Project Name:- Deploy an application on EKS and expose it using ALB Ingress controller.
 Sumit Kumar
Sumit Kumar
Prerequisite- Configure AWS CLI, install Kubectl and eksctl.
Step1- Create cluster using fargate.
eksctl create cluster --name demo-cluster --region us-east-1 --fargate
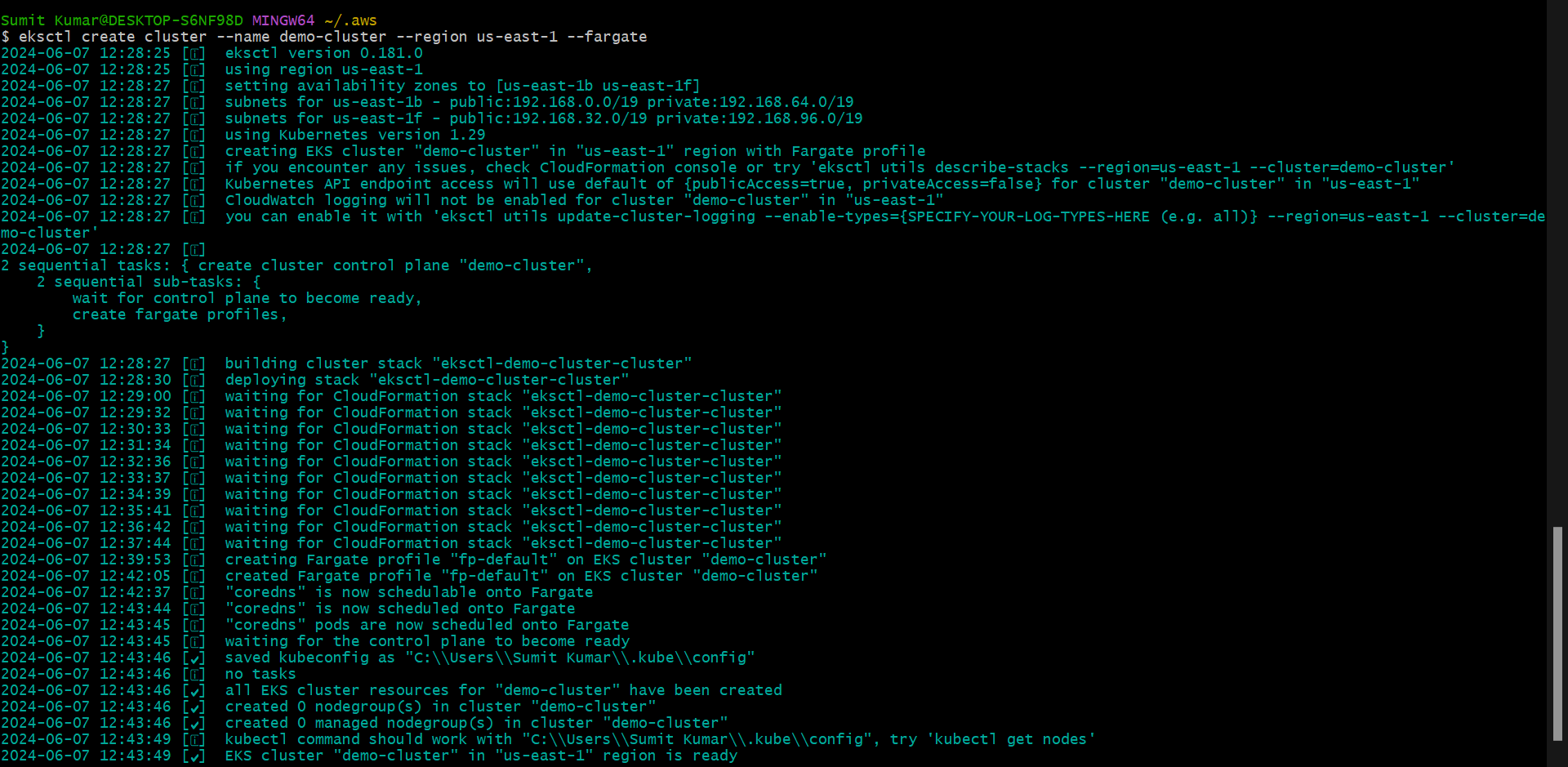
eksctl utility creates everything for us and it will take 10 to 15mins.
