How to Set Up Custom URLs for Oracle Autonomous Database with Customer-Managed ORDS 24.3 and Let's Encrypt
 Timo Herwix
Timo Herwix
Introduction
In the first part of this series, we showed you how to install and configure a Customer-Managed ORDS 24.3 for an Autonomous Database. We walked you through installing an ORDS standalone instance and running it on port 8080 without SSL encryption, which is suitable for initial development. However, ORDS can also be set up to run over HTTPS for secure communication. You can use a self-signed certificate for development, but for production, it's best to use your own SSL certificate to ensure that your SSL certificates are trusted by clients and browsers, providing a higher level of security and trustworthiness.
Setting up HTTPS for your Customer-Managed ORDS offers another significant advantage: your own Custom URL. This boosts your brand identity and makes your Oracle Autonomous Database more memorable 🚀
In this guide, we'll cover the steps required to configure ORDS with HTTPS and your own custom URL 🔐
Prerequisites
If you've already followed the first part of this series, you can jump right into the next steps 😉
If not, please read the first part to see how to set up an Autonomous Database and Compute Instance. Follow the steps until you have provisioned an ADB and VM and completed everything on the VM up to the step "Installing and Configuring Customer-Managed ORDS"
The last step you should have completed is: sudo yum install ords -y

DNS Setting
Before we start, we need to make our DNS settings. To do this, go to your domain provider and add an "A" record in the DNS settings with the Public IP address of the compute instance so that the VM is mapped to the domain.
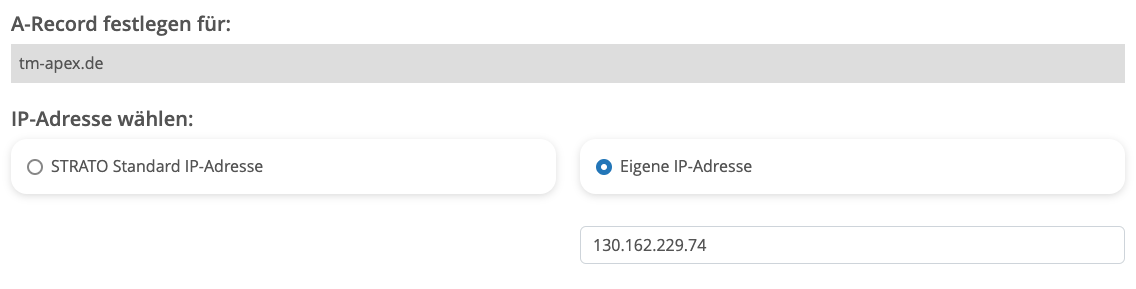
This mapping is essential for the next steps, where we will configure ORDS to use HTTPS and set up your custom URL. With the DNS settings in place, your domain will direct traffic to your compute instance, allowing users to access your Oracle Autonomous Database securely and efficiently.
Configure Firewall and Ingress Rules
Next step is to make sure you have an OCI Security List rule that opens port 80 (HTTP) and 443 (HTTPS) to make it accessible to your client machine. On the Compute instance, you also need to ensure that the firewall port for HTTP and HTTPS is open.
Just run the following command as opc or root user:
sudo firewall-cmd --permanent --zone=public --add-service=http
sudo firewall-cmd --permanent --zone=public --add-service=https
sudo firewall-cmd --reload
Next, we need to update the Ingress Rules for the VCN to allow incoming HTTP and HTTPS traffic. So it is not enough to open the VM's firewall.
Navigate to "Networking > Virtual Cloud Networks" and select the VCN where the VM is located. Under "Resources" click on "Security Lists" and there on the "Default Security Lists" of your network.
