Admir - The Great Admin Access Heist! - NRF24CTF
 kurtnettle
kurtnettleProblem Statement
In the heart of the digital world lies a powerful admin panel known as Admir—an interface that controls the core functionalities and sensitive data of a high-stakes web application. Hidden from the eyes of most, this admin panel is believed to contain secrets capable of altering the course of events in the cyber realm. However, the guardians of Admir, convinced of their impenetrable defenses, have overlooked one critical flaw: a logical vulnerability in their authentication process.
You, a daring cybersecurity enthusiast, have been entrusted with a mission of utmost importance. Your objective? To exploit this oversight, bypass the login restrictions, and unveil the hidden treasures within Admir. Will you emerge victorious, or will the guardians discover your infiltration?
Prerequisites
- Burpsuite (basic request manipulation)
Solution
The first thing after seeing a web challenge I do is firing up the burpsuite.
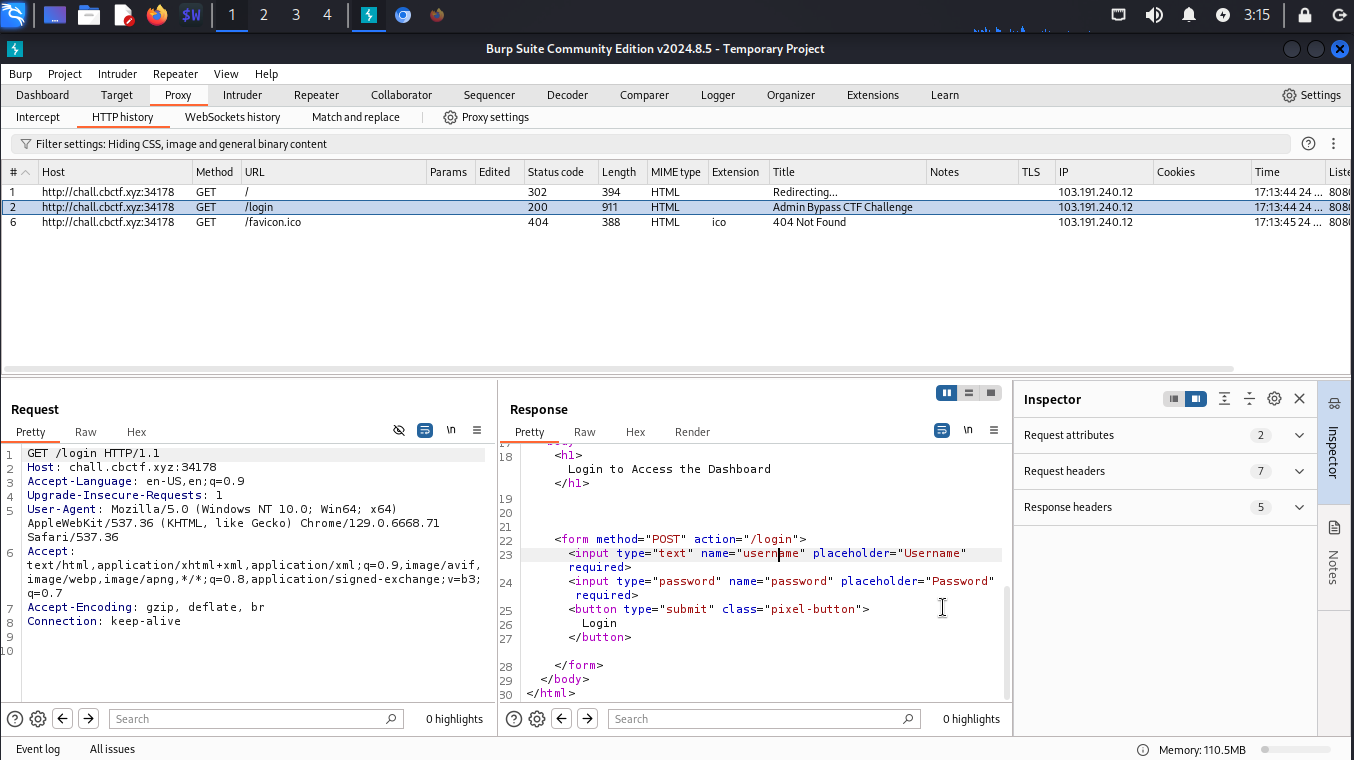
We can see a form and the first thing came to my mind was this must some injection problem. I tried random credentials at first like admin admin later some common sql injection to see if the website throws any error but I didn’t get any.