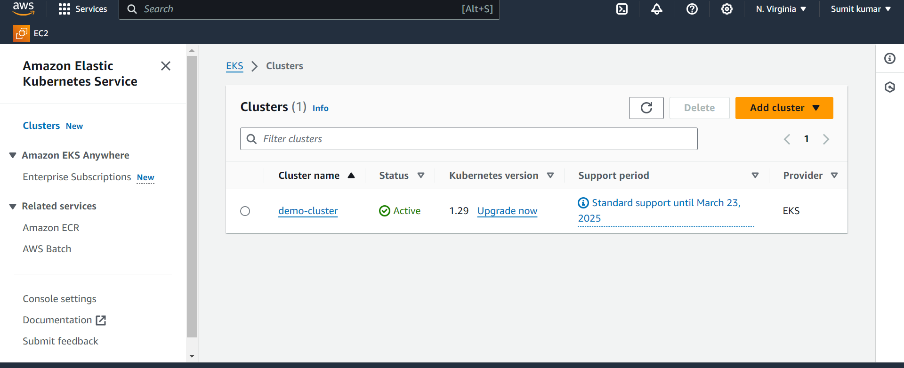
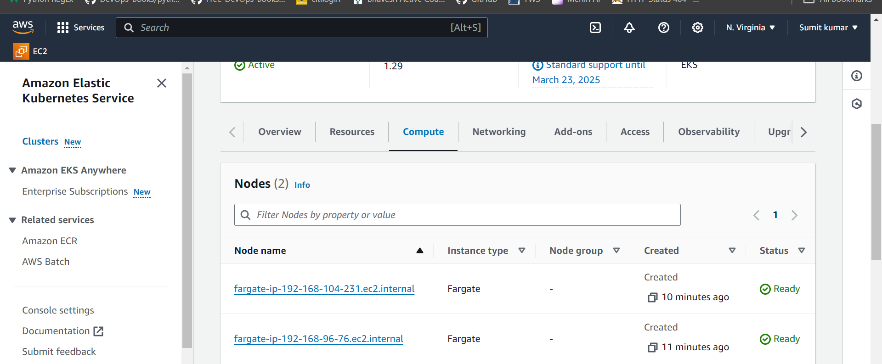
Step2- Change Context.
aws eks update-kubeconfig --name demo-cluster --region us-east-1
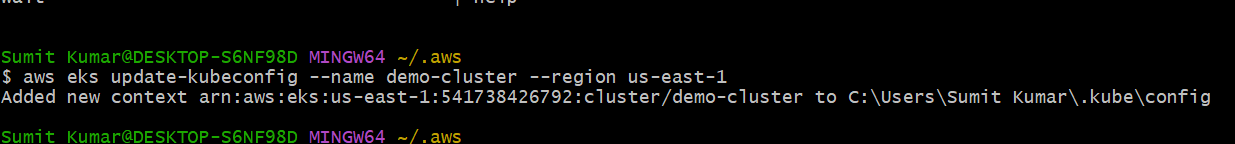
Step3- verify the current context.
kubectl config current-context
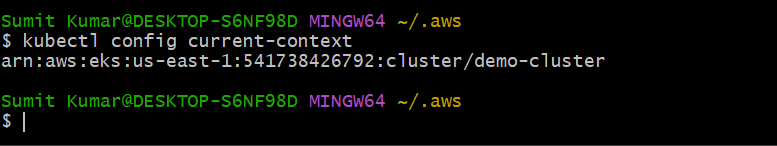
Nugget-A context tells kubectl which cluster to talk to. There could be many clusters.
Contexts are defined in the kubeconfig file. which is located at ~/.kube/config
Step4- Create fargate profile by name “alb-sample-app” and also create namespace for this
fargate profile by name “game-2048”.
