SonarQube Essentials: Why It’s Crucial in CI Pipelines
 NaveenKumar VR
NaveenKumar VRTable of contents
Hello and welcome, fellow DevOps enthusiasts! Thanks for joining this exploration. In the upcoming sections, we’ll dive into SonarQube, uncover its benefits, and discuss why it’s essential for your projects.
Let’s jump in and get the code quality party started!
Let’s start with this question:
What is SonarQube
- SonarQube is a code quality and security analysis tool that also functions as a Static Application Security Testing (SAST) tool.
Wait! What is SAST (Static Application Security Testing) ?
SAST is a testing technique that analyses an application’s source code to identify security vulnerabilities without executing it.
For example Imagine having someone who examines every line of code, highlighting potential security weaknesses(such as Sensitive Data Exposure, SQL Injection) before you package and run the application.
Why and When Should I use SonarQube ?
Great question! Here’s a quick answer:
To avoid Technical debt in your codebase by catching code quality issues early.
To protect your code from security vulnerabilities, ensuring it meets security standards. (Eg: Sensitive Data Exposure, Hardcoded Secrets, SQL Injection)
When you lack the time or resources to manually review every line of code for compliance with best practices.
To ensure sufficient test coverage, helping you confirm that your code behaves as expected and meets its requirements.
To maintain coding standards consistently
To continuously improve code quality over time
If you want to tackle any or all of the issues mentioned above, integrating SonarQube into your development stack can significantly enhance your code quality and security practices, ensuring a more robust and maintainable codebase.
Technical debt: Some of you might be wondering, "What is technical debt in a codebase?" Trust me, I had the same question at one point! 😊
It refers to the future cost of rework or maintenance required when code is written quickly to meet immediate needs rather than following the best practices or optimal solutions. (Some Common Technical Debts refers to coding practices, duplicated code, and complex methods). » Wait ! what 😲 ? Can you speak in a language what is understandable
Got you ! Let’s consider Flipkart preparing for the Big Billion Day sale. They want to apply a 30% discount on all products. To meet this urgent request, instead of implementing a flexible discount logic that allows for easy changes, you hardcode the 30% discount directly into the codebase.
Later, if they decide to change the discount to 20% for specific products, you’ll need to go back and manually update the code. This creates technical debt because, at some point, you’ll have to rewrite the entire discount logic to make it adaptable for various scenarios. If you keep taking such quick shortcuts to meet urgent needs, the codebase will eventually become messy and difficult to maintain.
I hope it's now clear why and when to use SonarQube. Let's explore what SonarQube offers to address all these issues.
What Capabilities Does SonarQube Offer to Tackle These Challenges?
Let us explore the various capabilities offered by SonarQube to address these challenges and examine how we can effectively leverage them.
Code Quality Management
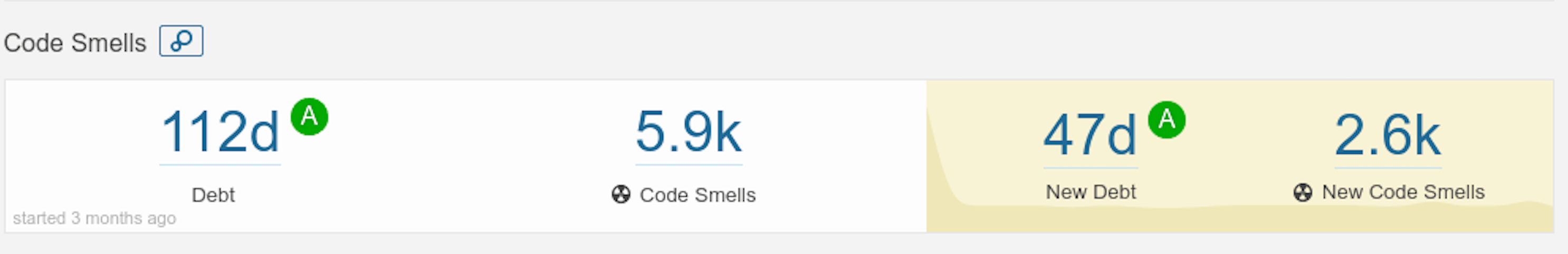
Code Smells Detection:
As the name implies, the code smell report highlights potential areas of poor design or bad coding practices that could lead to maintainability challenges down the road.
It offers developers guidance on coding standards and best practices, along with suggestions for improvement.
