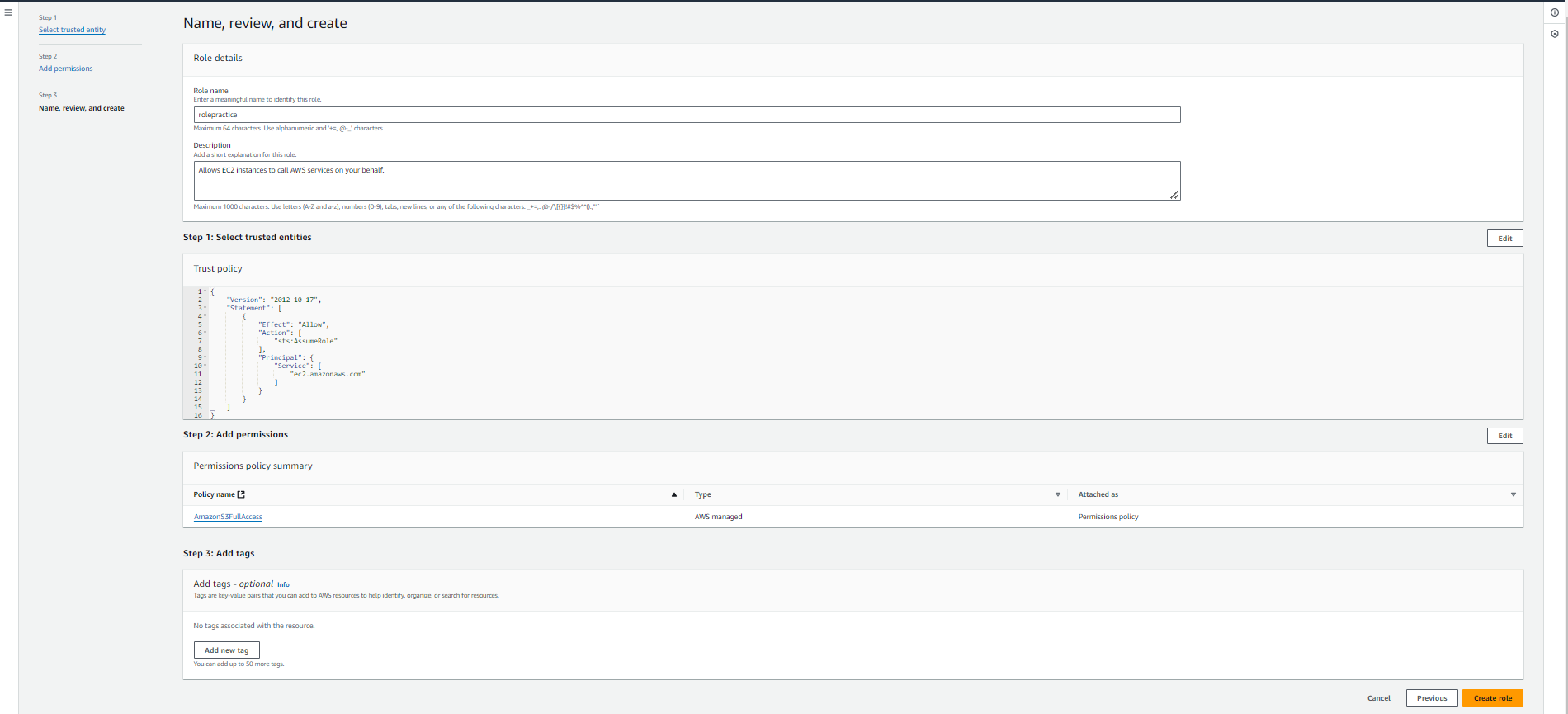
Now that we’ve selected AWS Service and chosen EC2 as our trusted service, it’s time to assign permissions. On the Permissions dashboard, you can choose from AWS Managed Policies, Customer-Managed Policies, or Job Function Policies. For this demo, let’s select AmazonS3FullAccess to grant the EC2 instance full access to an S3 bucket.