Well, not all paragraphs are useless; sometimes they are helpful and you should read them well :) I read the statement with patience again and was looking for clues. The part “logical vulnerability” immedietly clicked on my mind.
Did they forget to use a proper if-else statement when checking the credentials? We've all done basic if-else tasks and we know what can go wrong if we use incorrect logic in the program :) Maybe the server is checking the username and password separately or forgot to include a && in the condition part :3
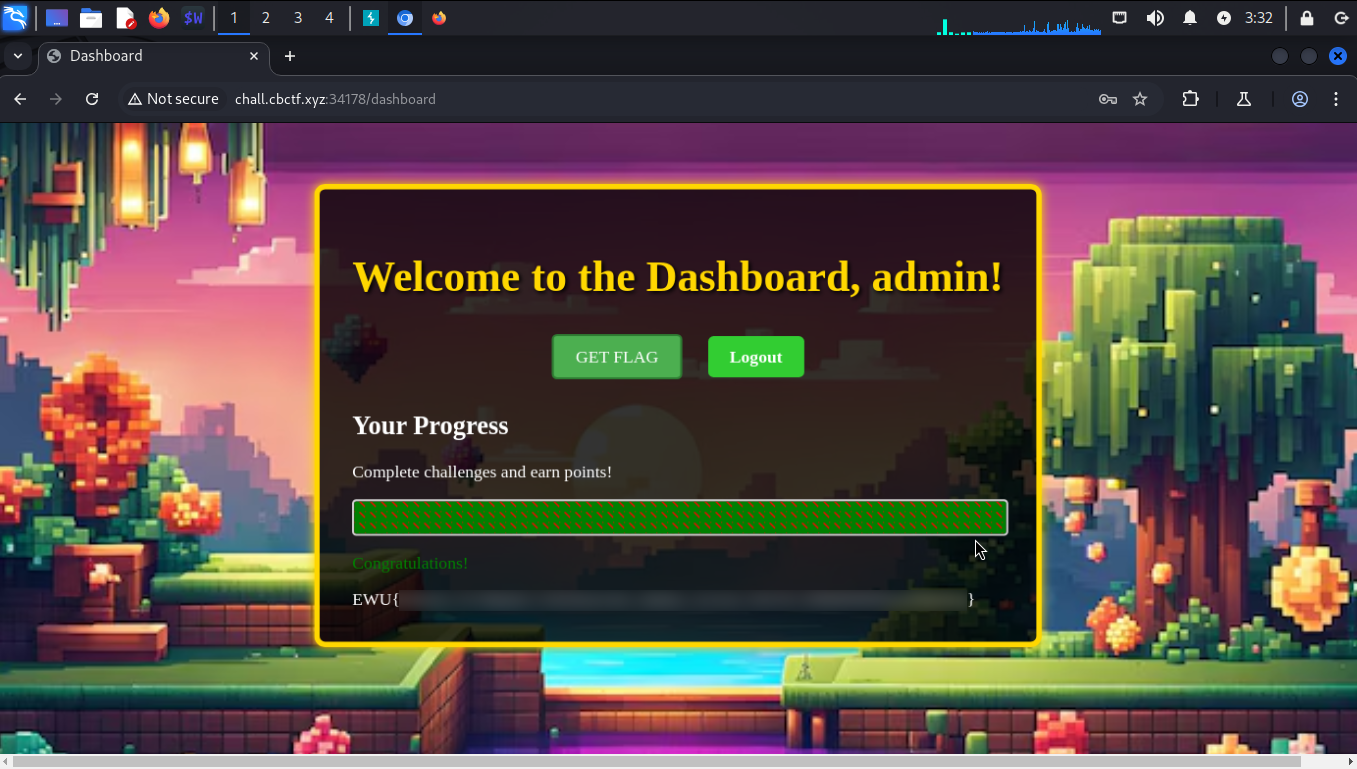
So, theoretically, if we can guess the username correctly, we should get the flag.
