VPC Tutorial #5: AWS Private Links: Step-by-Step Guide for Setting Up an Endpoint Service
 Shivprasad Waghmare
Shivprasad Waghmare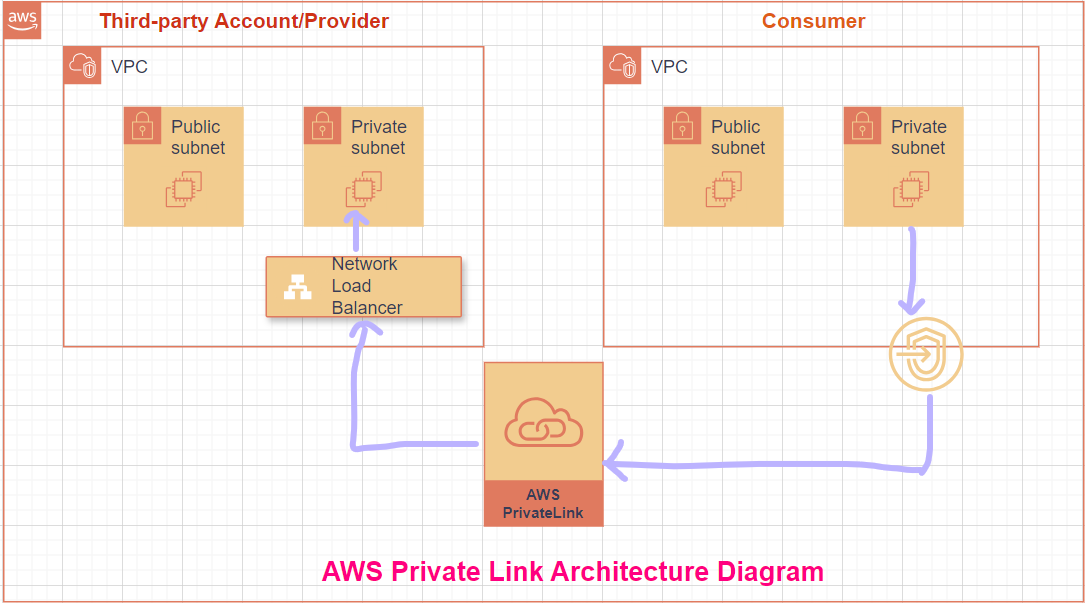
Introduction: In this guide, I will walk you through setting up an AWS Endpoint Service using Private Link. AWS Private Link allows you to access services securely over a private network, without exposing traffic to the internet.
Table of contents -
VPC & components
EC2
NLB & Target group
Endpoint service
Endpoint interface
Create Provider VPC & components
