Securing Secrets with SOPS: An Introduction
 Maxat Akbanov
Maxat Akbanov
SOPS (Secrets OPerationS) is an open-source tool developed by Mozilla for managing secrets — such as passwords, API keys, and confidential configuration data — in a secure and convenient manner. Initially launched in 2015 as a Mozilla project, it has been donated and accepted to CNCF on May 17, 2023. It serves as an editor for encrypted files, supporting various formats including YAML, JSON, ENV, INI, and binary files. SOPS integrates seamlessly with key management systems like AWS KMS, GCP KMS, Azure Key Vault, age, and PGP to encrypt and decrypt data.

The main benefit of the tool is that you don’t have to encrypt and decrypt the files with one tool and then read them with another tool. Sops allows you to edit and read the secret values right inside the sops text editor! Hence, you avoid using two tools and simplify the secret management. The secret values inside the sops editor are encrypted and decrypted automatically.
SOPS is a powerful tool that bridges the gap between security and usability in secret management. By integrating with industry-standard key management systems and supporting a variety of file formats, it provides a secure and efficient way to handle sensitive information within collaborative and automated environments.
Key Features
Multi-Format Support
- YAML, JSON, ENV, INI, and Binary Files: SOPS can handle a variety of file formats commonly used in configuration and environment settings.
Encryption Mechanisms
AWS KMS, GCP KMS, Azure Key Vault: Leverage cloud-based key management services to encrypt and decrypt secrets.
age: A modern, simple, and secure file encryption tool.
PGP: Utilize Pretty Good Privacy keys for encryption, supporting both public and private key pairs.
Selective Encryption
- Encrypts Only the Values: SOPS encrypts the values within the file while keeping the keys and structure in plaintext. This approach allows the file to remain human-readable in terms of structure and facilitates easier version control and diffing.
Version Control Friendly
- Git Integration: Encrypted files can be safely stored in version control systems like Git, enabling collaborative workflows without exposing sensitive information.
Ease of Use
Transparent Editing: SOPS allows you to edit encrypted files as if they were unencrypted. It handles the encryption and decryption transparently during the editing process.
Command-Line Interface: Provides a CLI
sopstool for easy integration into scripts and automation pipelines.
Installation on Linux
Binaries and packages of the latest stable release are available at https://github.com/getsops/sops/releases.
To install
sopson Linux on an AMD64 architecture:# Download the binary curl -LO https://github.com/getsops/sops/releases/download/v3.9.1/sops-v3.9.1.linux.amd64 # Move the binary in to your PATH sudo mv sops-v3.9.1.linux.amd64 /usr/local/bin/sops # Make the binary executable sudo chmod +x /usr/local/bin/sopsInstall
cosigntool for checksum and signature verification:# Download the latest release file for your Linux architecutre (e.g. amd64) wget https://github.com/sigstore/cosign/releases/download/v2.4.1/cosign-linux-amd64 # Move the binary in to your PATH sudo mv cosign-linux-amd64 /usr/local/bin/cosign # Make the binary executable chmod +x /usr/local/bin/cosignVerify the installation:
# Download the checksums file, certificate and signature curl -LO https://github.com/getsops/sops/releases/download/v3.9.1/sops-v3.9.1.checksums.txt curl -LO https://github.com/getsops/sops/releases/download/v3.9.1/sops-v3.9.1.checksums.pem curl -LO https://github.com/getsops/sops/releases/download/v3.9.1/sops-v3.9.1.checksums.sig # Verify the checksums file cosign verify-blob sops-v3.9.1.checksums.txt \ --certificate sops-v3.9.1.checksums.pem \ --signature sops-v3.9.1.checksums.sig \ --certificate-identity-regexp=https://github.com/getsops \ --certificate-oidc-issuer=https://token.actions.githubusercontent.com
How SOPS Works
Data Encryption Key (DEK)
- SOPS generates a symmetric Data Encryption Key for encrypting the actual data within the file.
Master Key Encryption
- The DEK is encrypted using one or more master keys from your chosen key management services (e.g., AWS KMS, GCP KMS, Azure Key Vault, PGP).