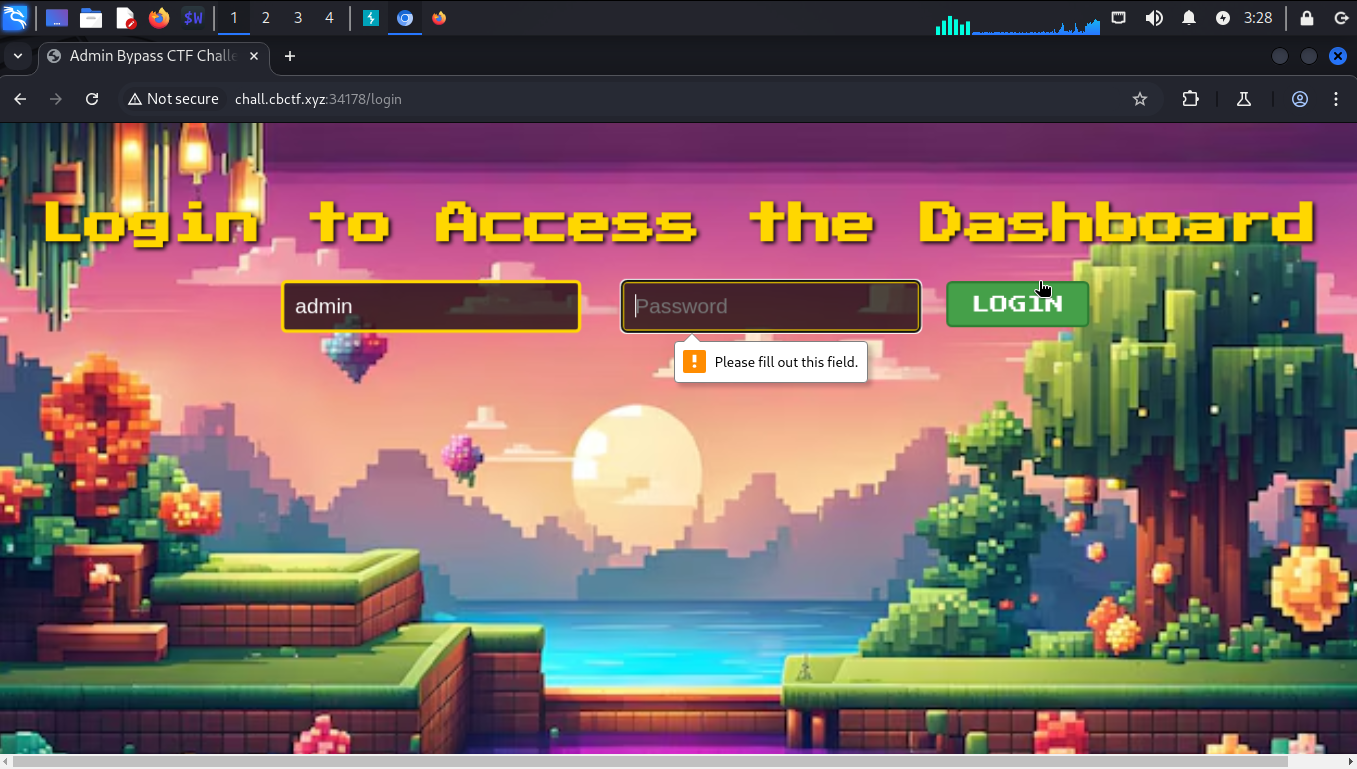
Ah, it's not letting us send just the username. Let's intercept the request then.
