Exploring Advanced Kong Ingress Controller Plugins on EKS
 Heloise Reina Viegas
Heloise Reina Viegas
Introduction
In this blog post, we will explore how to configure and use advanced plugins with the Kong Ingress Controller (KIC) on an Amazon EKS cluster. Specifically, we will delve into JWT Token, Request Transform, and AWS Lambda plugins. These plugins enhance the functionality of your services by adding security, transformation, and integration capabilities.
Prerequisites
Before we begin, ensure you have the following prerequisites:
An AWS account
An EKS cluster set up and running
Kong Ingress Controller installed
You can follow the detailed steps to install KIC from the Kong documentation.
Additionally, deploy any test service and configure an ingress resource. For simplicity, we will skip the Gateway API. Refer to the Kong documentation for more details.
Plugins
We will configure the below plugins:
JWT Token
Request Transform
AWS Lambda
In this article, we will focus on the last three plugins. The first three have been documented in detail by Kong.
JWT Token
JWT (JSON Web Token) Token is used for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. In this section, we will create a JWT token and configure it with Kong.
First, create a secret and key using base64 encoding:
echo -n 'jwtkey' | base64 #key echo -n 'jwtsecret' | base64 #secretCreate Kubernetes secret
apiVersion: v1 kind: Secret metadata: name: alex-jwt namespace: default labels: konghq.com/credential: jwt stringData: algorithm: HS256 secret: and0c2VjcmV0 # base64 for 'jwtsecret' key: and0a2V5 # base64 for 'jwtkey'Create kong consumer resource
apiVersion: configuration.konghq.com/v1 kind: KongConsumer metadata: name: alex-consumer namespace: default username: alex credentials: - alex-jwt #secret-nameCreate the plugin
apiVersion: configuration.konghq.com/v1 kind: KongPlugin metadata: name: jwt-plugin namespace: default plugin: jwtAnnotate ingress or service resource
kubectl annotate ingress echo konghq.com/plugins=jwt-pluginUse jwt.io to create a JWT token. In the CLI, run:
date +%s echo $((1697539200 + 3600)) # use this as the value for “exp” in the payloadThe payload will be:
{ "iss": "and0a2V5", # key "sub": "1234567890", "name": "alex", "iat": 1516239022, "exp": 1697539200 # Example expiration time }For the signature, paste the secret encoded value from step 1.
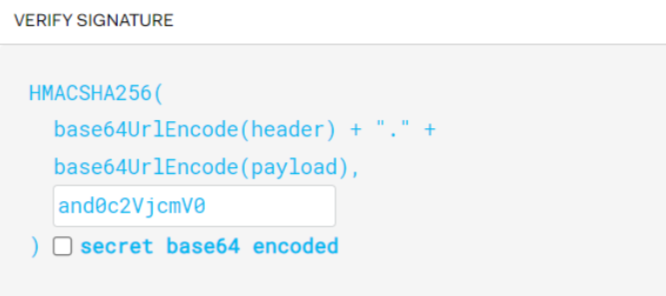
Test Using the Token
curl $PROXY_IP/echo?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhbmQwYTJWNSIsInN1YiI6IjEyMzQ1Njc4OTAiLCJuYW1lIjoiYWxleCIsImlhdCI6MTUxNjIzOTAyMiwiZXhwIjoxNzI5MTg0NjA1fQ.mmQVyqBNpOCJogpioHEqTTciUbPWQm56ipwaMKyseT4Note:
export PROXY_IP=$(kubectl get svc --namespace kong kong-gateway-proxy -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')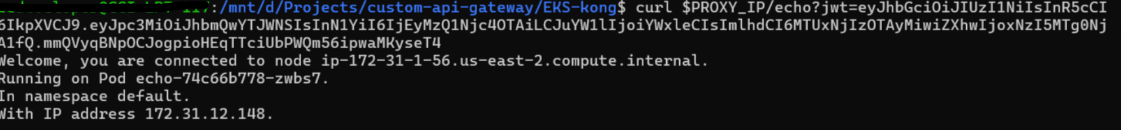
Request Transform
Request Transform plugin allows you to modify requests before they reach your upstream services. You can add, remove, or replace headers and other request properties.
Create the Plugin
apiVersion: configuration.konghq.com/v1 kind: KongPlugin metadata: name: request-transformer config: add: headers: - "x-added-header:added-value" remove: headers: - "x-remove-header" replace: headers: - "x-replace-header:replaced-value" plugin: request-transformerAnnotate ingress
kubectl annotate ingress echo konghq.com/plugins=request-transformer # we can annotate multiple plugins eg. # kubectl annotate ingress echo konghq.com/plugins=jwt-plugin,request-transformer --overwriteTest
curl -i -H "x-remove-header: to-be-removed" -H "x-replace-header: old-value" $PROXY_IP/echo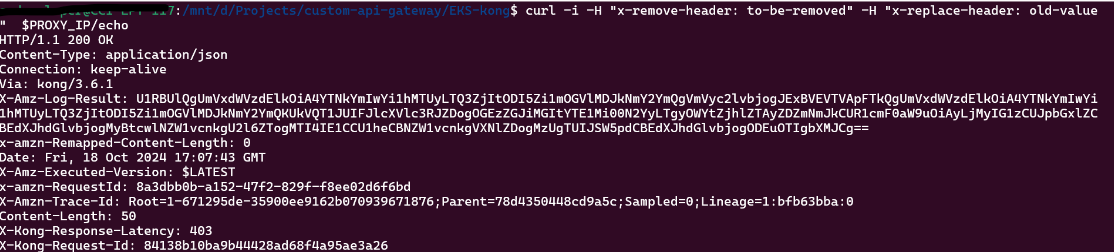
AWS Lambda
AWS Lambda plugin allows you to invoke AWS Lambda functions from within Kong. This is useful for integrating serverless functions into your API gateway.
Follow the steps described in the AWS Lambda Plugin documentation.
Create the plugin
apiVersion: configuration.konghq.com/v1 kind: KongPlugin metadata: name: aws-lambda-example plugin: aws-lambda config: aws_region: "us-east-2" function_name: "MyLambda" #requiredAnnotate ingress
kubectl annotate ingress echo konghq.com/plugins=aws-lambda-exampleTest
curl -i $PROXY_IP/echo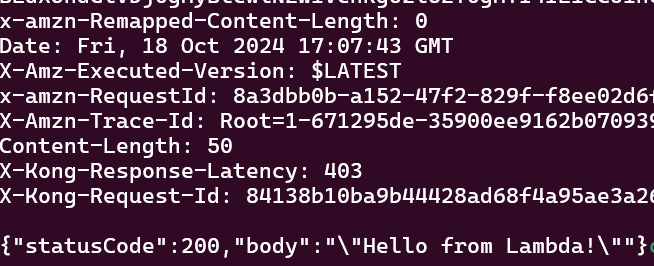
Conclusion
In this blog post, we explored how to configure and use advanced plugins with the Kong Ingress Controller on an Amazon EKS cluster. We covered the JWT Token, Request Transform, and AWS Lambda plugins, which enhance your services by adding security, transformation, and integration capabilities. By leveraging these plugins, you can significantly improve the functionality and flexibility of your API gateway.
Feel free to experiment with these plugins and explore other capabilities offered by Kong. Happy configuring!
Subscribe to my newsletter
Read articles from Heloise Reina Viegas directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Heloise Reina Viegas
Heloise Reina Viegas
Exploring DevOps tools and practices.