Unlocking Secrets: A Comprehensive Guide to Installing HashiCorp Vault 🔐🔓
 Tanvir Sayyad
Tanvir Sayyad
HashiCorp Vault is a fundamental cross-platform tool created with extreme flexibility to secure sensitive data and manage secrets. It is very versatile in different environments and is an essential solution for perforce construction and cloud in physical constructs. This guide thoroughly enumerates the process of installing Vault on multiple platforms, with clearer steps on to properly configure and operate it.
Vault’s Versatile and Platform-Agnostic Capabilities
Vault has the capability to integrate and operate with multiple platforms. Vault can be deployed on cloud data centers or traditional servers and still be fully functional. Following are some modern examples of the most notable deployment settings for Vault:
Kubernetes: Vault is most suitable for operating within cloud-driven Kubernetes environments, such as Amazon ECS, EKS, and other managed Kubernetes services.
Cloud Instances: Vault can run on cloud vendor-provided virtual machines such as AWS, Azure, and GCP.
On-Premises: There are plenty of enterprises that choose to install Vault on VMware virtual environments or physical servers, which allows control over the infrastructure itself. This is usually the choice for applications requiring sensitive security.
Local Development: For development or testing, Vault can also be installed and run on a local workstation for building and testing flexibility
Not only does Vault provide flexibility across deployment environments, but it also Vault supports multiple operating systems as well, including:
macOS
Windows
Linux
FreeBSD
NetBSD
OpenBSD
Solaris
However, the enterprise deployment tends to be on various Linux distributions, such as Ubuntu, Amazon Linux, CentOS, or Red Hat Enterprise Linux.
Step-by-Step Vault Installation Process 🛠⚙️
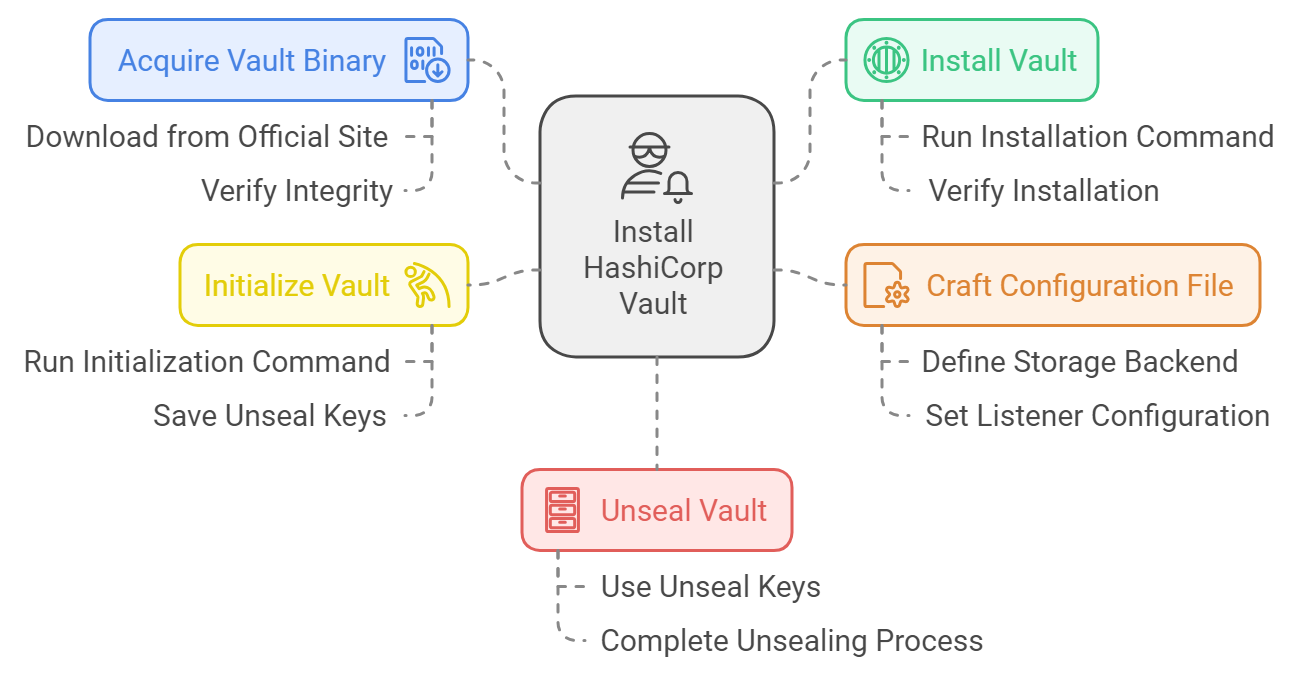
In order to install Vault properly, one is always advised to follow an orderly approach. Be it manual installation or automated provisioning, the process has certain key steps involved:
1. Download the Vault Binary 📑
The first step in the process is to download the Vault binary via HashiCorp official site at vaultproject.io, redirecting users to the releases webpage at releases.hashicorp.com/vault. Alternatively, depending on your operating system, you may straight-up use a package manager such as apt, yum, or Homebrew to install Vault.