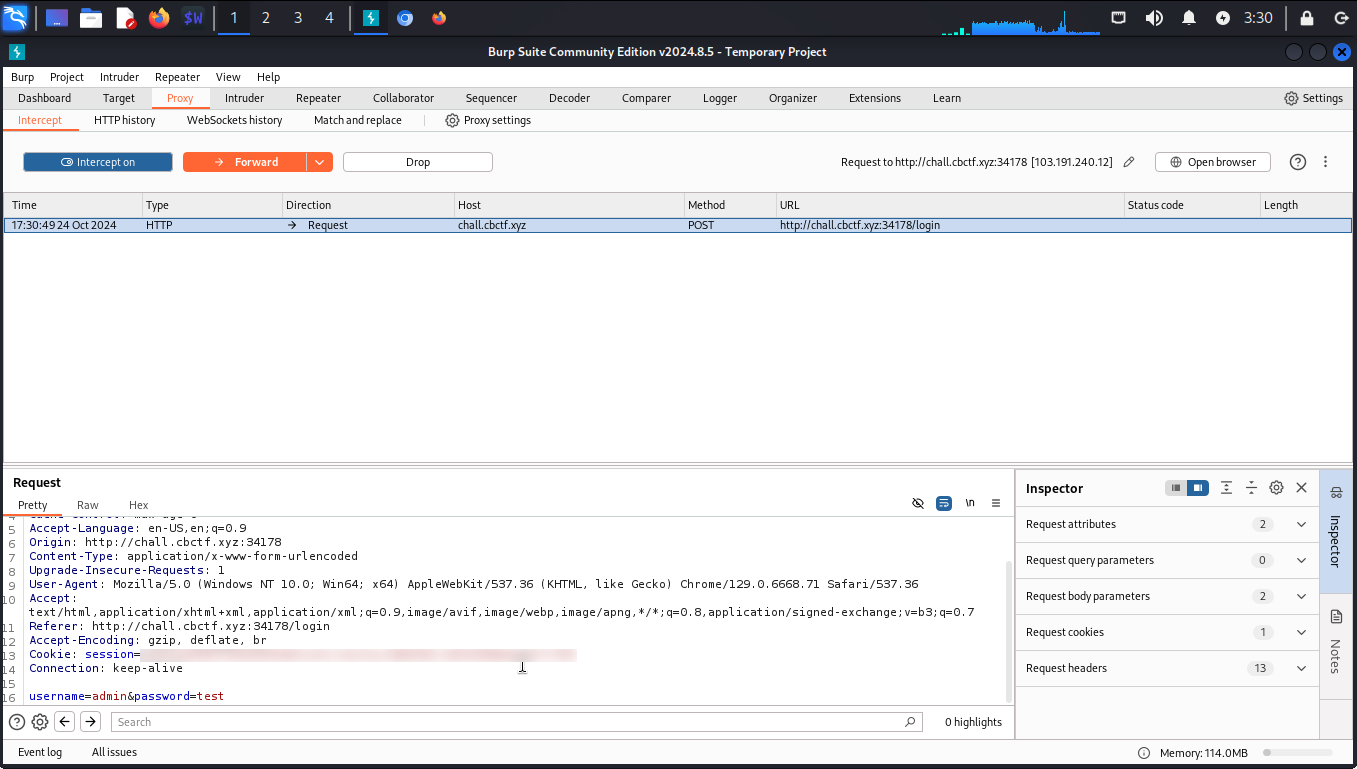
Removing the parameter password should do the work.