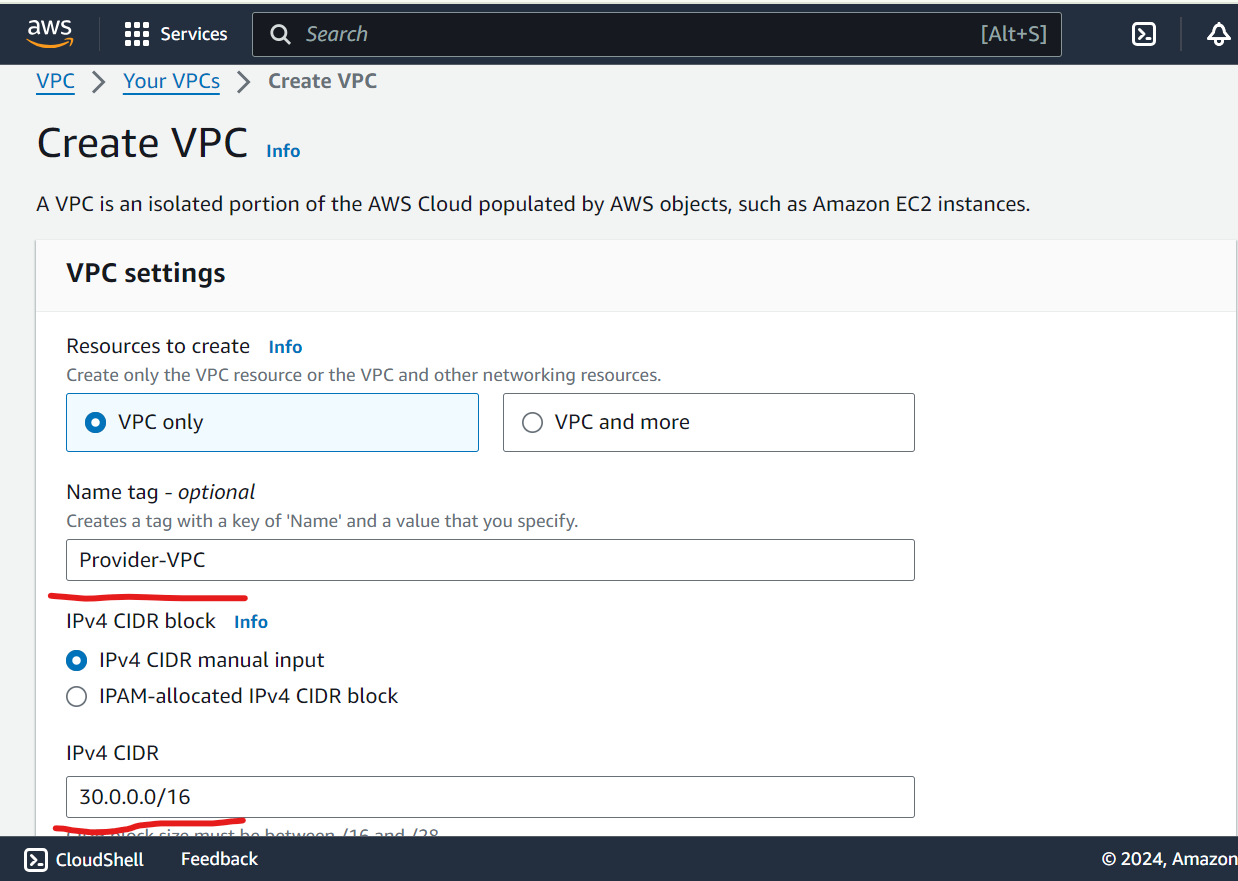
Create VPC
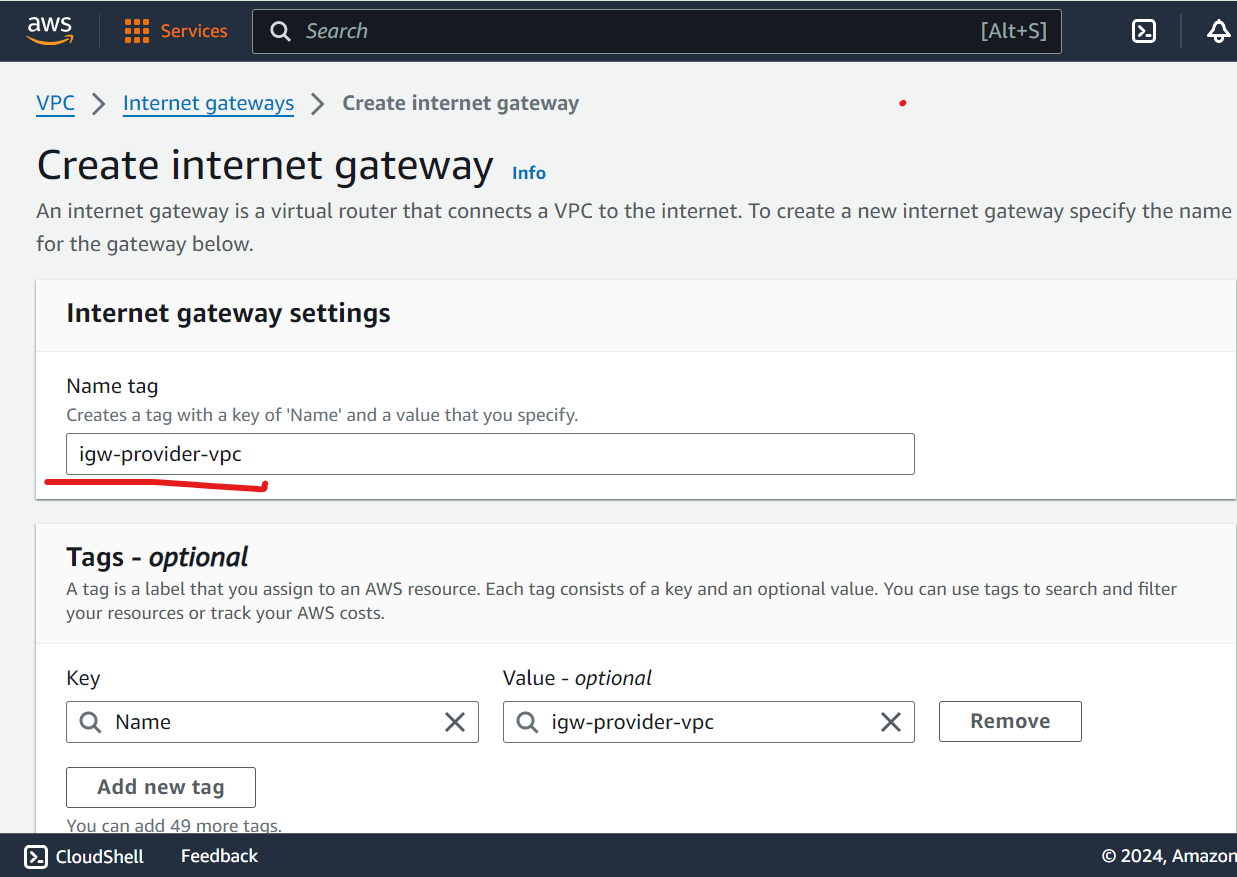
Create IGW and attach to VPC
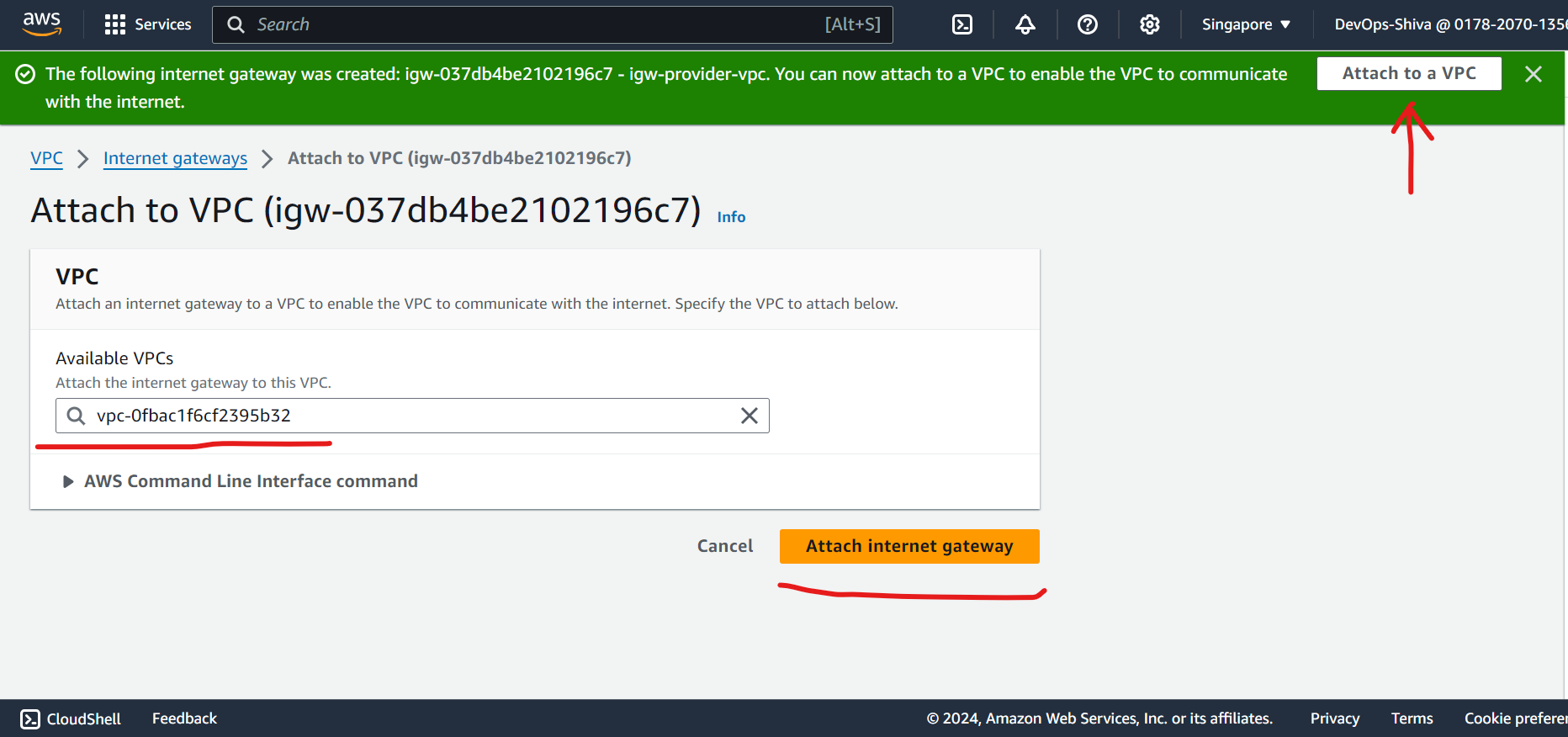
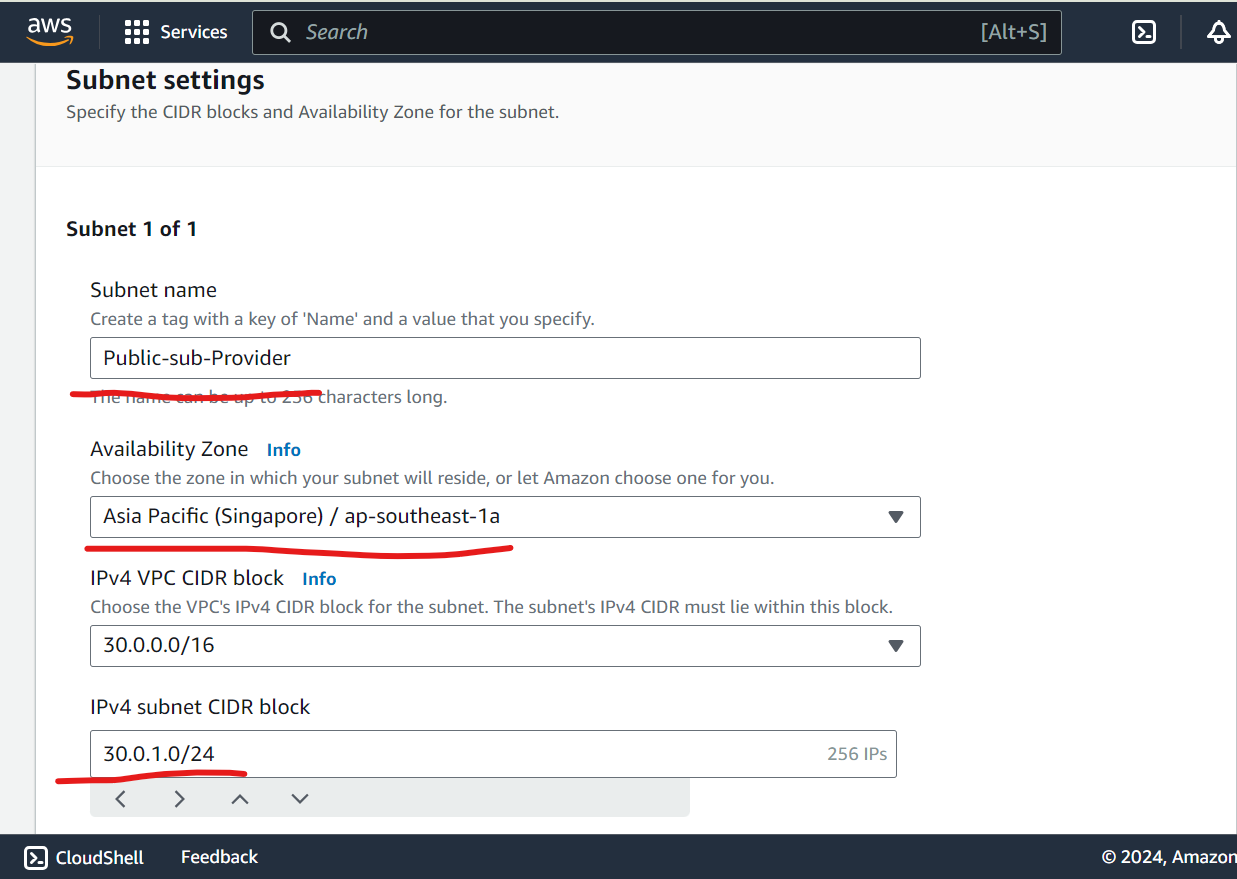
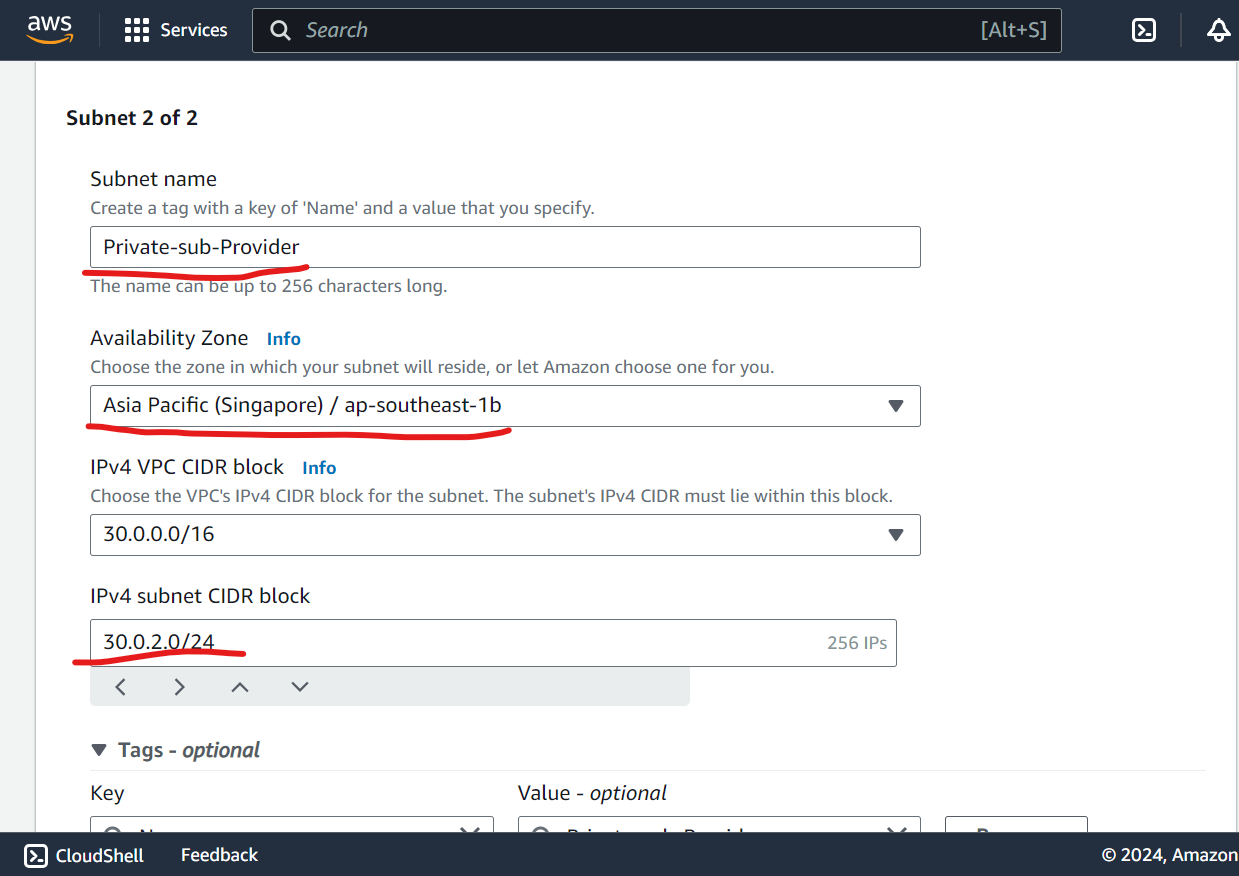
Create Public & Private Subnet
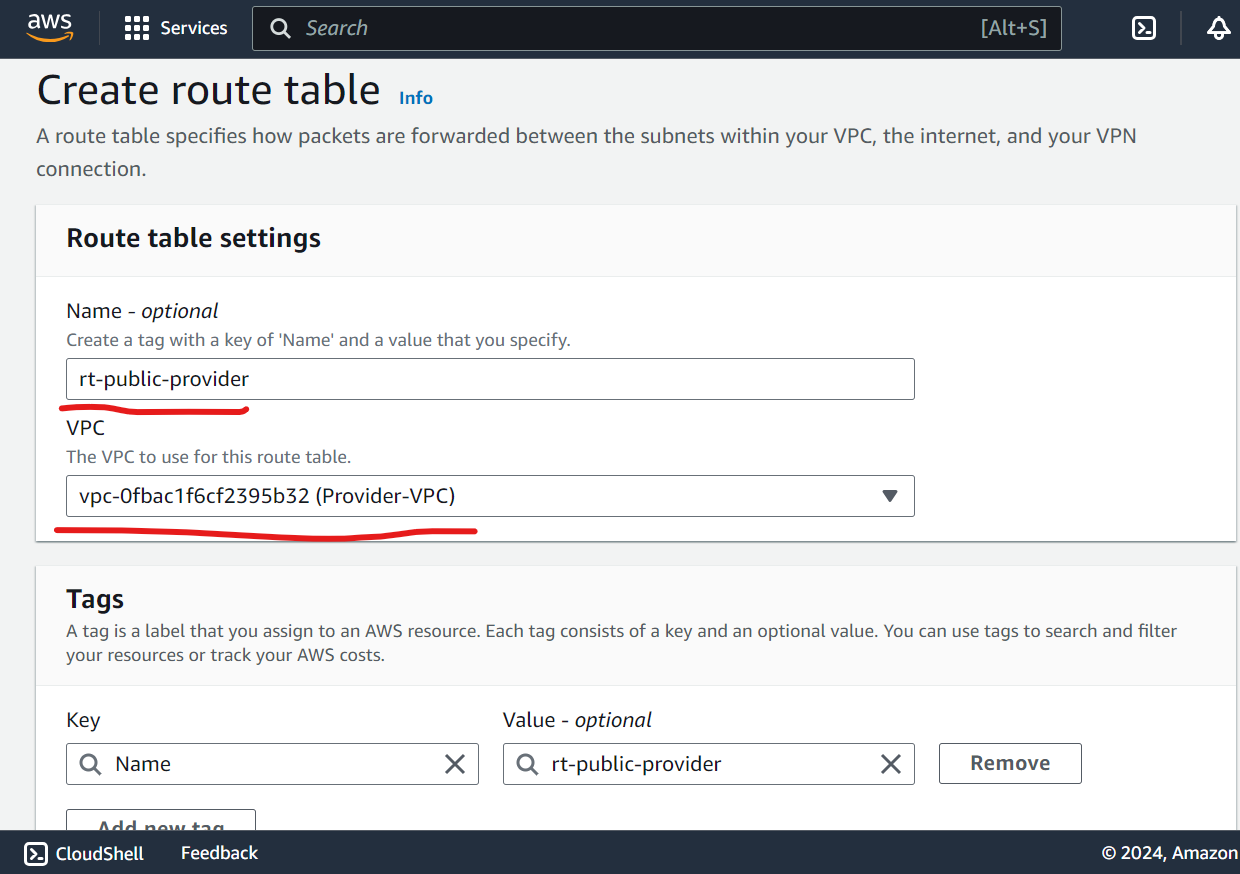
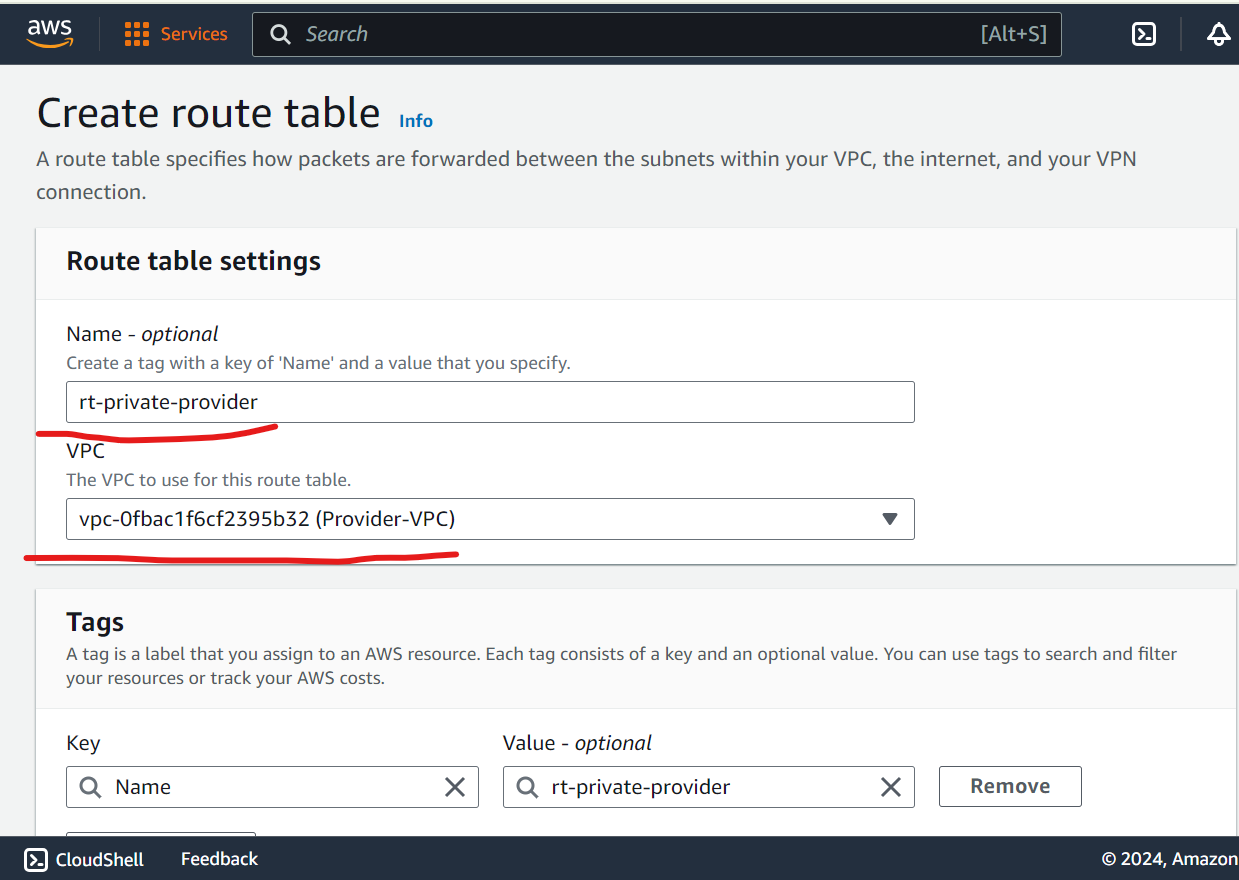
Create Public and Private route Table
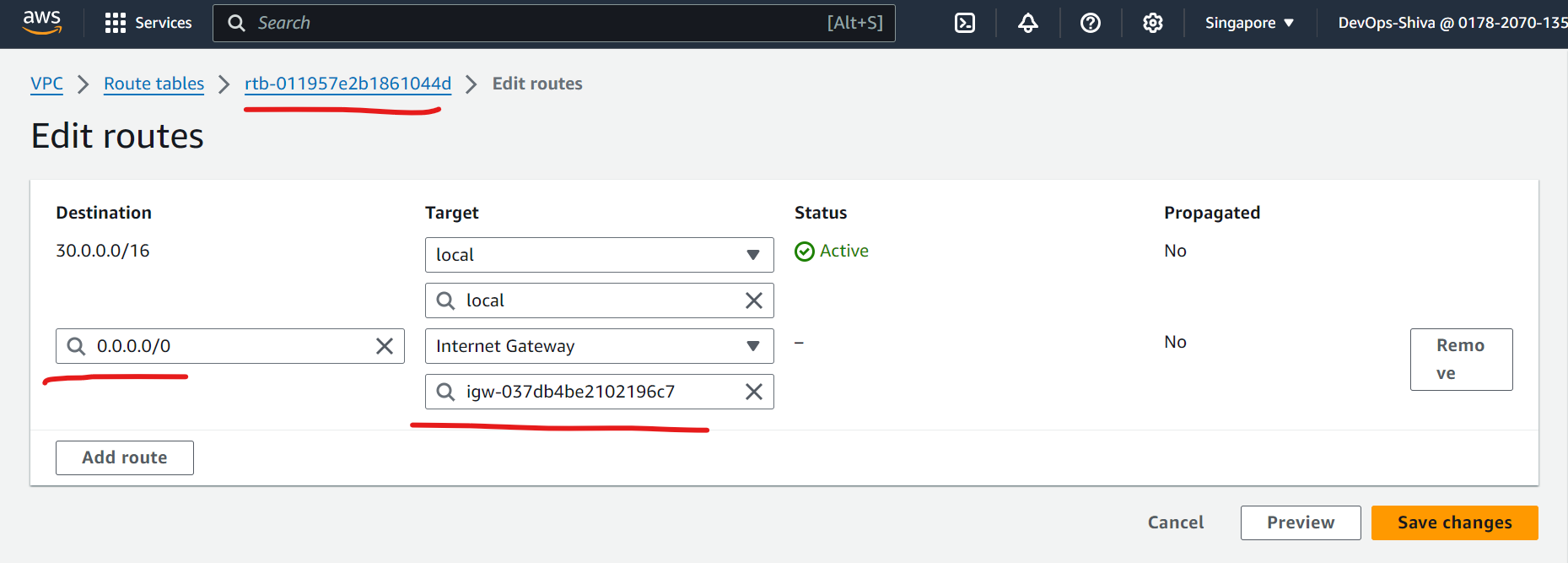
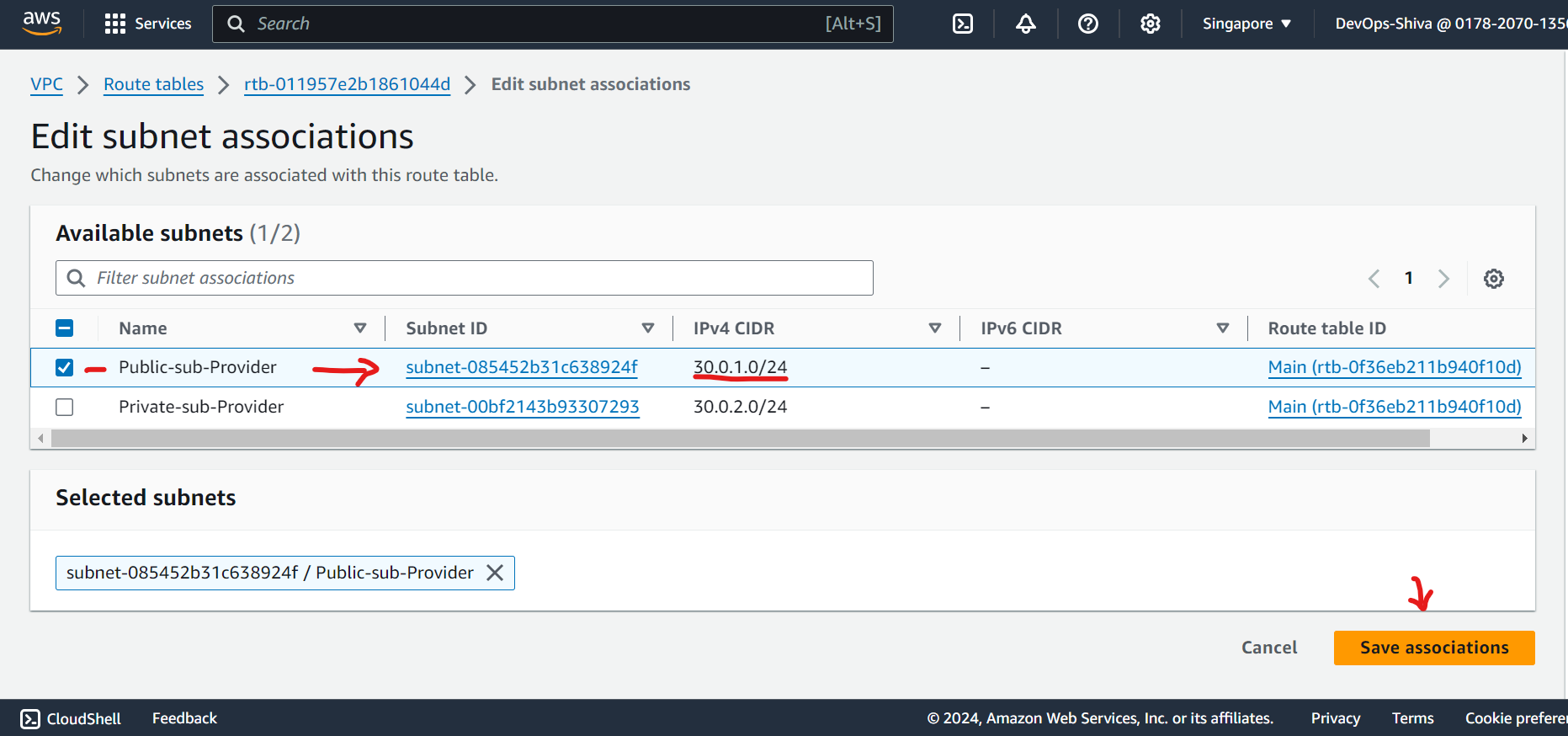
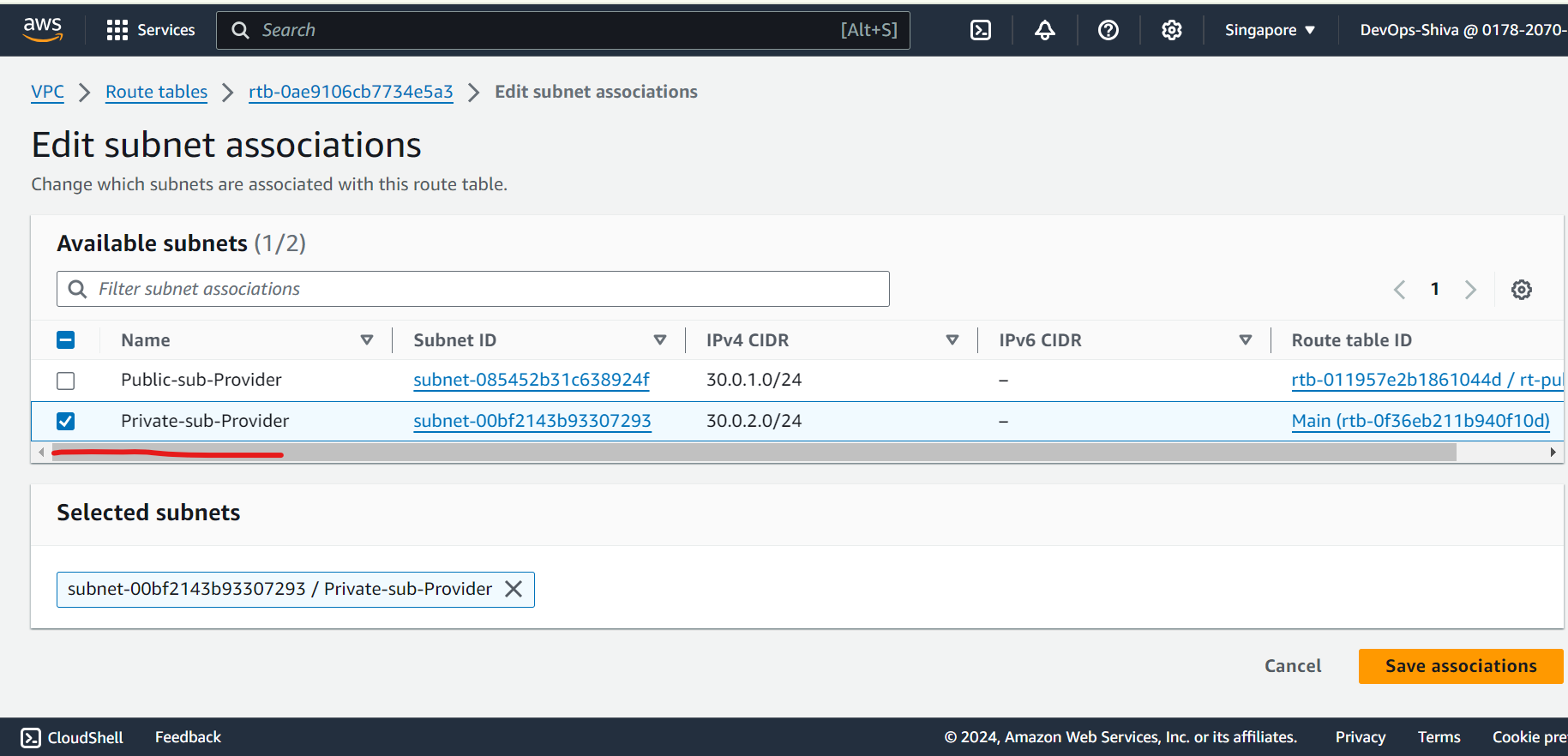
Edit routes and attach subnets association.