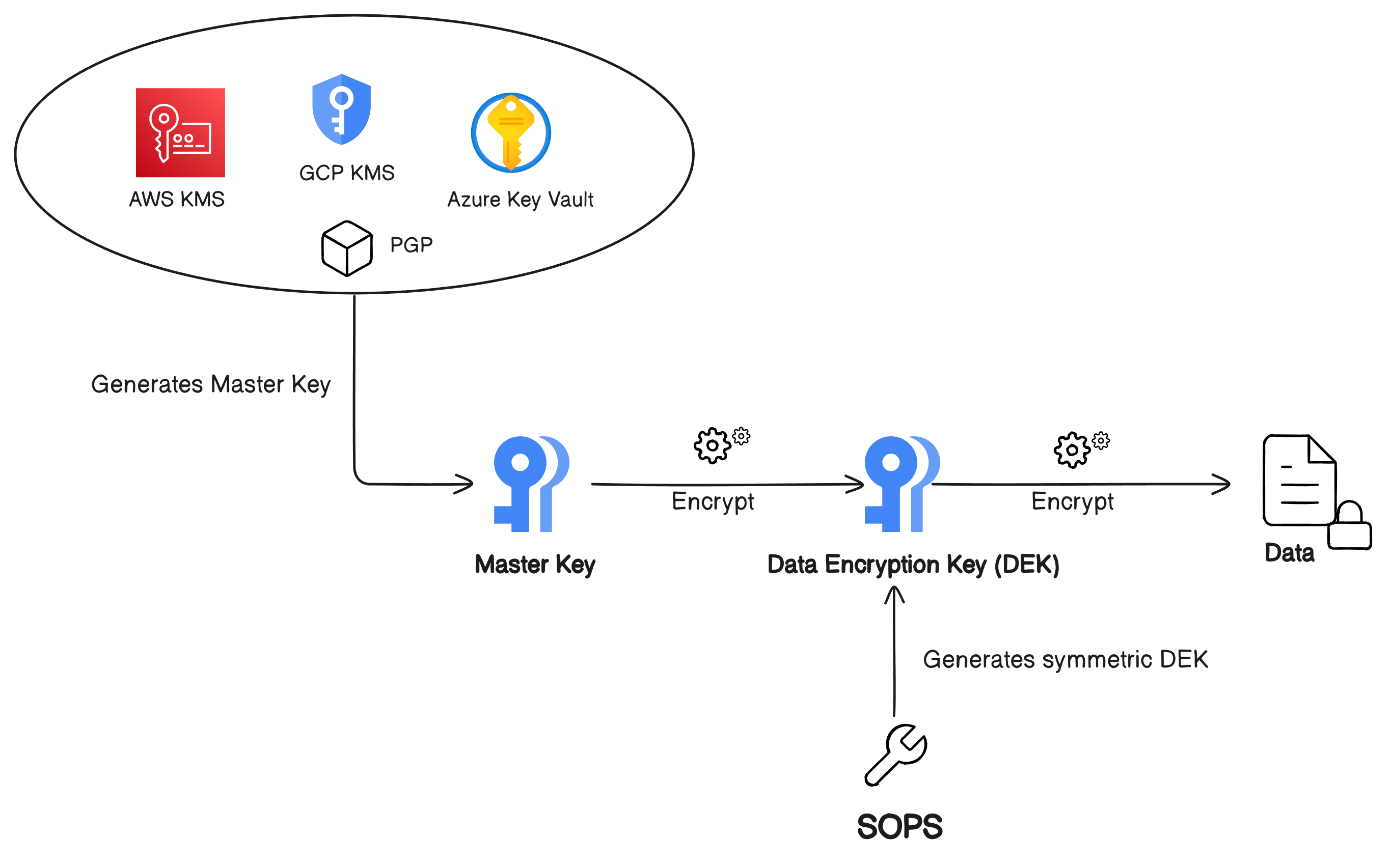
File Structure Preservation
- By encrypting only the values and not the keys or structure, SOPS ensures that the file remains partially readable. This feature is particularly useful for understanding the configuration without exposing sensitive data.
Decryption Process
- When you open a file with SOPS, it decrypts the values on-the-fly using the appropriate master keys. After editing, it re-encrypts the values before saving.
