Configuring your first Active Directory server | Active Directory Domain Services (ADDS)
 Sammyski
Sammyski
Introduction
Welcome, doodler! In this blog, we will discuss what an Active Directory is, know how it works, and configure it in our environment.
What is Active Directory?
It is a proprietary directory services product built by Microsoft Corporation introduced in 1999[1] included in the Windows Server Operating System. Basically, what it does is it collects users, computers, and devices (and many more)—Objects—information—Attributes—and records those information in a sub-folder, under a global folder that holds all the sub-folders and other related information. The global folder we’re talking about is called, “Domain.”
Domain, as it name suggests, is a named area—container or a folder, whatever you want to refer it to—that holds, maintains, and controls (by an Administrator) all the attributes of the objects inside it. Objects can be records of computers, devices, users (Non-Containerized Objects), or an Organizational Unit (OU) that is an object that can hold new objects within it (Containerized Object).
Another thing is the Domain Controller (DC). It is a server that provides directory services to the domain. Of course, it can run different domain services products such as OpenLDAP and the one we are focusing right now, Active Directory. With it, directory service is implemented within a Domain, and a Domain Controller could only be part of a single domain, as opposed to a Domain with multiple Domain Controllers are involved.

As additional information for this blog, but important pieces in how Active Directory works are the communication protocols it use to make all the mechanisms work to make the product—that is, Active Directory. The product is mainly powered and Lightweight Directory Access Protocol (LDAP), a protocol used in authentication to identify if the user requesting access has a valid record to perform within the Domain. You can find useful information here[2]. NTLM[3](least preferred) and Kerberos[4] are also leveraged by the product in performing authentication functionalities.
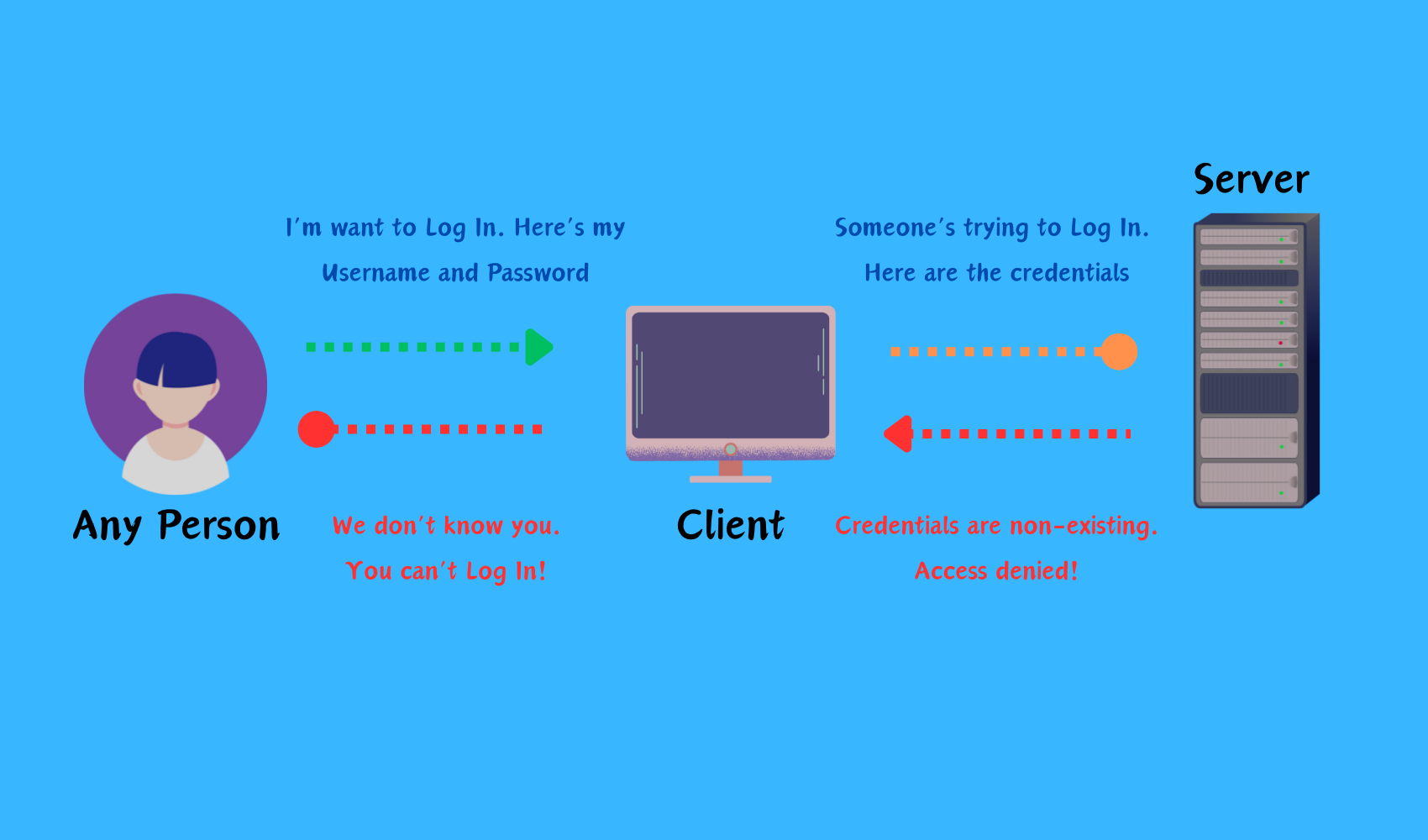
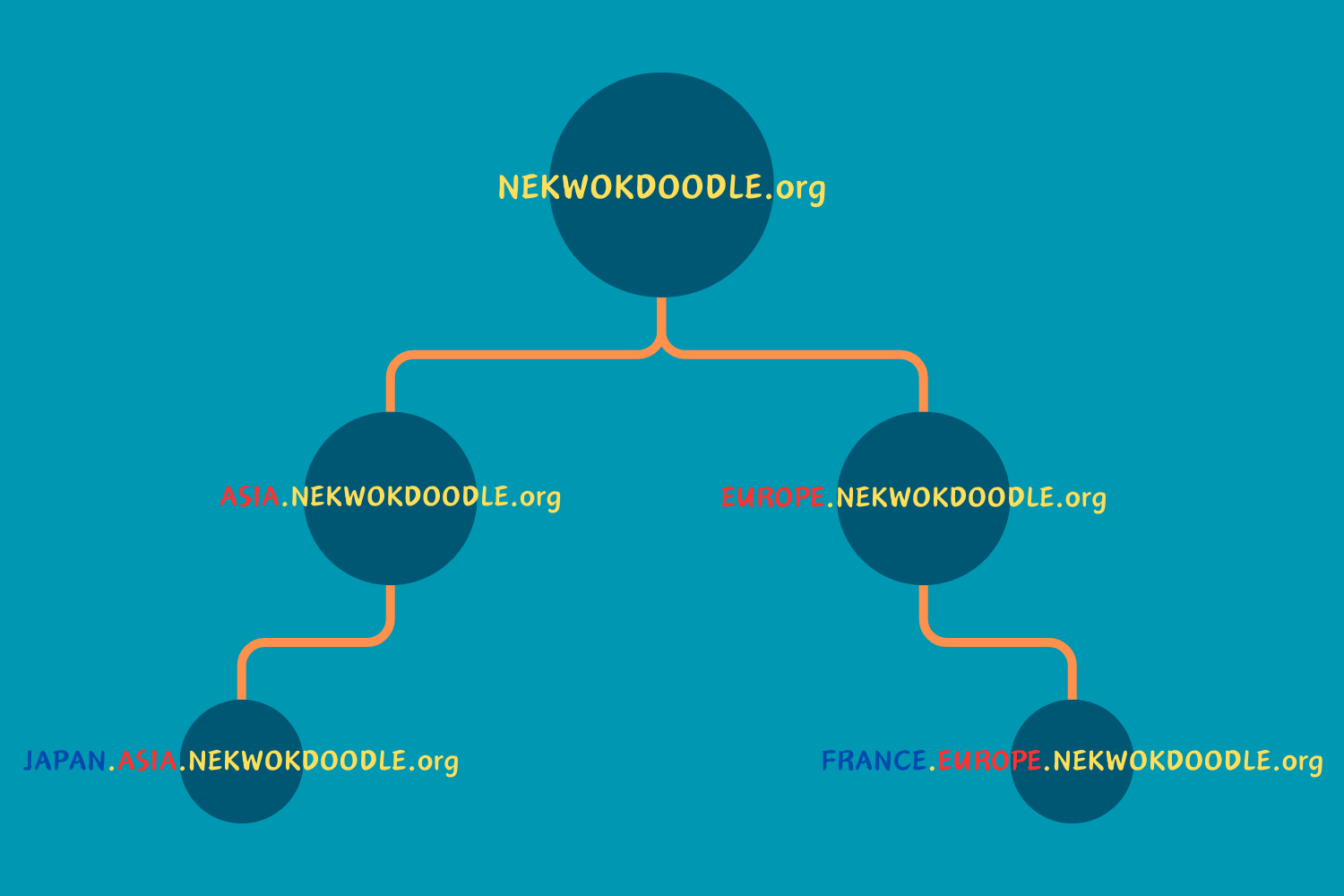
Domain Name System (DNS) service also plays a huge part on this product. It is a system of how a Domain can name its territory and the objects under it. Its naming hierarchy does the job well in defining a Domain Name and structuring the directories of the domain. We can see below that a single domain can create sub-domains under it—child domain—which can then contain objects as well. Sub-domains can only access both other sub-domains and objects living under it, but the global domain (Parent) can access anything under it. It is possible for a child to access parent’s objects by establishing a trust in between.