Where Can I check this on Sonarqube? You can check this on the SonarQube Dashboard page of the project itself.
Note: While the suggestions provided by the code smell report aren't necessarily bugs, they serve as valuable indicators that the detected code may lead to potential issues in the future. Let's embrace these insights and enhance our coding practices together!
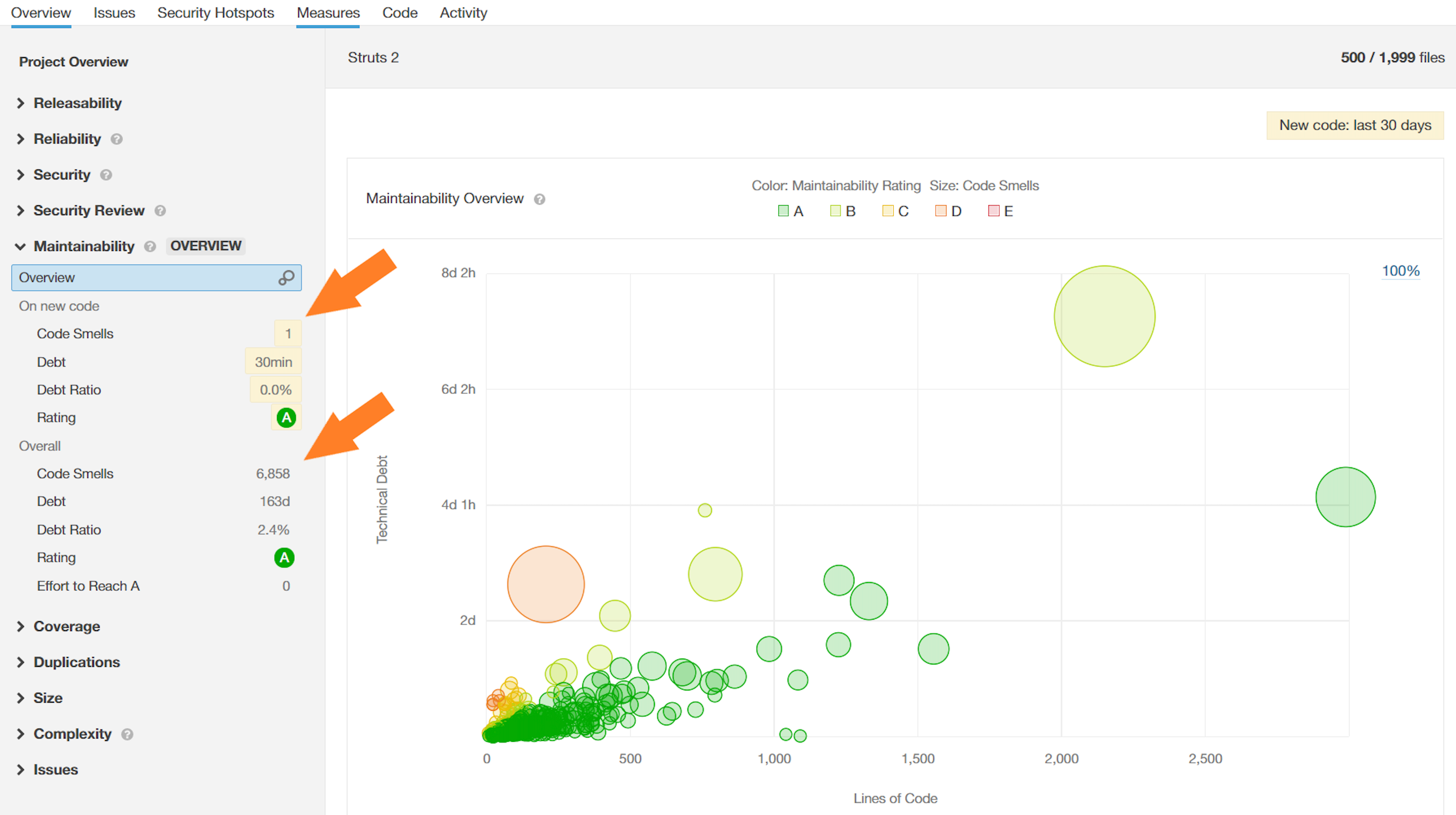
Maintainability Rating
SonarQube assigns a rating to your code known as the Maintainability Rating, which is based on the Technical Debt Ratio. This rating reflects the effort required to resolve identified issues.