Use Cases
Secure Configuration Management
- Store application configurations that contain secrets in a secure manner.
Infrastructure as Code (IaC)
- Embed encrypted secrets within your IaC templates for tools like Kubernetes, Terraform, or Ansible.
Collaborative Environments
- Allow multiple team members to access and edit secrets securely without sharing plaintext secrets.
Automated Deployment Pipelines
- Integrate SOPS into CI/CD pipelines to decrypt secrets during the deployment process securely.
Using SOPS with PGP and a text file
Below is an example of how to encrypt and decrypt a text file using SOPS with PGP.
Prerequisites
Install GPG (GNU Privacy Guard):
On Ubuntu:
sudo apt install gnupgGenerate a PGP key pair if you don't already have one:
gpg --full-generate-keyUse RSA encryption (default).
Provide your name, email, and password as requested.
List the generated key and keep the note of the key fingerprint:
gpg --list-secret-keys "<your_key_name>"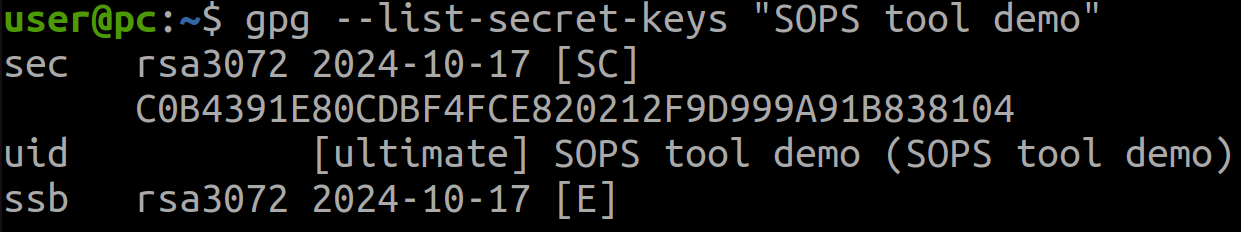
Export the PGP public key to encrypt files:
gpg --armor --export [key_id] > my-public-key.ascExport the PGP private key to decrypt files:
gpg --armor --export-secret-keys [key_id] > my-private-key.asc
Encrypting a Text File using SOPS and PGP
Create a sample text file to encrypt:
echo "my-secret-password" > secret.txtConfigure the default encryption and decryption behavior of SOPS tool. Create a file named
.sops.yamlunder the$HOMEdirectory with the Key ID from the previous steps:creation_rules: - pgp: >- C0B4391E80CDBF4FCE820212F9D999A91B838104Encrypt the file using SOPS and your PGP key:
