From Code to Cloud: Deploying an Azure Virtual Network with Terraform
 Rabiatu Mohammed
Rabiatu MohammedTable of contents
Terraform is an Infrastructure as Code (IaC) tool that allows you to define, build, and manage cloud infrastructure. Instead of manually configuring resources in Azure, Terraform lets you write code to automatically create and manage these resources. In this post, I’ll show you how I used Terraform to create an Azure Virtual Network (VNet), Subnet, Network Security Group (NSG), and a Virtual Machine (VM).
Initializing Terraform: (terraform init)
Before we can start deploying our resources, we need to initialize Terraform. This step downloads all the necessary provider plugins, like the Azure provider, and sets up your working directory.
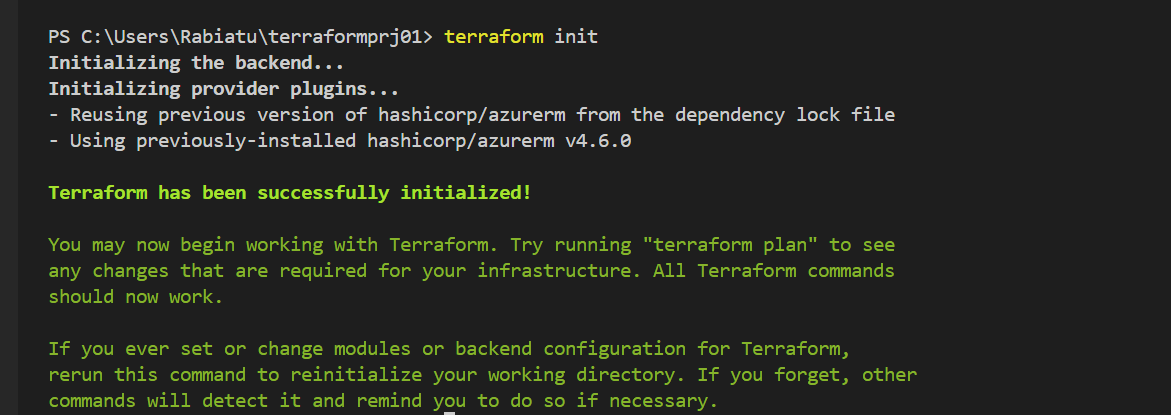
This command initializes the working directory and prepares it for the upcoming Terraform operations. After running terraform init, Terraform is ready to deploy your infrastructure.
Getting Started with Terraform
