Satoshi Scoop Weekly, 18 Oct 2024
 Cryptape
CryptapeTable of contents
- Crypto Insights
- Vulnerabilities in Bitcoin Core Versions Prior to v25.0
- A Consensus Failure Vulnerability Affecting BTCD Full Nodes
- Explaining Why Nostr Matters in Ten Minutes
- Lightning Network Node Testing Made Easy With lnprototest
- Will the .io Domain Disappear? How Geopolitics Reshapes Digital Infrastructure
- Q3 2024 Asian Web3 Market Trends
- Top Reads on Blockchain and Beyond

Crypto Insights
Vulnerabilities in Bitcoin Core Versions Prior to v25.0
Bitcoin Core developer Niklas Gögge disclosed three vulnerabilities affecting Bitcoin Core versions prior to v25.0:
CVE-2024-35202 remote crash vulnerability (High severity)
DoS due to inv-to-send sets growing too large (Medium severity)
Hindered block propagation due to mutated blocks (Medium severity)
A Consensus Failure Vulnerability Affecting BTCD Full Nodes
Antoine Poinsot and Niklas Gögge disclosed CVE-2024-3836, a consensus failure vulnerability affecting BTCD full nodes. Bitcoin Core’s FindAndDelete function only removes exact matches of signatures from the signature script. The BTCD implementation's removeOpcodeByData function, however, removes any data containing the signature from the script. This can cause BTCD to delete more data from the signature script than Bitcoin Core does before verifying commitments, leading to one system considering a commitment valid while the other not. Any transaction with an invalid commitment is invalid, the same goes for blocks, causing a consensus split between Bitcoin Core and BTCD. Nodes out of consensus could be tricked into accepting invalid transactions and might fail to see the latest transactions that the rest of the network has confirmed, potentially leading to money loss.
Explaining Why Nostr Matters in Ten Minutes
This talk outlines why Nostr matters by highlighting several key concepts.
Identity: Represented by a pair of public and private keys, functioning as an open social credit score not limited to specific platforms.
Notes: Signed posts allowing anyone to verify authorship and ensure content integrity without permission.
Relays: Servers that anyone can run, facilitating communication within the Nostr network.
Nostr promotes voice by circumventing centralized censorship, freedom from API accessibility changes imposed by platforms, authenticity/truth through hashing to verify notes, and the ability to transact with Bitcoin, supporting decentralized finance.
Video: Short Text Note by ODELL
Lightning Network Node Testing Made Easy With lnprototest
As the Lightning Network is rapidly evolving, each node must ensure compliance with the protocol specifications before upgrading to a new version. lnprototest (GitHub repo), a Python library communicating via BOLT8, establishes connections and sends noise messages among peers. To work with lnprototest, a Lightning implementation needs to develop a Runner in Python. This Runner interacts with lnprototest's workflow, serving as a bridge between the test framework and the Lightning node.
Will the .io Domain Disappear? How Geopolitics Reshapes Digital Infrastructure
The UK's relinquishment of the Chagos Archipelago (official name: British Indian Ocean Territory, corresponding domain: .io) to Mauritius will dissolve the geopolitical entity behind the .io domain. The International Organization for Standardization (ISO) is expected to remove the country code IO, promoting the Internet Assigned Numbers Authority (IANA) to cease new .io domain registrations and phase out existing ones.
The .io domain has long been popular among startups, especially those in the cryptocurrency. The author indicates that IANA might create new rules to allow .io to continue existing, as it could represent a significant source of revenue.
Q3 2024 Asian Web3 Market Trends
Asia's Web3 market is burgeoning, driven by tech-savvy populations, proactive governments, and enterprise involvement, with South Korea, Japan, and Vietnam as key players.
New regulations in South Korea, Indonesia, and Thailand are facilitating blockchain innovation, with sandbox regulations encouraging experimentation in RWAs, DeFi, and digital asset services.
Emerging markets like China and Cambodia present both opportunities and risks. China’s unofficial involvement remains significant despite regulations, while Cambodia offers potential for small and medium-sized businesses willing to navigate legal complexities.
Top Reads on Blockchain and Beyond
Overview of Bitcoin, Ethereum, and Solana Restaking Stack
This article reviews and evaluates the restaking frameworks within Bitcoin, Ethereum, and Solana ecosystems, highlighting projects in each. In terms of Bitcoin, three projects are involved: Babylon, Pell Network, and Photon. Each tackles distinct challenges within’ Bitcoin:
Babylon leverages Bitcoin’s staking and restaking capabilities to enhance the security of other PoS blockchains. It converts Bitcoin’s economic value into economic security, offering protection for other blockchains. Babylon operates its own PoS chain using the Cosmos SDK and supports non-custodial staking and restaking directly from Bitcoin without the need for third-party trust.
