Securing Kubernetes Operations with Runtime Security Best Practices
 Subhanshu Mohan Gupta
Subhanshu Mohan GuptaTable of contents

Welcome to the 9th installment of my Kubernetes series wherw we’ll dive into advanced runtime security techniques for Kubernetes environments to detect anomalies, enforce strict container security policies, and mitigate risks in production.
Introduction
Securing Kubernetes environments is a top priority in today's fast-paced DevOps world. While Kubernetes offers robust security features, runtime security often remains a critical but overlooked area. Runtime security ensures that your containers are monitored continuously, policies are enforced, and any anomalous behaviour is detected and mitigated in real-time. In this article, we’ll explore runtime security strategies for Kubernetes environments using tools like Falco, Sysdig, and Aqua Security to safeguard your operations and show how these tools can be integrated into your DevSecOps pipeline.
The Challenge: Runtime Threats in Kubernetes Environments
When Kubernetes workloads are deployed, they interact with various internal and external components making them vulnerable to various attacks. Without proper runtime monitoring attacks like privilege escalations and resource hijacking or malware injection can go unnoticed until they cause serious damage. Attackers exploit runtime vulnerabilities to escape containers, access sensitive data or even take control of the entire cluster.
The solution? Implementing runtime security that continuously monitors your running containers, detects any abnormal activity, and enforces security policies to shut down threats before they escalate.
Key Runtime Security Strategies
Detecting Anomalous Activity with Falco
Falco is an open-source runtime security tool that monitors system calls and detects suspicious behaviour in real-time. It can alert you if a container starts accessing sensitive files, changing configurations, or performing unauthorized network connections.Example Use Case: Imagine you have a containerized web application running in production, and one of your containers is compromised via a vulnerability in the app. The attacker tries to access sensitive
/etc/shadowfiles. Falco would detect this unauthorized attempt and trigger an alert, allowing your team to immediately respond before any damage occurs.Enforcing Policies with Aqua Security
Aqua Security provides runtime protection by defining security policies, like controlling which images can run or limiting container privileges. It ensures that only compliant containers, which pass through security checks, are allowed to execute in the production environment.Example Use Case: Consider a scenario where an attacker tries to inject malicious code by deploying a vulnerable container. Aqua Security would enforce policies that block non-compliant or unsigned containers, preventing this attack vector.
Monitoring and Incident Response with Sysdig
Sysdig offers deep visibility into container activity by monitoring syscalls, network activity, and Kubernetes events. It’s powerful for post-incident analysis, allowing you to inspect runtime activity and determine the root cause of a security breach.Example Use Case: After detecting an attack with Falco, Sysdig can help trace back the attacker's steps, showing how they entered the environment, what processes were executed, and what data may have been compromised. This data can then be used to patch vulnerabilities and prevent future attacks.
Real-World Example: Securing an E-commerce Platform with Falco, Sysdig, and Aqua Security
Let’s consider a real-world example: an e-commerce company running a Kubernetes cluster for their online store. They deploy microservices for payments, inventory, and customer data in separate containers.
Threat Scenario: A vulnerability in the payment processing microservice allows an attacker to execute unauthorized code within the container. The attacker then tries to elevate privileges to gain access to sensitive customer information stored in the database.
Runtime Security Implementation:
Falco monitors the Kubernetes environment and detects anomalous system calls as the attacker tries to access restricted database files.
Aqua Security enforces policies that prevent containers from running in privileged mode or mounting sensitive directories.
Sysdig provides detailed insights into the incident, allowing the security team to analyze the attacker's actions and mitigate the vulnerability for future deployments.