eksctl create fargateprofile \
--cluster demo-cluster \
--region us-east-1 \
--name alb-sample-app \
--namespace game-2048
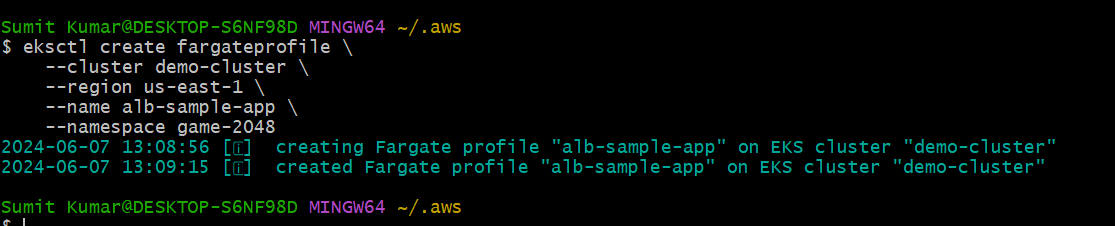
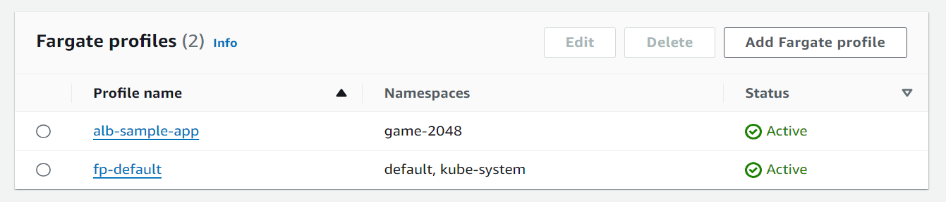
Nugget- Fargate profile specifies which pod should run on fargate based on namespsce.
Step5- Run this command
kubectl apply -f https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.5.4/docs/examples/2048/2048_full.yaml
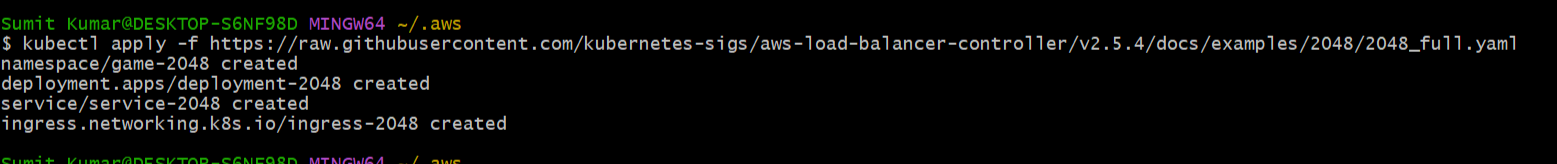
Nugget- ALB Ingress Controller will read ingress resource and whenever it will find the matching rule it will forward the request to service-2048 and service-2048 will forward the request to pod available in game-2048 namespace.
Actually here we have created deployment, Service and Ingress .Now we also have to install Ingress Controller. But before this lets see our resources are running or not?
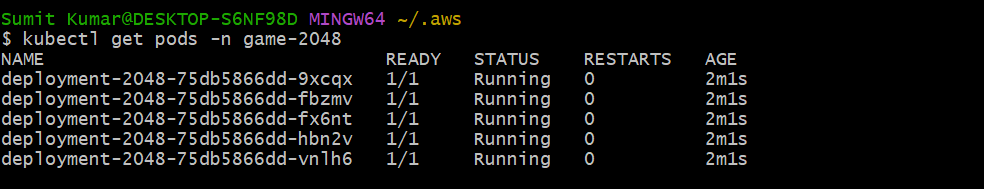
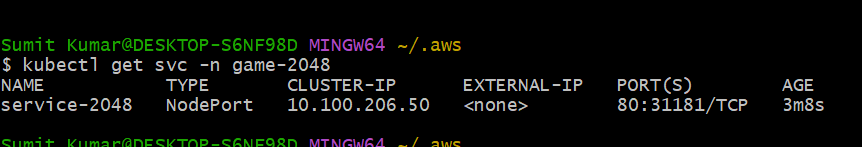
The service is also in running state. The service has the Cluster-IP and type is Nodeport but no external IP which means anybody which has access to VPC they can talk to this pod using the NODE-IP address followed by Port. But our goal is to make someone(user,customer) outside of AWS make access to this Pod. For that we have created Ingress.
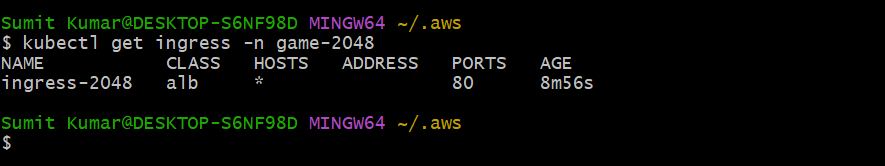
See ingress has also created☝️. It has class, port but there is no address. So when we will deploy Ingress controller then we will see address here. Now we will create Ingress controller that Will read ingress resource named ingress-2048 and it will create a ALB in AWS enviroment. Note that it Will not only create the ALB but also configure the ALB.