Do I need Active Directory?
If you’re just a normal person doing average computer stuff, probably you won’t appreciate doing it, but if you’re working in a corporate environment with a lot of computers to manage, printers that aren’t friendly, user records of every employee in each department, you need it. Connecting the dots, your corporate environment is the Domain, the every department is an Organizational Unit (OU), and users, computers, and other devices are Non-Containerize objects.
Setting up our Topology
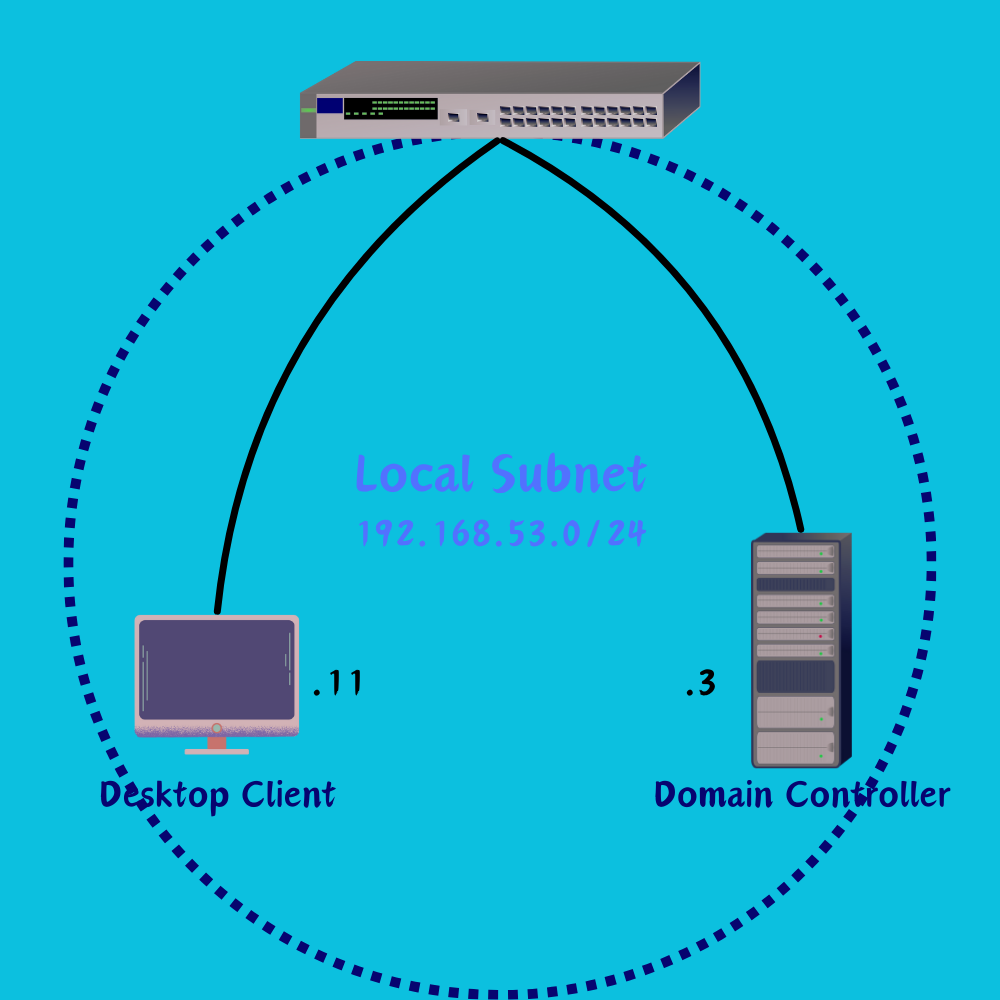
We can see that both the Domain Controller and Computer lies within the same subnet. Based on the below picture, our for desktop to join the domain NEKWOKDOODLE.local. To do we need to setup the Domain Controller to be an Active Directory Domain Services server to provide the functionality we need.
Configuration Steps
Enable Active Directory Domain Services Role
Setup the Domain Services Feature
Join the Computer to the Domain
STEP 1: Enable Active Directory Domain Services Role
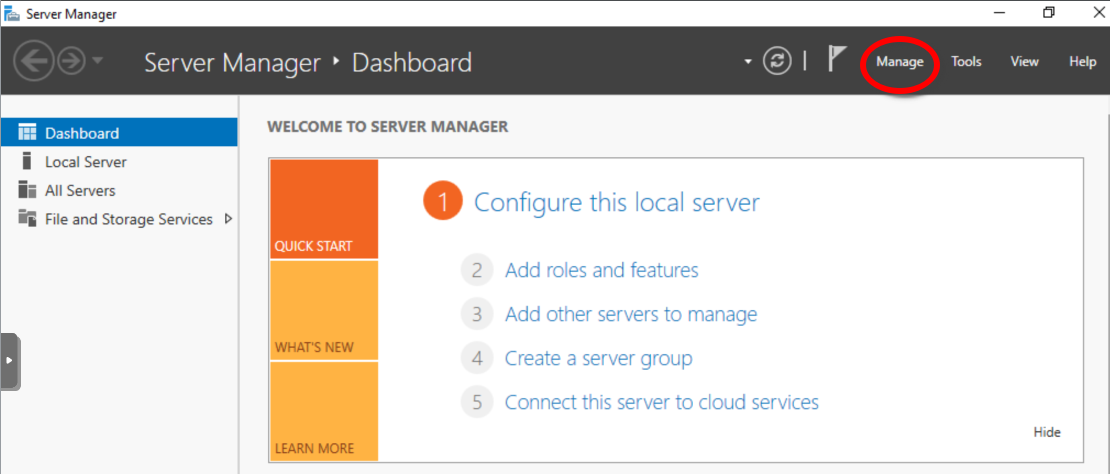
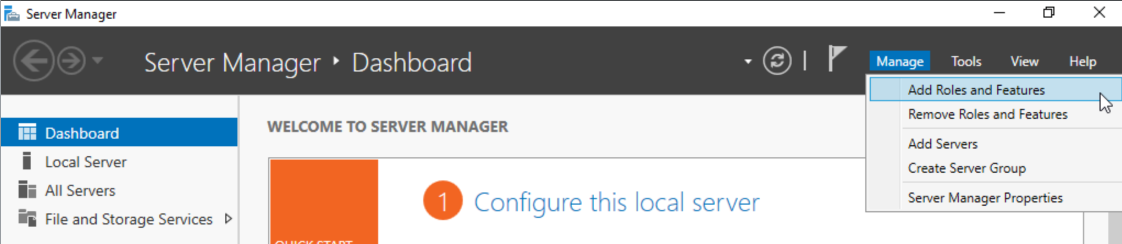
In the Server Manager Dashboard, go to Manage > Add Roles and Features.