Sequence Diagram
Here’s an architecture illustrating how to implement runtime security in your Kubernetes environment:
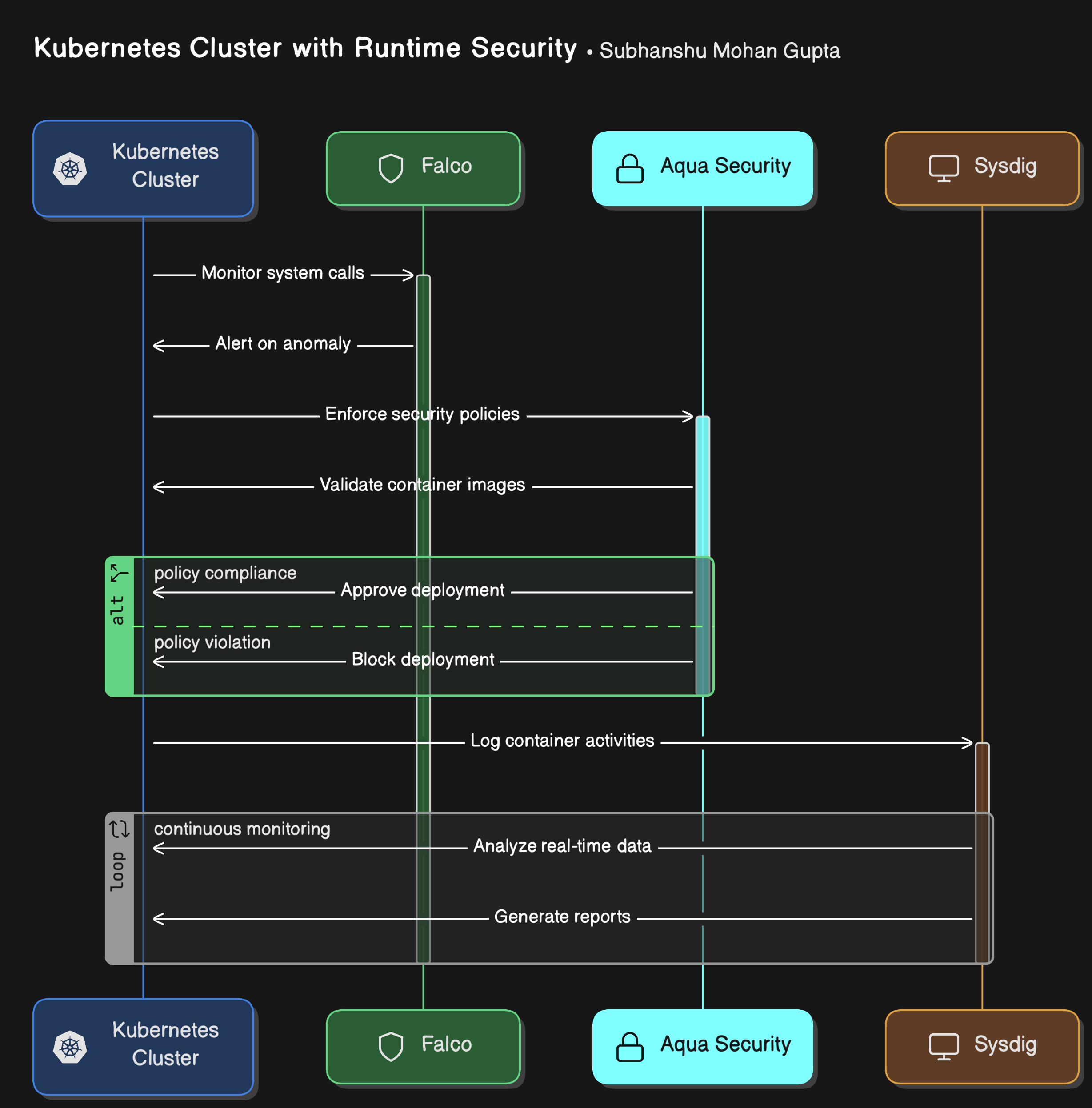
The architecture includes:
Kubernetes Cluster: Running various microservices in isolated containers.
Falco: Installed as a daemon set to monitor system calls and container activities across all nodes.
Aqua Security: Integrated into the CI/CD pipeline to enforce container security policies before deployment, and actively monitors runtime containers.
Sysdig: Integrated for monitoring, logging, and real-time analysis of container activities.
Implementation
To implement runtime security in your Kubernetes environment follow this step-by-step guide and it will take you through the necessary configurations, codes, and tools set up to secure your Kubernetes operations in real-time.
Step 1: Setting Up Your Kubernetes Cluster
Before we begin implementing runtime security, ensure that you have a Kubernetes cluster up and running. You can use Minikube for local testing or a cloud provider like GKE, EKS, or AKS for production.
# Start Minikube for local testing
minikube start
Make sure kubectl is installed and configured to interact with your cluster:
# Check the cluster status
kubectl cluster-info
Step 2: Installing Falco for Anomaly Detection
Falco is an open-source runtime security tool that monitors system calls and detects abnormal behaviour.
- Add the Falco Helm repository:
helm repo add falcosecurity https://falcosecurity.github.io/charts
helm repo update
- Install Falco using Helm:
kubectl create namespace falco
helm install falco falcosecurity/falco --namespace falco
- Verify the Falco installation:
kubectl get pods --namespace falco
Falco will now monitor system calls and generate alerts for any unusual activity. You can configure specific rules, such as detecting access to sensitive files:
# falco-rules.yaml
- rule: Unauthorized Access to Sensitive Files
desc: Detect access to sensitive files such as /etc/shadow
condition: open_read and fd.name in (/etc/shadow, /etc/passwd)
output: "Unauthorized access detected: %container.name (user=%user.name) trying to read %fd.name"
priority: WARNING
tags: [filesystem]
To apply custom Falco rules:
kubectl cp falco-rules.yaml falco/falco-<pod-name>:/etc/falco/falco-rules.yaml
kubectl exec -it falco-<pod-name> -- falco --reload
Step 3: Enforcing Security Policies with Aqua Security
Aqua Security enforces security policies on your containers to prevent vulnerabilities and secure runtime environments.
