What Is HTTP Proxy and How It Works
 GeeLark
GeeLark
What Are HTTP and HTTPS
HTTP
HTTP stands for Hypertext Transfer Protocol. It’s a set of rules that allows web browsers and web servers to communicate with each other. When you type a website address into your browser and hit enter, your browser sends a request using HTTP to the web server where the website is hosted.
The server then sends back the information requested, such as text, images, and videos, so your browser can display the website. HTTP is the foundation of data communication on the World Wide Web.
HTTPS
HTTPS stands for Hypertext Transfer Protocol Secure. It’s just like HTTP but with an added layer of security. When you use HTTPS, the communication between your web browser and the web server is encrypted. This means that any data sent back and forth is scrambled so that only your browser and the server can read it.
In Google Chrome, when you visit a website that uses HTTPS, the browser checks to ensure that the connection is secure. If everything is okay, Chrome will display a padlock icon and the message “Connection is Secure” in the address bar. This means that any data you send or receive from the website is protected from eavesdroppers and hackers.
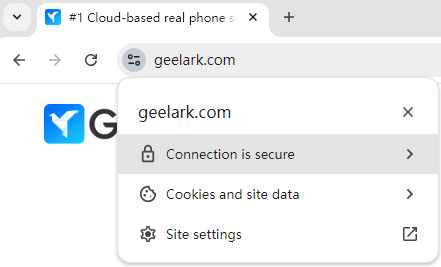
So, HTTPS is essentially HTTP with an extra “S” for security, making your online interactions safer.
What is an HTTP Proxy?
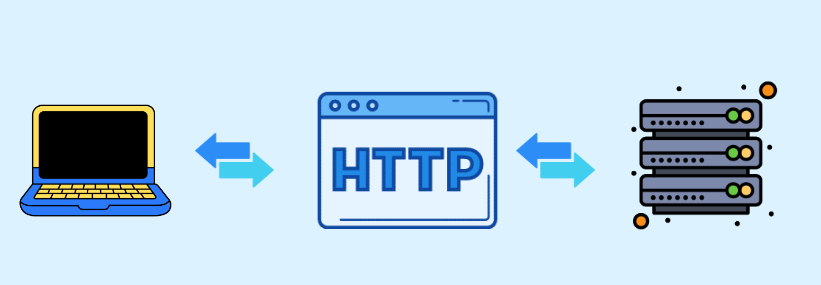
An HTTP proxy is a server that acts as an intermediary between a client and a web server, facilitating the forwarding of HTTP requests and responses. When a client, such as a web browser, makes an HTTP request to access a webpage, the request is first sent to the HTTP proxy server.
The proxy server then forwards this request to the web server, receives the response from the web server, and subsequently sends the response back to the client. This process introduces a layer of separation between the client and the web server, enhancing various aspects of the online experience.
Types of HTTP Proxies
Transparent Proxy
A transparent proxy, also known as an intercepting proxy, does not modify the request or response beyond what is necessary for proxy authentication and identification. It reveals the client’s original IP address to the web server, making it clear where the request originated.
Transparent proxies are often used for content filtering and caching in corporate environments, as they allow administrators to monitor and control user activities without requiring any configuration changes on the client side. This type of proxy is easy to deploy and manage, making it a convenient option for organizations. However, it does not provide anonymity or privacy, and can be detected and blocked by web servers.
Anonymous Proxy
An anonymous proxy hides the client’s IP address and other identifying information from the web server, providing a higher level of privacy compared to transparent proxies. While the web server knows that the request is coming through a proxy, it cannot determine the client’s actual IP address.
Anonymous proxies are commonly used to bypass geo-restrictions and access content that might be blocked in certain regions. While they offer enhanced privacy, they can be slower than transparent proxies due to the additional processing required and may still be detected by some advanced web server techniques.
High Anonymity Proxy (Elite Proxy)
High anonymity proxies, also known as elite proxies, offer the highest level of privacy. They not only hide the client’s IP address but also do not reveal that the request is coming through a proxy. The web server treats the request as if it is coming directly from a client, making it extremely difficult to trace back to the original source.
These proxies are ideal for users who require maximum privacy and security, but they can be slower and more expensive.
