Privileged Docker Containers: The Silent Backdoor to Your Host System
 jack kweyunga
jack kweyunga
In this article, I will demonstrate how to use a privileged Docker container to access the host system's resources, such as the network, file system, devices, kernel, and more.
I understand that privileged containers are not always used for harmful purposes, but for this article, that will be my focus.
What does it mean for a Docker container to be privileged?
A regular Docker container has some security rules and is usually kept separate from the host system—that's the whole point of containerization, right? This makes it safer and uses resources better.
But when you take away those security rules and barriers, the container becomes privileged. You can do this by adding the —privileged flag when you start the container.
sudo docker run --privileged -it ubuntu
What can a privileged Docker container access from the host?
When you run a Docker container in privileged mode, it gets a lot more access to the host system's resources, letting it do way more than a regular container. Here's a closer look at what a privileged Docker container can tap into:
File system: A privileged Docker container can access the host's entire file system, allowing it to read, write, and modify files across all mounted drives and directories.
Devices: Privileged Docker containers can directly access hardware devices on the host, such as hard drives, network interfaces, GPUs, and USB devices.
Kernel: Privileged Docker containers can interact with the host's kernel, allowing them to load and unload kernel modules, change kernel parameters, and perform operations that require kernel-level access.
System-level operations: A privileged Docker container can perform system-level tasks like a root user on the host, allowing it to manage processes, configure services, and change system settings.
Root privilege: A privileged Docker container with root access can execute any command on the host, providing significant control but also posing major security risks due to potential unauthorized access or changes.
Demo
The demo shows you how to run a simple demo container using the BusyBox Docker image in privileged mode. BusyBox is a lightweight image that has a bunch of common UNIX tools. The demo uses Docker Compose to make setting up and managing the container easier with a YAML file. This setup gives you a peek at what you can do with containers in privileged mode, but also the risks that come with it.
services:
busybox:
image: busybox
privileged: true # activated here
network_mode: host # connect to the host network
pid: host
ipc: host
volumes:
- /:/host # mount all of the host
tty: true # Enable TTY
stdin_open: true # Keep stdin open
command: chroot /host
Save the content in a file like docker-compose.yml and then run the following command in the same folder.
sudo docker compose run --rm busybox
After running the command, you'll notice we can now access the root user of the host machine with alarming ease.
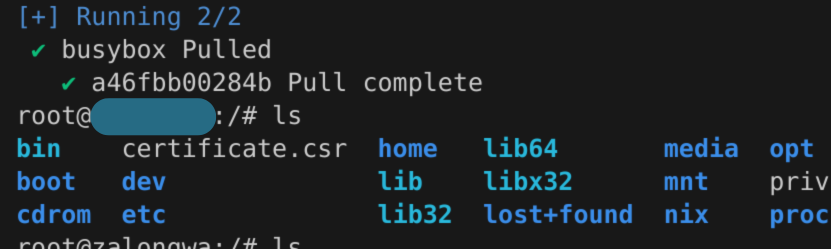
Using that shell, you have root access to the host machine and can execute any commands on it.
When could this be considered a backdoor?
As demonstrated, you were able to execute the privileged Docker container while logged into your system. This may initially appear secure, but it is crucial to consider the associated risks. For instance, what if a malicious actor manages to deploy a Docker container on your system and access it remotely? This could happen if an attacker exploits vulnerabilities in your system's security.
In another scenario, consider an attacker gaining access to an exposed Docker daemon. This risk arises if the daemon is not adequately secured or is unintentionally exposed to the internet. With access to the Docker daemon, an attacker could run a privileged container, granting them root access to your host system. This access would enable the execution of any command on your system, potentially resulting in data breaches, unauthorized data manipulation, or even complete system control.
These examples really highlight why it's super important to lock down Docker daemons and containers. You definitely don't want anyone sneaking in and causing security issues.
Conclusion
I hope this article has helped you understand the big risks that come with privileged Docker containers. If a bad actor gets into one, they could potentially take over your whole host system. To keep things safe and secure with Docker, here's what you should do:
Lock down privileged containers: Always run them in a super secure environment with tight access controls to keep out unauthorized users.
Keep the Docker daemon hidden: Never let the Docker daemon be visible on the internet, as it's a hot target for hackers always on the lookout for weak spots.
By sticking to these tips, you can really cut down the chances of privilege escalation and container escapes, keeping your systems safe and sound.
Seeking expert guidance in Ops, DevOps, or DevSecOps? I provide customized consultancy services for personal projects, small teams, and organizations. Whether you require assistance in optimizing operations, improving your CI/CD pipelines, or implementing strong security practices, I am here to support you. Let's collaborate to elevate your projects. Contact me today | LinkedIn | GitHub
Subscribe to my newsletter
Read articles from jack kweyunga directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

jack kweyunga
jack kweyunga
Am a DevSecOps practitioner, software engineer and a life long learner.