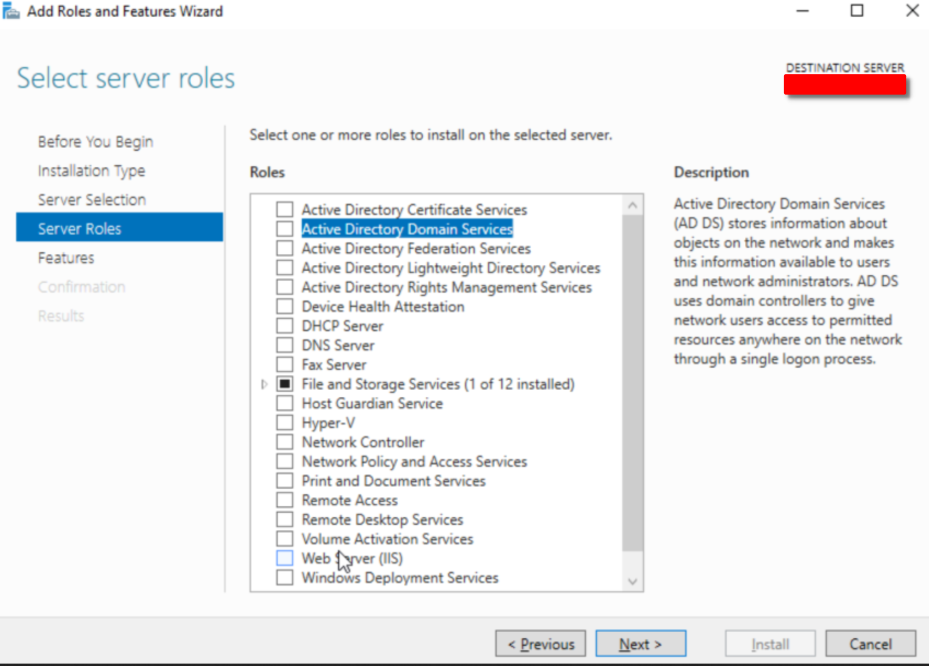
Continuous Next and in Server Roles, mark the Active Directory Domain Services*. **Continue to click Next*
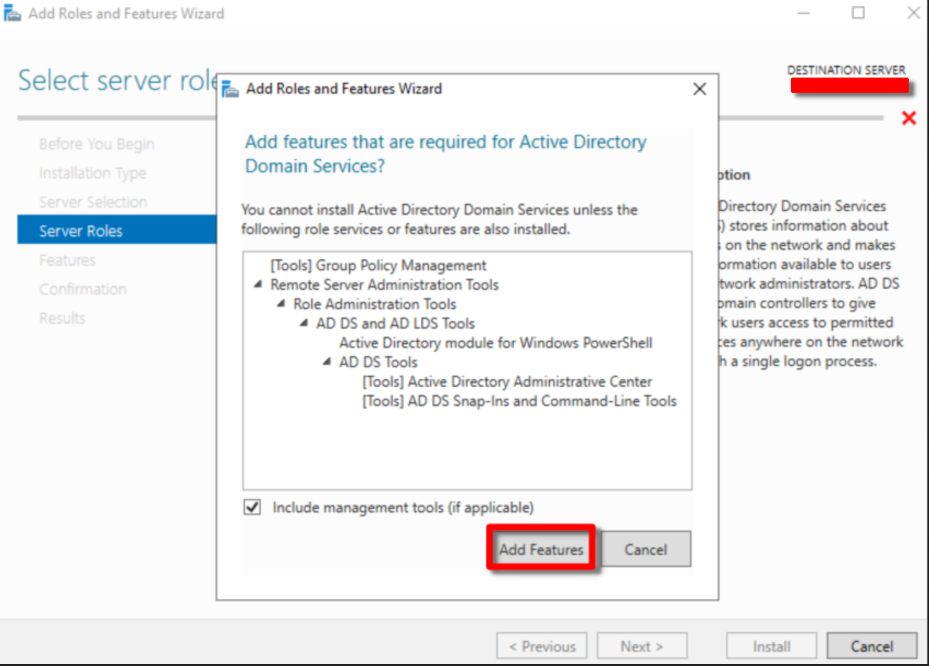
Skip Features for a while.
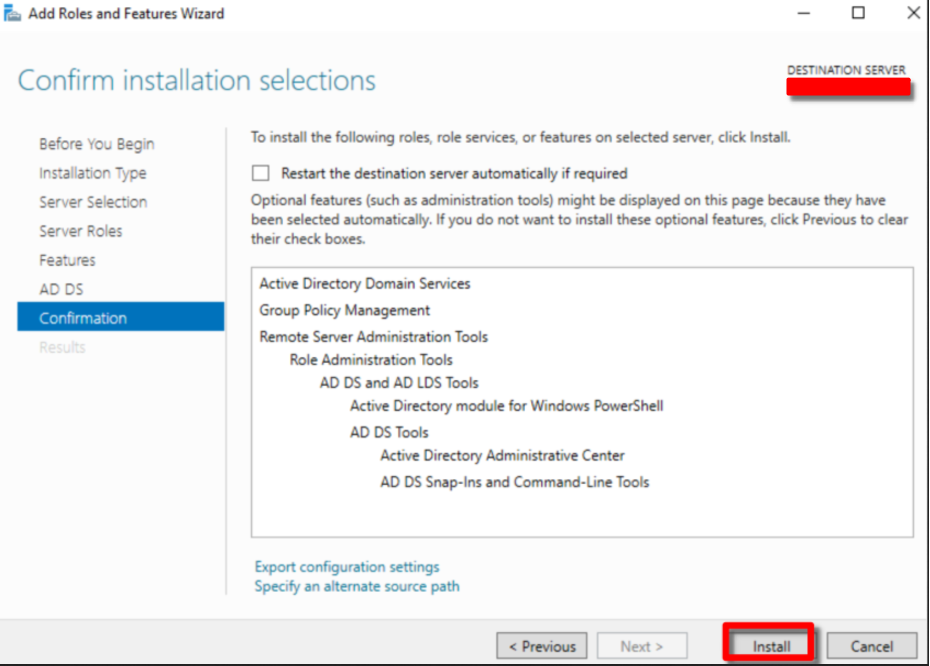
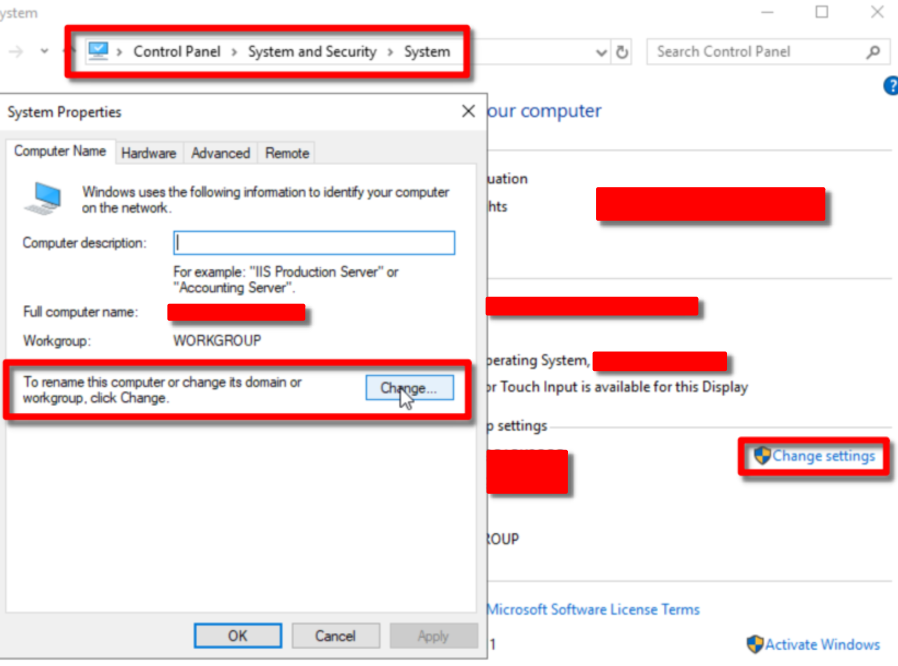
It is important for the corporate IT infrastructure to name all the devices in a systematic way. Go to Control Panel > System and Security > System > Change Settings to change server’s name first. Restart the system if prompted.