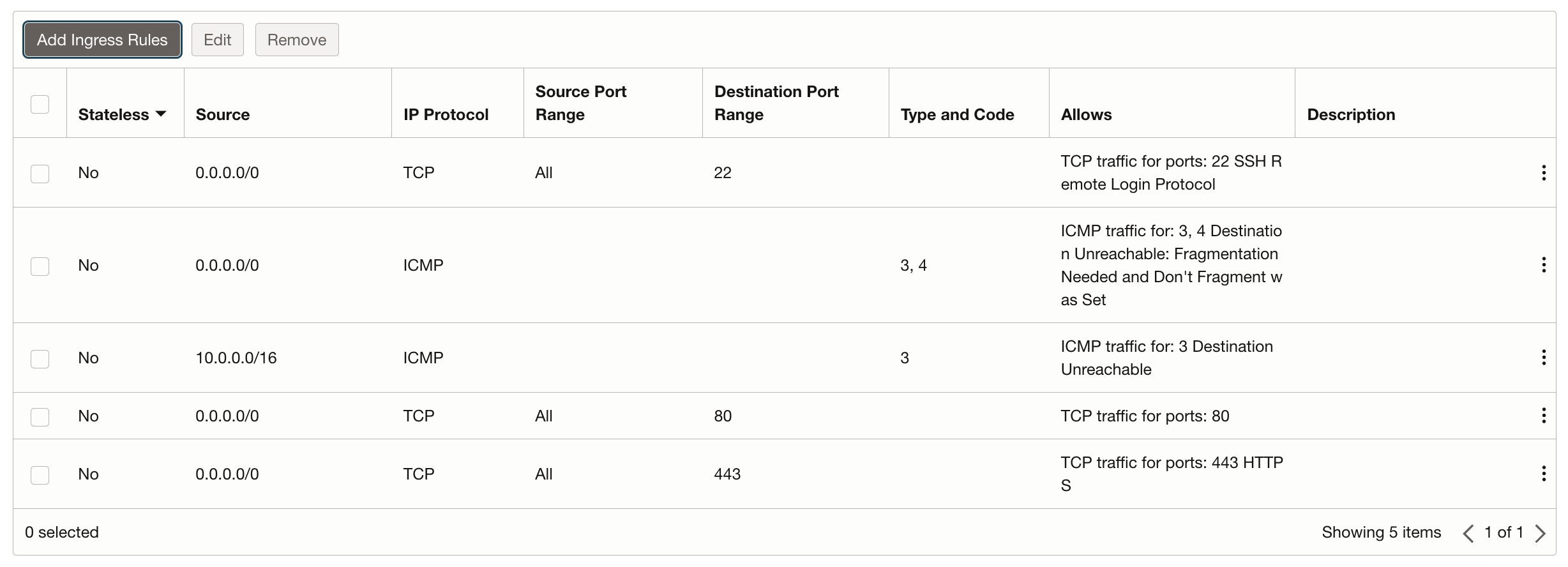
For HTTP and HTTPS traffic, we need two more rules. So click on "Add Ingress Rules".
Select CIDR as Source Type and as Source CIDR enter 0.0.0.0/0 so that everything can connect to it, and as Destination Port Range enter 80 for the first rule (HTTP) and 443 for the second rule (HTTPS).
If you've set up some rules for HTTP as we mentioned in the previous blogpost, you can remove them by running the following command:
sudo firewall-cmd --remove-port=8080/tcpYou can do the same thing in the OCI Console for the Ingress Rule for Port 8080. Just go ahead and remove that entry.
Finally, let's add a couple more firewall rules for our Customer-Managed ORDS. By default, ORDS uses port 8443 or another high port, but the standard port for HTTPS is 443. Wouldn't it be great to use the default HTTPS port directly for ORDS without needing an extra web server or proxy?
Here's the deal: Linux doesn't let non-privileged users open ports below 1024, and running ORDS as root isn't a great idea. The easiest fix is to use another firewall rule to set up an internal port-forward. So, let's allow incoming traffic on port 443 and then forward all that traffic to port 8443.
Just run this command as the opc or root user:
sudo firewall-cmd --permanent --add-port=8443/tcp
sudo firewall-cmd --permanent --add-forward-port=port=443:proto=tcp:toport=8443
sudo firewall-cmd --reload
To ensure that all your firewall rules are configured correctly, you can run a command to list all the active rules. This will help you verify that the rules have been applied as intended and that there are no conflicts or missing entries.