Step6- Run this command
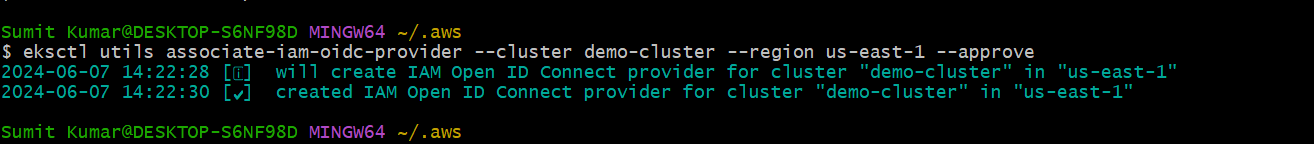
eksctl utils associate-iam-oidc-provider --cluster demo-cluster –region us-east-1 –approve
We are associating OIDC provider to the Cluster.
Nugget-To get secure and scalable access management for pods running in EKS cluster. We use service account and OIDC provider.
Every pod can use service account.Service account helps pod to interact with K8S APIs. EkS verify the identity of service account using token issued by OIDC Provider. K8S map the Service account to IAM role using OICD. So OIDC provider authenticate service Account.

Step7- Actually ALB controller is a pod and it has to talk to ALB so it needs a role. For this we first define IAM policy by;-
curl -O https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.5.4/docs/install/iam_policy.json
This will download policy and after that we have to create IAM policy by;-
aws iam create-policy \
--policy-name AWSLoadBalancerControllerIAMPolicy \
--policy-document file://iam_policy.json
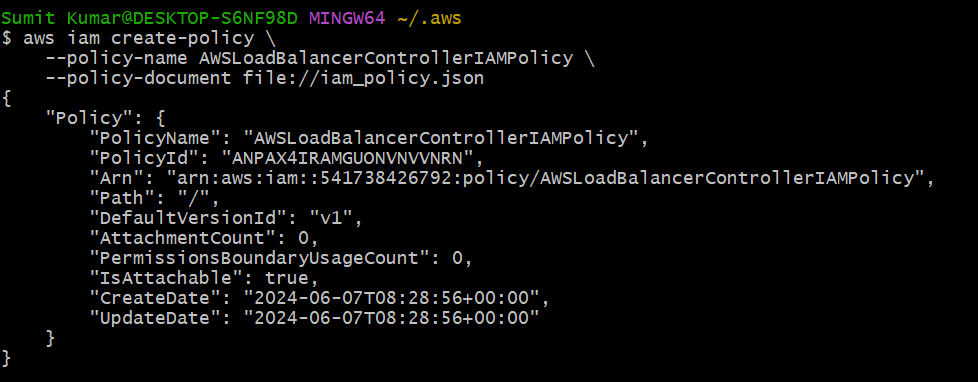
Now create role by;-
eksctl create iamserviceaccount \
--cluster=<your-cluster-name> \
--namespace=kube-system \
--name=aws-load-balancer-controller \
--role-name AmazonEKSLoadBalancerControllerRole \
--attach-policy-arn=arn:aws:iam::<your-aws-account-id>:policy/AWSLoadBalancerControllerIAMPolicy \
--approve
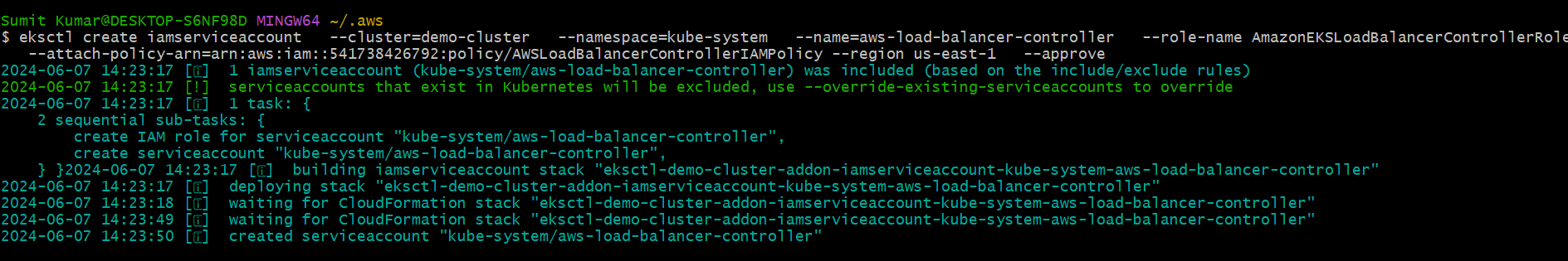
Here i am also attaching the role to the service account of the pod.