First, create an account on the Aqua Security website and deploy the Aqua Enterprise or Community Edition.
Install the Aqua Security Operator in your Kubernetes cluster:
kubectl apply -f https://deploy.aquasec.com/aqua-operator.yaml
- Deploy the Aqua Gateway and Console:
kubectl apply -f https://deploy.aquasec.com/aqua-console.yaml
- Create runtime policies in Aqua to prevent the execution of untrusted containers:
apiVersion: aquasec.com/v1alpha1
kind: RuntimePolicy
metadata:
name: block-privileged-containers
spec:
description: "Disallow privileged containers"
rule:
- action: "block"
match: { container: { privileged: true } }
- Apply the runtime policy:
kubectl apply -f block-privileged-containers.yaml
Aqua Security will now block any container that runs in privileged mode, enforcing strict container security policies.
Step 4: Monitoring and Incident Response with Sysdig
Sysdig allows you to monitor container activities and respond to incidents with deep visibility into container runtime behaviours.
Create a Sysdig account and get your agent installation command from the Sysdig Console.
Install Sysdig Agent on Kubernetes:
kubectl create namespace sysdig-agent
kubectl apply -f https://raw.githubusercontent.com/draios/sysdig-cloud-scripts/master/agent-k8s.yaml
- Configure your Sysdig agent with the API key you get from the Sysdig Console:
apiVersion: v1
kind: ConfigMap
metadata:
name: sysdig-agent-config
namespace: sysdig-agent
data:
dragent.yaml: |
api_key: YOUR_API_KEY
- Apply the Sysdig agent config:
kubectl apply -f sysdig-agent-config.yaml
- Verify Sysdig installation:
kubectl get pods --namespace sysdig-agent
Sysdig will monitor container activity in real-time and provide detailed information in the case of an incident. You can use the Sysdig CLI to inspect containers after detecting an anomaly with Falco.
For example, if Falco detects an unauthorized file access, use Sysdig to investigate:
sysdig -pc container.id=<container_id> evt.type=execve
This command lists all the commands executed within the compromised container, helping with incident analysis.
Step 5: Testing Runtime Security
Let’s simulate a security breach to test if the system is working.
- Deploy a simple vulnerable container that tries to access the
/etc/shadowfile:
apiVersion: v1
kind: Pod
metadata:
name: suspicious-pod
spec:
containers:
- name: suspicious-container
image: busybox
command: ["sh", "-c", "cat /etc/shadow"]
- Deploy the pod:
kubectl apply -f suspicious-pod.yaml
- Falco should trigger an alert since the container tries to read
/etc/shadow. You can check the logs:
kubectl logs -l app=falco -n falco
Aqua Security will block the deployment if the container is running in privileged mode (based on policies created earlier).
Sysdig will capture the activity, and you can analyze it for post-incident investigation.
Step 6: Setting Up Alerts and Dashboards
- Falco can be integrated with third-party systems like Slack, PagerDuty, or Elasticsearch for alerting:
helm install falco falcosecurity/falco --set falco.jsonOutput=true --namespace falco
- Sysdig provides a dashboard for monitoring runtime events. You can configure Sysdig’s alert system to notify you when suspicious activities occur.
Conclusion
By incorporating runtime security best practices with tools like Falco, Aqua Security, and Sysdig, you can detect, prevent, and mitigate threats in your Kubernetes environments. These tools work in synergy to provide full-stack protection, from monitoring system calls to enforcing security policies, ensuring that your containers stay secure even in production.
Start by adding these runtime security strategies to your Kubernetes workflow today, and safeguard your workloads from emerging threats before they impact your operations.
What’s next?
Stay tuned for the final chapter of this series where we’ll explore about -
Accelerating Deployment Velocity: Optimizing Build Times and Reducing Image Sizes in Kubernetes. In this upcoming article, we’ll focus on practical techniques to shrink Docker image sizes, optimize CI/CD pipelines, and speed up Kubernetes deployment cycles using tools like Kaniko for building images directly in Kubernetes, multi-stage builds, and caching strategies to enhance deployment speed and efficiency.
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.