Execute the following command to display all the current firewall rules:
sudo firewall-cmd --list-all
This command will provide a detailed overview of your firewall settings, including the active zones, services, ports, and other configurations. The output should look something like this:
public (active)
target: default
icmp-block-inversion: no
interfaces: ens3
sources:
services: dhcpv6-client http https ssh
ports: 8443/tcp
protocols:
forward: no
masquerade: no
forward-ports:
port=443:proto=tcp:toport=8443:toaddr=
source-ports:
icmp-blocks:
rich rules:
In this example, you can see that ports 80, 443, and 8443 are open for TCP traffic. Additionally, there is a forward-port rule that redirects traffic from port 443 to port 8443. This setup ensures that ORDS can use the standard HTTPS port (443) while internally forwarding the traffic to its default port (8443).
No SSL Certificate? Use Let's Encrypt for that!
If you don't have a valid SSL certificate, you can use Let’s Encrypt! Let’s Encrypt is an SSL certificate authority managed by the Internet Security Research Group (ISRG). It uses the Automated Certificate Management Environment (ACME) to automatically provide free SSL certificates that are trusted by almost all major browsers. For most cases, the best way to install Let’s Encrypt certificates is by using the official Certbot tool. Certbot makes it easy to get and install a certificate, and it can even update your web server configuration automatically. Just follow the steps below to install Certbot and get your certificate.
From a terminal, connect to your Oracle Cloud VM first:
ssh -i ssh-key-my-customer-ords.key opc@130.162.229.74
Next, switch to the root user by using the following command.
sudo su
Then, enable the EPEL repository for your Oracle Linux version.
cd /tmp
wget https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
rpm -Uvh /tmp/epel-release-latest-8.noarch.rpm
Next, install snapd which is an App Store for Linux.
# install snapd
dnf install -y snapd
systemctl enable --now snapd.socket
systemctl start snapd
ln -s /var/lib/snapd/snap /snap
# install and refresh core
snap install core
snap refresh core
Finally, install CertBot.
# install certbot
snap install --classic certbot
ln -s /snap/bin/certbot /usr/bin/certbot
Now we can run CertBot with the following command.
certbot certonly -d tm-apex.de --key-type rsa
You will be asked a few things to answer.
In the end, it should look something like this:
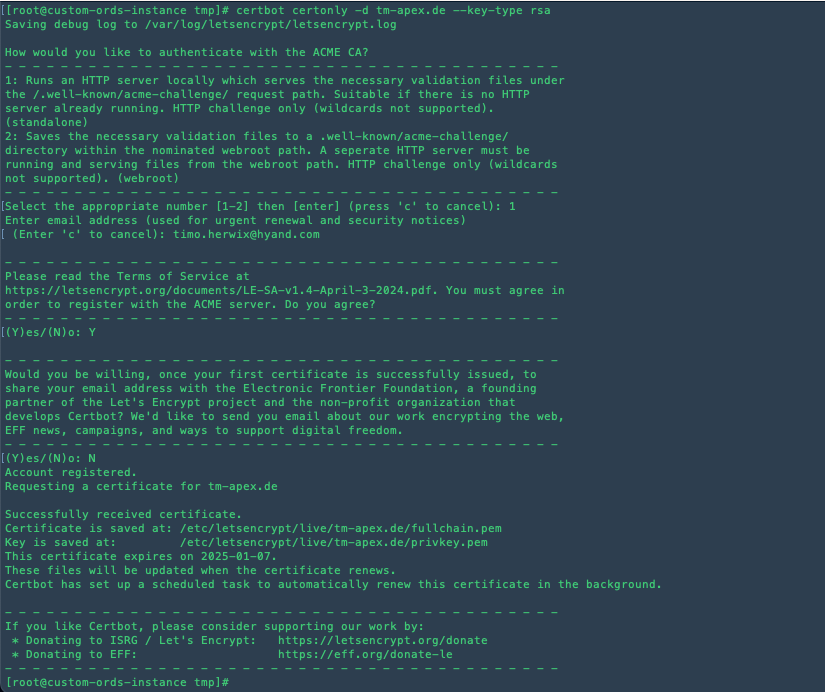
By following these steps, you can easily secure your website with a free SSL certificate from Let’s Encrypt, ensuring that your users' data is protected with industry-standard encryption.