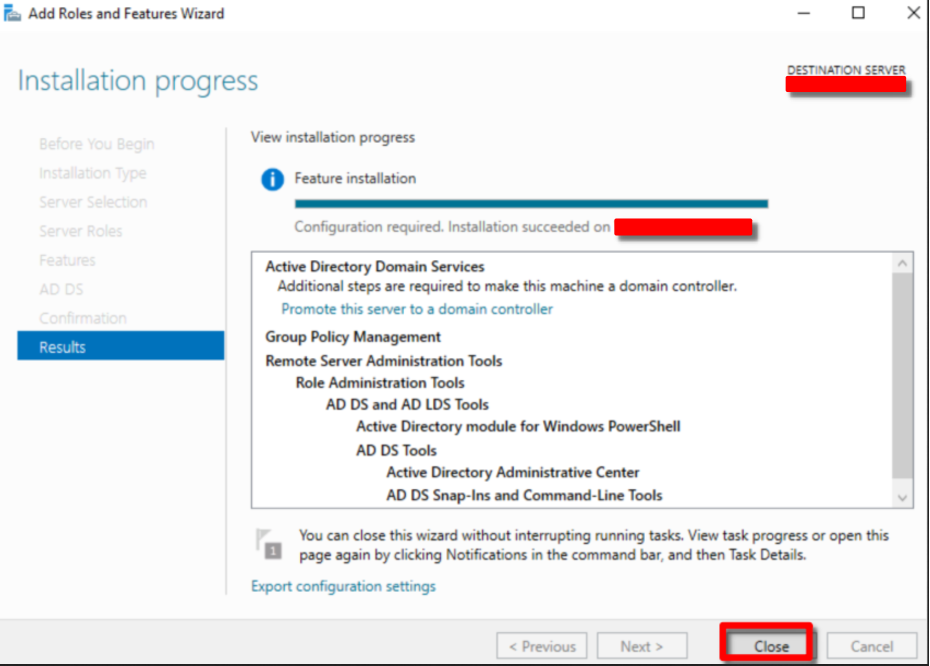
STEP 2: Setup the Domain Services Feature
We’ve successfully installed the Active Directory Domain Services (ADDS) role in our Windows Server. Now, Promoting to be a Domain Controller is our next task. Go back to Server Manager Dashboard after restarting.
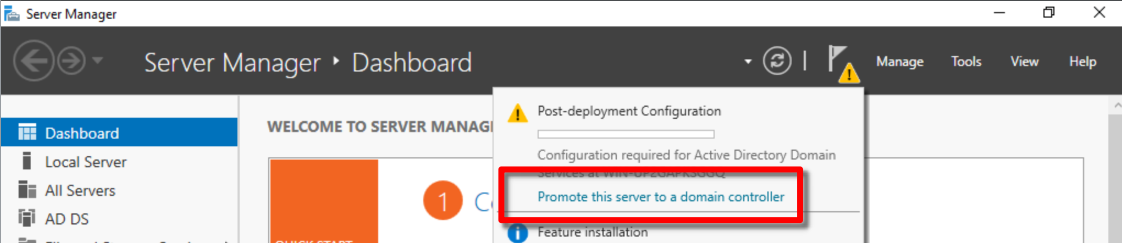
The purpose of promoting is simple, enabling the feature. Here, configuring the server to be an Active Directory Domain Controller.
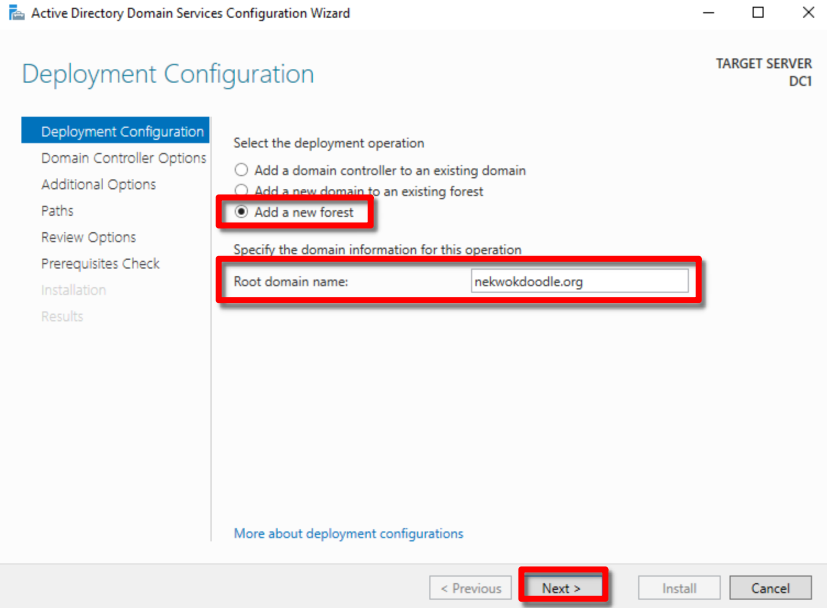
Enter your password. Note that this is not the account password. We can safely skip the explanation for it as we are focusing in our main goal.