By leveraging this rating, teams can effectively prioritise their refactoring efforts, concentrating on areas with lower maintainability scores to enhance overall code quality.
You can view the available Maintainability Ratings through this link.
Where Can I check this on Sonarqube? You can check the Maintainability Rating Under measures tab in SonarQube
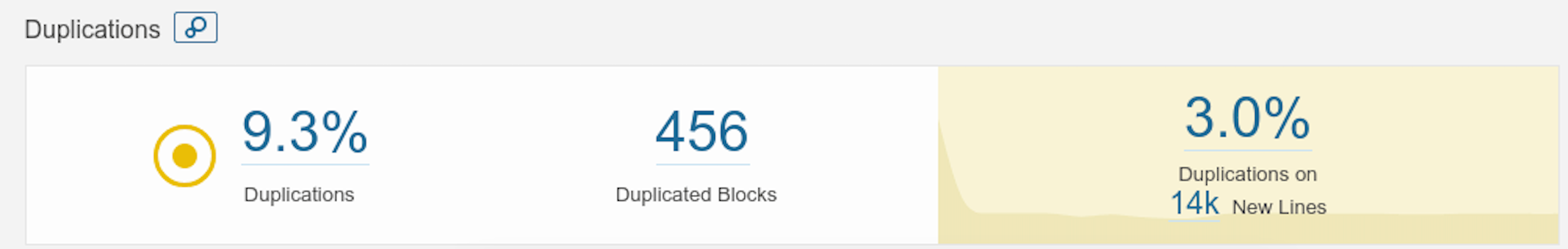
Duplicated Code Detection
Identifies the duplicate blocks of codes.
The lesser the number the more better your code is
Where Can I check this on Sonarqube? You can check this on the SonarQube Dashboard page of the project itself.
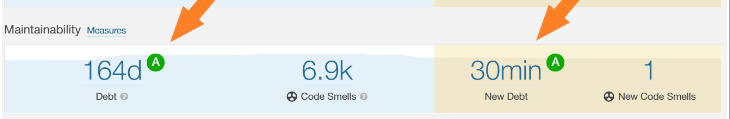
Technical Debt Management:
SonarQube continuously tracks the evolution of technical debt, making it easier for teams to prioritise addressing technical issues.
Offers historical trends and dashboards to visualize how technical debt changes over time.
It also provides you the effort required to fix the code issue in terms of time such as Hours or days.
Security Vulnerability Detection
Static Application Security Testing (SAST):
SonarQube performs SAST to identify common security vulnerabilities, such as SQL injection, cross-site scripting (XSS), and hardcoded passwords on the source code.
Provides remediation guidance for detected security issues, helping developers fix vulnerabilities before code reaches production.
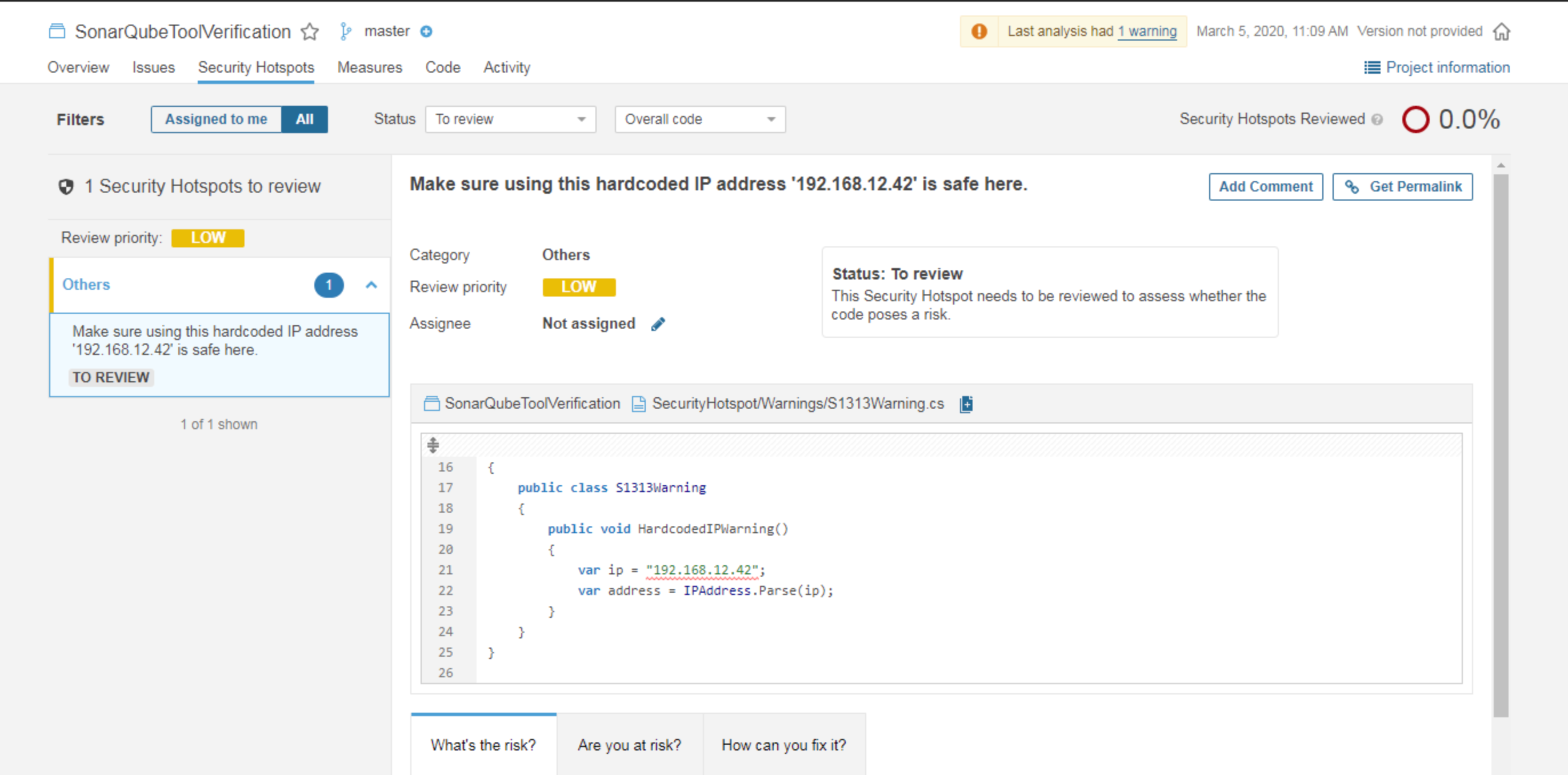
Security Hotspots
Highlights areas of code that require manual review for potential security implications.
SonarQube comes with built-in security rules based on industry standards and best practices. These rules help developers adhere to security guidelines by flagging potential vulnerabilities during the development process.