First, let's start by setting up Terraform for Azure. You need to use the azurerm provider for this, which tells Terraform that you're working with Azure resources.
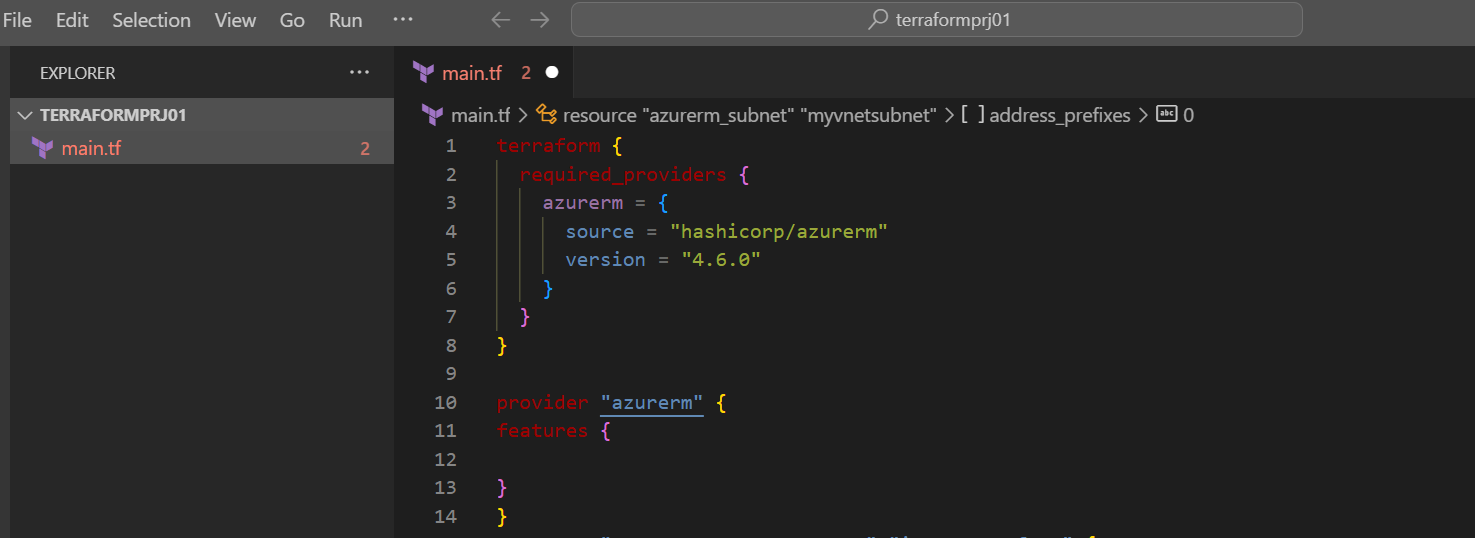
This block of code just says: "Hey Terraform, we're working with Azure resources, and here’s the provider version we're using."
Creating a Resource Group
In Azure, all resources are organized into Resource Groups. The first step in my deployment was to create a resource group called terraformIT in the UK South region. A resource group is essentially a container that helps you keep all related resources together.
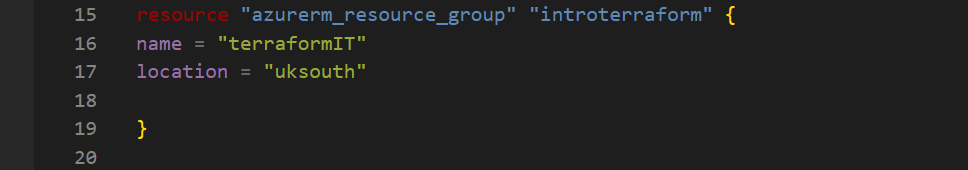
Setting up a Virtual Network (VNet) and Subnet
Next up, I created a Virtual Network (VNet). A VNet is like a private network in the cloud, where all your resources (like VMs) communicate securely. I also created a subnet, which is a smaller network inside the VNet.
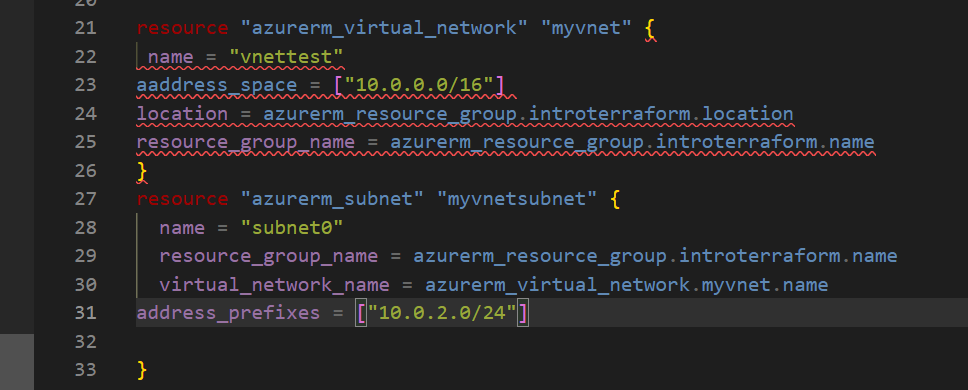
This defines
The VNet with an address range of
10.0.0.0/16, where my cloud resources will communicate.The subnet uses a smaller address range (
10.0.2.0/24) to organize and control traffic within the VNet.