Create and attach NAT gateway
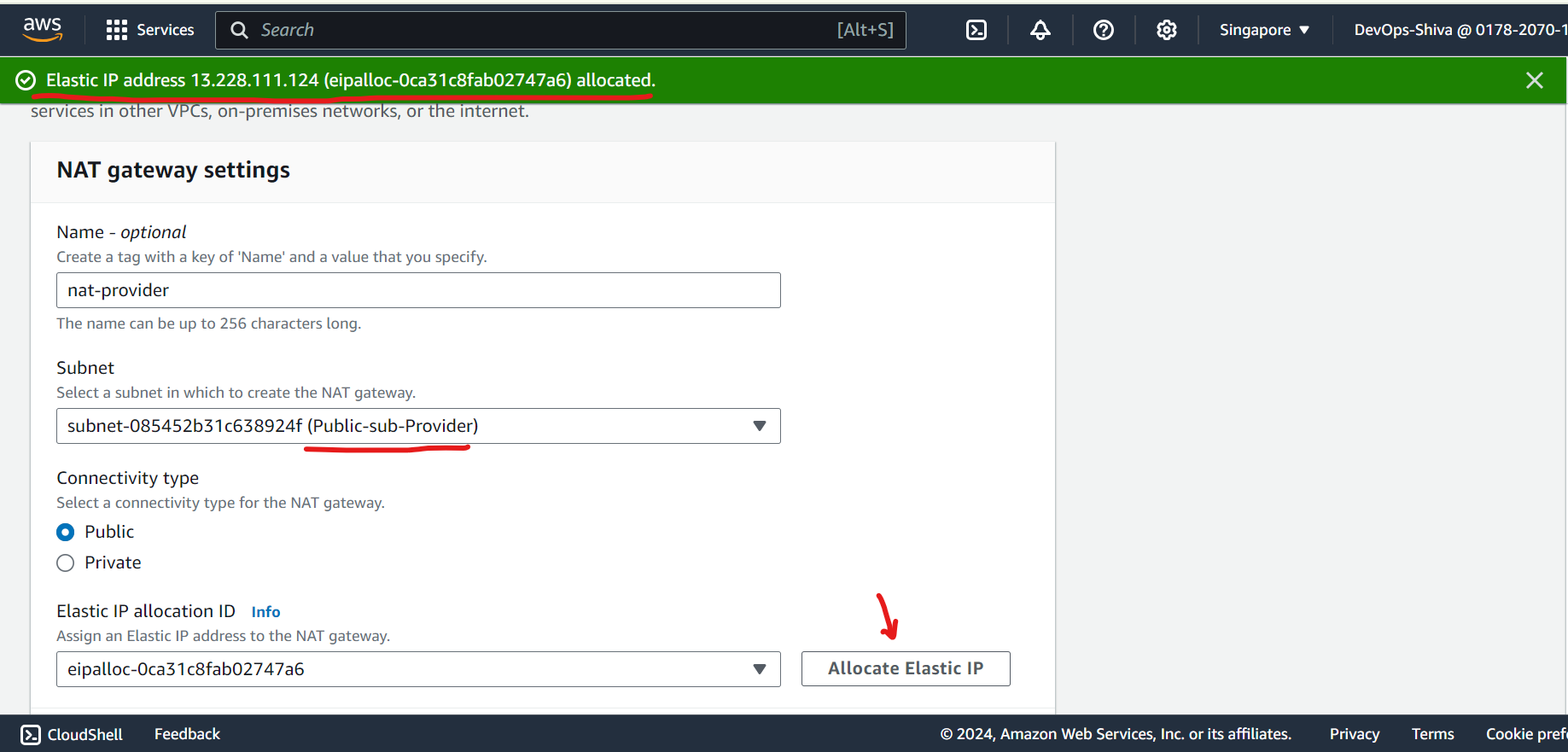
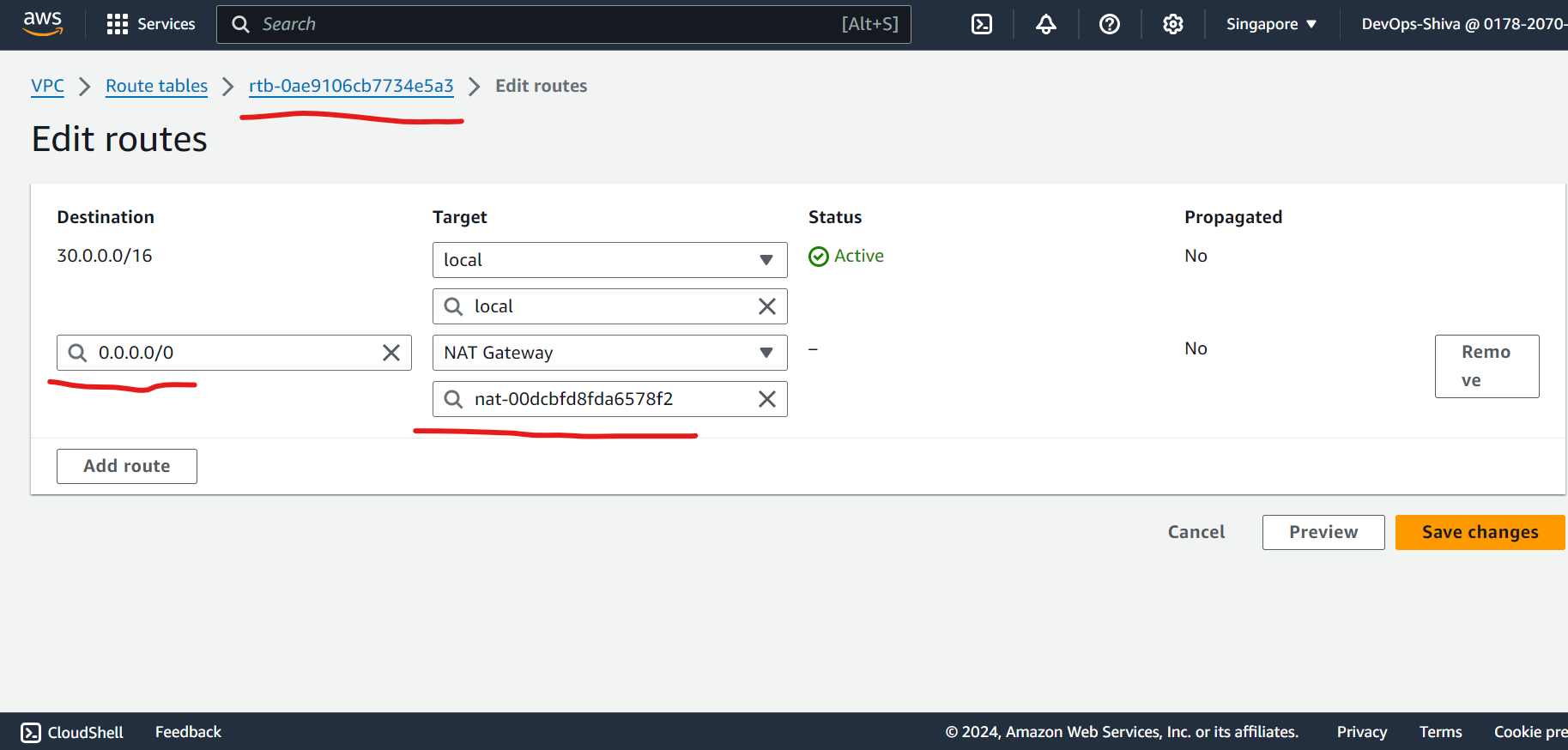
- Note - Immediately remove NAT gateway and release E-IP once you installed nginx web server to private instance. Otherwise the purpose of the demo won’t be fulfill.
Launch Public & Private EC2 Instances - Provider
Create Public EC2 instance - I will use same key pair across demo(not a best practice in production), Ubuntu 22.04, T2 micro instance, SG - open port 22.
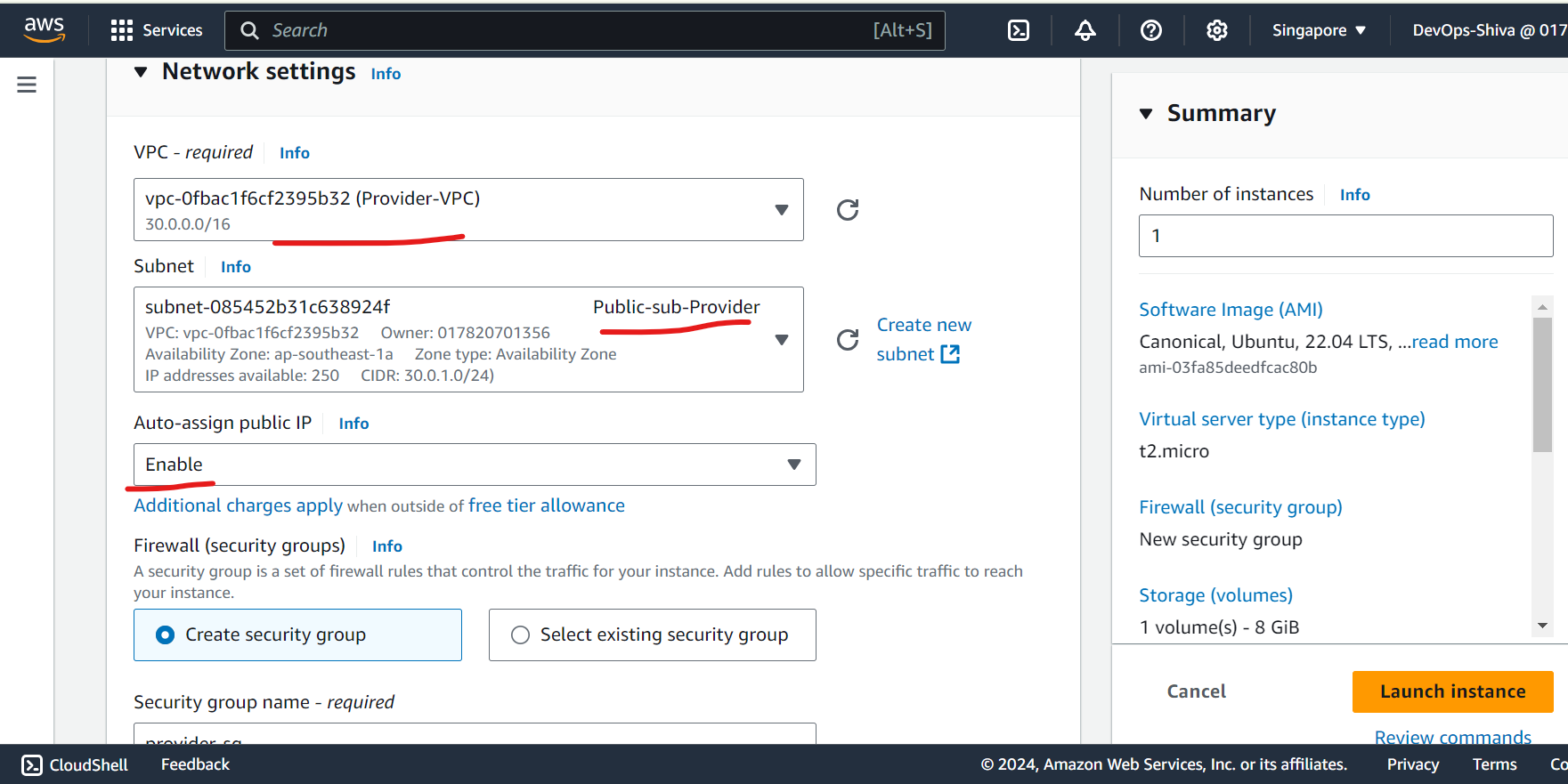
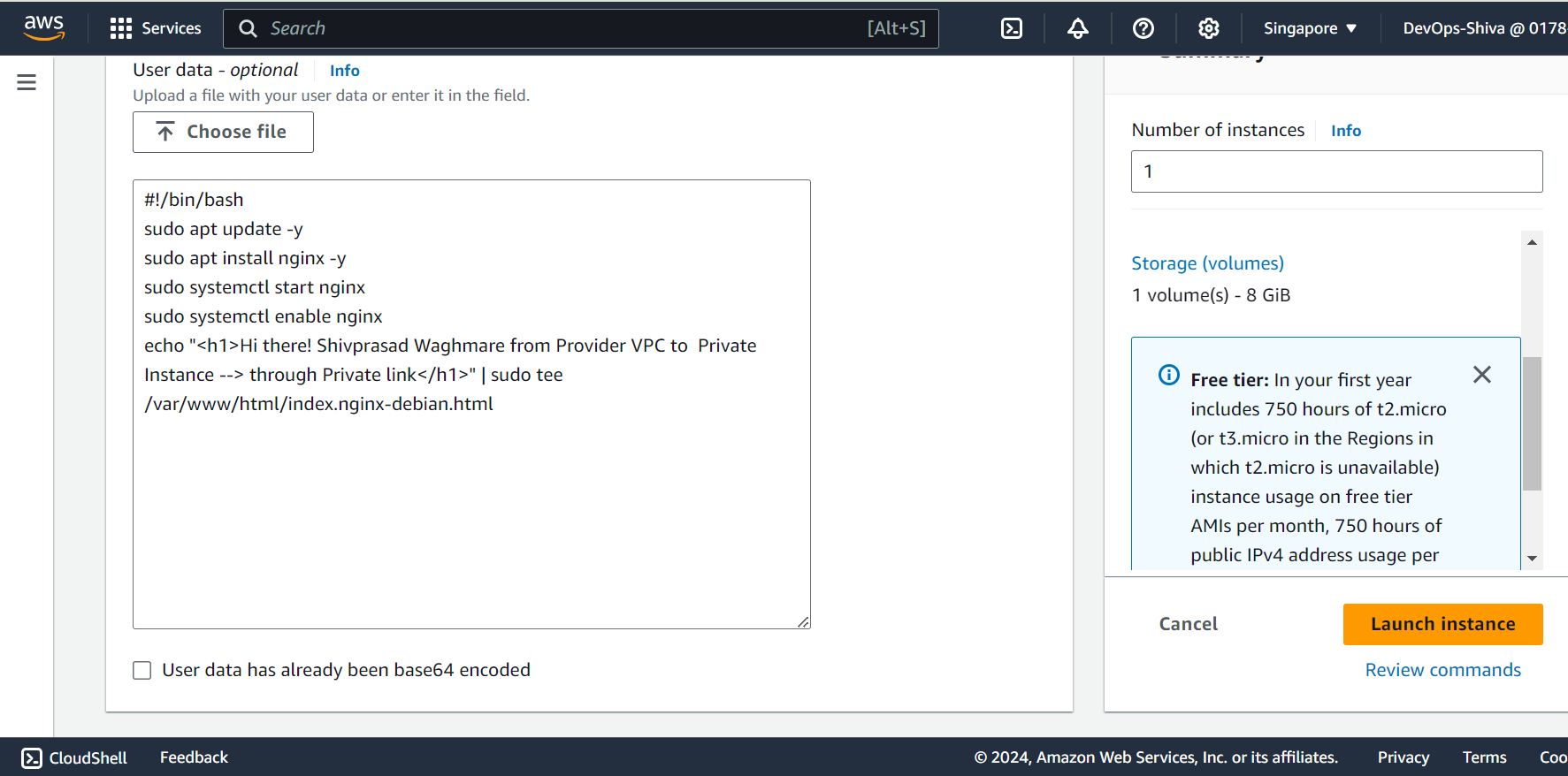
Create Private EC2 instance - will use same key pair across demo(not a best practice in production), Ubuntu 22.04, T2 micro instance, SG - open port 22. Add nginx user data script to test the through browser.