Where Can I check this on Sonarqube? You can check this on the SonarQube Security Hotspot Tab
Code Coverage and Test Execution
Code Coverage Analysis:
This feature shows the percentage of your code that is covered by test cases.
Why it is needed? Test cases are written by developers to check if the code works as it should. They help ensure that the program does what it's supposed to do.
Code Coverage Analysis Identifies untested parts of the codebase, allowing teams to prioritise adding tests to improve code reliability.
Note: You need to perform code coverage analysis using the appropriate tool for your programming language and then export the report to SonarQube for it to be available in the SonarQube dashboard.
Analysis: The more the percentage the better the code is
Where Can I check this on Sonarqube? You can check this on the SonarQube Dashboard page of the project itself.

Quality Gate
As the name suggests, it acts as a gate between your code and the production branch.
It allows you to define quality gates (rules) based on metrics such as code coverage, code smells, bugs, and security vulnerabilities. For example, you can set rules like a minimum code coverage of 90% or a maximum duplication rate of 10% etc.
This ensures that only code that meets your quality standards is merged, helping maintain the integrity and reliability of the main branch.
Where Can I check this on Sonarqube? You can check this on the SonarQube Quality Gate Section

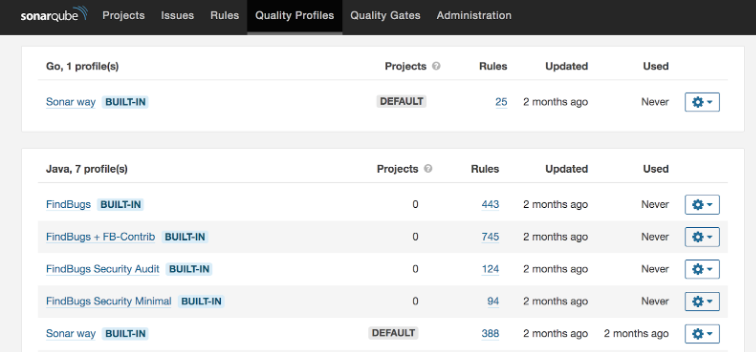
Quality Profile
A Quality Profile is a collection of coding rules and guidelines that define what constitutes acceptable code quality for a specific programming language or project. It dictates how code is analysed and what issues are reported.