sops --encrypt secret.txt > secret.enc.txtThis will encrypt the
secret.txtfile with the default PGP key specified in.sops.yamlfile.Verify the encrypted content:
cat secret.enc.txtYou should see a YAML structure with encrypted content that looks like this:
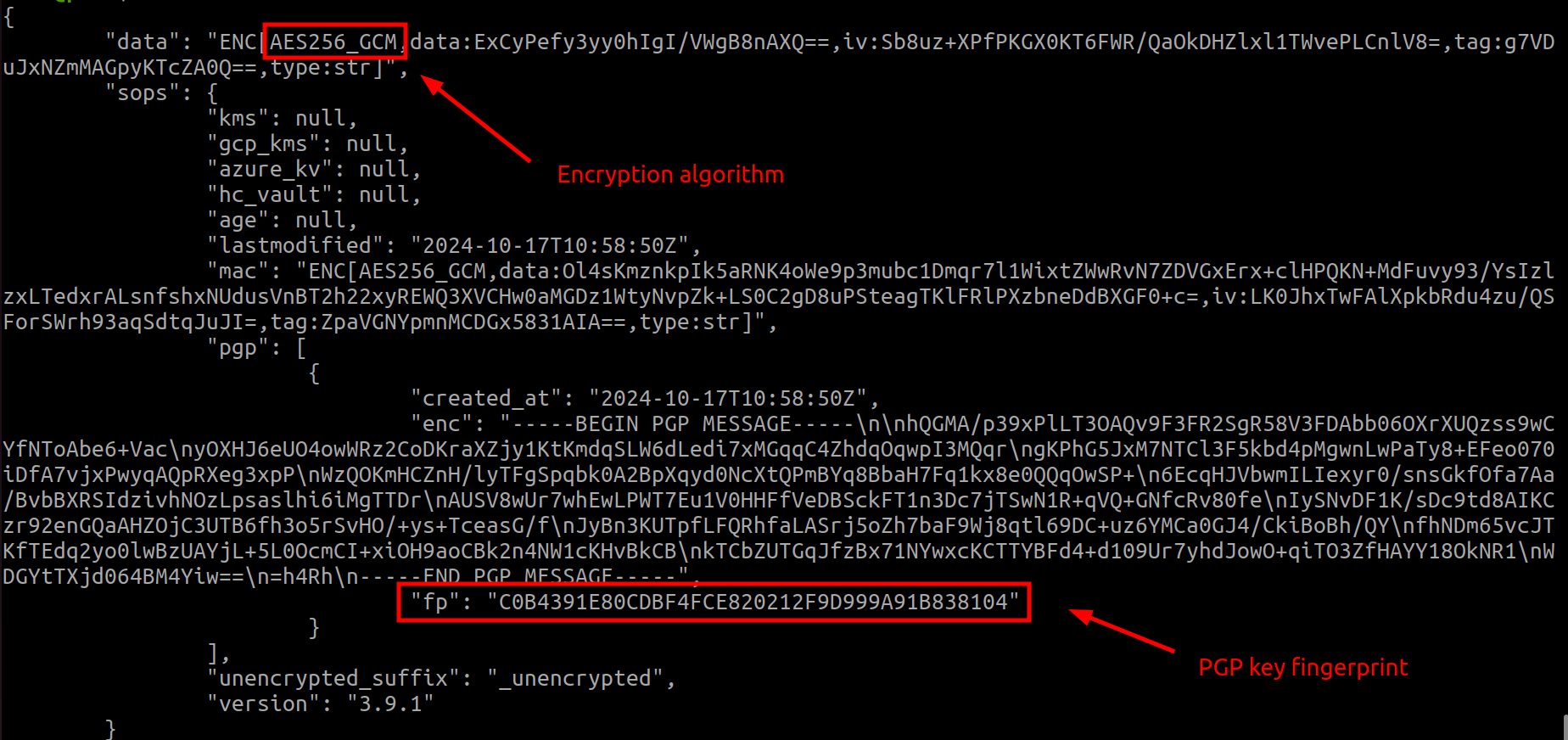
Decrypting the Text File
Use SOPS to decrypt the encrypted file:
sops --decrypt secret.enc.txt > decrypted.txtView the decrypted content:
cat decrypted.txtYou should see the original text:
my-secret-password
Automating Decryption in Configuration Files
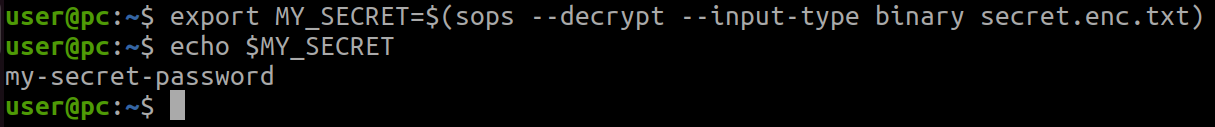
You can use SOPS-encrypted files in your configuration by decrypting them on the fly, such as:
export MY_SECRET=$(sops --decrypt --input-type binary secret.enc.txt)
This example shows how to use SOPS with PGP to encrypt and decrypt a text file. With PGP encryption, you can ensure that only users with the appropriate private key can decrypt the file, making it ideal for managing secrets in infrastructure code or configuration files.
References:
Subscribe to my newsletter
Read articles from Maxat Akbanov directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Maxat Akbanov
Maxat Akbanov
Hey, I'm a postgraduate in Cyber Security with practical experience in Software Engineering and DevOps Operations. The top player on TryHackMe platform, multilingual speaker (Kazakh, Russian, English, Spanish, and Turkish), curios person, bookworm, geek, sports lover, and just a good guy to speak with!