Understanding SSH: A Gateway to Secure Remote Connections
 Shagufta Gulnaar Mohammed
Shagufta Gulnaar Mohammed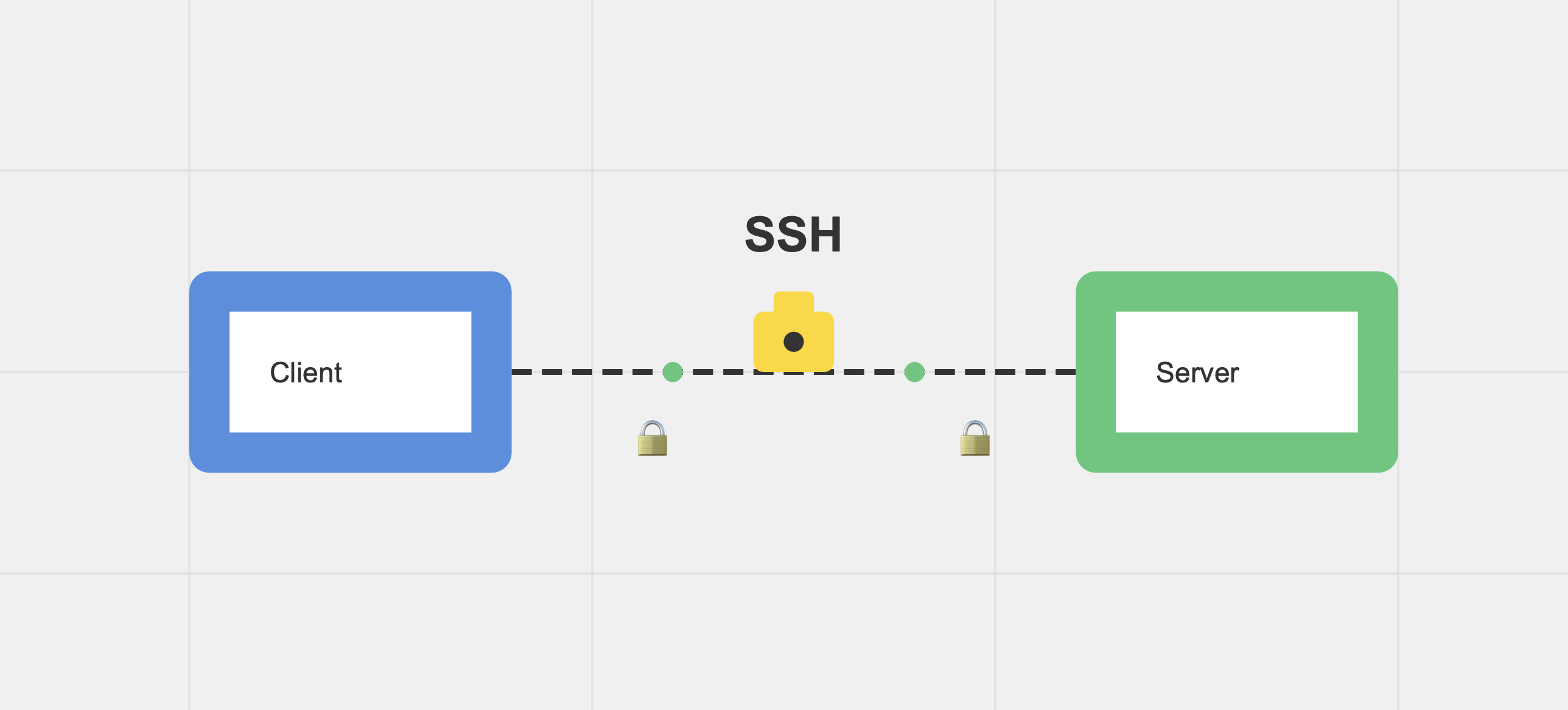
In this blog, we'll explore how SSH works, focusing on connecting to an EC2 instance and the importance of keys in securing your connection.