Reverse Proxy
A reverse proxy is positioned in front of web servers and forwards client requests to the appropriate backend server. Unlike forward proxies, which serve the client’s interests, reverse proxies serve the interests of the web server.
They are commonly used for load balancing, improving performance, and enhancing security by distributing incoming requests across multiple servers.
Reverse proxies enhance load balancing and performance while providing additional security by masking backend servers. However, they require more complex setup and configuration and can become a single point of failure if not properly managed.
Distorting Proxy
A distorting proxy provides anonymity by changing the client’s IP address to a random, incorrect one. This type of proxy alters the headers in the HTTP request to make it appear as though the request is coming from a different location entirely. Distorting proxies are useful for evading geographic restrictions and enhancing privacy.
They offer a good level of anonymity and are useful for bypassing geo-restrictions. However, they can be less reliable due to the random IP address assignment, and some services may detect and block distorted requests.
Use Cases of HTTP Proxies
HTTP proxies are incredibly versatile tools with a wide range of applications. They help manage multiple accounts, bypass geo-restrictions, enhance security, and improve browsing efficiency.
Managing Multiple Social Media Accounts
Many people need to manage several social media accounts for business or personal reasons. By providing different IP addresses for each account, HTTP proxies can help you avoid detection and keep your accounts safe from being blocked.
HTTP proxies can be particularly useful when used with GeeLark Cloud Phone. GeeLark allows users to manage multiple Android phones on the cloud, which is perfect for handling several social media profiles. By configuring HTTP proxies, each GeeLark Cloud Phone can have its own unique IP address, adding an extra layer of security and anonymity.
The key advantage of using GeeLark Cloud Phone is that each cloud phone has a different device ID, just like different physical devices. This helps to avoid issues related to account association and potential blocks. By integrating proxies, each cloud phone will appear to come from a different location, further reducing the risk of detection and ensuring smooth operation.
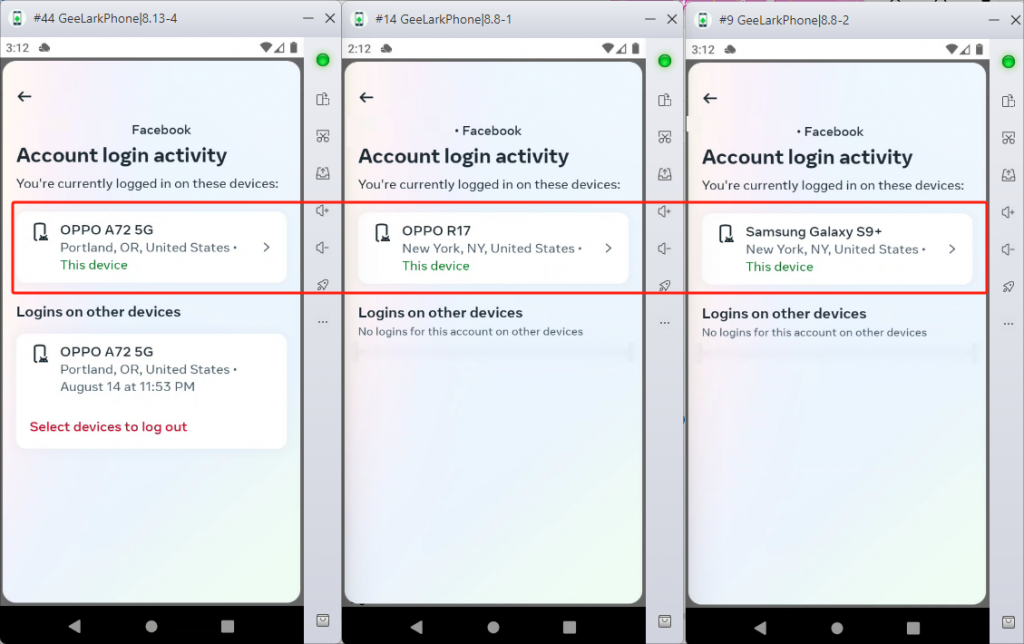
Account Farming
Account farming involves creating and managing many new accounts. This is useful for various online activities, such as marketing or testing. HTTP proxies can help you avoid detection and bans from platforms.
By frequently changing your IP address, it will look like each new account comes from a different user, reducing the risk of getting banned.