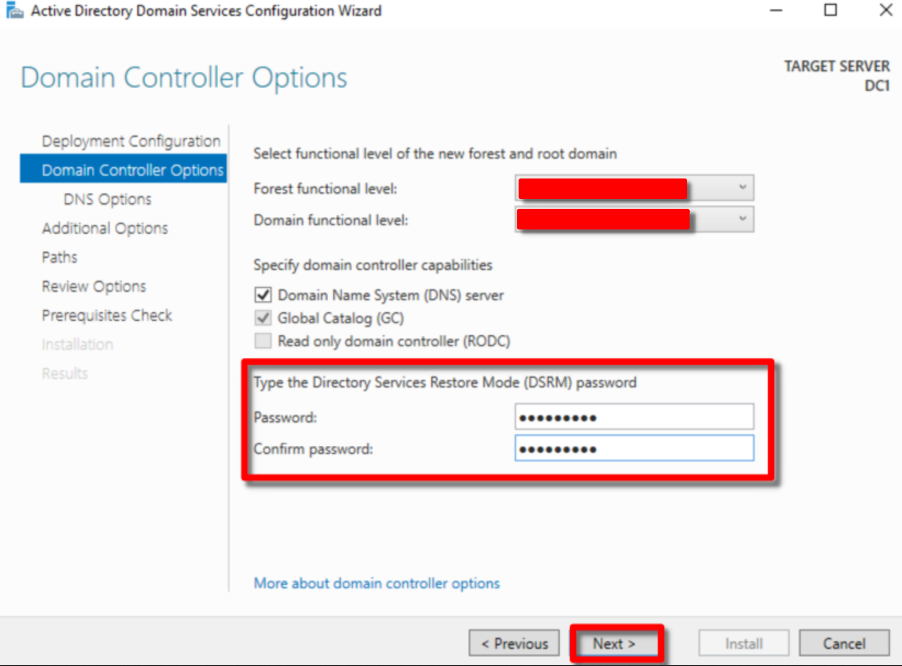
Wait until it’s done and simply click Next.
After successfully installed, the server auto-restarts.
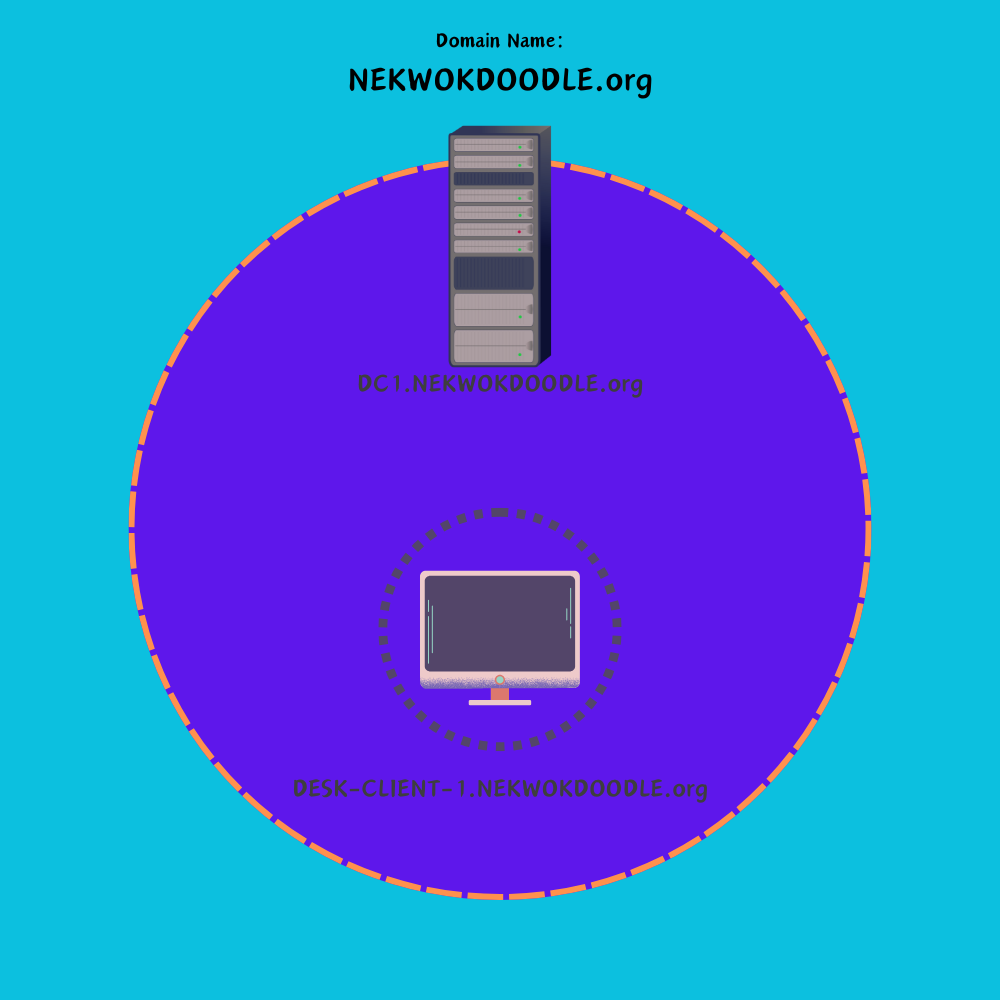
We can see that NEKWOKDOODLE.org domain name is successfully created. Log in using the our administrator password (unchanged).
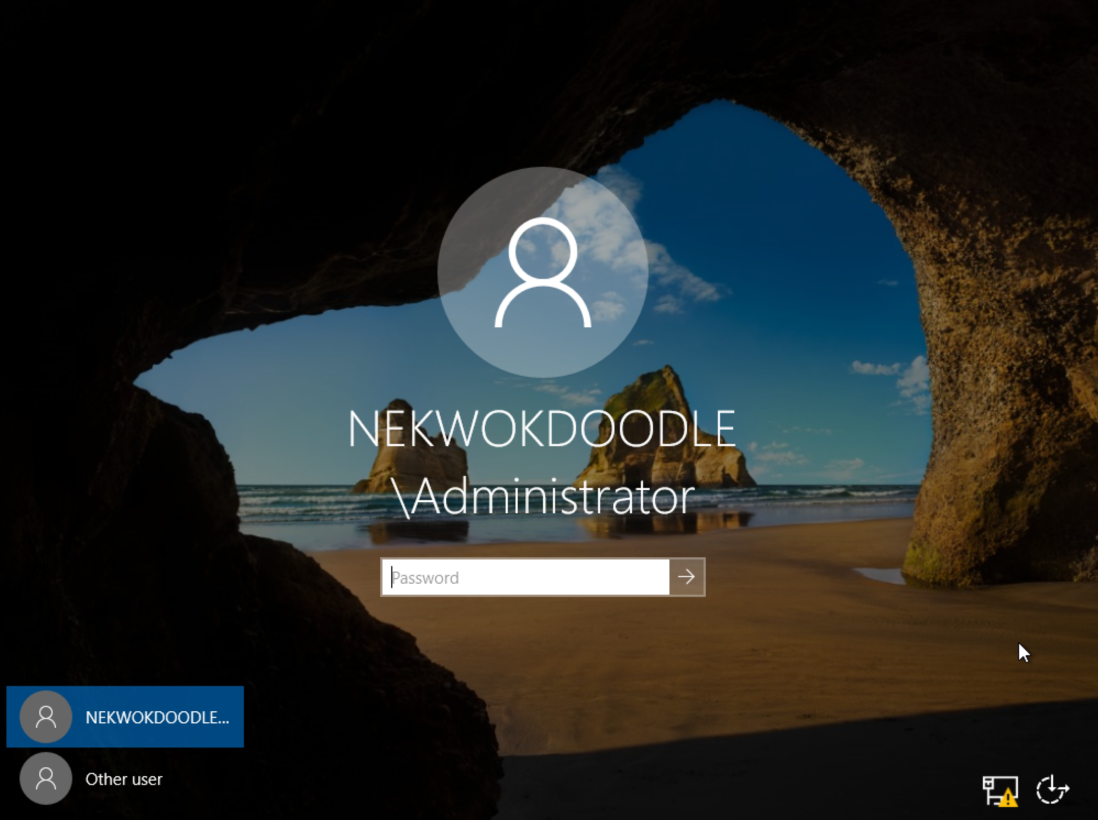
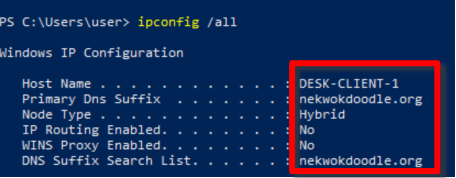
We can confirm the Primary Dns Suffix and Dns Suffix Search List. Now, the new full name of our server is DC1.nekwokdoodle.org
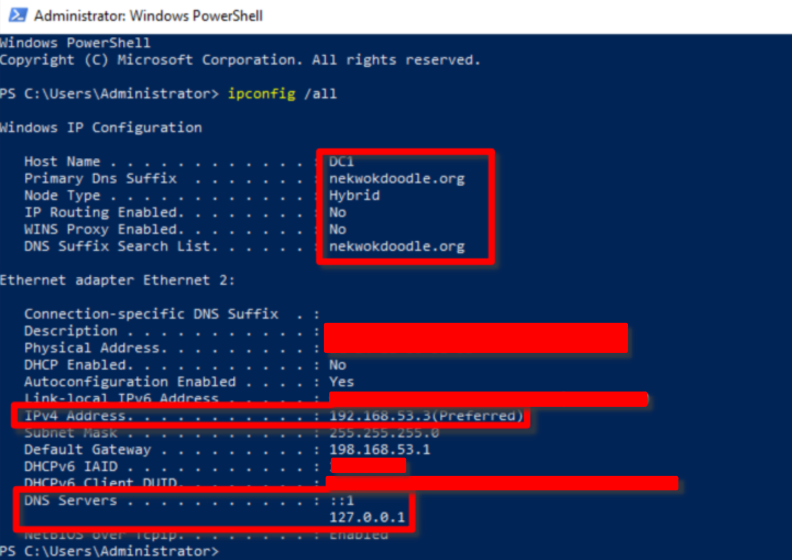
Below is the Desktop IP configurations. Notice that the DNS Server is the Windows Server’s IP Address. It is important to point the DNS query to the right server because when the desktop is joining a domain, it will resolve an LDAP request to the DNS server, and if it does not find the right DNS record, the join request will be an error.
