AWS Identity and Access Management (IAM): The Cornerstone of Secure Access Control
 Venkata Pavan Vishnu Rachapudi
Venkata Pavan Vishnu RachapudiTable of contents
- 1. IAM Users, Roles, and Groups
- 2. IAM Policies
- 3. IAM Access Analyzer
- 4. Credential Reports
- 5. Securing S3 with Secure Transport Policies
- 6. Service Control Policies (SCPs)
- 7. Attribute-Based Access Control (ABAC)
- 8. Tag-Based Roles
- 9. IAM Permission Boundaries
- 10. Revoking IAM Role Sessions
- Conclusion
- Additional IAM Entities
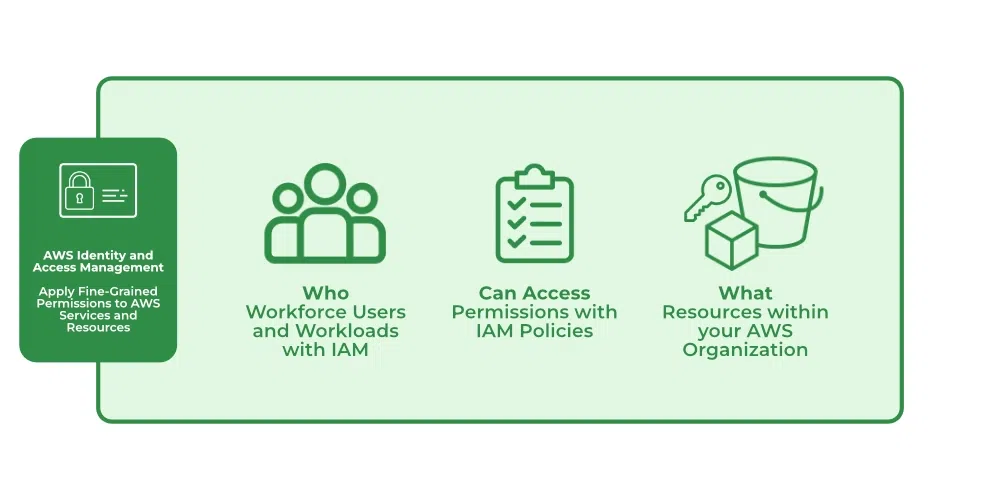
AWS Identity and Access Management (IAM) is essential for controlling access to your AWS resources. It allows you to define who can access what, under which conditions. Whether managing permissions for users, applications, or services, understanding IAM's core components and advanced features is vital for maintaining a robust security posture.
1. IAM Users, Roles, and Groups
IAM Users: Represent individuals or services that require AWS access. Users have credentials (passwords, access keys) and inherit permissions through policies.
IAM Roles: Provide temporary permissions to users or services, enabling them to act on AWS resources. They are crucial for scenarios like cross-account access or granting permissions to AWS services.
IAM Groups: A collection of IAM users sharing the same permissions, simplifying access management across teams.
2. IAM Policies
IAM policies are JSON documents that define permissions within your AWS environment. Key components include:
Action: The operations allowed (e.g.,
s3:PutObject).NotAction: Specifies exceptions to broad permissions.
Effect: Determines whether the action is allowed or denied.
Principal: Specifies which user or service the policy applies to.
Condition: Adds additional logic, like restricting access to secure channels (SSL only).
3. IAM Access Analyzer
IAM Access Analyzer helps identify resources shared with external accounts, continuously monitoring your environment for unintended access. If an S3 bucket is publicly accessible or a resource is shared with external accounts, Access Analyzer flags it, ensuring prompt remediation of risks.
4. Credential Reports
Credential reports provide a summary of all users and their security credentials, including MFA usage, access key age, and password health. This tool is essential for maintaining security best practices, such as regularly rotating access keys, enforcing MFA, and auditing inactive credentials.
5. Securing S3 with Secure Transport Policies
You can enforce secure (HTTPS) access to your S3 buckets by defining policies that deny insecure HTTP requests. For example:
jsonCopy code{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": "arn:aws:s3:::mybucket/*",
"Condition": {
"Bool": {
"aws:SecureTransport": "false"
}
}
}
]
}
This policy ensures only secure, encrypted communications (HTTPS) are allowed for accessing the S3 bucket.
