🚀Day-7: How I Configured AWS VPC Peering Between Mumbai and Virginia Regions 🚀
 Santhosh Haridass
Santhosh Haridass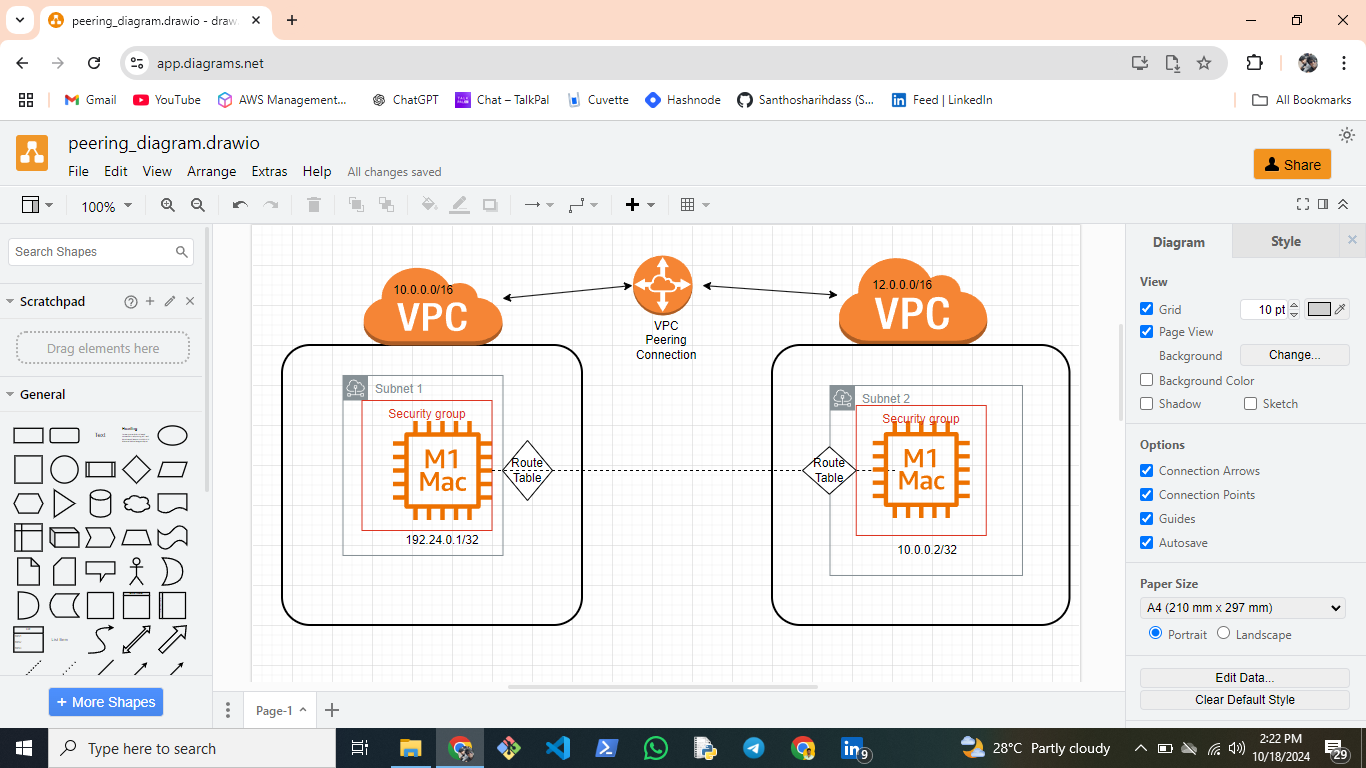
Step Process:
In this post, I’ll walk you through the step-by-step process of configuring VPC Peering between two different AWS regions: Mumbai (ap-south-1) and Virginia (us-east-1). VPC Peering enables private communication between VPCs across regions, creating a robust and secure network architecture.
Step-by-Step Breakdown:
1. Create VPCs in Different Regions
First, I created two separate VPCs in the Mumbai and Virginia regions.
Ensured both VPCs had distinct CIDR blocks to avoid IP conflicts, which is critical for a successful VPC Peering connection.
2. Set Up Subnets and Route Tables
Inside each VPC, I defined public and private subnets to segment the network properly.
Associated each subnet with appropriate route tables for managing traffic. This helps in directing traffic to the correct destinations within and between VPCs.
3. Attach Internet Gateways
For both VPCs, I attached an Internet Gateway to enable instances in public subnets to access the internet.
This step ensures that public-facing instances can communicate with the internet while maintaining the isolation of private subnets.
4. Establish the VPC Peering Connection
Next, I initiated a VPC Peering request from the Mumbai VPC and accepted it in the Virginia VPC.
This established a private link between the two VPCs, allowing them to communicate over private IP addresses.
5. Update Route Tables
After the peering connection was established, I updated the route tables in both VPCs.
Added routes in the Mumbai VPC pointing to the Virginia VPC’s CIDR block and vice versa. This ensures that traffic between the VPCs is routed through the VPC Peering connection.
6. Configure Security Groups
To allow communication between instances in the two VPCs, I configured security groups to permit inbound and outbound traffic over private IPs.
Ensured the security groups allow the necessary ports for the services running on the instances.
7. Test the Connection
I launched EC2 instances in both the Mumbai and Virginia VPCs.
Used their private IP addresses to test communication between them, confirming that the peering connection was working perfectly.
8. Internet Access for Public Subnets
For instances in the public subnets, I verified their internet access by ensuring the route tables had entries pointing to the Internet Gateway.
Instances in the private subnets continued to communicate with each other over the VPC peering connection without internet access.
Key Takeaways:
VPC Peering is an excellent solution for securely connecting VPCs across different AWS regions.
It allows for scalable, multi-region architectures without the need for a VPN or additional network configurations.
With proper route table updates and security group settings, cross-region communication is straightforward and efficient.
Future Enhancements:
Integrate a multi-region failover strategy using Route 53 for better redundancy.
Explore advanced network security configurations like Network ACLs to further tighten security.
Subscribe to my newsletter
Read articles from Santhosh Haridass directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Santhosh Haridass
Santhosh Haridass
🚀 𝐀𝐛𝐨𝐮𝐭 𝐌𝐞 "Hi, I'm Santhosh Haridass, a DevOps student passionate about cloud computing and automation. I'm currently learning AWS, Linux, Docker, and CI/CD pipelines, with a focus on automating workflows and building scalable solutions. My goal is to become a skilled DevOps/Cloud engineer, and I'm excited to share my learning journey and projects with the community."