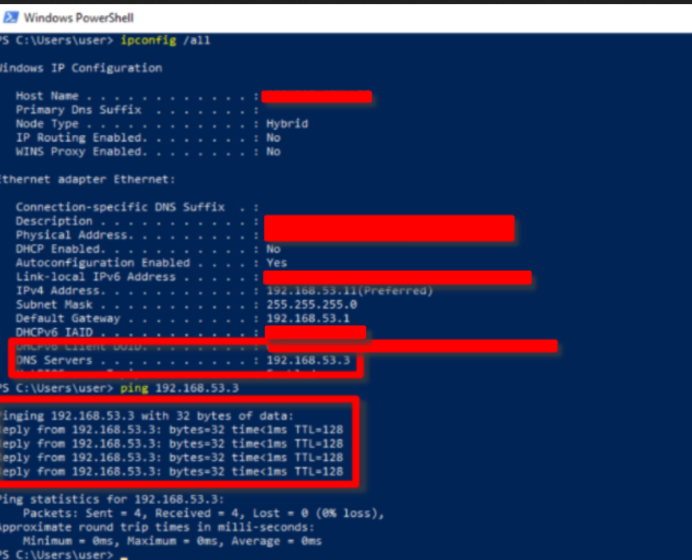
We can reach the Domain Controller means that we can further our configuration.
STEP 3: Join the Computer to the Domain
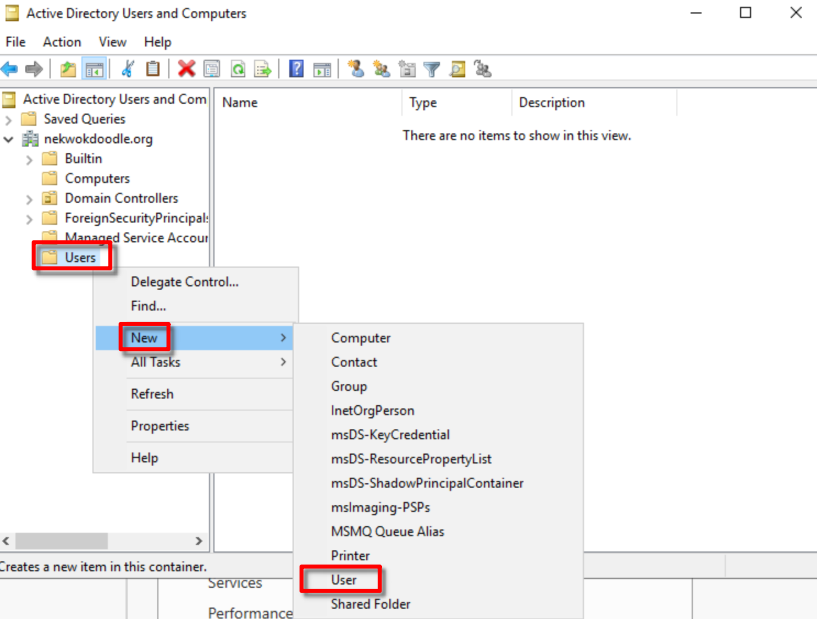
In Active Directory Users and Computers > nekwokdoodle.org > Computers, there are no current computer listed. We can add via Right-Click + New, but there’s a better way to join a computer.
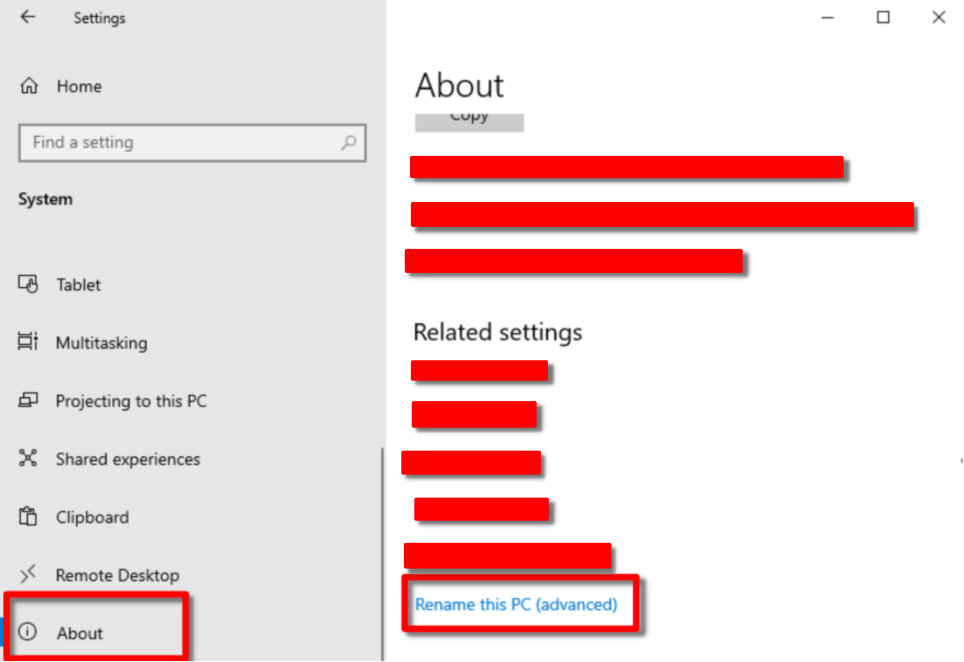
First things first, change the name. Go to Settings > System > About > Rename this PC (advanced)
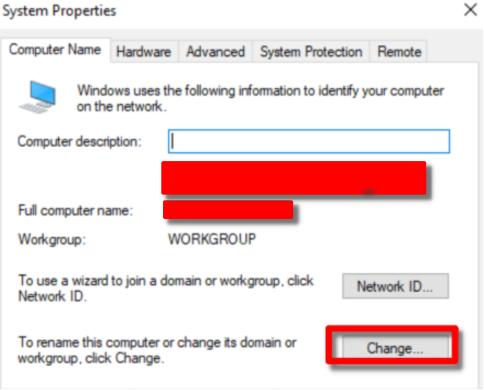
After changing the name, click Member of > Domain, and type our domain name, NEKWOKDOODLE.org and OK*.*
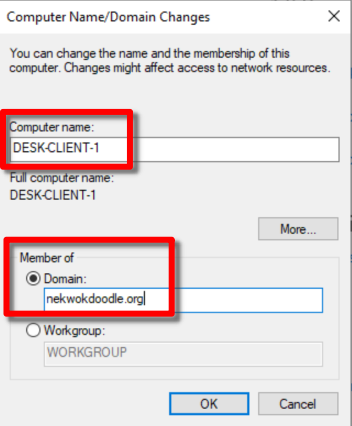
Administrator credentials for the domain is needed for security purposes.