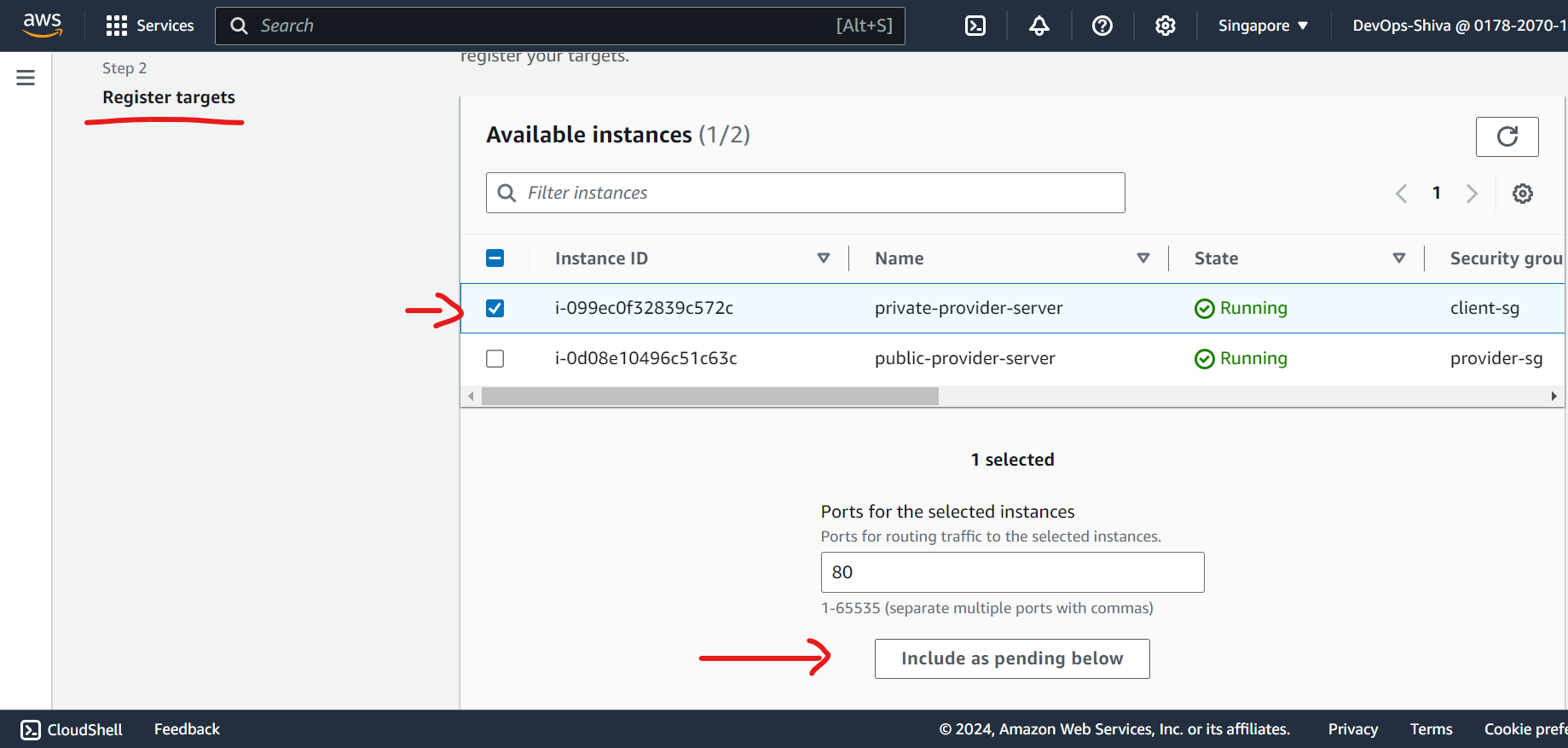
Create NLB and TG
Create Target group - a logical grouping of instances.
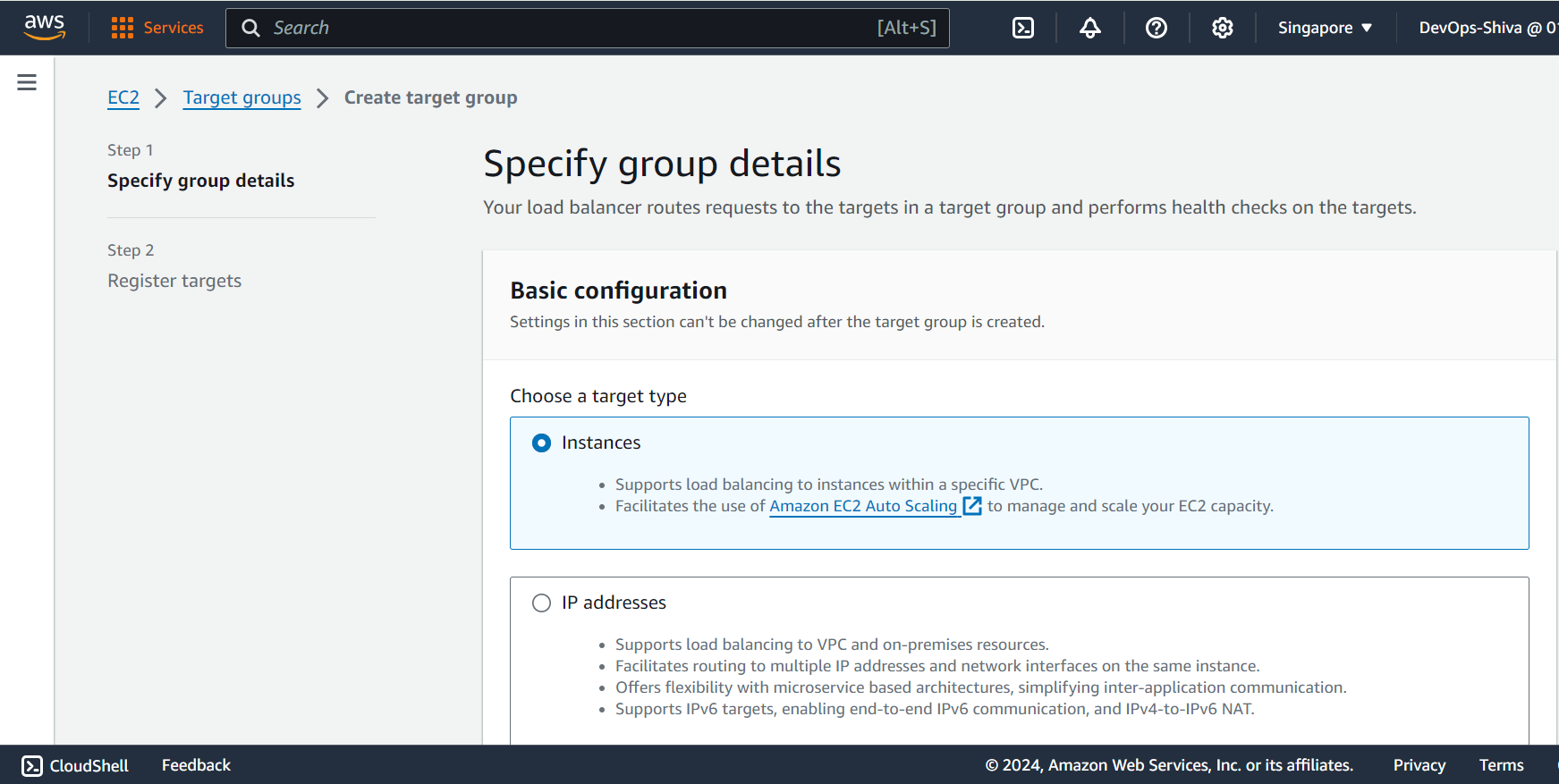
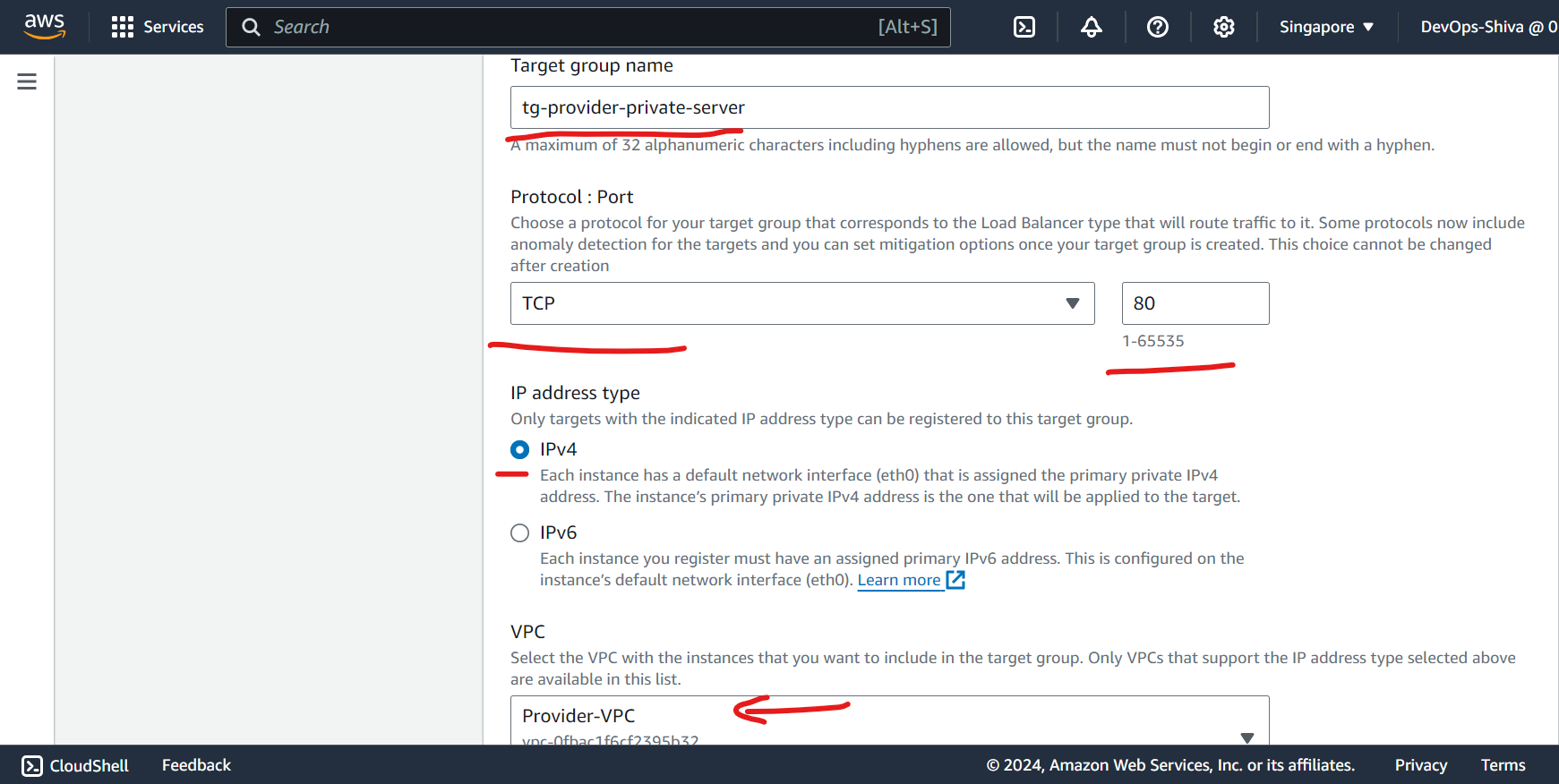
Create NLB - Keep a internal facing, IPv4 enabled, attach private subnet, in sg - open port 80 as well , add listeners as follows and keep remaining default and heat enter .