Securing the Network with a Network Security Group (NSG)
Security is critical in the cloud, so I created an NSG to control inbound and outbound traffic for the subnet. Here, I configured the NSG to allow SSH access so I can remotely connect to the VM later.
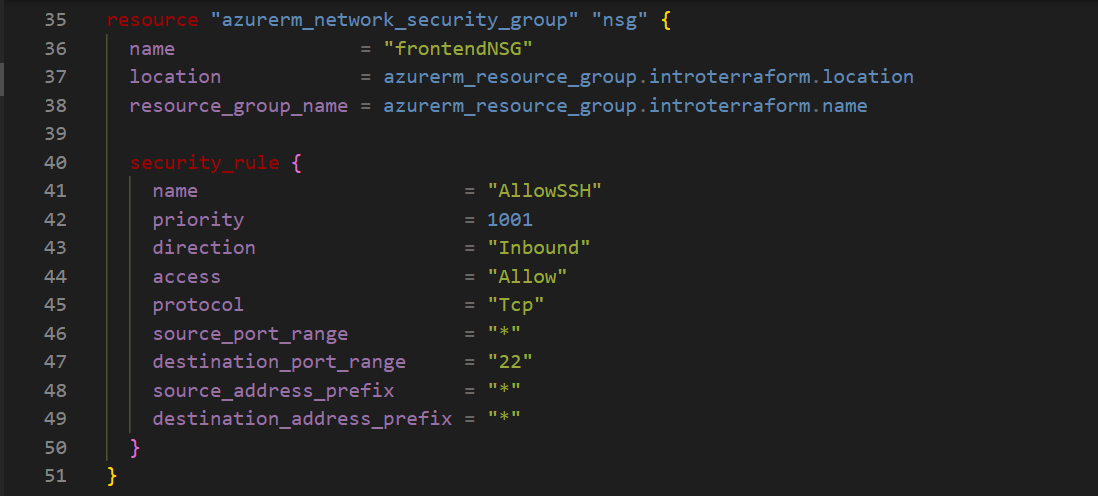
This NSG allows SSH traffic over port 22, which I’ll need to access my VM.
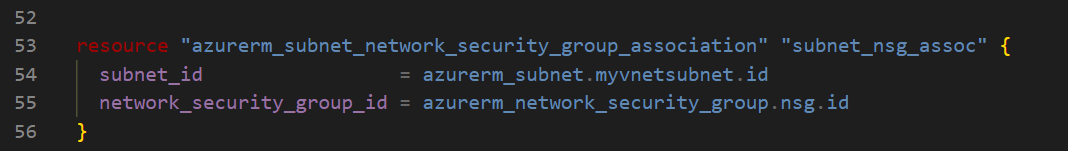
Associating the NSG with the Subnet
To apply the security rules to the resources in my subnet, I associated the NSG with the subnet using the following code:
Previewing Changes