Step8- Run this command.
helm repo add eks https://aws.github.io/eks-charts
Step9- Run this command.
helm repo update eks
Step10- Run this command.
helm install aws-load-balancer-controller eks/aws-load-balancer-controller \
-n kube-system \
--set clusterName=demo-cluster \
--set serviceAccount.create=false \
--set serviceAccount.name=aws-load-balancer-controller \
--set region=us-east-1 \
--set vpcId=<your-vpc-id>
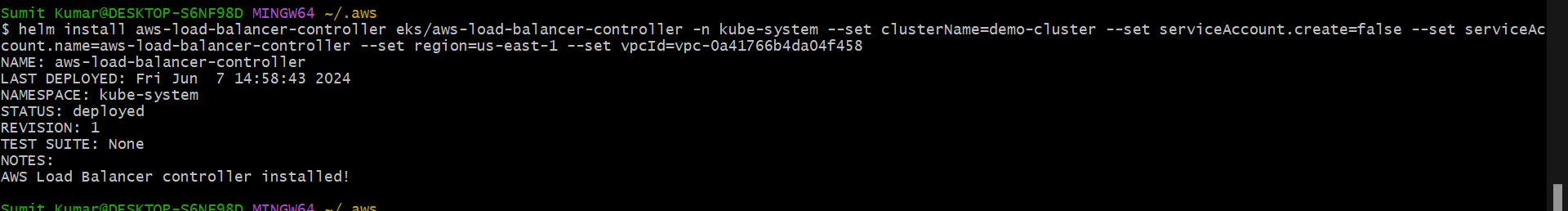
We have successfully installed load balancer controller.
Step11- Run this command.
kubectl get deployment -n kube-system aws-load-balancer-controller
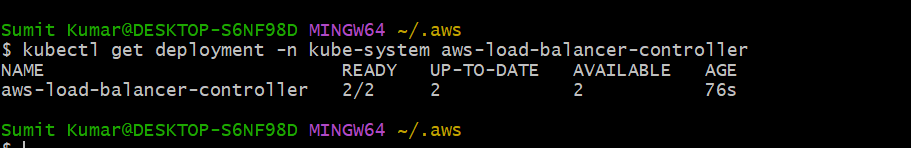
See load balancer controller(Ingress Controller) is working fine. It has two replicas. It will Continuously watches for ingress resources(ingress-2048) and it it will create ALB in two AZ. Now go to Aws and see if this Controller has created ALB or not?
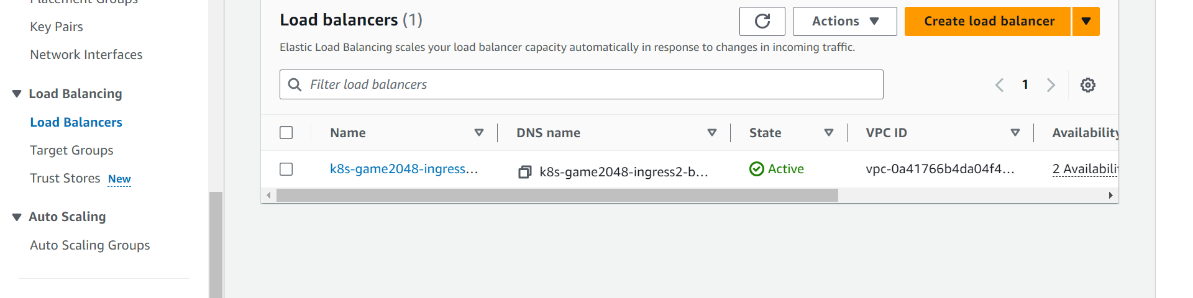
So it has created ALB successfully we can see☝️
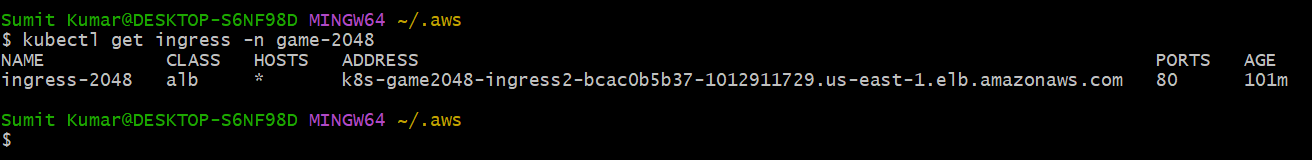
This address(k8s-game2048-ingress2-bcac0b5b37-1012911729.us-east-1.elb.amazonaws.com)is created by Ingress controller for load balancer by watching ingress resource.
