NetCat - 1 - NRF24CTF
 kurtnettle
kurtnettleTable of contents
Problem Statement
One Of My Student Cheating On Pentest Exam, He Didn't Know But I Can See!! Can You See? Flag Format For All Questions: EWU{some_text}
0xRobiul
Identify Lab & Attackbox!
Example: EWU{ServerIP_AttackerIP}
blogger.pcapng
Prerequisites
IP addresses (basics)
Wireshark (basic use of filters and statistics)
Solution
Reading the word "cheating," the first thing that came to my mind was Google search. So I filtered out the DNS requests
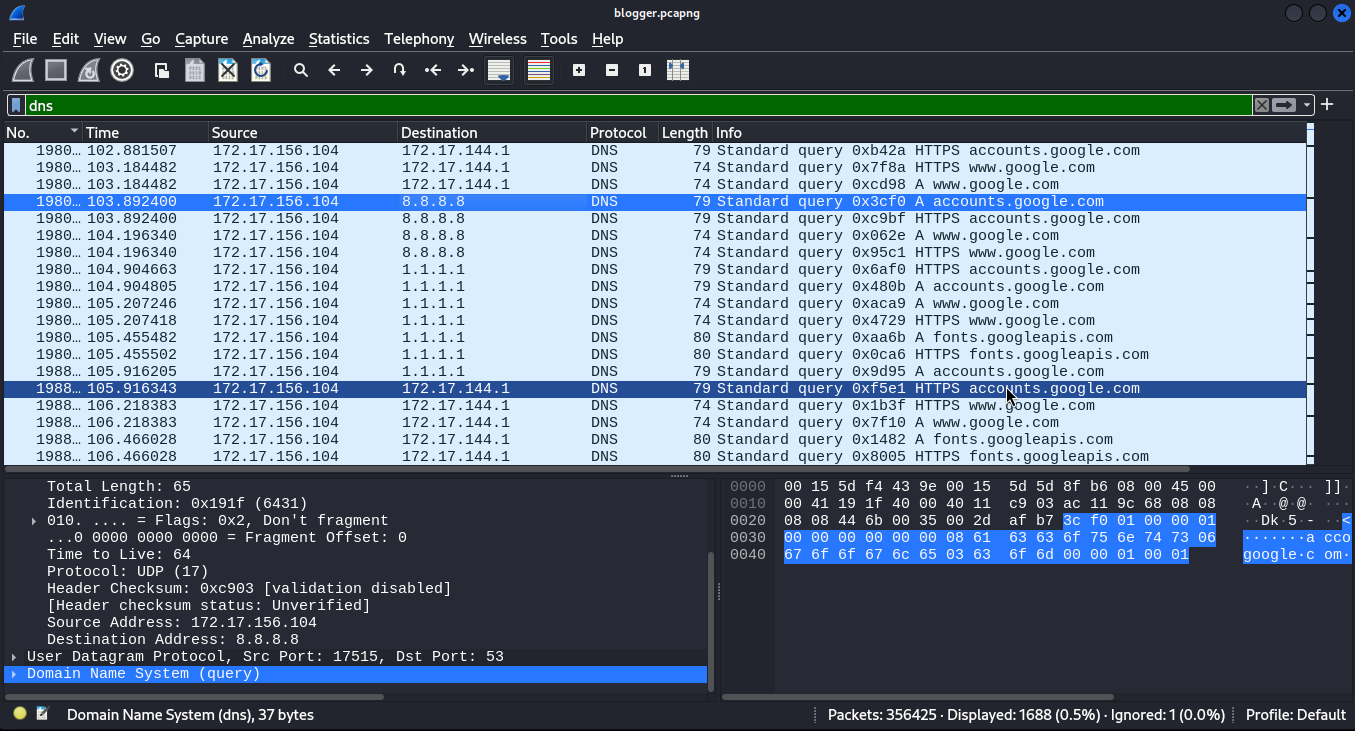
Looking further, I noticed the attacker was using DoH and making several queries. Next, I thought about listing all the IPv4 addresses to see which one has a large number of packets.
