An In-Depth Look at the Verizon 2024 Data Breach Investigations Report
 Aboelhamd Abdellatif
Aboelhamd Abdellatif
The 2024 Data Breach Investigations Report (DBIR) by Verizon is a crucial document that outlines the latest trends and patterns in cybersecurity breaches. As organizations increasingly rely on digital infrastructures, understanding the landscape of cyber threats has never been more critical. This year's report offers vital insights that can help businesses fortify their defenses.
Surge in Ransomware Attacks
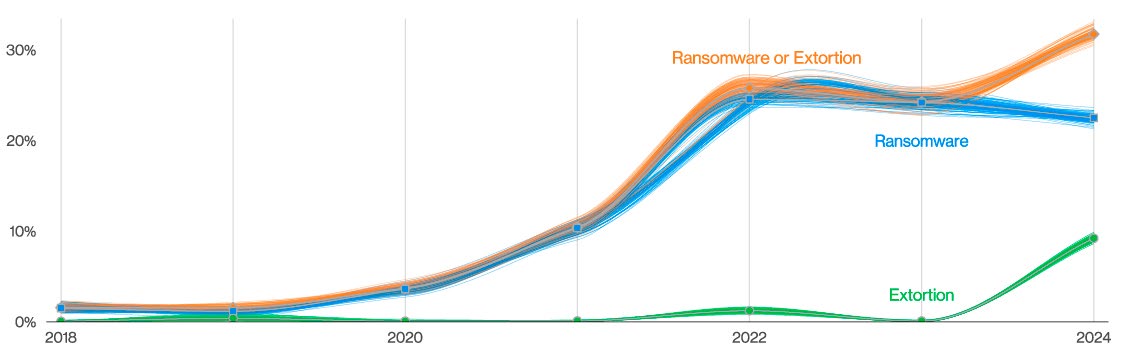
One of the most alarming findings from the report is the significant rise in ransomware incidents, which now account for 29% of all breaches. Ransomware attacks are especially prevalent in sectors like healthcare and government, where attackers know the potential for high payouts exists due to the sensitive nature of the data. These attacks often leverage advanced encryption techniques, locking organizations out of their own systems until a ransom is paid.
To combat this growing threat, organizations should implement multi-layered security strategies that include:
Regular data backups: Ensuring that backups are performed frequently and are stored offline can mitigate the impact of a ransomware attack.
Incident response plans: Having a well-defined plan allows organizations to respond swiftly to breaches and minimize damage.
Employee training: Regular workshops on identifying potential ransomware threats can empower staff to act as the first line of defense.
The Persistent Danger of Phishing
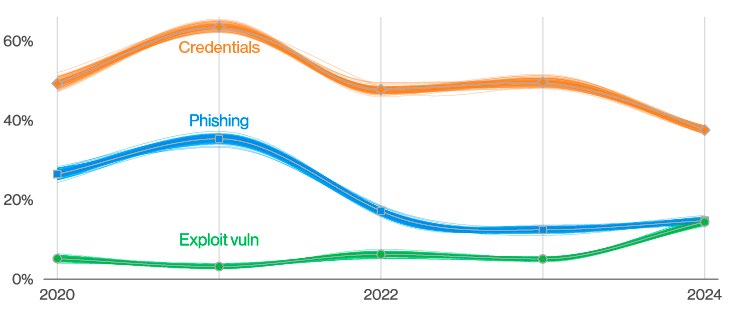
Phishing remains a prevalent threat, involved in 39% of reported breaches. Cybercriminals are becoming increasingly sophisticated, using social engineering tactics to manipulate individuals into revealing sensitive information or downloading malicious software. The report notes a shift toward more personalized phishing attempts, where attackers tailor messages based on victims’ social media activity or corporate communications.
Organizations can reduce the risks associated with phishing by:
Conducting simulated phishing exercises: Regular tests can help employees recognize phishing attempts and improve their response.
Implementing multi-factor authentication (MFA): This adds an extra layer of security, making it more difficult for attackers to gain unauthorized access.
The Rise of Insider Threats
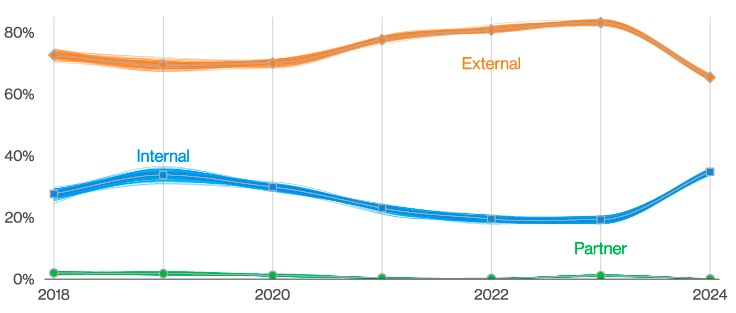
The report also sheds light on the growing significance of insider threats, which can originate from both malicious actors and well-intentioned employees who inadvertently compromise security. Insider threats accounted for a considerable portion of breaches, often resulting from inadequate access controls or insufficient employee training.
To combat insider threats, organizations should focus on:
Robust access control measures: Limiting access to sensitive information based on job roles can minimize risks.
Ongoing employee training and awareness programs: Regular updates on security protocols can help employees understand their responsibilities in protecting organizational data.
The Need for Proactive Cybersecurity Strategies
With the evolving landscape of cyber threats, the report emphasizes the necessity for organizations to adopt a proactive cybersecurity posture. This includes:
Regular security assessments: Organizations should conduct vulnerability assessments and penetration testing to identify and remediate weaknesses.
Investment in advanced threat detection technologies: Utilizing artificial intelligence and machine learning can enhance an organization's ability to detect and respond to potential threats in real time.
Sector-Specific Vulnerabilities
Different industries face unique cybersecurity challenges. For example, the healthcare sector is particularly vulnerable due to the value of patient data. Cybercriminals often target healthcare providers, knowing that compromised data can be sold on the dark web. By understanding these sector-specific threats, organizations can tailor their security measures to protect sensitive information effectively.
Conclusion
The 2024 Data Breach Investigations Report serves as a wake-up call for organizations to reevaluate their cybersecurity strategies. With ransomware, phishing, and insider threats on the rise, businesses must prioritize comprehensive security measures. By investing in employee training, enhancing threat detection capabilities, and adopting a proactive approach, organizations can better defend against the increasing frequency and sophistication of cyber threats.
For those interested in exploring these findings further, the full report is available here.
Subscribe to my newsletter
Read articles from Aboelhamd Abdellatif directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aboelhamd Abdellatif
Aboelhamd Abdellatif
Cybersecurity Infrastructure Specialist | Aspiring Penetration Tester With over 5 years of experience in designing and securing ICT infrastructures, I specialize in implementing systems that protect critical assets and ensure operational efficiency. My work focuses on enhancing security measures, ensuring compliance, and safeguarding environments against evolving cyber threats. Currently, I'm expanding my skill set in offensive security, having completed foundational courses on TryHackMe, including the Introduction to Cyber Security, Pre-Security, and Cyber Security Complete Beginner paths. Additionally, I hold hands-on certifications in BlackArch Linux, Netcat, and C++ for Pentesters from EC-Council, and I’m actively preparing for OSCP and CEH certifications to deepen my expertise in penetration testing and vulnerability assessment.