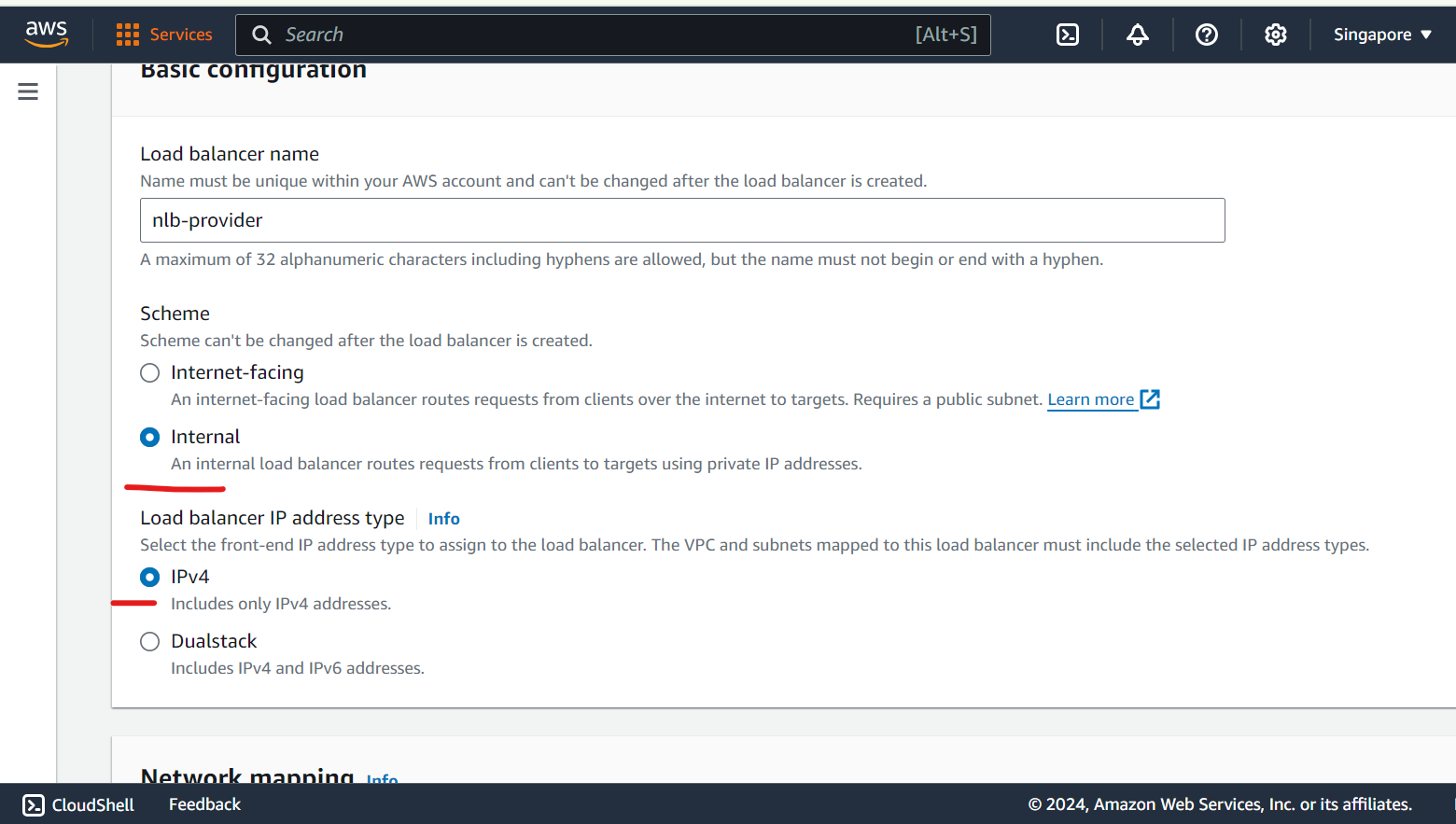
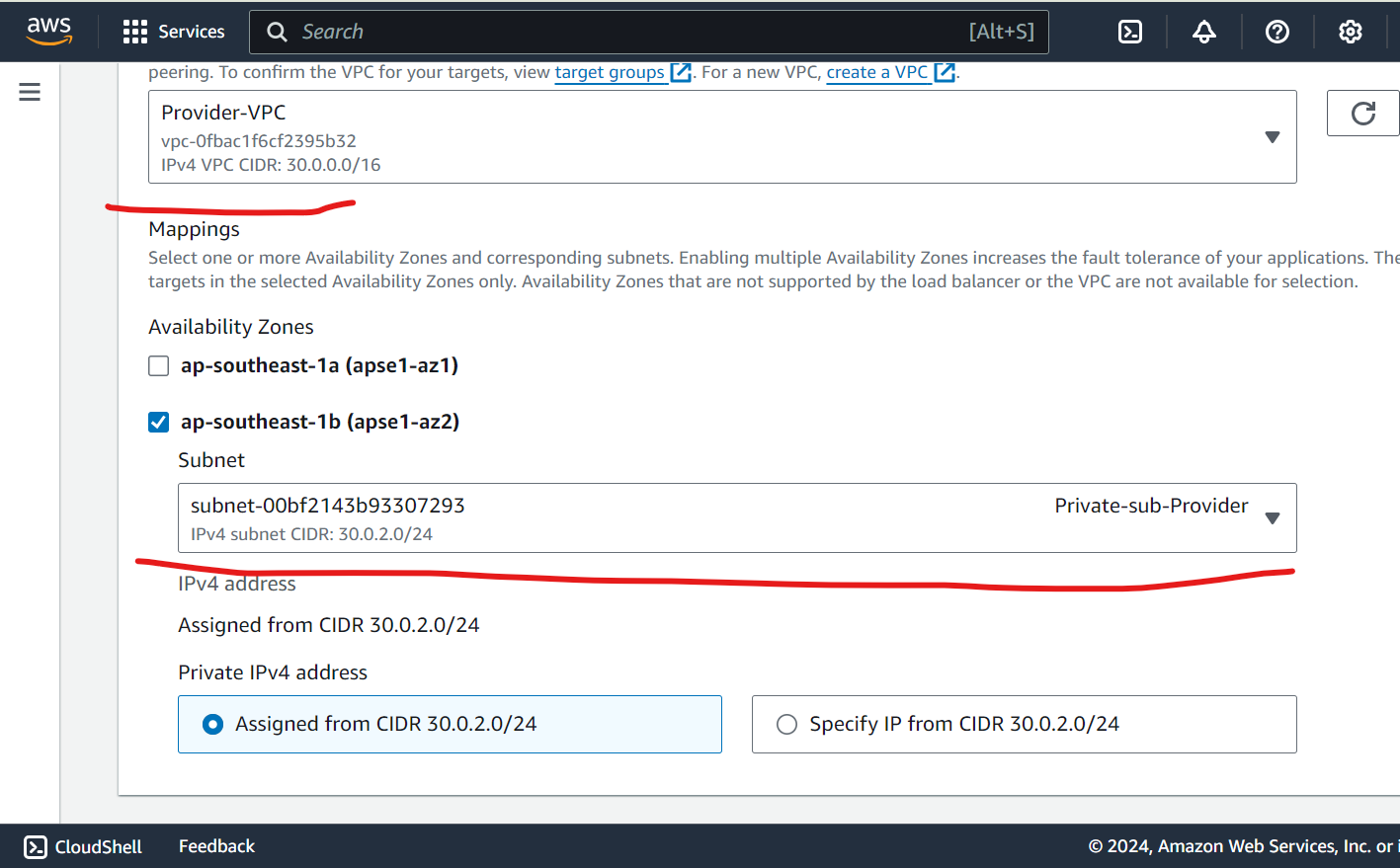
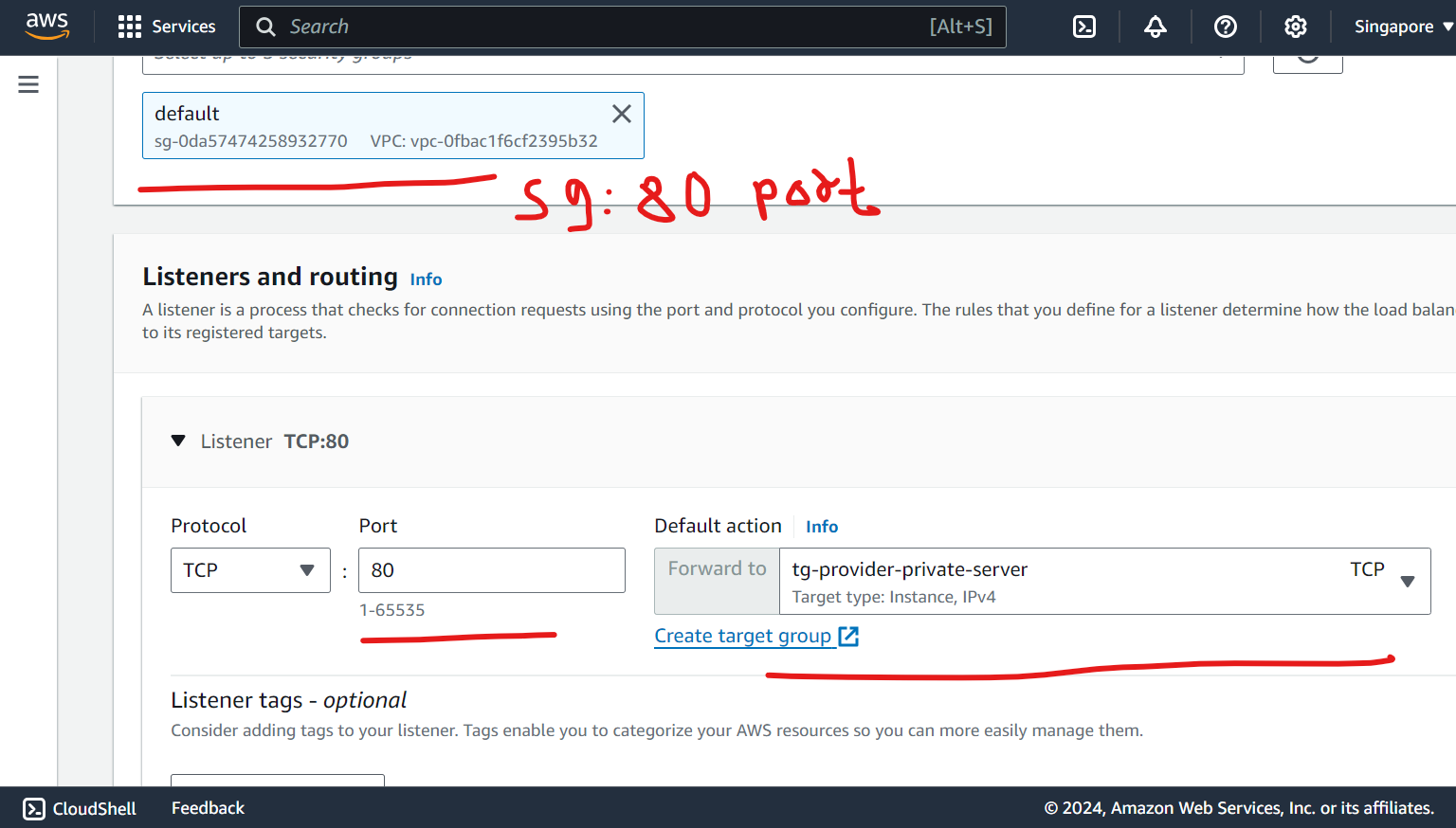
Wait some time for nlb to up and running before Endpoint service create.
Create Endpoint service
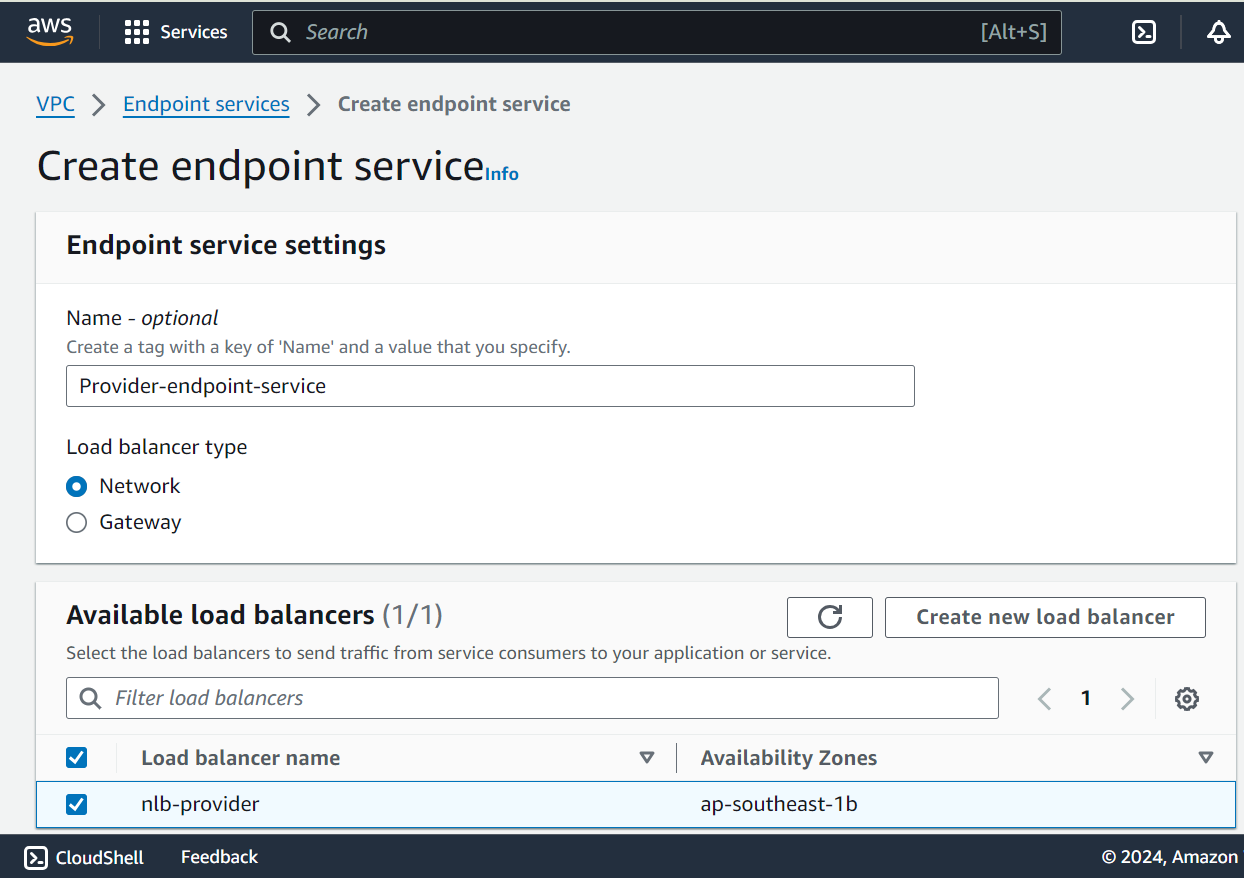
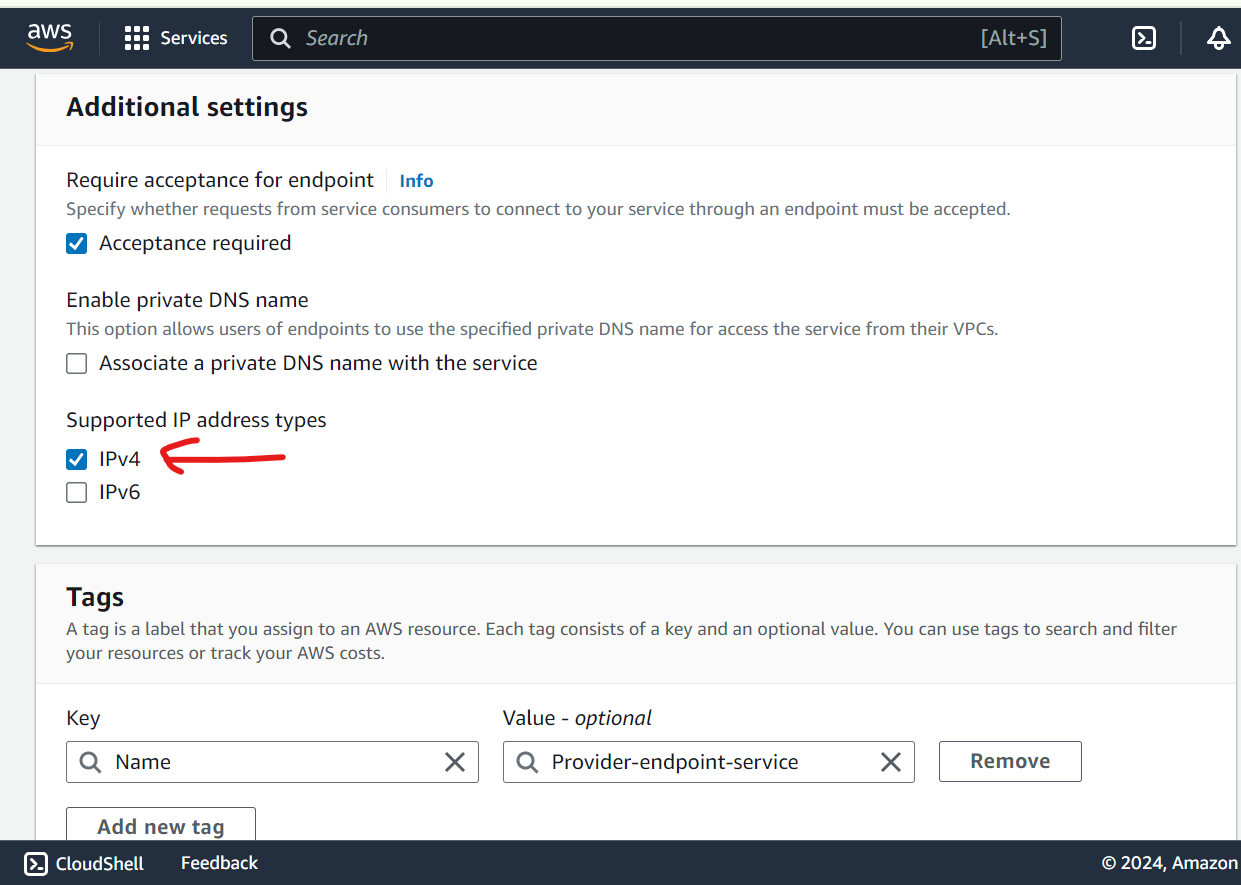
Create Client VPC & components
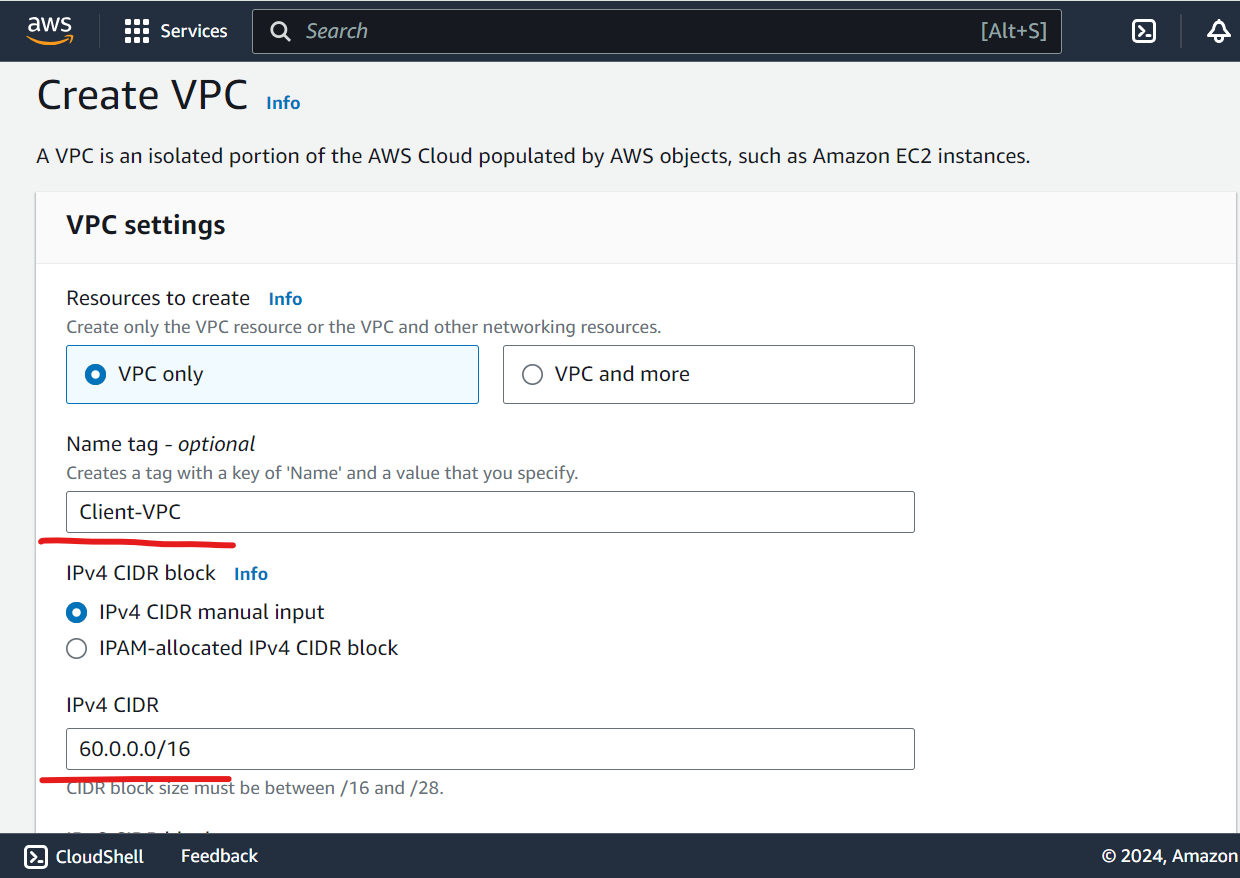