Finally, create a directory /etc/pki/ords and change its ownership to oracle:oinstall. Then, copy the SSL certificate and private key from the Let's Encrypt directory to /etc/pki/ords, and set the permissions of both files.
mkdir /etc/pki/ords
chown -R oracle:oinstall /etc/pki/ords/
cp /etc/letsencrypt/live/tm-apex.de/fullchain.pem /etc/pki/ords
cp /etc/letsencrypt/live/tm-apex.de/privkey.pem /etc/pki/ords
chmod 644 /etc/pki/ords/fullchain.pem
chmod 644 /etc/pki/ords/privkey.pem
Configuring Customer-Managed ORDS
Now we can start configuring our Customer-Managed ORDS. To do this, switch the user to oracle with the following command.
sudo su - oracle
To ensure that we can execute ords commands from any directory, we need to update the .bash_profile file for the oracle user. This will allow us to set up the environment variables and paths correctly. You can use any text editor you prefer. In this example, we'll use vi:
vi ~/.bash_profile
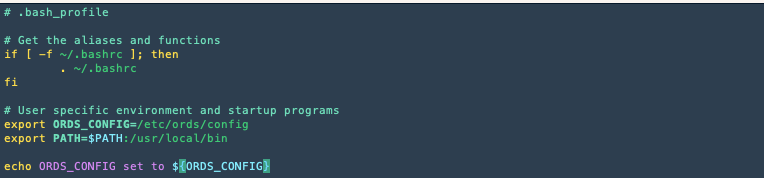
Add the following lines to the end of the file. These lines will set the environment variables and update the PATH to include the directory where ords is installed:
export ORDS_CONFIG=/etc/ords/config
export PATH=$PATH:/usr/local/bin
echo ORDS_CONFIG set to ${ORDS_CONFIG}
It should look something like this:
In vi, you can save and close the file by pressing Esc, typing :wq, and then pressing Enter. To apply the changes made to the .bash_profile, run the following command:
source ~/.bash_profile
Next, we need to adjust the connection pool settings to ensure optimal performance and resource management. This step is crucial for handling multiple database connections efficiently. To do this, execute the following command:
ords config set jdbc.InitialLimit 1
ords config set jdbc.MaxLimit 3
ords config set jdbc.MinLimit 0
You can adjust this numbers based on what your application needs and how much traffic you expect.
The next step is to configure your Customer-Managed ORDS. Use the ORDS Command-Line Interface (CLI), which will guide you through the setup by asking for the necessary information.
ords install adb --interactive --prompt-password
Enter the following installation prompts to continue:
Entering the Autonomous Database Wallet Path: /opt/oracle/Wallet.zip
Enter a number to select the TNS Network alias to use: e.g. 1
Enter the Administrator Username: ADMIN
Enter the Database Password for ADMIN: Password1234!
Entering the ORDS Runtime Database Username: ORDS_PUBLIC_USER2
Entering the Database Password for ORDS_PUBLIC_USER2: Password1234!
Entering the PL/SQL Gateway Database Username: ORDS_PLSQL_GATEWAY2
Enter the Database Password for ORDS_PLSQL_GATEWAY2: Password1234!
Entering a Number to Select and Enable Additional Feature: 1
Enter a Number to Configure and Start ORDS: 1
Entering a Number to Select a Protocol: 2
Entering the HTTP Port: 8443
Enter a number to select the certificate type: 2
Enter the path for the SSL Certificate:
/etc/pki/ords/fullchain.pemEnter the path for the SSL Certificates private key:
/etc/pki/ords/privkey.pem
When you're all done, it should look something like this.