Quality Profiles help teams establish consistent coding standards across projects, allowing for tailored rule sets based on language and project needs.
In the screenshot below, you can see the quality profiles for Java and Go. You can set quality profiles, which are sets of rules tailored for specific programming languages, to ensure that your code meets the desired quality standards. Each profile contains predefined rules that help identify issues related to code quality, security vulnerabilities, and best practices specific to that language.
Alright I understood the tools sets that SonarQube offers. Now my next question will be How can I use this tool what are the options I have
How to use SonarQube to Scan Code
Before we dive into how to use SonarQube, let me share a little secret with you: SonarQube is essentially a reporting and analysis tool that presents the analysis of your code in a structured way. So you need to generate report and send it to SonarQube to make full use of it.
How can I Generate Report ?
Good Question! There is a tool called SonarScanner. This will scan your code and send the report to the SonarQube server.
Once this is done, you can fully harness the powerful features that SonarQube has to offer!
Now you may have many questions like,
How SonarScanner knows my SonarQube server
How it knows what to scan and so on.
We will cover all those things in the series of blogs on “How to scan our source code using SonarQube“
For now, please remember that you need SonarScanner to generate reports and send them to SonarQube, where the magic of code analysis happens.
As we know, we need to use SonarScanner to generate reports. Here are the available options for running SonarScanner on your code:
Run Locally: You can execute SonarScanner on your local machine to analyze your code and generate reports.
Configure in Your CI Pipeline: You can integrate SonarScanner into your Continuous Integration (CI) pipeline, allowing it to run automatically each time you commit code. This ensures that code quality checks are consistently applied.
Run in Docker: If you prefer containerization, you can run SonarScanner within a Docker container. This approach simplifies environment management and ensures consistency across different machines.
Use SonarCloud: If you're looking for a cloud-based solution, consider using SonarCloud, which offers similar features without the need for local setup. You can connect it to your repository for automated analysis.
That concludes this extensive blog. What I aimed to share with you is:
What is SonarQube
why and when we use it
Capabilities It Offers
How to Use SonarQube Briefly (We will cover in detail in a separate blog)
Summary:
What is SonarQube?: SonarQube is a code quality and security analysis tool that also functions as a Static Application Security Testing (SAST) tool.
Why Use SonarQube?: Integrate SonarQube to avoid technical debt, protect against security vulnerabilities, maintain coding standards, and ensure sufficient test coverage.
Understanding Technical Debt: Technical debt accumulates when quick fixes are applied instead of following best practices, leading to maintenance challenges down the line.
Capabilities Offered by SonarQube: Explore features like code smells detection, maintainability ratings, duplicated code detection, and security vulnerability detection.
Code Coverage Analysis: Measure how much of your code is covered by tests, helping you prioritise testing efforts for improved reliability.
Quality Gates: Set rules based on metrics like code coverage and bugs to ensure only high-quality code is merged into the main branch.
Quality Profiles: Customize coding rules for specific programming languages to maintain consistent coding standards across your projects.
Generating Reports with SonarScanner: Use SonarScanner to analyze your code and send reports to SonarQube for comprehensive analysis.
Multiple Usage Options: Run SonarScanner locally, integrate it into your CI pipeline, use it in Docker, or leverage SonarCloud for cloud-based analysis.
What is Next ?
In the next blog, we will explore in detail how to set up the infrastructure for SonarQube, covering topics such as:
Which edition to use
What type of infrastructure is suitable
How to calculate the resources needed for the SonarQube infrastructure
Setting up SonarQube according to industry standards
Thank you for taking the time to read this blog! I hope you found valuable insights throughout. If you have any feedback or notice any mistakes, please feel free to share in comments—I'm always happy to make corrections.
Happy learning, and I look forward to seeing you in the next blog!
Subscribe to my newsletter
Read articles from NaveenKumar VR directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