Create VPC
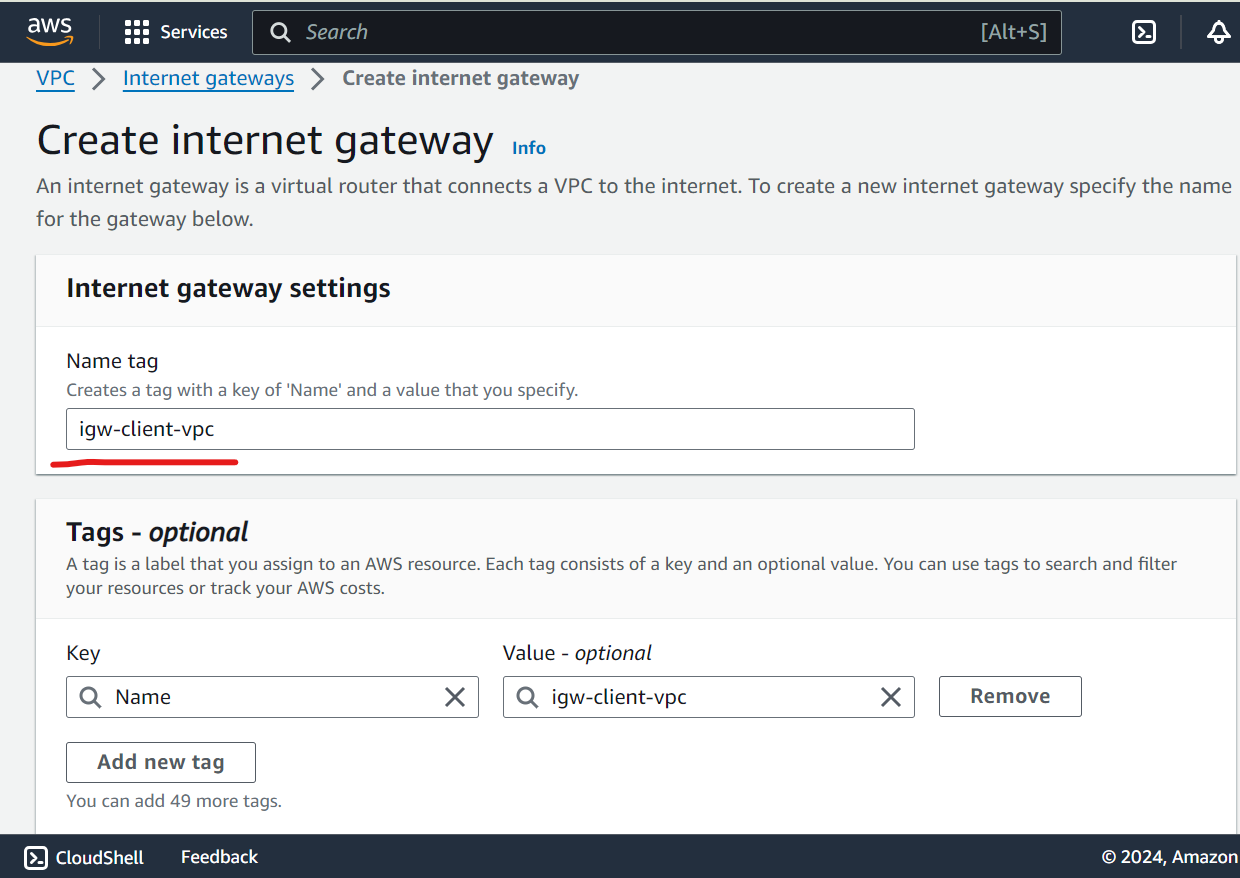
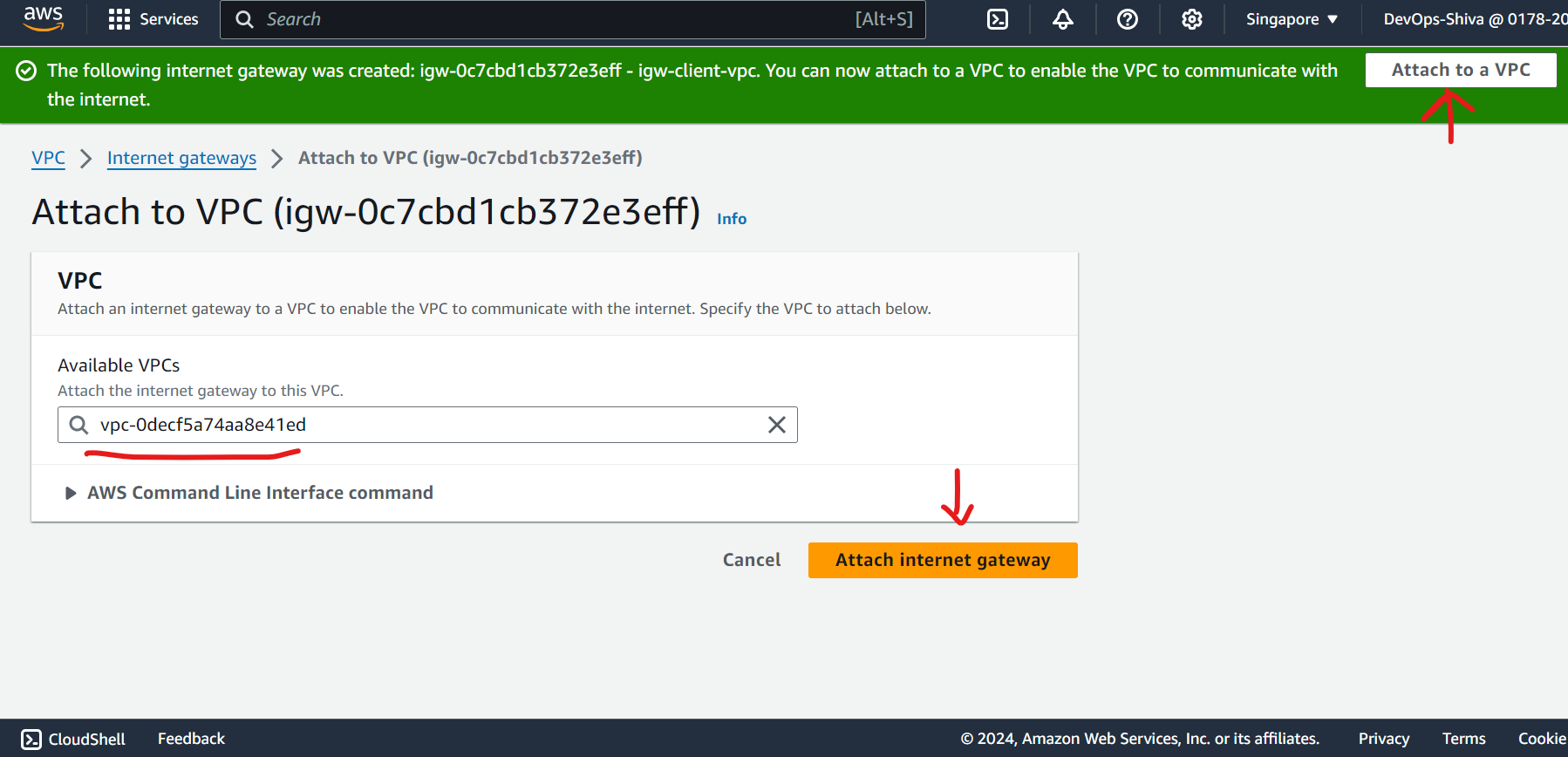
Create IGW and attach to VPC
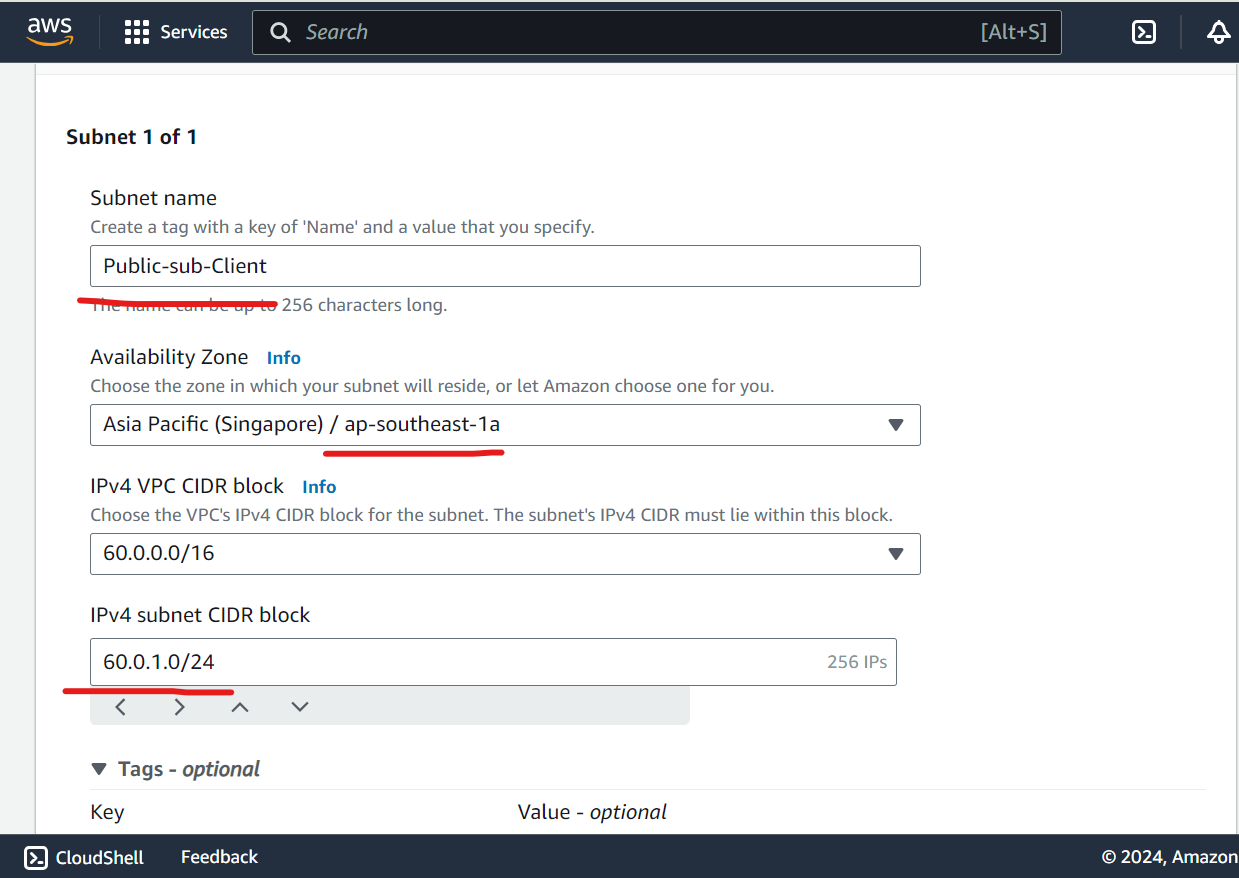
Create Public & Private Subnet
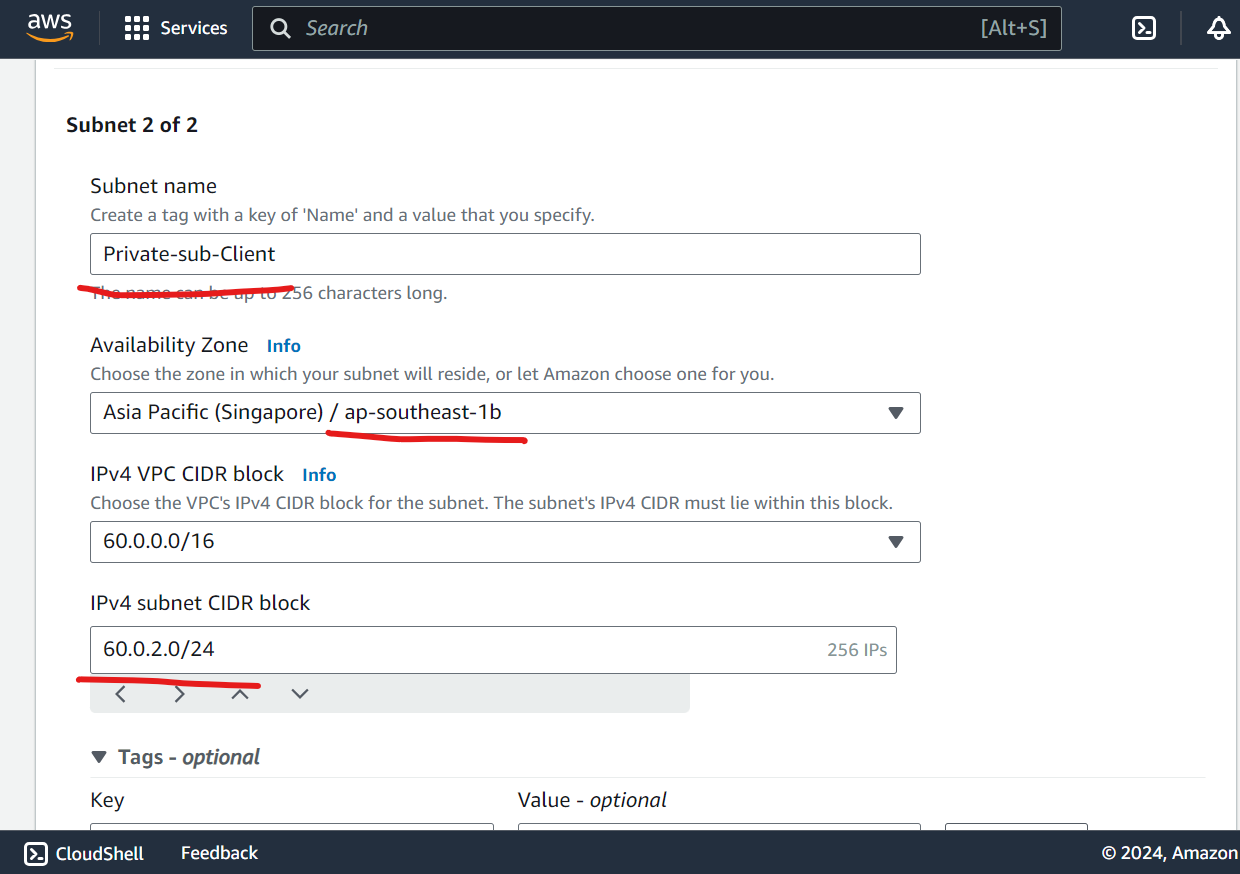
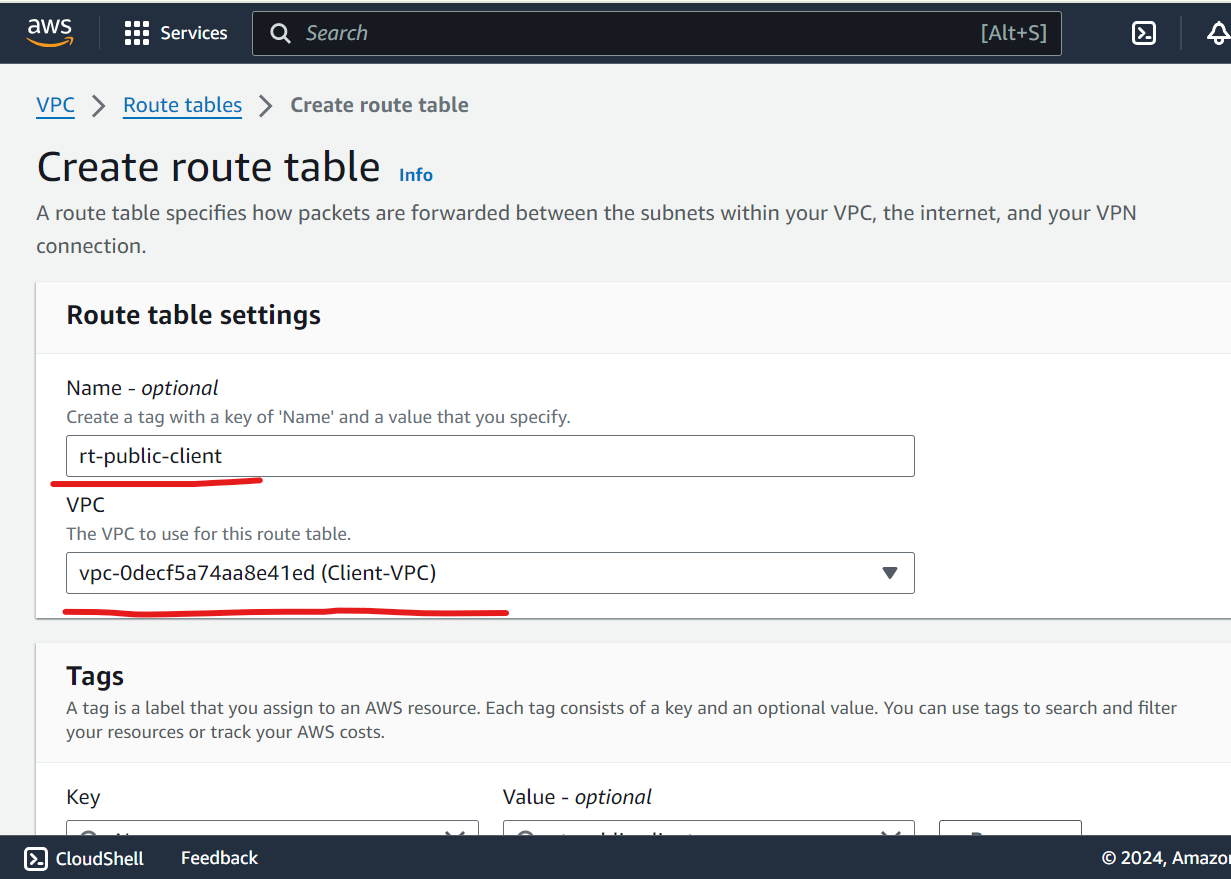
Create Public and Private route Table
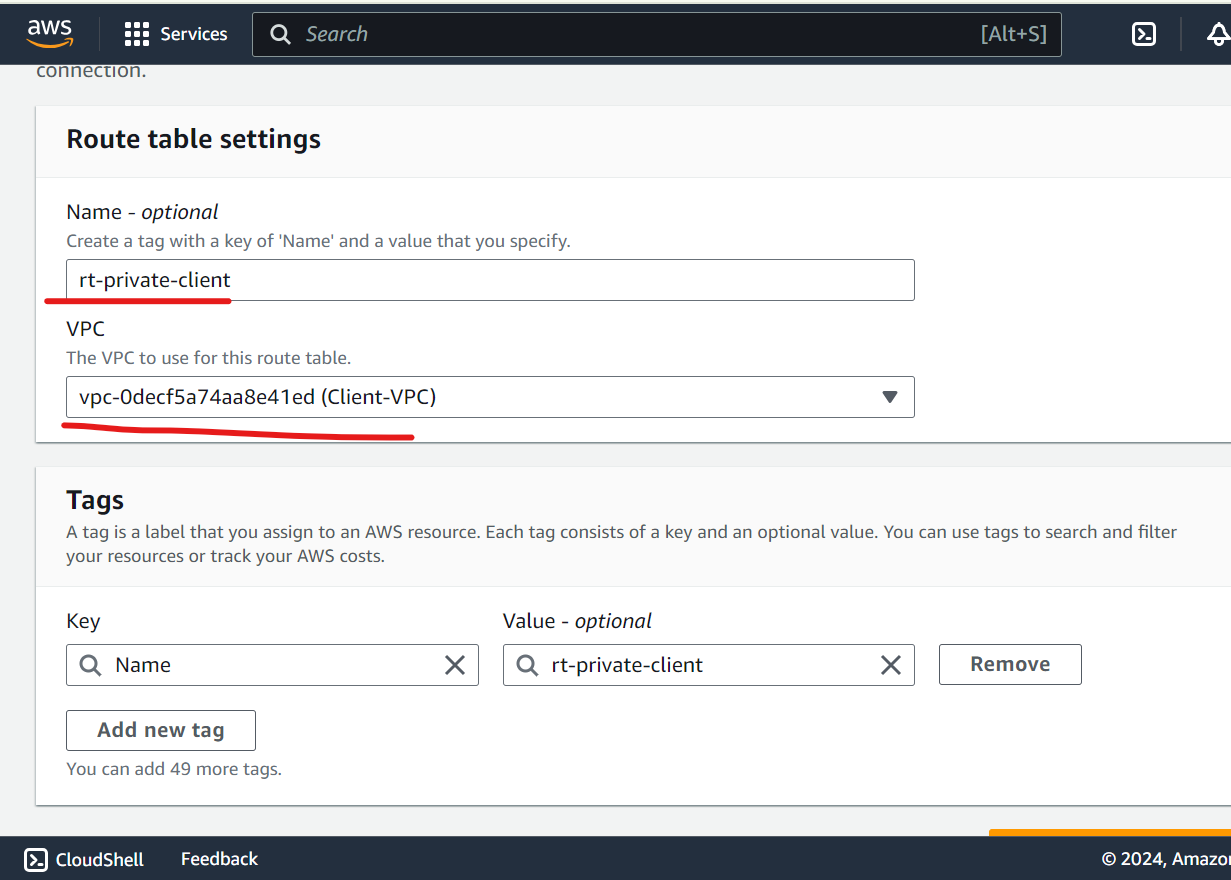
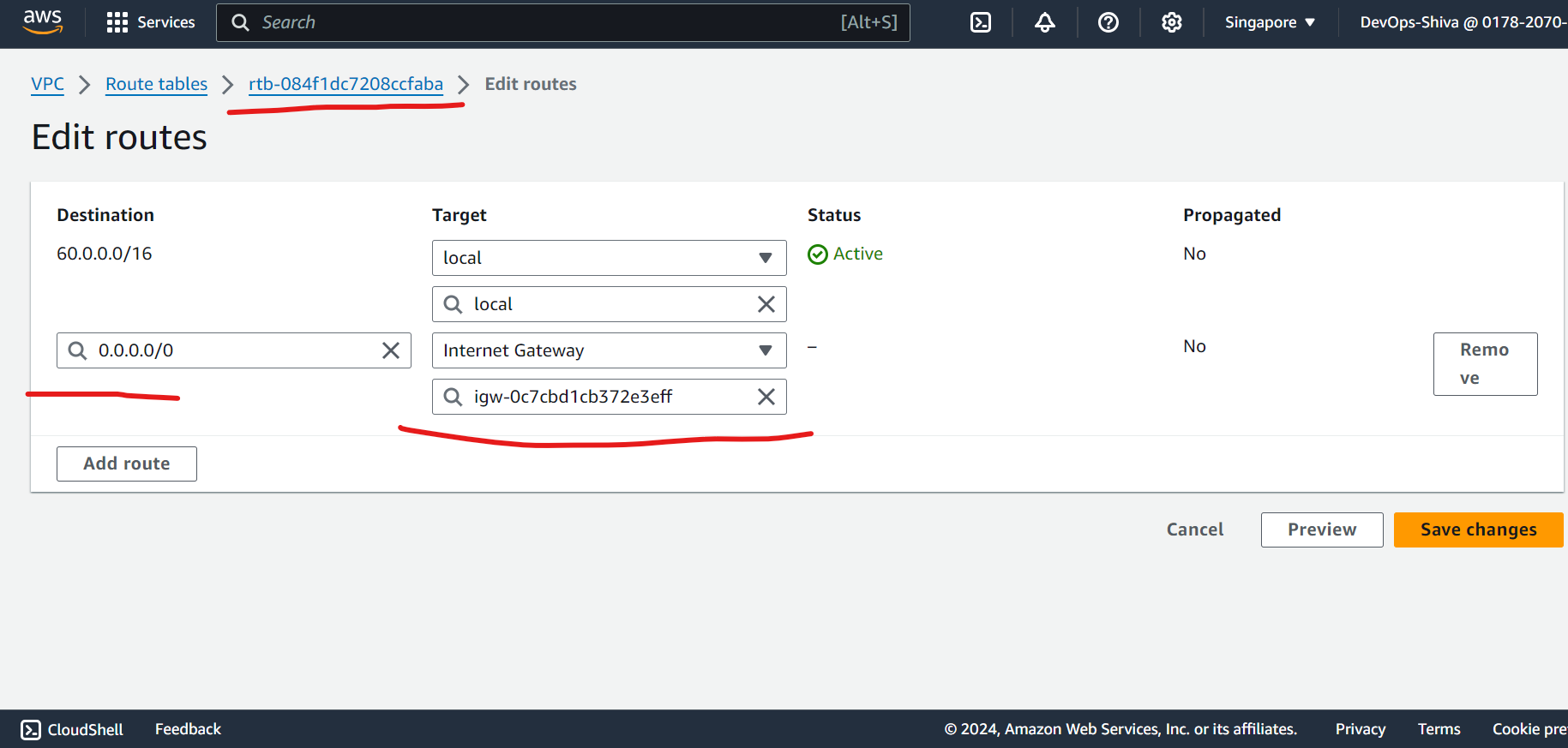
