Mastering IAM: Unraveling Identity-Based and Resource-Based Policies on AWS
 Pooja Manellore
Pooja Manellore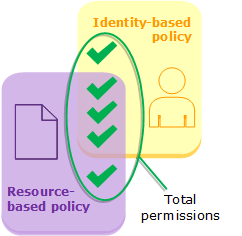
Understanding IAM: Identity-Based vs. Resource-Based Policies
In today's cloud landscape, Identity and Access Management (IAM) is crucial for securing and managing resources. It's a universal concept, not exclusive to AWS, and it focuses on two critical functions:
Authentication: Proving your identity, typically via username and password, to access a system.
Authorization: Proving that you have the right permissions to access specific resources.
IAM Essentials: Users, Groups, and Permissions
Users: Individuals who need access to AWS services and resources. Permissions determine what actions they can perform.
Groups: Collections of users with similar roles. Instead of assigning permissions to each user, you can assign them to the group, and all members inherit those permissions.
Permissions: Define what actions users, groups, or roles can perform on AWS resources.
In IAM, these entities (users, groups, and roles) are referred to as identities, while AWS services such as EC2, S3, and RDS are called resources. Permissions define what actions an identity can perform on a resource.
IAM in AWS: Identity-Based Policy
An Identity-Based Policy is a permission policy attached directly to users, groups, or roles. These policies allow you to control access to AWS services and resources based on the identity of the user.
For example, in an organization, the root user (the account’s owner) has full access to all resources. However, root access should not be widely shared due to the security risks involved. Instead, IAM allows you to create users with specific permissions, minimizing the risk if a single account is compromised.
Assigning permissions to individual users can be time-consuming and difficult to manage, especially when multiple users share similar roles. This is where groups come in handy. You can create a group with the necessary permissions and add users to it, simplifying permission management. Similarly, roles allow temporary access for third-party users or services without the need for long-term credentials.
Thus, identity-based policies are ideal when you're assigning permissions directly to users, groups, or roles. These policies give you flexibility and control over who can access what within your AWS environment.
What is a Resource-Based Policy?
While identity-based policies are attached to users, groups, or roles, a Resource-Based Policy is attached directly to the resource itself. Instead of managing access by assigning permissions to identities, you can attach a policy directly to resources like S3 buckets, granting specific users access.
For instance, you can attach a resource-based policy to an S3 bucket, specifying which users can access it. However, it’s important to note that resource-based policies only allow you to specify users or roles as principals, not groups .
Resource-based policies are supported by several AWS services, including:
Amazon S3
Amazon API Gateway
AWS Lambda
Amazon SNS
Amazon SQS
And many more. Some services like Amazon VPC and AWS Systems Manager support resource-based policies partially, meaning they can offer resource-based access control for specific functions but may rely on identity-based policies for others.
Subscribe to my newsletter
Read articles from Pooja Manellore directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pooja Manellore
Pooja Manellore
I have completed my B.Sc. in Computer Science in 2024 and have gained skills in Data Analytics, HTML, and CSS. I am currently advancing my expertise by learning DevOps, aiming to secure a role as a DevOps Engineer. I am eager to join a company immediately where I can apply my skills and continue growing in this field