What is SSH?
SSH (Secure Shell) is a network protocol that allows you to connect to a remote system securely over an unsecured network. In simple terms, it lets you log on, control, and modify your server from your local machine.
How SSH Works
Imagine your computer and the remote machine (e.g., an EC2 instance) both have their own "shell" or command-line interface. These shells communicate securely using SSH, protected by a mechanism known as public and private key authentication. Without the correct private key, you won’t be able to access the remote machine.
Public Key: This key resides on the remote server (like an EC2 instance). It is publicly available and doesn’t need to be hidden.
Private Key: This key is kept secret on your local machine. It’s required to connect to the remote server.
The idea is that if you possess the private key, you can securely connect to the remote server that has the corresponding public key. If your private key is missing or not correctly set up, you won’t be able to gain access.
Steps to Set Up SSH Key-Based Authentication
Connecting to an AWS EC2 Instance from Your Local Machine
To connect to an EC2 instance, follow these steps:
Create an EC2 Instance: During setup, you'll be asked to create a new key pair. Save the private key (.pem file) generated during this process.
Download the Key: After creating the key pair, your browser will automatically download the private key. This key will be used to establish a connection to your EC2 instance.
Use SSH to Connect: Here’s an example command to connect using your private key:
ssh -i your-private-key.pem ec2-user@your-ec2-instance-public-dnsOpen Your SSH Client: This is your terminal. Type
ssh. If you receive valid output, it means SSH is installed and ready to use.Navigate to Your Key Location: Move to the directory where your private key is stored:
cd /path/to/your-key-directoryChange File Permissions: Set the correct permissions for your key to ensure its security:
chmod 400 your-private-key.pemConnect to the Remote Server: Finally, run the SSH command to connect:
ssh -i your-private-key.pem ec2-user@your-ec2-public-ip
Connecting from Local to Remote via SSH Key Generation
To connect to the remote EC2 instance by generating a key pair on the remote server:
SSH into the Remote EC2 Server:
ssh user@remote_server_ipNavigate to the .ssh Directory:
cd ~/.sshGenerate SSH Key Pair on the Remote Server:
ssh-keygen -t rsa -b 4096This command creates:
Private Key (e.g.,
id_rsa)Public Key (e.g.,
id_rsa.pub)
Append the Public Key to
authorized_keys:cat id_rsa.pub >> authorized_keysThis adds the public key to the
authorized_keysfile, allowing authentication from the corresponding private key.Copy the Private Key from the Remote EC2 Server to the Local Server:
- Caution: Copying the private key can pose security risks. Ideally, generate the key pair on your local machine instead. If you still need to copy it and have SSH access, use:
scp ~/.ssh/id_rsa user@local_server_ip:~/.ssh/
Ensure the Private Key File on Your Local Server Has the Correct Permissions:
chmod 400 ~/.ssh/id_rsaConnect from the Local Server to the Remote Server: Now, you can SSH into the remote server using the private key:
ssh -i ~/.ssh/id_rsa user@remote_server_ip
Connecting One EC2 Server to Another EC2 Server Using SSH
If you need to connect one EC2 server to another, follow these steps:
The first EC2 server (EC2-server-1) should have the private key file (key-pair.pem) that allows access to the second server (EC2-server-2).
Move to the .ssh Directory on EC2-server-1:
cd ~/.sshCopy the Key-Pair: Place the private key (key-pair.pem) in the .ssh directory.
Connect from EC2-server-1 to EC2-server-2: Use the SSH command to initiate a connection:
ssh -i key-pair.pem ec2-user@EC2-2-ip
By following these steps, you can set up secure communication between two servers, making it easier to manage distributed environments.
Summary
SSH is a secure way to connect to remote machines, and understanding the roles of the public and private keys is crucial for managing this connection. Always ensure your private key is secure, use strong pass-phrases when possible, and only share it when absolutely necessary.
Subscribe to my newsletter
Read articles from Shagufta Gulnaar Mohammed directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