Pell Network integrates Bitcoin into the DeFi ecosystem using cross-chain technology, addressing the challenges of Bitcoin’s lack of liquidity and additional revenue streams.
Photon expands Bitcoin’s ability to execute smart contracts without altering its core structure. It implements staking and restaking directly on the Bitcoin mainnet, overcoming the limitation of no native smart contract support. All processes related to staking and restaking are verified on the Bitcoin mainnet, ensuring high security while offering flexible staking options.
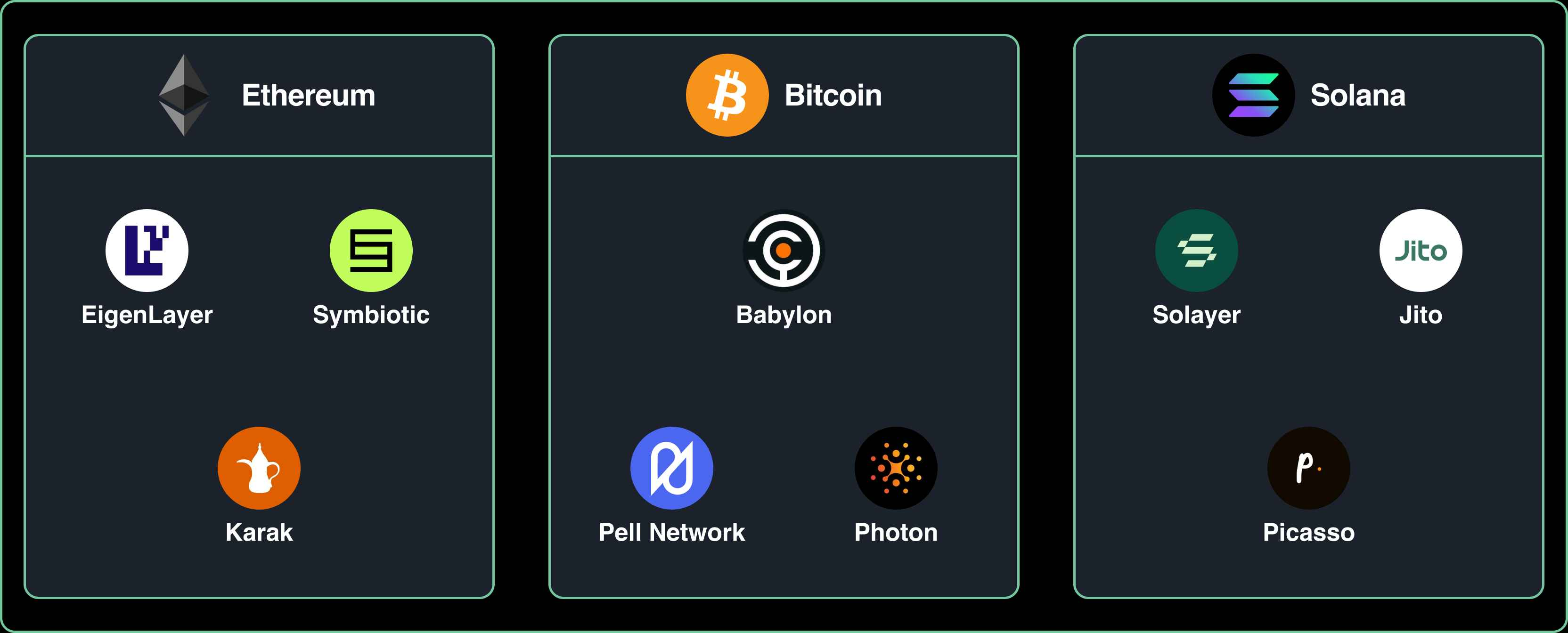
Image Source: Four Pillars
How to Optimize C++ Code for CKB-VM: Porting Bitcoin as an Example
This post details the direct porting and optimization of Bitcoin’s C++ code over to CKB virtual machine (CKB-VM). The work highlights the challenges and solutions, particularly for overcoming binary size limitations. This attempt indicates the potential for broader C/C++ code libraries porting to CKB-VM.
Adaptor Signatures: Unlocking the Potential of Applications in Zero-Knowledge Proof Construction and More
This article explores the potential of adaptor signatures, particularly their applications in zero-knowledge proof constructions and the on-chain verification of statements beyond the secp256k1 generator G, outlining a theoretical framework for using adaptor signatures in Zero-Knowledge Proof construction, despite practical verification challenges. It includes theoretical discussions on multi-base single statements, and proposes a practical method of embedding curve points in transaction messages to facilitate BIP340 signatures, enabling the verification of discrete logarithm equality (DLEQ) relationships on-chain.
Subscribe to my newsletter
Read articles from Cryptape directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