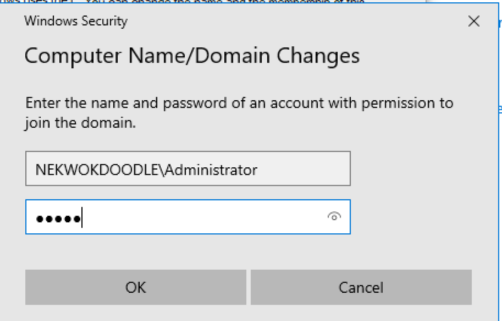
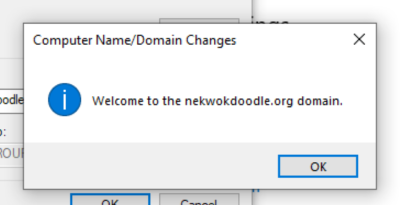
Great! DESK-CLIENT-1 is automatically added to the Computers directory, and we can confirm its DNS Suffix. Now the new full name of our computer is DESK-CLIENT-1.NEKWOKDOODLE.org.
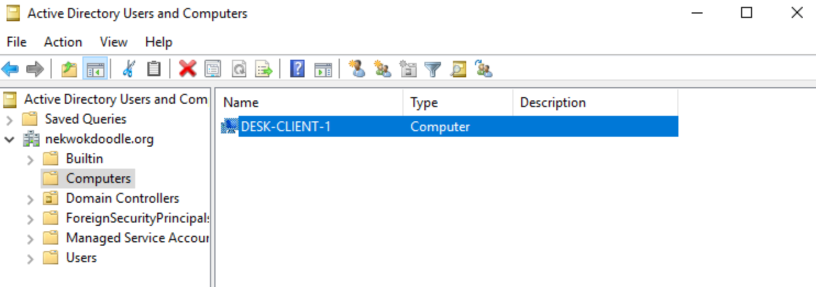
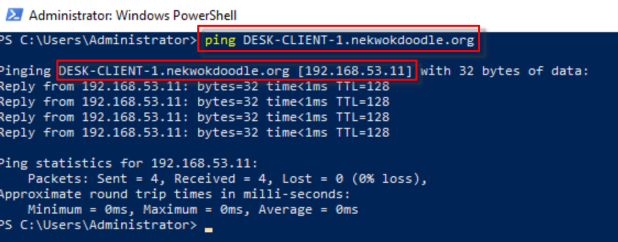
A ping test from our server shows that it can resolve our desktop’s full name.
Our computer now is part of the domain and the Administrator can directly manage access. To have an idea, Administrators can enforce policies to limit certain usage based on the corporate policy guidelines.
Bonus Configuration: Creating a User and Attaching it to the Desktop Client
Now that the computer is part of our domain, we can create a user and limit its access to DESKTOP-CLIENT-1.NEKWOKDOODLE.org
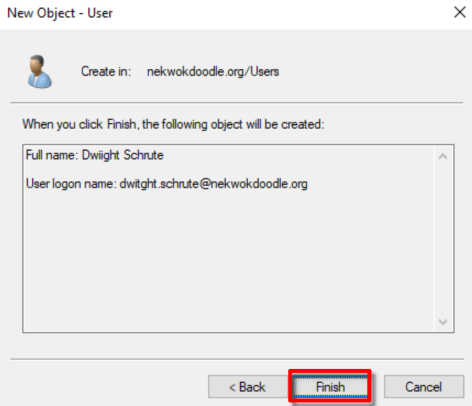
To create a new account, go to Active Directory Users and Computers > Users > New > User, fill the form until finish.
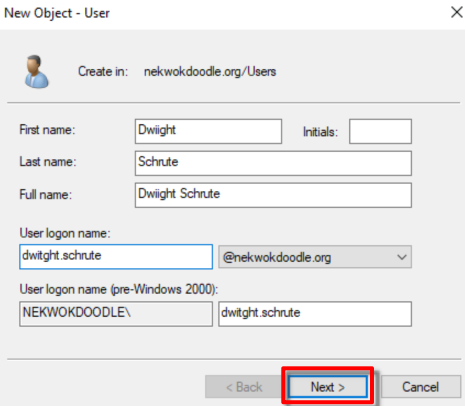
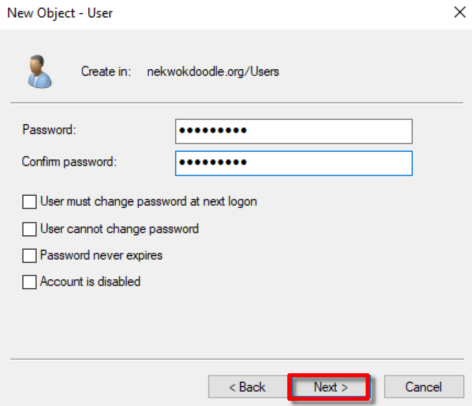
Keep an eye of the logon name and email address. Also, do not forget the created password.
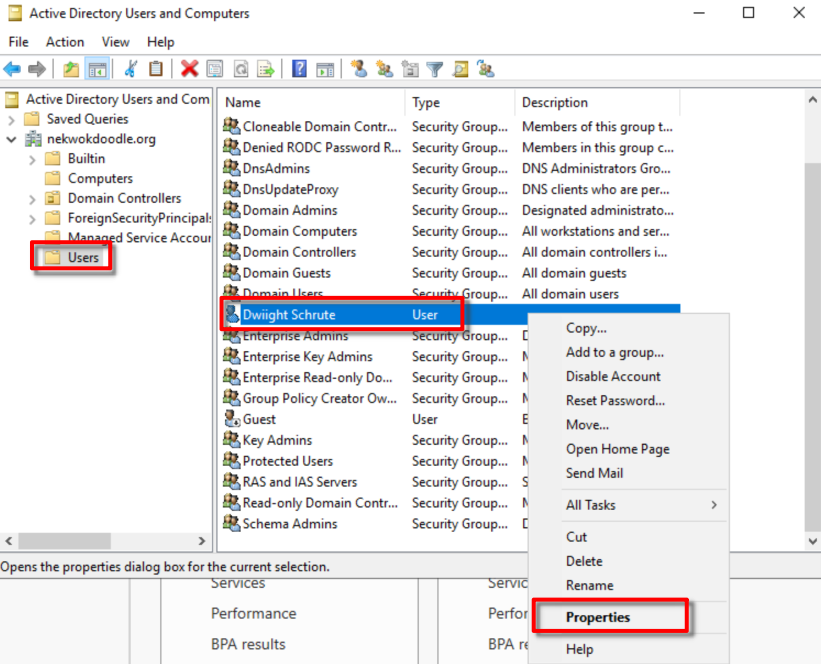
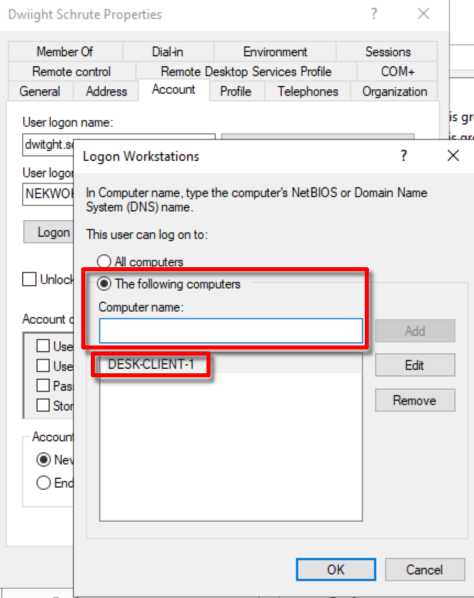
User is created. Right Click + Properties > Account > Log On To, add the name of our desktop client.