Crypto Giveaways
Crypto giveaways often require quick actions and multiple accounts to maximize gains. HTTP proxies can help you access these giveaways from different locations.
By bypassing geographic restrictions, you can participate in more giveaways. Proxies provide IPs from various countries, allowing you to access more opportunities.
Accessing Geo-Restricted Content
Sometimes, you need to access content or services that are only available in certain countries. HTTP proxies can help you get around these geographic restrictions.
By providing IP addresses from different countries, you can easily access geo-restricted content.
Data Caching and Content Filtering
If you access a lot of data frequently, HTTP proxies can cache this data to improve speed and efficiency. They can also filter unwanted content, making your browsing experience smoother.
Transparent proxies can cache commonly accessed data, reducing load times. They can also filter out unnecessary or harmful content, providing a safer browsing experience.
How to Set Up HTTP Proxies in GeeLark
Before creating your cloud phone profiles, it’s essential to set up your proxies first. Follow this simple guide for a smooth setup:
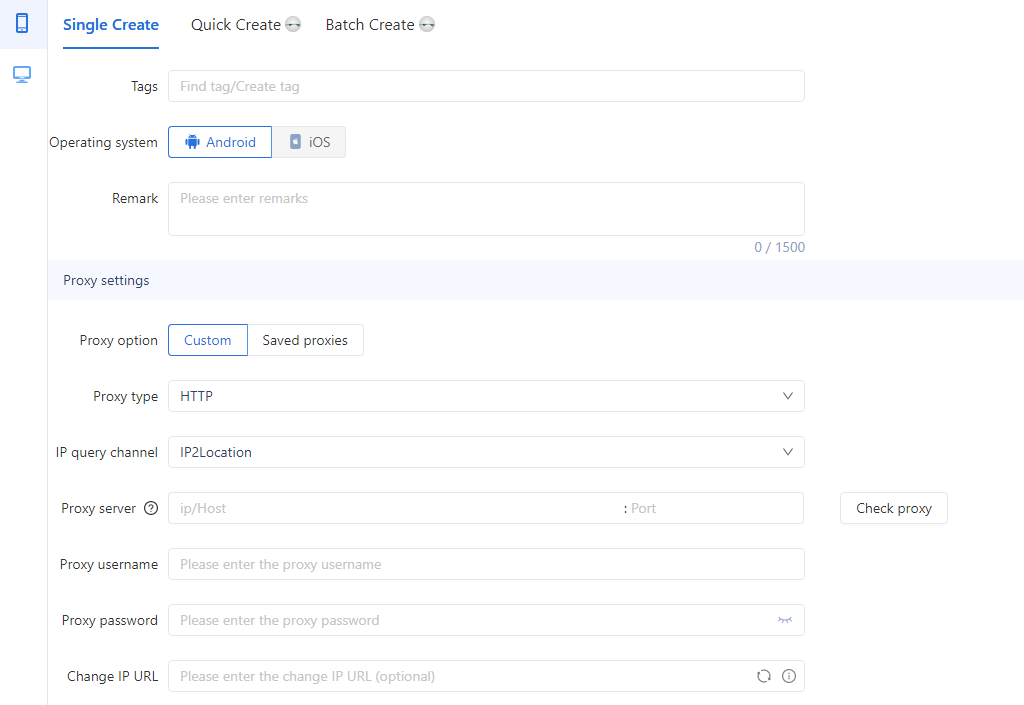
1. Select the proxy type——HTTP
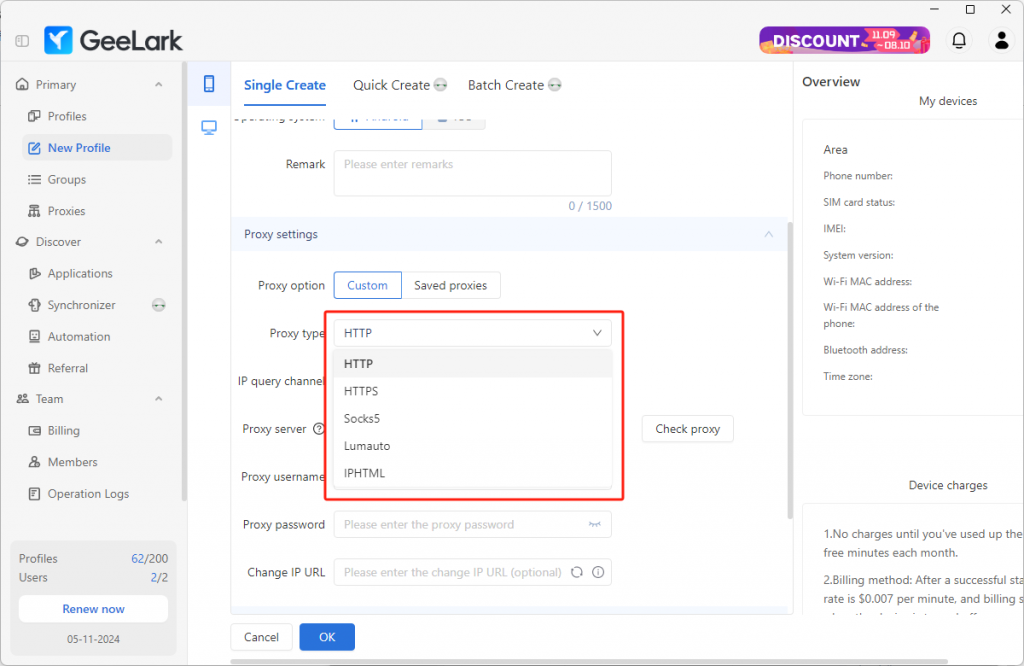
2.Fill in the proxy details, such as the proxy server, port, username, and password in GeeLark to ensure seamless integration with your mobile device.
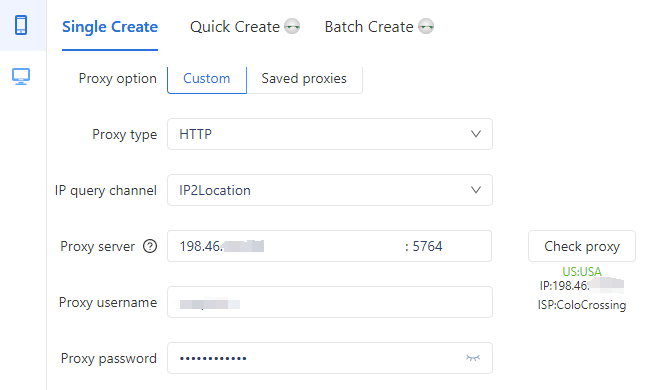
3.Click on “Check Proxy” to verify your connection.
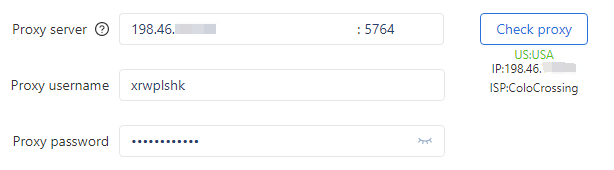