Edit routes and attach subnets association.
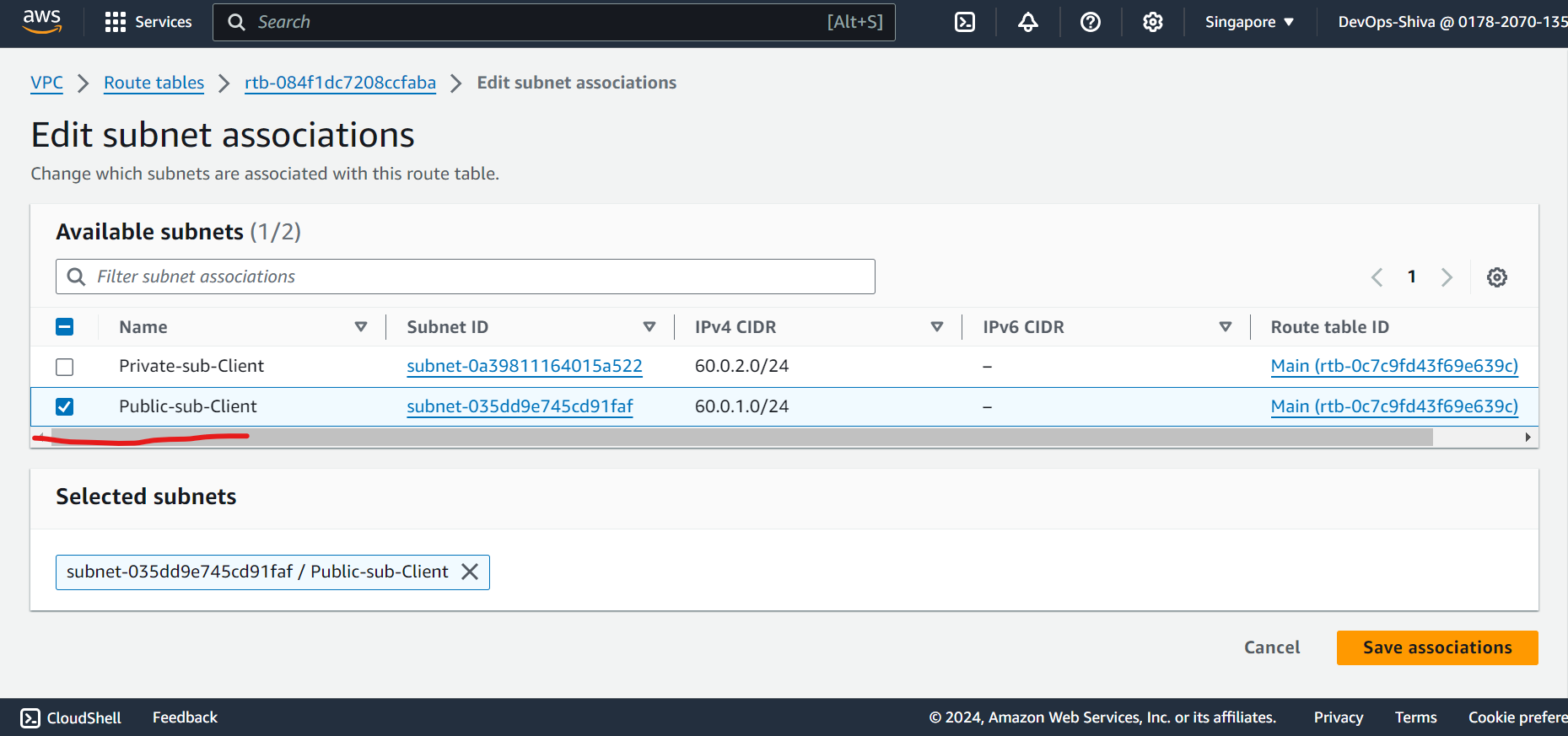
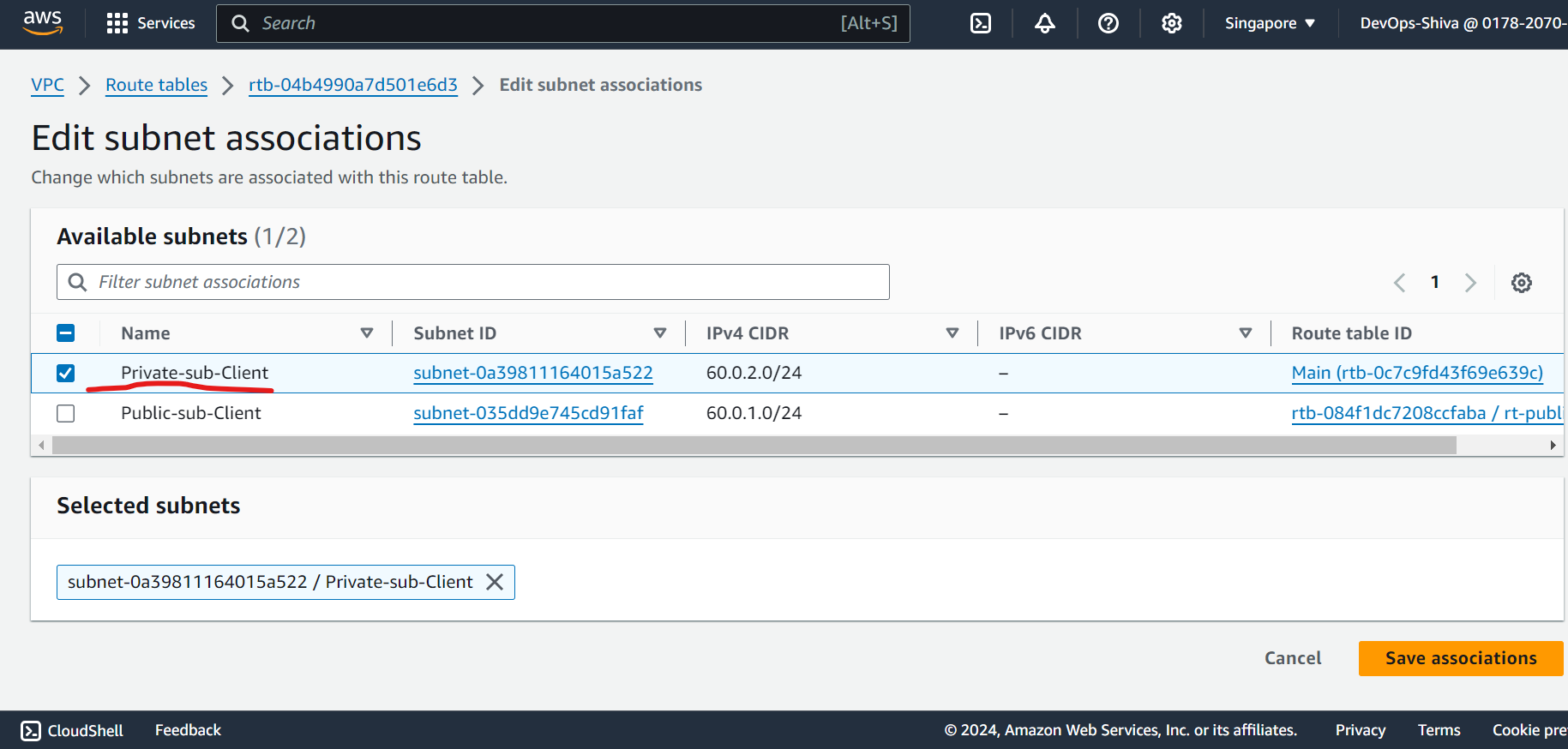
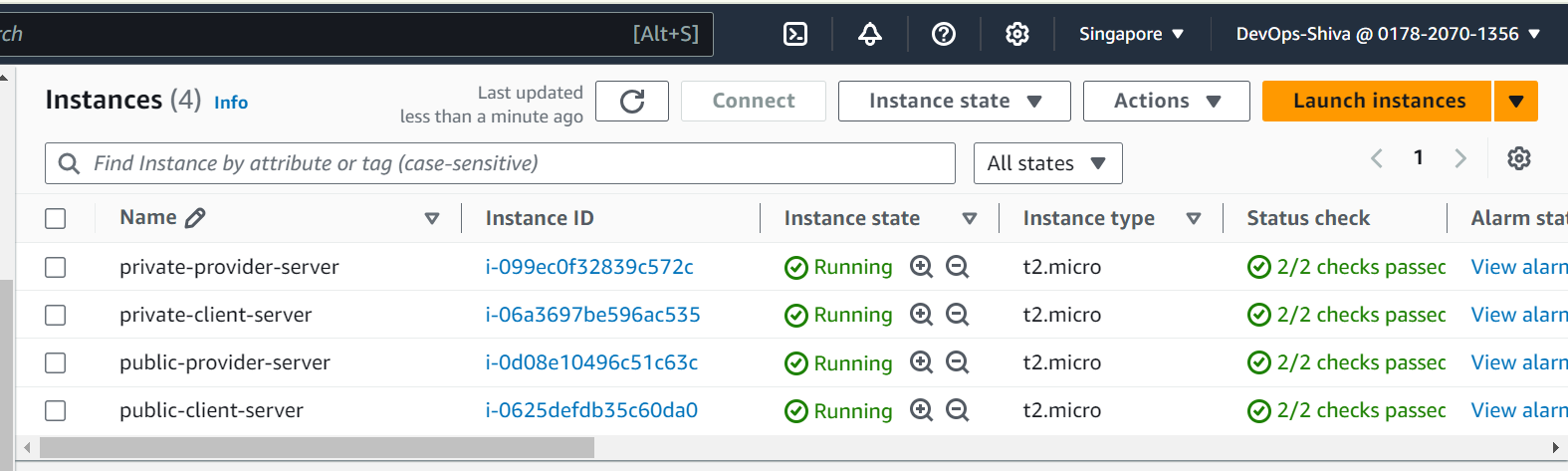
Launch Public & Private EC2 Instances → Client
Create Public EC2 instance - I will use same key pair across demo(not a best practice in production), Ubuntu 22.04, T2 micro instance, SG - open port 22.