Another Solution
We can do this in another way too :3 I didn't include 'inspect element' in the prerequisite list because it would be a big spoiler for the write-up 😂 and I wouldn't be able to show off my burpsuite skills.
Do you remember earlier when we couldn't send just the username because the form was asking for a password? It was because of a HTML attribute required
(Yeah, I know. You'll just remove it now, no need to read further. Cya never)
Have a great day!
Alright, let’s see what happens after removing it.
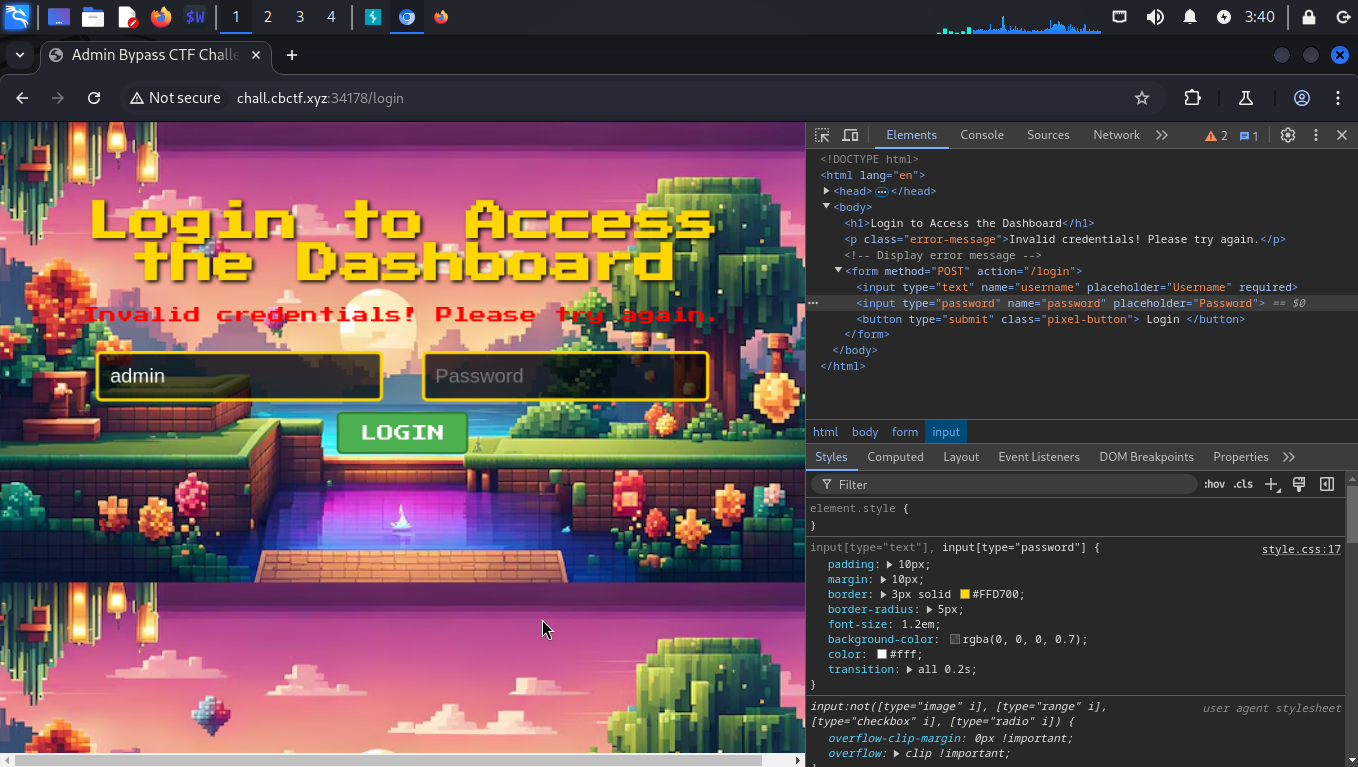
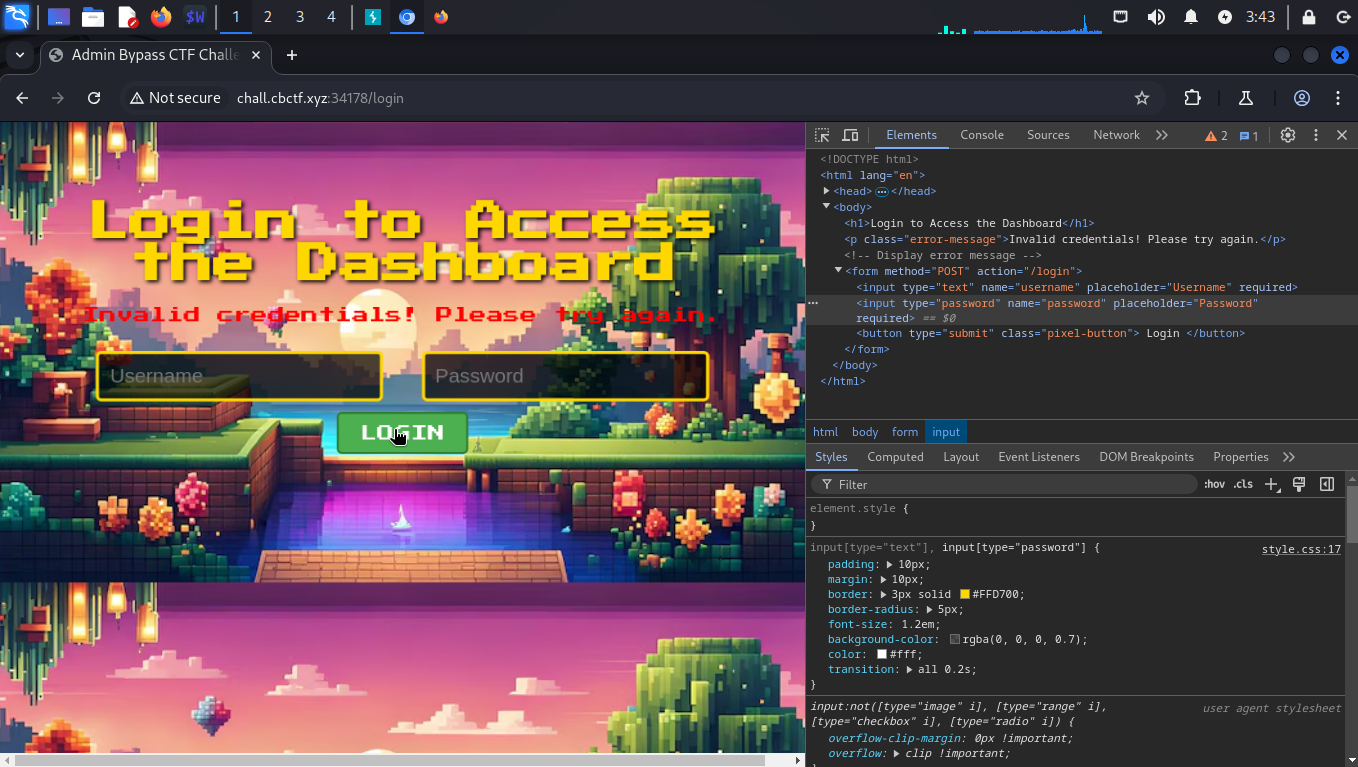
It’s showing incorrect password 😂 But why?