6. Service Control Policies (SCPs)
SCPs are used within AWS Organizations to set guardrails across your accounts. While IAM policies define access within a single account, SCPs restrict access across all accounts in an AWS Organization. For example, you can prevent users from creating IAM users or accessing resources in certain regions across all accounts.
7. Attribute-Based Access Control (ABAC)
ABAC allows defining permissions based on resource or user tags rather than static roles, making permissions more dynamic and scalable. For example, you can grant a user access to resources tagged with department=finance, automatically updating their permissions as tags change.
8. Tag-Based Roles
Tag-based roles provide flexibility by dynamically assigning permissions based on resource or user tags. This simplifies permission management, especially in large environments. An example policy for dynamic role access is:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:StartInstances",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestTag/Team": "Development"
}
}
}
]
}
This policy allows only users tagged with Team: Development to start EC2 instances, enhancing access management efficiency.
9. IAM Permission Boundaries
IAM permission boundaries are an advanced feature that defines the maximum permissions that IAM roles and users can have. They act as a "fence" around IAM policies, ensuring that users and roles can only access resources and perform actions within the limits defined by the boundary.
Use Case: Permission boundaries are particularly useful in scenarios where you want to delegate permission management but still maintain control over the actions that can be performed.
Example: If you have a permission boundary that allows only
s3:ListBucketands3:GetObject, even if a user has a policy granting broader permissions, they will only be able to perform the actions allowed by the boundary.
By implementing permission boundaries, organizations can enforce security and compliance requirements while allowing teams to manage their own permissions more flexibly.
10. Revoking IAM Role Sessions
Using AWS Management Console:
Sign in to the AWS Management Console.
Go to the IAM Console:
- Navigate to the IAM service from the AWS Management Console.
Select "Roles":
- Click on Roles in the left sidebar and find the role whose sessions you want to revoke.
View "Session Details":
- Select the role and navigate to the "Trust relationships" tab or look for any section detailing active sessions.
Terminate Sessions:
While AWS doesn't provide a direct way to revoke sessions through the console, you can:
Update the trust policy to deny access (e.g., remove or update conditions).
Use the AWS CLI or AWS SDK to revoke session tokens on active sessions.
Using AWS CLI:
Delete the Role or Modify its Trust Policy: This effectively revokes ongoing sessions:
iam delete-role --role-name <role-name>Using Session Policies: Modify the session policy to deny further access:
iam update-assume-role-policy --role-name <role-name> --policy-document file://policy.jsonRevoke Specific STS Tokens: Manage access keys associated with the session token, though AWS does not provide a direct way to revoke STS tokens via CLI.
Important Notes:
Revoking IAM role sessions impacts users and processes using those roles, so ensure to communicate any changes.
Consider using Multi-Factor Authentication (MFA) to further secure roles and access.
Apply IAM policies that include conditions to limit when a role can be assumed.
Conclusion
AWS IAM is a powerful tool for securing cloud environments. By mastering key concepts like IAM users, roles, policies, and advanced features such as Access Analyzer and ABAC, you can build a robust security framework that scales with your cloud infrastructure. Always audit, plan, and automate where possible to maintain the highest security standards.
Additional IAM Entities
Here are a few IAM entities that are often used in conjunction with access management:
Source IP: The originating IP address of the requestor, which can be used in conditions to restrict access based on the request's origin.
VPC IP: The IP address associated with the Virtual Private Cloud (VPC), providing an additional layer of network security.
VPC Endpoint IP: The IP address associated with a VPC endpoint, enabling secure access to AWS services from within a VPC without needing an internet gateway.
These entities can enhance your IAM policies by allowing you to specify conditions based on network location or request origin.
Subscribe to my newsletter
Read articles from Venkata Pavan Vishnu Rachapudi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Venkata Pavan Vishnu Rachapudi
Venkata Pavan Vishnu Rachapudi
I'm Venkata Pavan Vishnu, a cloud enthusiast with a strong passion for sharing knowledge and exploring the latest in cloud technology. With 3 years of hands-on experience in AWS Cloud, I specialize in leveraging cloud services to deliver practical solutions and insights for real-world scenarios. Whether it's through engaging content, cloud security best practices, or deep dives into storage solutions, I'm dedicated to helping others succeed in the ever-evolving world of cloud computing. Let's connect and explore the cloud together!