☑️Day 44: Diving In Cluster Role & Cluster Role Binding in Kubernetes🚀
 Kedar Pattanshetti
Kedar Pattanshetti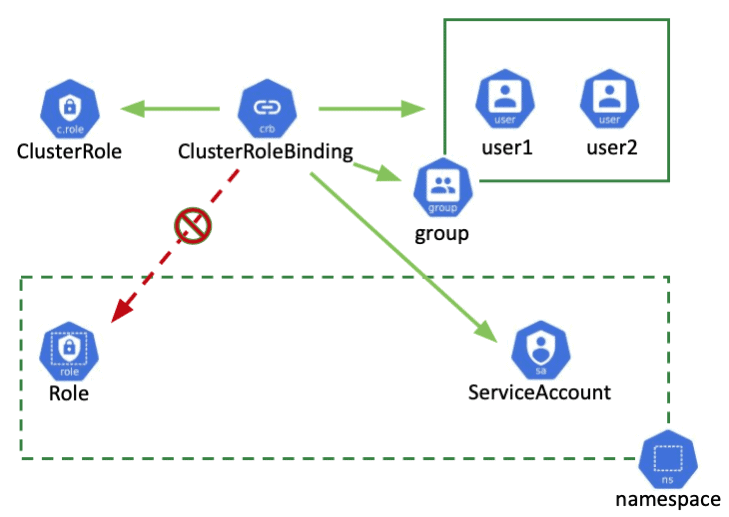
🔹Table of Contents :
Introduction
What is ClusterRole?
What is ClusterRoleBinding?
Real-Time Scenario
Components of ClusterRole and ClusterRoleBinding
ClusterRole: Rules and permissions
ClusterRoleBinding: Mapping to a subject
Hands-on Practice: Cluster Admin Operations
Step-by-Step Tasks with Commands
Task 1: Create a ClusterRole with admin privileges
Task 2: Bind the ClusterRole to a user or service account
Task 3: Perform cluster-wide operations
Task 4: Delete the ClusterRole and ClusterRoleBinding
Real-Time Use Cases in DevOps
Key Takeaways
Welcome to Day 44! Today, I delved into ClusterRole and ClusterRoleBinding, two key components of Kubernetes security that enable cluster-wide access control. These concepts are vital in DevOps to manage and secure large-scale Kubernetes clusters. In this newsletter, I’ll walk you through the theory, real-time examples, and step-by-step commands to help you master these topics.
✅1. What is ClusterRole?
ClusterRole defines a set of permissions (create, read, write, delete) that can be used across all namespaces.
Unlike a Role (which operates within a specific namespace), ClusterRole applies cluster-wide.
Use Cases:
Grant read-only access to all nodes or pods in every namespace.
Provide admin privileges across the cluster to a specific user or service account.
Allow monitoring tools to query the health of the entire cluster.
✅2. What is ClusterRoleBinding?
ClusterRoleBinding is used to assign a ClusterRole to a user, group, or service account.
It ensures the specified subject can perform the permitted actions defined in the ClusterRole, across all namespaces.
✅3. Real-Time Scenario
Imagine your company has a centralized DevOps team responsible for managing production and development clusters.
- Use Case:
You create a ClusterRole with administrative privileges and bind it to the DevOps service account. This allows them to create, read, update, and delete resources cluster-wide, ensuring smooth operations.
✅4. Components of ClusterRole and ClusterRoleBinding
ClusterRole: Defines the rules/permissions (e.g., get, list, delete pods).
ClusterRoleBinding: Maps the ClusterRole to a subject (user or service account).
✅5. Hands-on Practice: Cluster Admin Operations
In this section, I created a ClusterRole with admin access and practiced the key tasks such as create, read, write, delete operations across all namespaces. Let’s dive into the commands:
Step-by-Step Tasks with Commands
Task 1: Create a ClusterRole with Admin Privileges
Create a YAML file for ClusterRole:
# cluster-admin-role.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: cluster-admin-role rules: - apiGroups: [""] resources: ["pods", "nodes", "services"] verbs: ["get", "list", "create", "delete"]Apply the ClusterRole YAML:
kubectl apply -f cluster-admin-role.yamlVerify the ClusterRole:
kubectl get clusterroles | grep cluster-admin-role
Task 2: Bind the ClusterRole to a User or Service Account
Create a ClusterRoleBinding YAML:
# cluster-admin-binding.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: cluster-admin-binding subjects: - kind: User name: devops-admin apiGroup: rbac.authorization.k8s.io roleRef: kind: ClusterRole name: cluster-admin-role apiGroup: rbac.authorization.k8s.ioApply the RoleBinding:
kubectl apply -f cluster-admin-binding.yamlVerify the ClusterRoleBinding:
kubectl get clusterrolebindings | grep cluster-admin-binding
Task 3: Perform Cluster-Wide Operations
Create a Pod in any Namespace:
kubectl create namespace dev kubectl run nginx-pod --image=nginx -n devList Pods Across All Namespaces:
kubectl get pods --all-namespacesDelete a Pod from Another Namespace:
kubectl delete pod nginx-pod -n dev
Task 4: Delete the ClusterRole and ClusterRoleBinding
Delete the ClusterRoleBinding:
kubectl delete clusterrolebinding cluster-admin-bindingDelete the ClusterRole:
kubectl delete clusterrole cluster-admin-role
✅6. Real-Time Use Cases in DevOps
Service Accounts for Automation:
- ClusterRoles are assigned to service accounts running CI/CD pipelines (e.g., Jenkins) to deploy and manage resources across multiple namespaces.
Centralized Monitoring Systems:
- Monitoring tools like Prometheus need ClusterRoles to scrape metrics from all nodes, pods, and services.
Grant Temporary Access:
- In incidents or troubleshooting scenarios, a ClusterRoleBinding can be temporarily created to give admin access to DevOps engineers.
✅7. Key Takeaways
ClusterRoles enable access across the entire cluster, while Roles operate within a namespace.
ClusterRoleBinding ensures users or service accounts can perform actions defined in a ClusterRole.
Use RBAC policies wisely to maintain security and follow the principle of least privilege.
🚀Thanks for joining me on Day 44! Let’s keep learning and growing together!
Happy Learning! 😊
#90DaysOfDevOps
Subscribe to my newsletter
Read articles from Kedar Pattanshetti directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