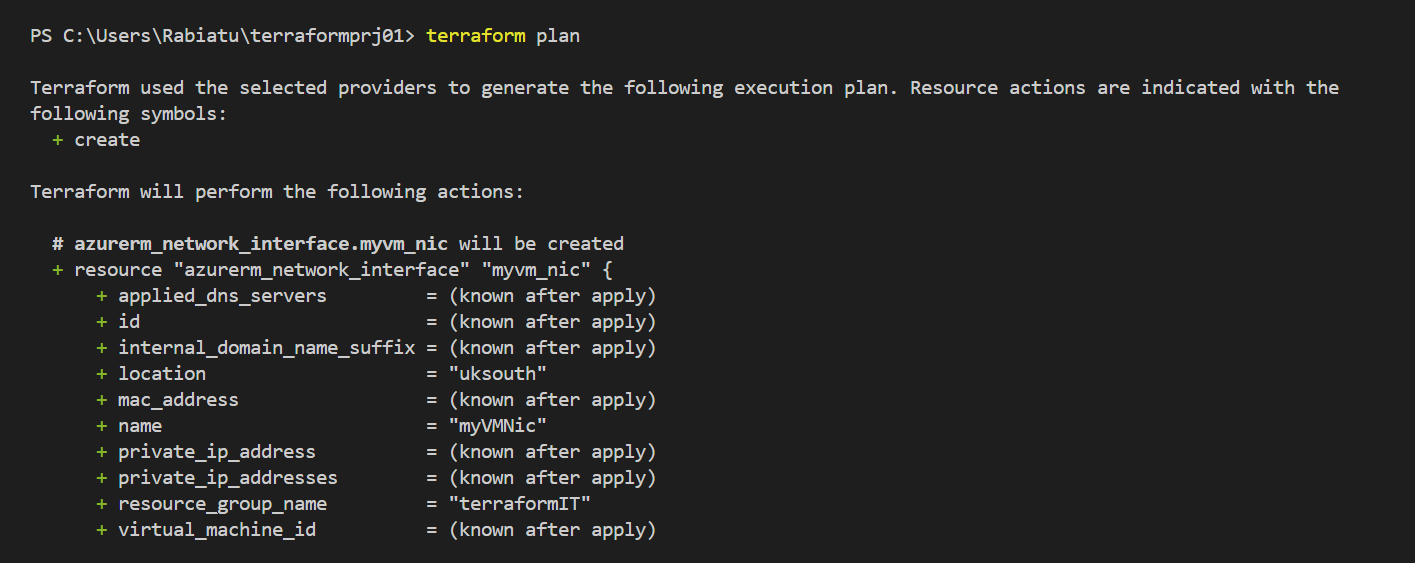
Before applying changes, it’s good practice to run terraform plan. This previews what Terraform is going to do and shows you any potential issues.
Applying the Configuration
Once I was happy with the plan, I ran terraform apply to deploy my infrastructure.

Terraform will ask for confirmation before proceeding with the deployment. After confirming with yes, Terraform will start creating the resources.
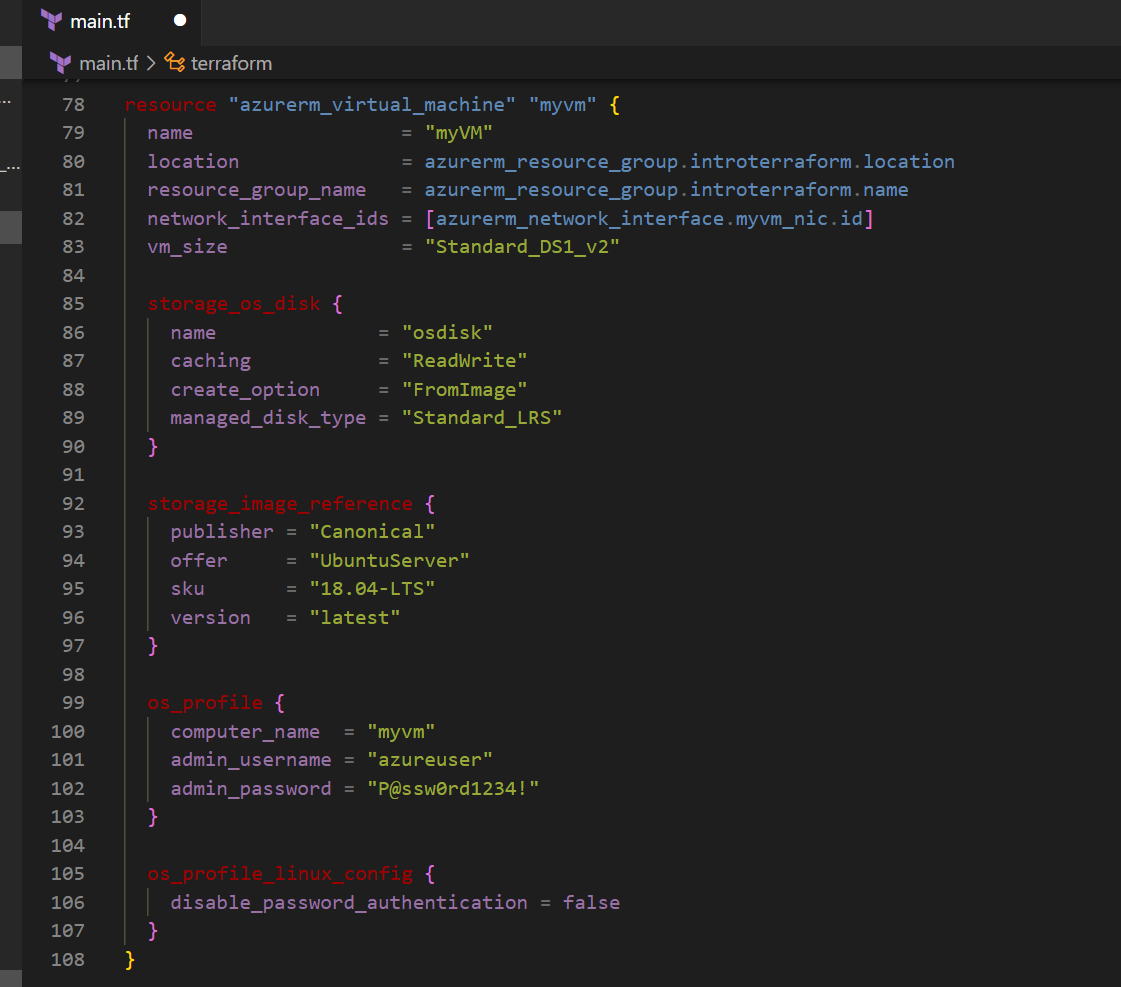
Deploying a Virtual Machine (VM)
Finally, I deployed an Ubuntu Virtual Machine. This VM will live in the subnet, and I’ll be able to access it via SSH.