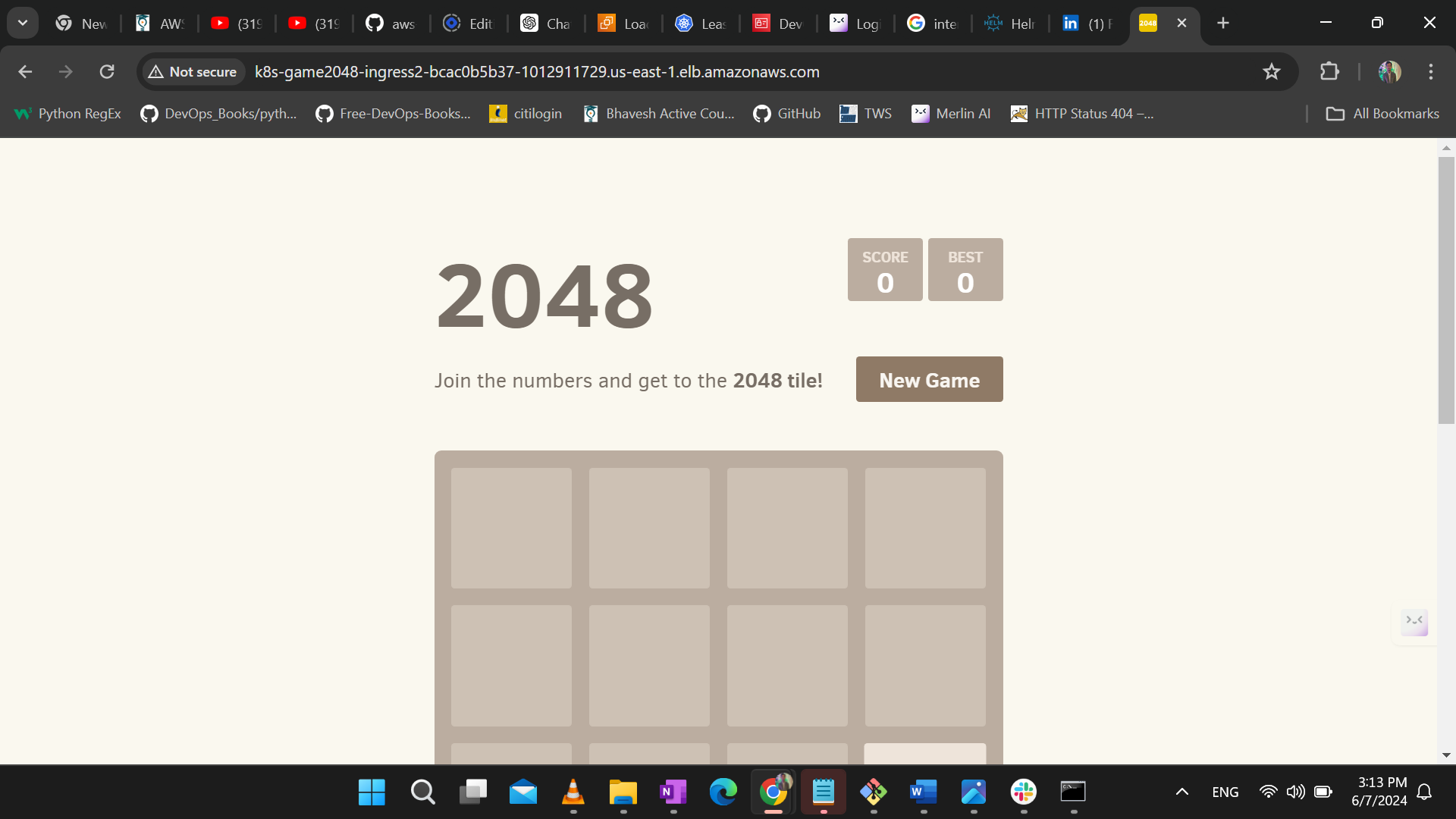
Step12- Now access the applicaton using this address on web browser.
Subscribe to my newsletter
Read articles from Sumit Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sumit Kumar
Sumit Kumar
DevOps Engineer