To list the endpoints click Statistics > Endpoints
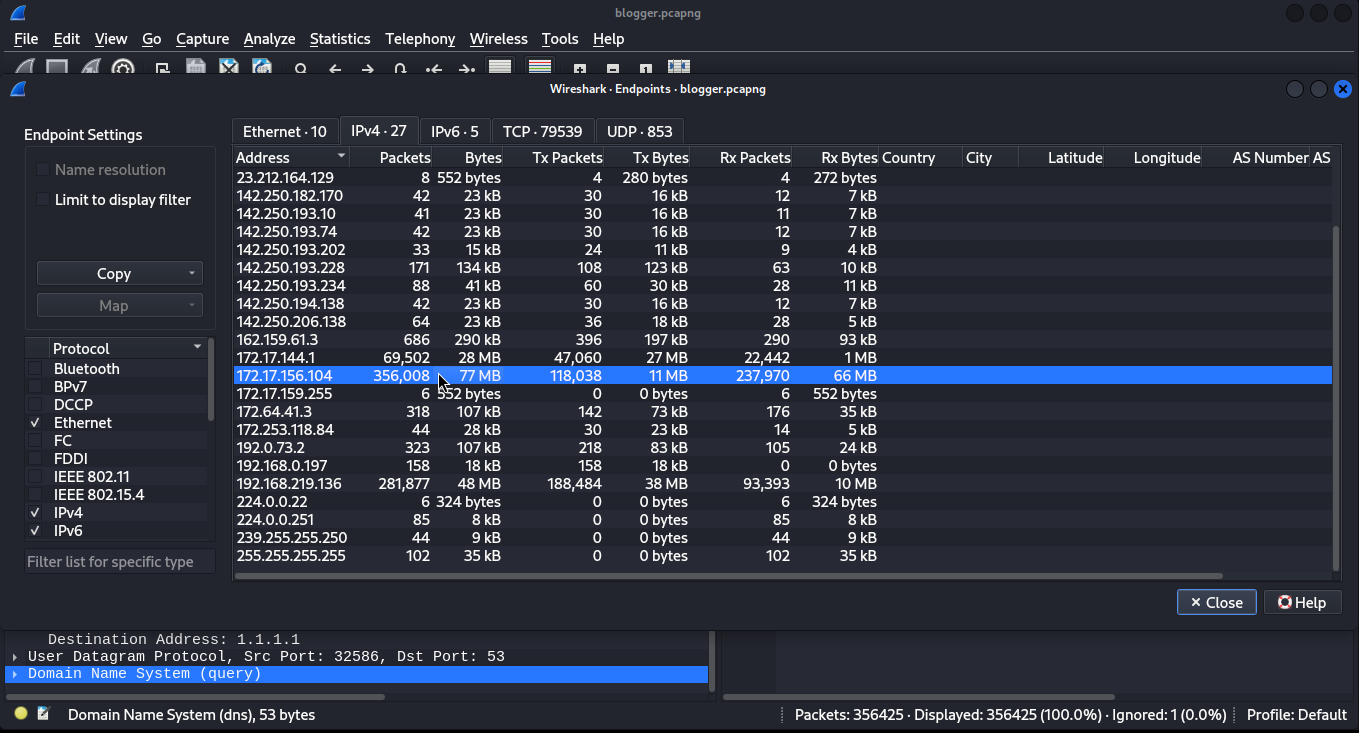
We found two IPv4 addresses with a large number of packets. Since we already know the attacker's address, we can surely say that 192.x.x.x is the server's address.
Conclusion
- Wireshark is an excellent packet analyzer. We should grasp the basics of it. Even with basic knowledge, we can be quite powerful.
Credits
Hashnode - for the amazing platform
EWU - for delaying this write-up (they restricted challenge access within <36 hours)
Subscribe to my newsletter
Read articles from kurtnettle directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