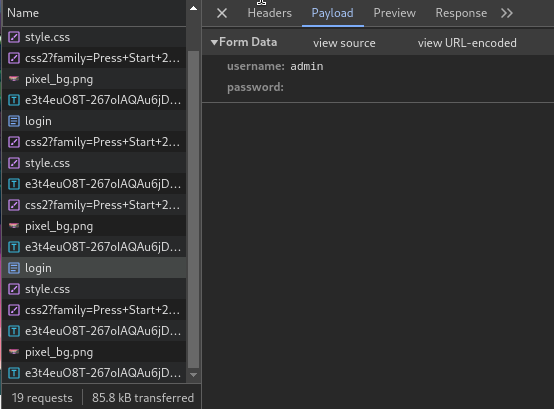
The submit button is still sending the password parameter to the sever and we can’t do it! not even a empty string!
So, one way is to delete the password input element. Now the submit button won’t send the password parameter.
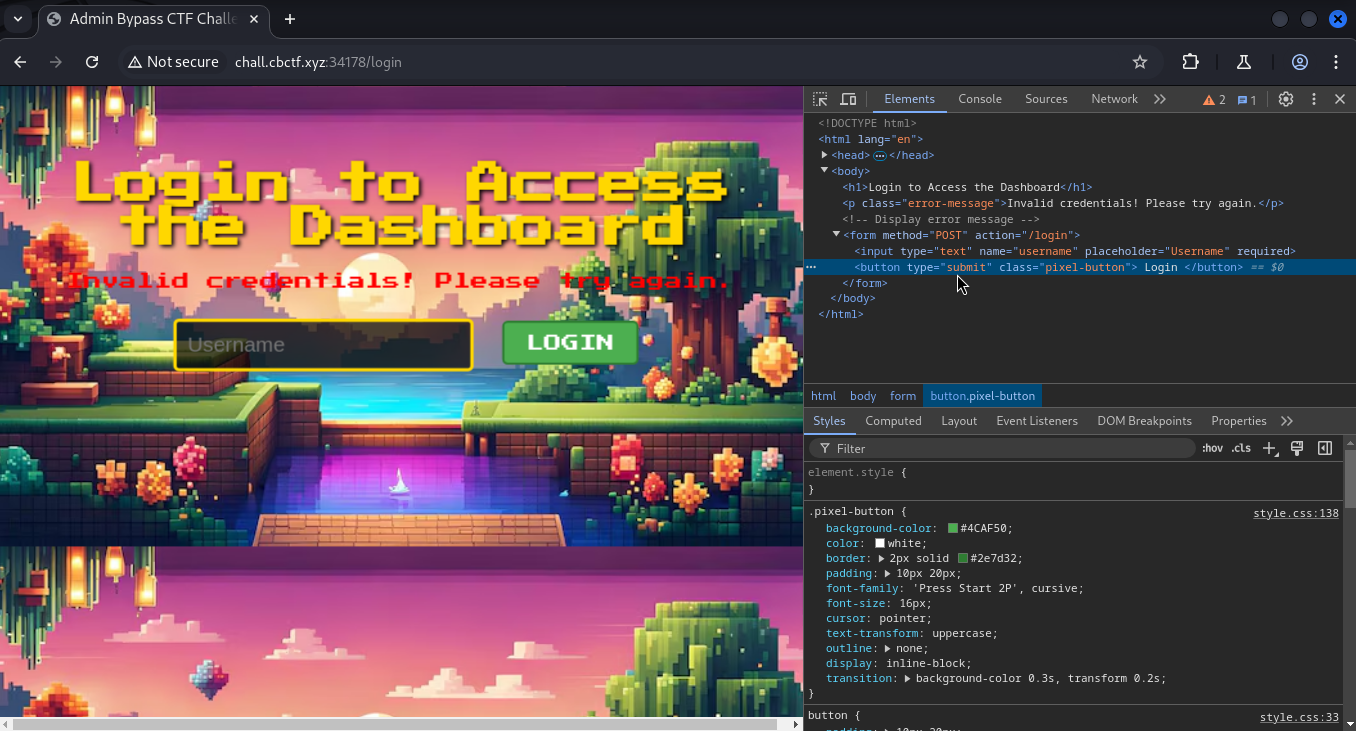
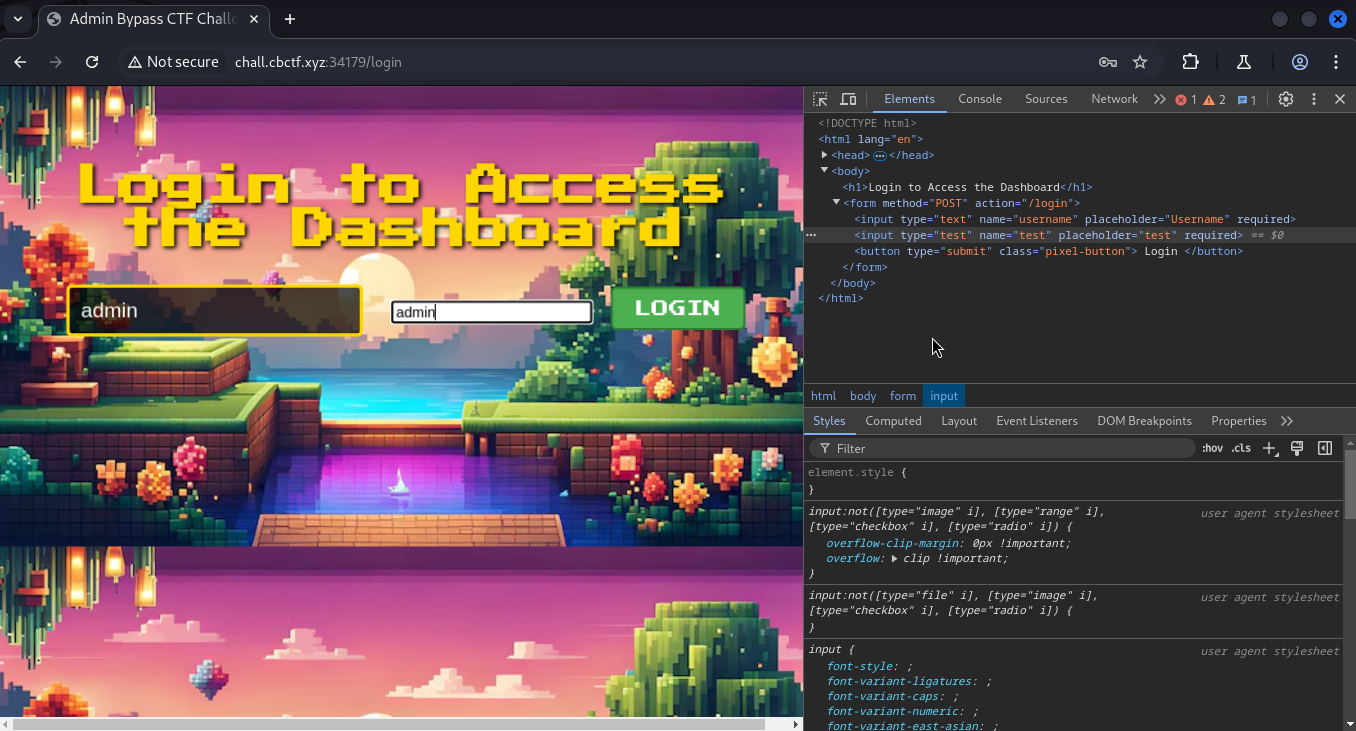
You might be wondering if the password parameter is the only culprit. I had the same thought while writing this! So, I renamed the element to something else, and it worked!
Conclusion
- Unfortunately, I failed to submit it during the contest :) Didn’t have burpsuite installed on my system. Remember I meantioned about my potato brain? Yes, a habit I have to launch burpsuite whenever I get a web challenge.
Credits
Hashnode - for the amazing platform
EWU - for delaying this write-up (they restricted challenge access after <36 hours)
Subscribe to my newsletter
Read articles from kurtnettle directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