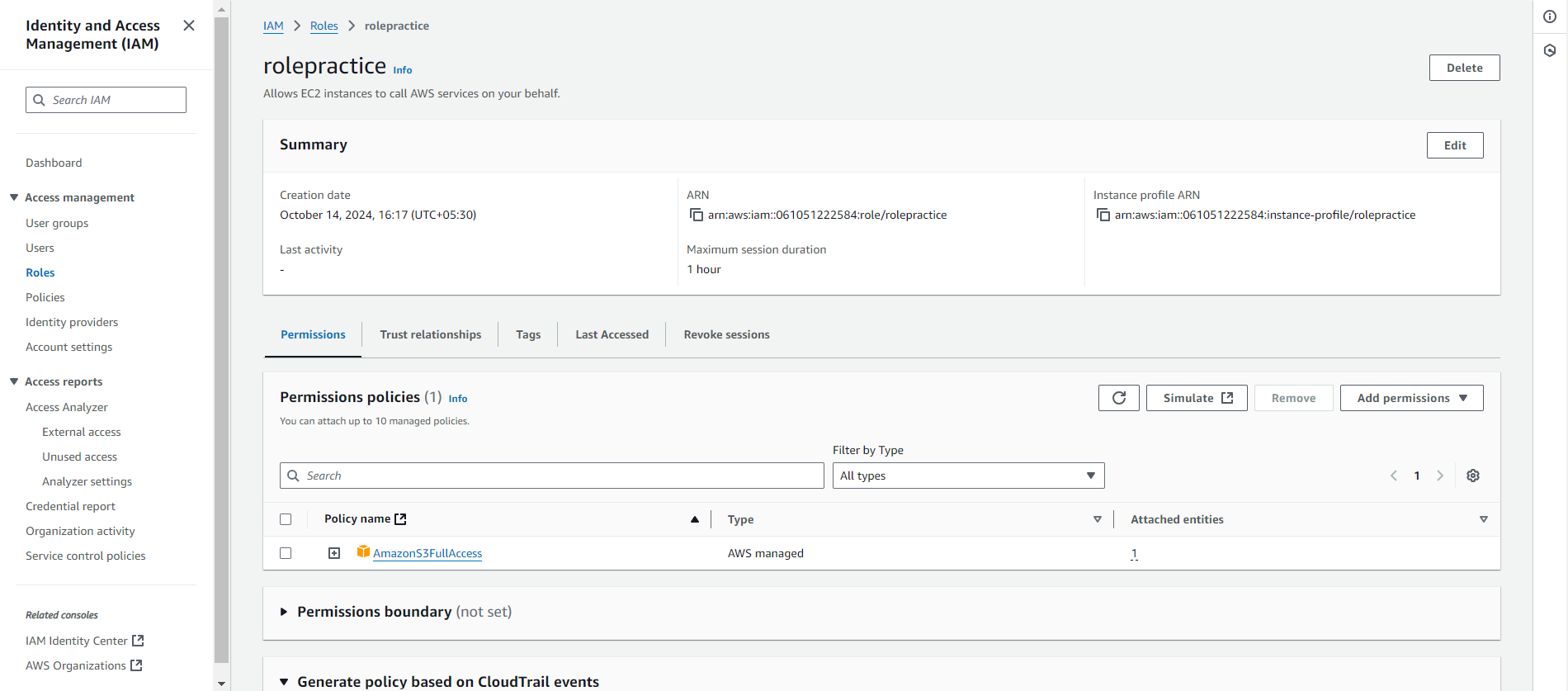
After assigning permissions, name your role—let’s call it rolepractice—then review the role and click Create Role.
Step 3: Attaching the Role to an EC2 Instance
Once the role is created, attach it to an EC2 instance. This will allow the instance to access the S3 bucket using AWS Management Console, AWS CLI, or AWS SDK. With the role in place, your EC2 instance can interact with S3 securely, without requiring permanent credentials.
AWS Service-Linked Roles:
Some roles don’t need to be created manually. AWS automatically generates Service-Linked Roles for services like Auto Scaling, RDS automatic backups, and managed database replication. These roles are fully managed by AWS, so you don’t need to worry about modifying or updating them.
Why Are IAM Roles So Important?
IAM roles in AWS are crucial because they provide secure, temporary access to resources for users, services, or applications without the need for long-term credentials. They enable fine-grained access control, facilitate cross-account access, service-to-service interaction, and federated authentication, all while keeping your environment safe and scalable.
The Speciality of Roles?
The specialty of an IAM role in AWS lies in its ability to provide temporary, secure access to AWS resources without needing long-term credentials like access keys and secret keys. It allows users, services, or applications to perform actions on AWS on a temporary, as-needed basis, ensuring:
Security: Roles eliminate the need to hard-code credentials, reducing the risk of exposure or misuse.
Flexibility: Roles can be assumed by various entities, such as EC2 instances, Lambda functions, or external users, enabling dynamic permissions.
Cross-account and service interaction: Roles allow access to resources across different AWS accounts and facilitate secure interactions between AWS services.
Subscribe to my newsletter
Read articles from Pooja Manellore directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pooja Manellore
Pooja Manellore
I have completed my B.Sc. in Computer Science in 2024 and have gained skills in Data Analytics, HTML, and CSS. I am currently advancing my expertise by learning DevOps, aiming to secure a role as a DevOps Engineer. I am eager to join a company immediately where I can apply my skills and continue growing in this field