Create Private EC2 instance - will use same key pair across demo(not a best practice in production), Ubuntu 22.04, T2 micro instance, SG - open port 22 and 80.
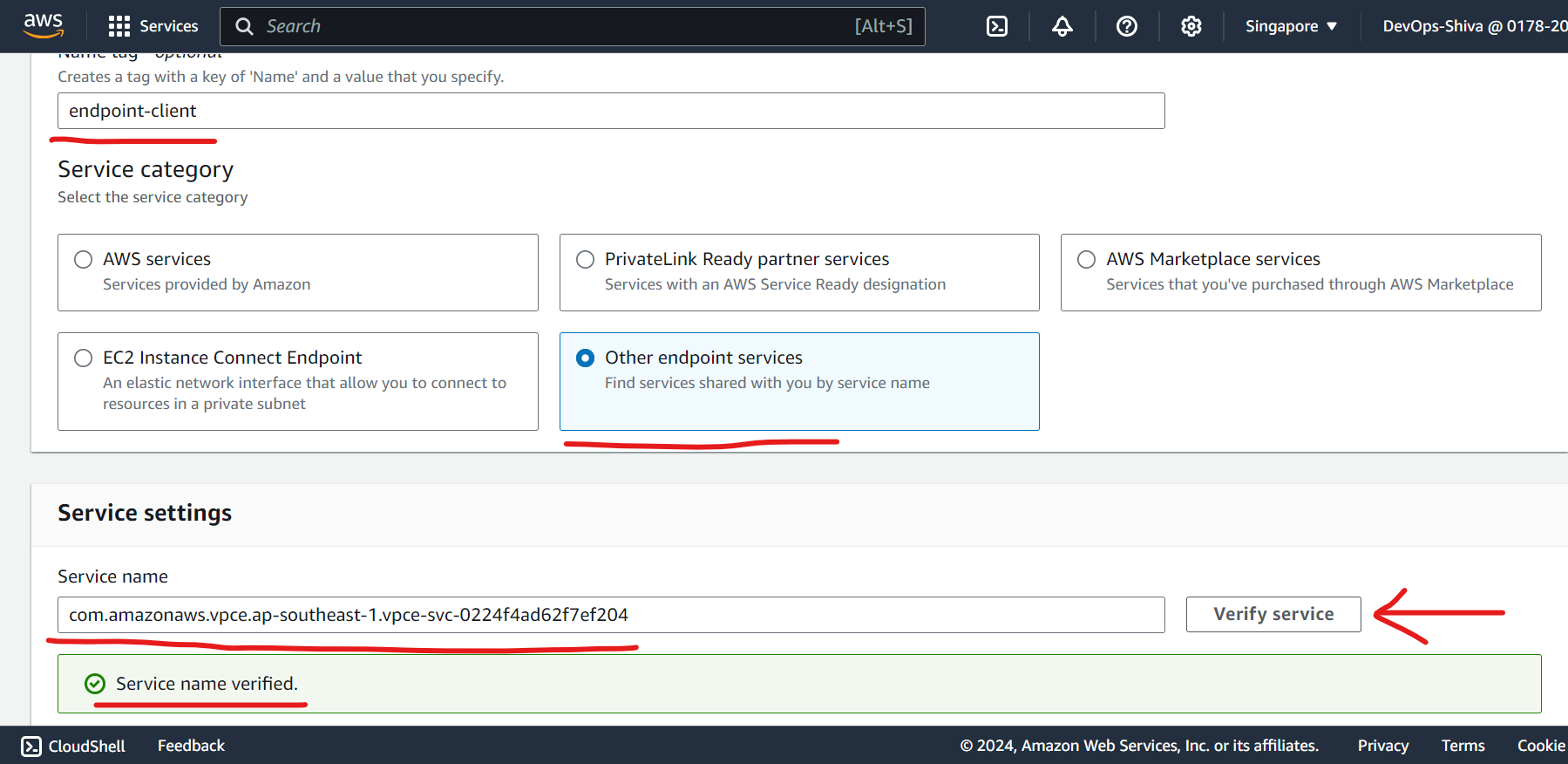
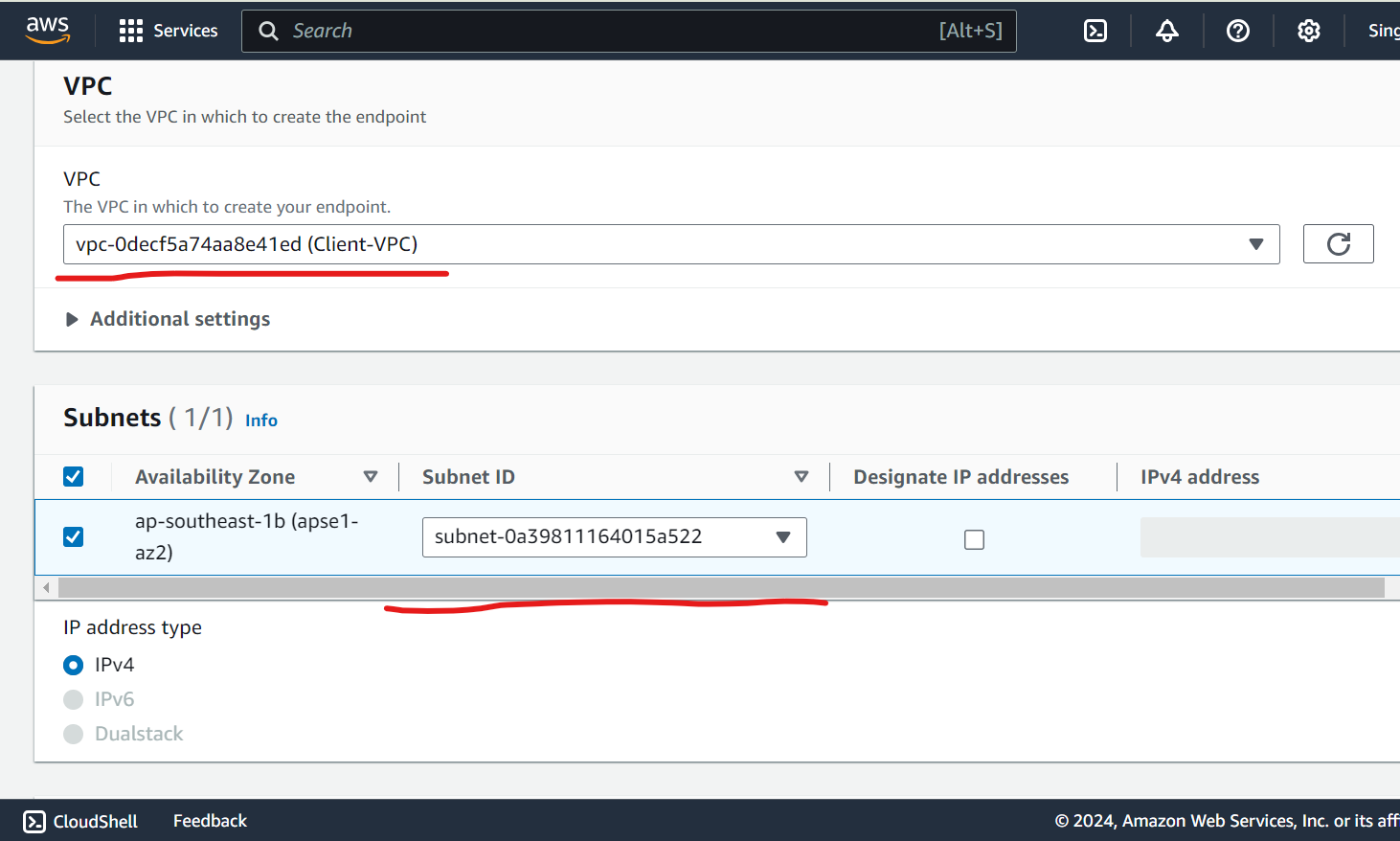
Create Endpoint Interface
Copy service name from Endpoint service and paste it to verify service while creating endpoint
Now you need to accept the endpoint connection, head over to provider-endpoint-service → endpoint connection as follows
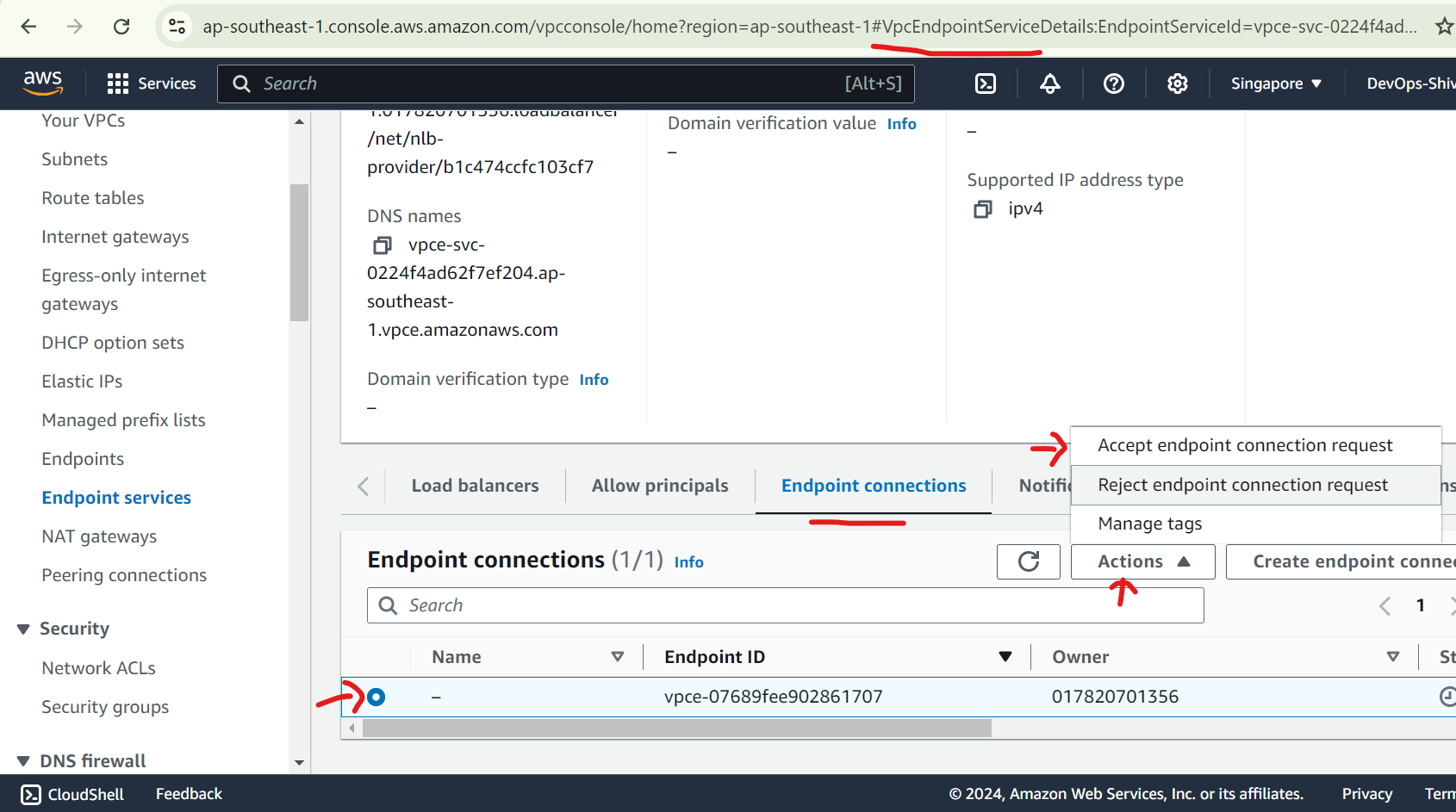
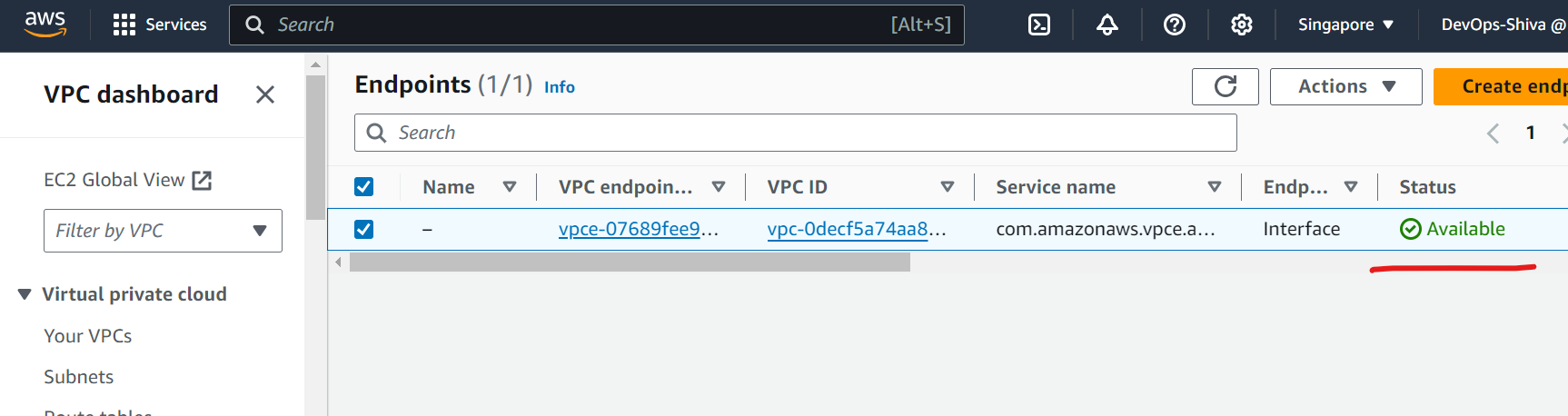
Heat accept. You can check the status available in endpoint interface.
Test
Heat Endpoint dns name from private-client-server you should see response like this
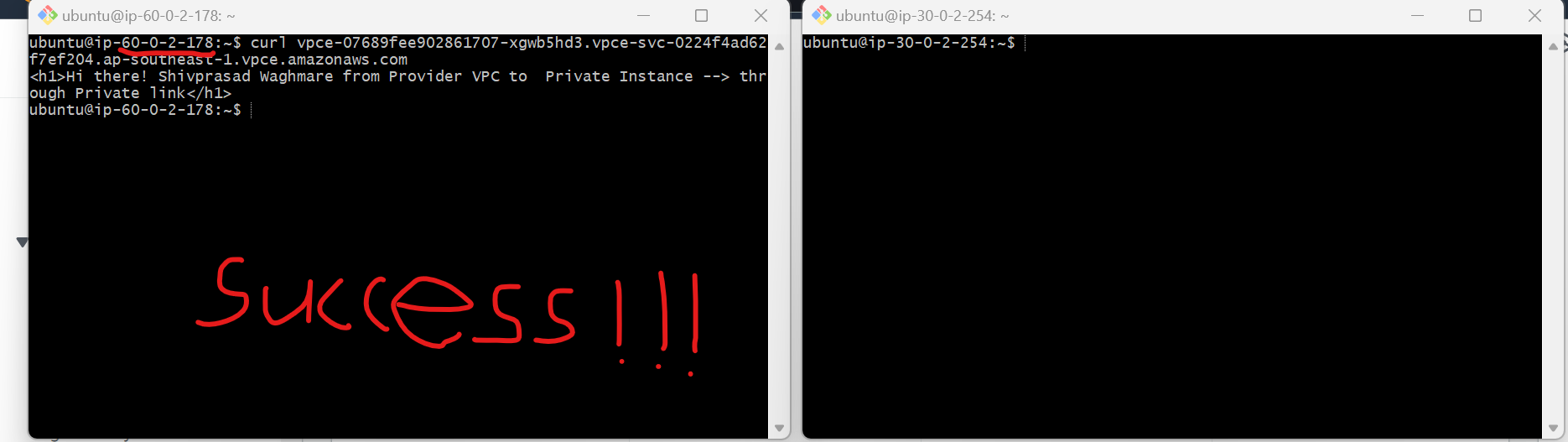
Cleanup
Delete VPC
Delete EC2 instances
Delete NLB and TG
Delete Endpoint service
Delete Endpoint
Key Takeaways
AWS PrivateLink provides secure and private access to services hosted in a VPC without requiring public internet exposure.
Endpoint Service: The service provider uses a Network Load Balancer (NLB) to expose the service within the VPC.
VPC Endpoint: The client creates an interface endpoint in their VPC to connect privately to the service provider's Endpoint Service.
Step-by-Step Setup: Involves creating an NLB, registering it as an Endpoint Service, configuring permissions, and establishing a VPC Endpoint in the client VPC.
Benefits: Enhanced security, simplified architecture (no need for internet gateways or VPNs), and automatic scalability.
Limitations: AWS Private Link is region-specific and doesn’t support all AWS services natively.
Subscribe to my newsletter
Read articles from Shivprasad Waghmare directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shivprasad Waghmare
Shivprasad Waghmare
"Accidental AWS/DevOps Engineer | AWS Community Builder | 7+ Years of Experience | Exploring AWS, Kubernetes, Terraform, Docker, Jenkins | Passionate about automating cloud infrastructure | Let’s explore the world of DevOps together!"