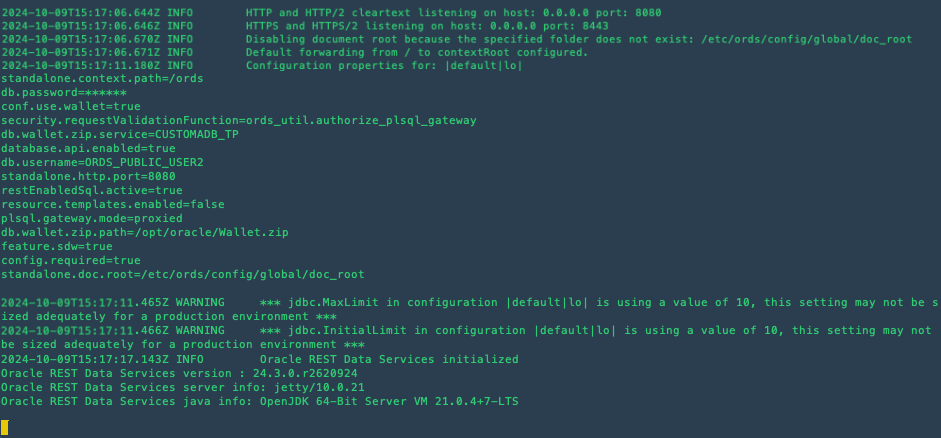
After setting these properties, it's a good practice to review and verify the configuration to ensure that all settings align with your performance goals. You can do this by checking the configuration files or using the ORDS management commands to list current settings:
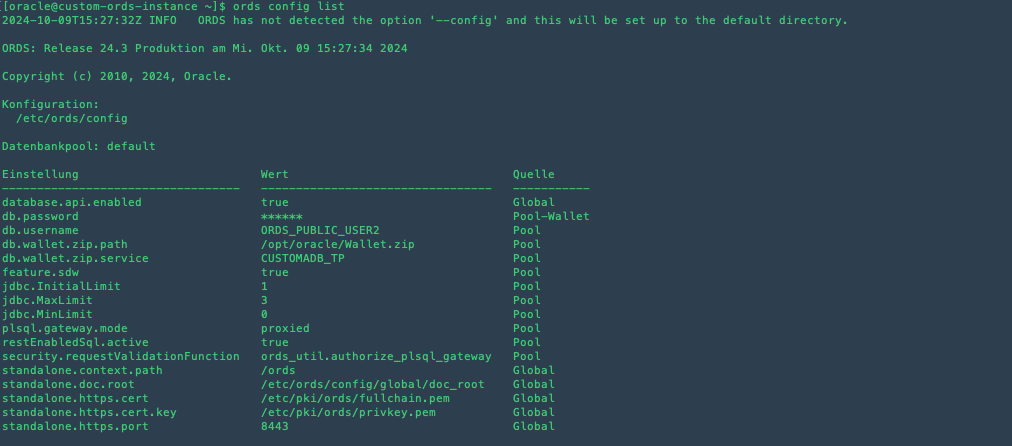
ords config list
This command will display all the current configuration properties, allowing you to confirm that your changes have been applied correctly.
Start your Customer-Managed ORDS
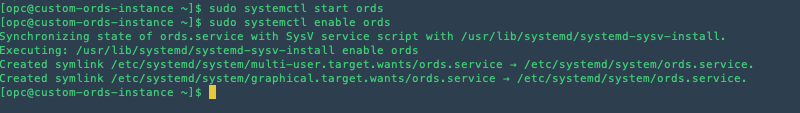
Finally, let's start ORDS and set it up to start automatically on boot with the following command.
sudo systemctl start ords
sudo systemctl enable ords
Test your Customer-Managed ORDS
With the setup now complete, you can access APEX or SQL-Developer Web using HTTPS and your own custom URL 🚀
https://tm-apex.de
Conclusion
Configuring a Customer-Managed ORDS with HTTPS and a Custom URL for your Oracle Autonomous Database significantly enhances security and brand identity. By following this guide, you can ensure secure communication through SSL certificates, streamline access with Custom URLs, and optimize database performance. With Let's Encrypt, obtaining and installing SSL certificates is straightforward and cost-effective. Setting up the necessary DNS, firewall, and ORDS configurations ensures a robust and secure environment, making your Oracle Autonomous Database both secure and easily accessible 👍
References
Subscribe to my newsletter
Read articles from Timo Herwix directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Timo Herwix
Timo Herwix
Timo joined Hyand in Ratingen, Germany, as a Senior Consultant in 2019, focusing on Oracle databases and APEX applications. With a background as a Data Warehouse Specialist, he has expertise in Database Administration, performance tuning, and SQL development. Timo is passionate about web development, cloud computing, and the architecture behind it, and became part of the Oracle ACE Community in 2023. He enjoys sharing his knowledge at conferences and through blog posts. When he's not working, you can find him traveling, hanging out with his family, or cooking up something in the kitchen.