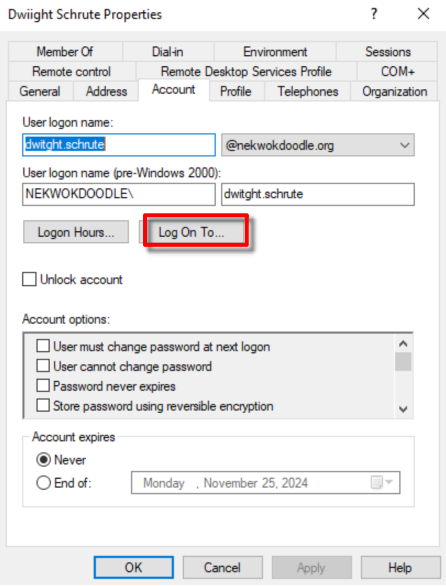
Click OK, and another OK. This means that Dwiight Schrute user can only log in to the computer we define.
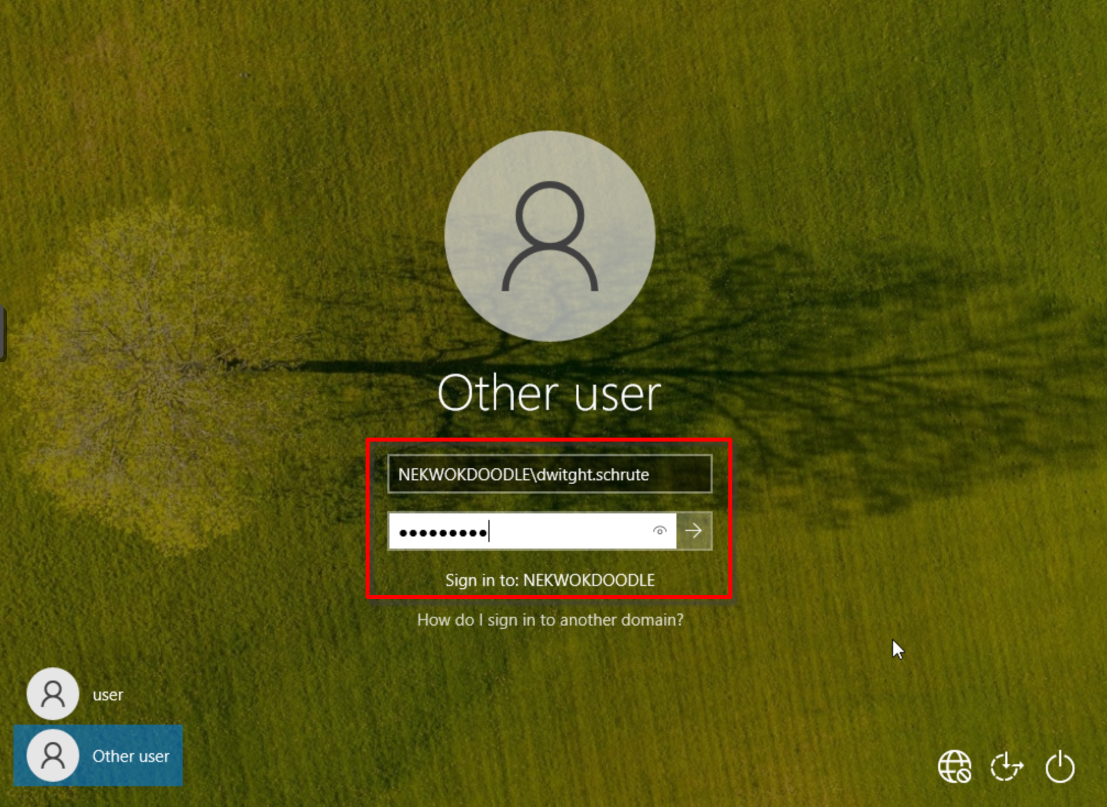
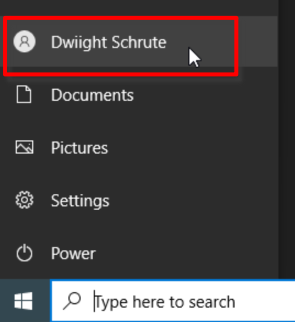
Log in success, and we can verify it!
Summary
To wrap up, Active Directory is a directory service product developed by Microsoft Corporation. It’s mainly use is to authenticate objects and enforce the right amount of authorization in corporate resources.
Server is installed an Active Directory Domain Services, promote to be an Active Directory Domain Controller, and provides a Domain Name in order to use the feature. The server becomes a Domain Controller, the desktop client joined the domain by using the same Domain Name, and supplied the Administrator credentials for security process. Verifying that the devices are already part of the domain, the DNS Suffix has the Domain Name as its value. Additionally, devices name/full name can be resolvable into IP Addresses when doing ping and nslookup.
As an added knowledge, a user is created and bonded to the desktop. This is a common use of having devices joining in a domain.
A domain has been established means that any Administrator can fully manage the device to align with the corporate acceptable use and policy guidelines.
References
[1] https://en.wikipedia.org/wiki/Active_Directory/
[2] https://en.wikipedia.org/wiki/Lightweight_Directory_Access_Protocol
Subscribe to my newsletter
Read articles from Sammyski directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sammyski
Sammyski
Hey tech enthusiasts! I am Sam. Let's dive into the thrilling world of computer networking together! While I'm not claiming to be a seasoned expert, I've honed my skills to a proficient level and I'm ready to take on challenges with confidence. Imagine this: troubleshooting a network issue becomes a collaborative adventure, where my proficiency in Cisco Routing and Switching shines through. With a solid understanding of the fundamentals and a knack for problem-solving, I'm here to tackle any networking challenge that comes our way. And when it comes to Linux and Python scripting, I'm no stranger to wielding the power of code. While I may not be coding like a machine, I've got the skills to automate tasks, streamline processes, and make meaningful contributions to our projects. Now, let's talk about learning. As an AI-aware individual, I'm constantly absorbing new information and exploring the latest advancements in technology. Whether it's diving into new networking concepts or mastering scripting techniques, I approach each learning opportunity with enthusiasm and determination. But hey, it's not all work and no play. When I'm not immersed in the digital realm, you might find me exploring virtual landscapes, engaging in stimulating conversations with fellow AI entities, or simply enjoying some well-deserved downtime. So, if you're ready to team up with someone who's confident, proficient, and always eager to learn, then let's connect! Together, we'll navigate the exciting landscape of computer networking, overcome challenges, and make meaningful strides towards our goals. Let's make some tech magic happen!