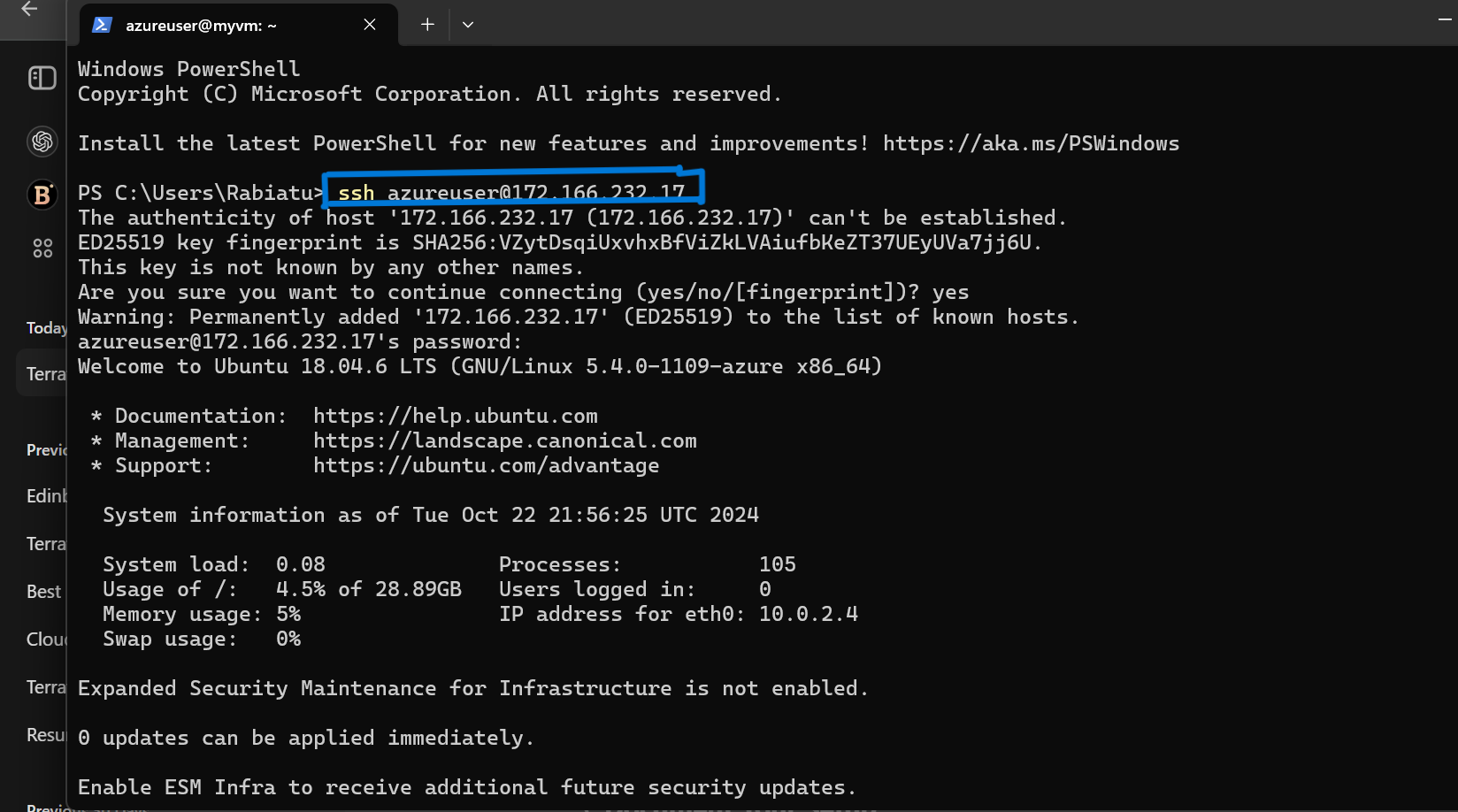
Connecting to the Virtual Machine
Once the VM was successfully deployed, I was able to connect to it using SSH. Since I allowed SSH traffic through the Network Security Group (NSG) on port 22, I could remotely manage the VM.
To connect, I used the following command in my terminal:
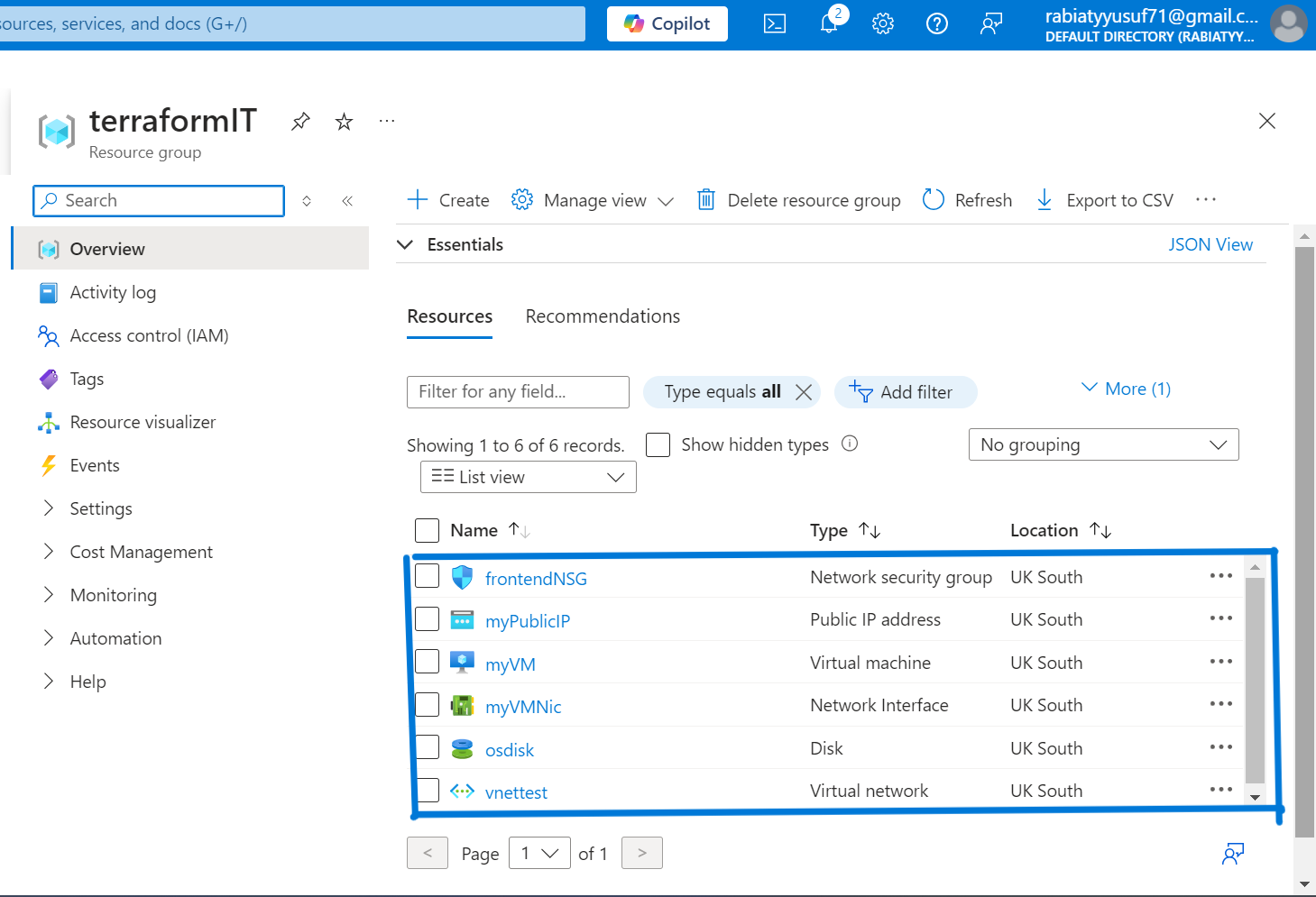
Verifying the Deployed Resources:
After running terraform apply, I checked the Azure portal to verify that all the resources were successfully deployed. As shown in the