Networking Fundamentals: Extending Your Network (TryHackMe)
 J3bitok
J3bitok
In this article, we’ll cover the write-up for Extending Your Network that covers Introduction to Port Forwarding, Firewall 101, VPN Basics, and LAN Networking Devices. Here are few definition of terms before covering the walkthrough:
Port forwarding is an essential component in connecting applications and services to the Internet. Without port forwarding, applications and services such as web servers are only available to devices within the same direct network.
A firewall is a device within a network responsible for determining what traffic is allowed to enter and exit. Think of a firewall as border security for a network. An administrator can configure a firewall to permit or deny traffic from entering or exiting a network based on numerous factors such as:
Where the traffic is coming from? (has the firewall been told to accept/deny traffic from a specific network?)
Where is the traffic going to? (has the firewall been told to accept/deny traffic destined for a specific network?)
What port is the traffic for? (has the firewall been told to accept/deny traffic destined for port 80 only?)
What protocol is the traffic using? (has the firewall been told to accept/deny traffic that is UDP, TCP or both?)
A Virtual Private Network (or VPN for short) is a technology that allows devices on separate networks to communicate securely by creating a dedicated path between each other over the Internet (known as a tunnel). Devices connected within this tunnel form their own private network.
What is the name of the device that is used to configure port forwarding?
routerWhat layers of the OSI model do firewalls operate at?
Layer3,Layer 4What category of firewall inspects the entire connection?
statefulWhat category of firewall inspects individual packets?
statelessWhat is the flag?
THM{FIREWALLS_RULE}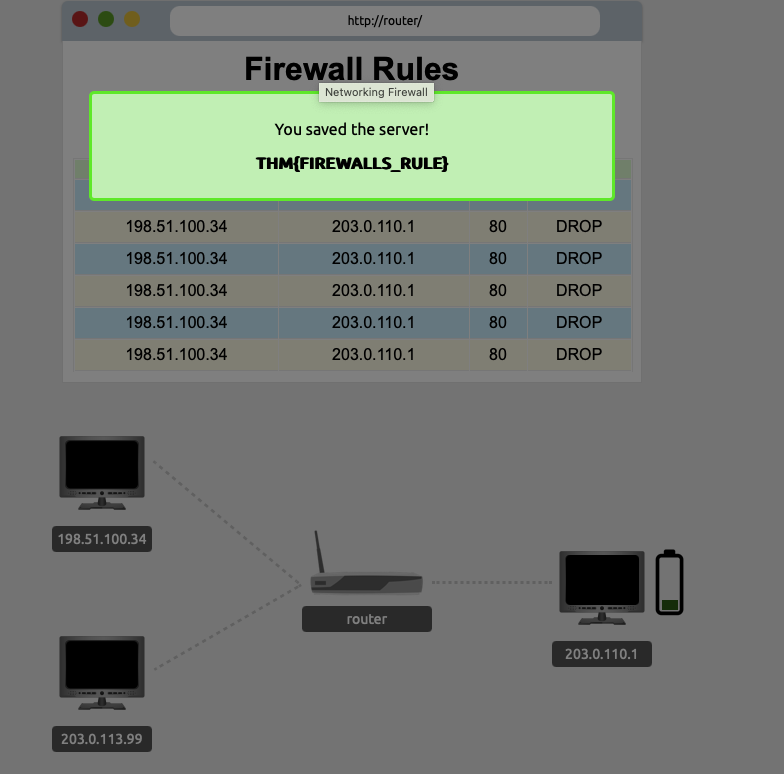
What VPN technology only encrypts & provides the authentication of data?
PPPWhat VPN technology uses the IP framework?
IPSecWhat is the verb for the action that a router does?
routingWhat are the two different layers of switches? Separate these by a comma I.e.: LayerX,LayerY
Layer2,Layer3What is the flag from the network simulator?
THM{YOU’VE_GOT_DATA}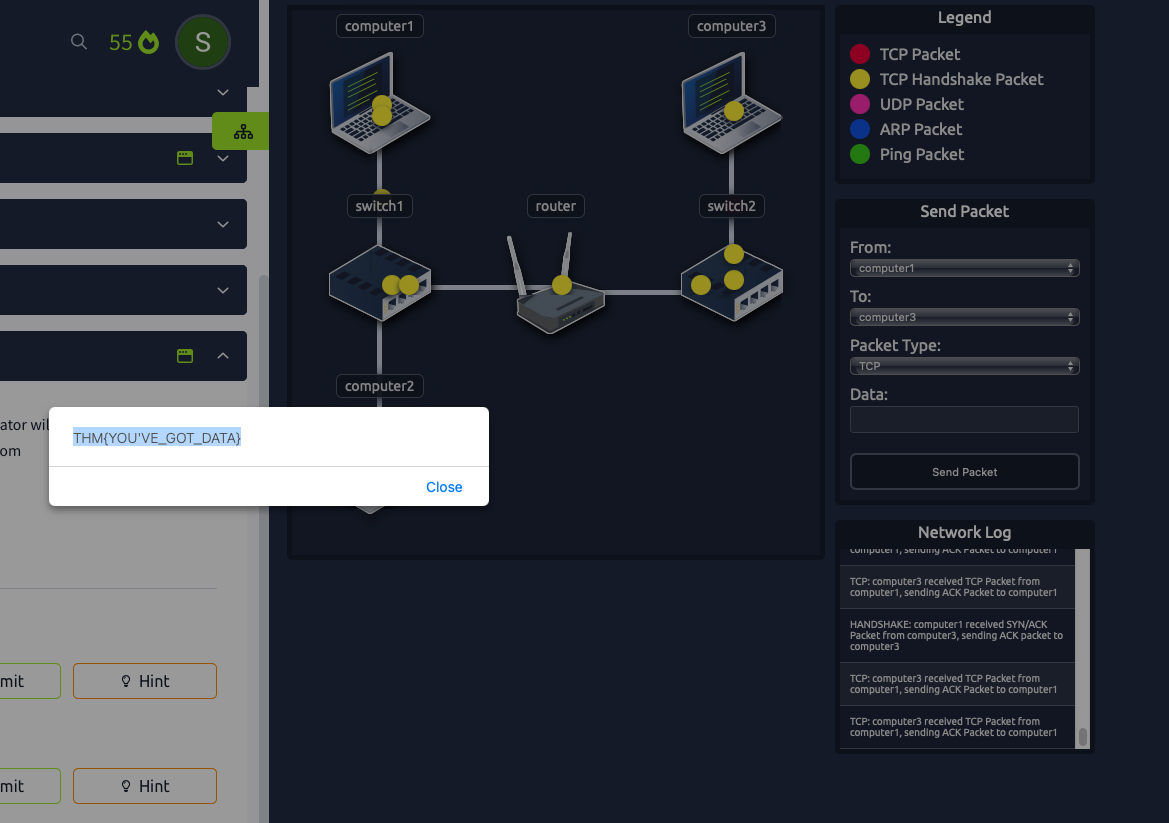
How many HANDSHAKE entries are there in the Network Log?
5
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges. We can also connect more on LinkedIn or X.
Subscribe to my newsletter
Read articles from J3bitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

J3bitok
J3bitok
Software Developer Learning Cloud and Cybersecurity Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship you can book a session with me on Mentorlst.com.