For example, on Ubuntu, you could use the terminal commands below to download and install Vault:
sudo apt-get update
sudo apt-get update && sudo apt-get upgrade -y
sudo apt install net-tools
wget -O- https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update && sudo apt install vault
This procedure ensures that the Vault binary can be found in the system path, and hence the application can be executed directly.
2. Write the Configuration File 📃
Once the installation is successful, the next task would be to create a configuration file that describes how Vault will behave: the storage backend, listener configuration, and clustering options. This configuration is particularly important in production scenarios, where high availability, redundancy, and good storage configuration would be required.
3. Start Vault and Initialize it ▶️
You then have to start Vault with your configured options. For the first time, Vault will require initializing-the process that will produce the master key for unsealing the vault. After initialized, the vault is ready to secure and manage your secrets.
4. Unseal Vault 🔓
After initialization, Vault is sealed, thus making a certain unsealing process required to regain access to its features. The sophisticated seal/unseal mechanism of Vault uses Shamir's Secret Sharing to operate, where the master key is divided into shares that must be read by trusted individuals. When the required number of key shares is provided, then Vault is operational.
Vault Installation: Automated Setup 🤖⚙️
Vault is deployed manually, which is pretty simple. In an automated way, though, it just gets done using tools like Helm for Kubernetes-based environments or package managers like apt and yum. Of these tools, Helm makes the installation of Vault in Kubernetes cluster's easier by taking the burden off configuring the system manually.
Running the below command will install Vault using Helm:
helm install vault hashicorp/vault
That command itself will install Vault into your Kubernetes cluster with no hassles related to configuring and setting it up-the ideal installation approach for Minikube, EKS, and other localized Kubernetes-based environments.
Quick Recap of the Installation Procedure 💡📄
Acquire Vault Binary: Download Vault from the official site or use a package manager.
Install Vault: Extract Vault's binary and add it to your system path.
Write the Configuration File: Express the parameters under which Vault will run, that is, storage and listener configurations.
Initializing Vault: Spin up Vault and perform an initial initialization that generates the master key.
Unseal Vault: Use the Shamir Secret Sharing algorithm to unseal Vault in the last step.
Conclusion 🎯
The HashiCorp Vault is a very flexible, platform independent solution whose design is to secure information of most sensitive kinds across entirely different forms of infrastructure. It is unparalleled in versatility-from deploying Vault on a cloud service through Kubernetes environments to using conventional on-premise servers. With this comprehensive guide, the installation is bound to be seamless, while Vault will be ready to manage secrets, keeping your data safe, and ensuring the confidentiality of your infrastructure.
References
Subscribe to my newsletter
Read articles from Tanvir Sayyad directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tanvir Sayyad
Tanvir Sayyad
Hi there! I am a competent DevOps Engineer with 2 years of experience in the IT domain with tools and technologies diversity. My professional background encompasses Jenkins, Ansible, HashiCorp Vault, Bitbucket, GitHub, Nexus, Maven, Ant, and Docker. Some of the technologies that I'm familiar with are Terraform, Kubernetes, and GitLab CI/CD. My thirst for learning is never quenched, and in turn, I share my views on it through my blog. Let's connect and learn DevOps together! Feel free to reach out if you’re interested in collaboration or discussions about DevOps innovations at tanvir.sayyad1011@gmail.com.!