screenshot below, the Virtual Network (vnettest), Network Security Group (frontendNSG), Virtual Machine (myVM), and other components were created and listed in the terraformIT resource group:
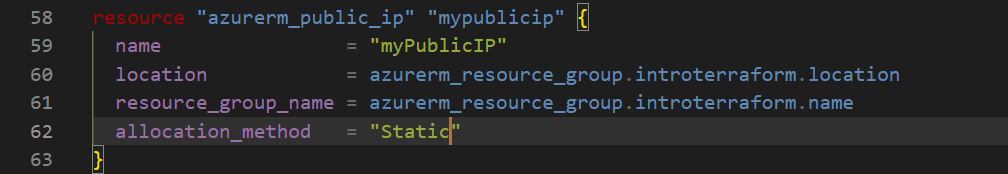
Lessons Learned
During this process, I encountered a few challenges, such as the static IP allocation requirement for Standard SKU public IP addresses. To fix this, I had to set the allocation_method to "Static" in my Terraform configuration:
Cleaning Up the Resources
Once I had everything working and no longer needed the infrastructure, I ran terraform destroy to clean up the resources and avoid any ongoing costs:
And that’s it! I successfully deployed an Azure Virtual Network, NSG, and VM using Terraform. If you’re just starting out with Terraform, this is a great hands-on project to familiarize yourself with automating cloud infrastructure.
Subscribe to my newsletter
Read articles from Rabiatu Mohammed directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rabiatu Mohammed
Rabiatu Mohammed
I work on securing, automating, and improving cloud environments. Always exploring better ways to build reliable, secure infrastructure.