Once everything is set, just hit OK to finalize the settings, and you’re ready to start using your cloud phones!
FAQs
Are HTTP proxies safe?
The safety of an HTTP proxy largely depends on the type of proxy you are using and how you configure it. Transparent proxies, for example, do not hide your IP address and are generally less secure. On the other hand, high anonymity proxies (also known as elite proxies) can offer a higher level of security and privacy by hiding your IP address and encrypting your traffic. It’s important to use a reputable proxy service to ensure your data is not being logged or misused.
What are HTTP proxies used for?
HTTP proxies serve various purposes, including:
Managing Multiple Accounts
Bypassing Geo-Restrictions
Enhancing Security and Privacy
Improving Browsing Efficiency
How do I use an HTTP proxy in GeeLark?
To use an HTTP proxy in GeeLark Cloud Phone, follow these steps:
Create a New Profile: Navigate to “New Profile” in GeeLark.
Configure Proxy Settings: Enter the proxy details such as the proxy server, port number, and authentication credentials if needed.
Save and Apply: Save the settings and apply them to your GeeLark Cloud Phone.
For a detailed guide on setting up HTTP proxies in GeeLark, you can refer to this link.
Subscribe to my newsletter
Read articles from GeeLark directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

GeeLark
GeeLark
The antidetect industry's first mobile antidetect solution that emulates real phones, not just web and mobile browsers. With GeeLark, multi-accounting on the phone becomes easy like never before!