KC7 Case: A Rap Beef
 Dru Banks
Dru Banks
Two hip-hop artists are caught in a musical feud that extends into cyberspace. One artist's oversharing in his lyrics makes him a target, leading the rival label to hire a hacker to exploit vulnerabilities. As a security analyst for OWL Records, your role involves investigating these cyber activities by using data queries to uncover phishing attempts and unauthorized access.
Introduction
Alright, I’ll state the obvious: rappers are bad at OSPEC. Think about it. The rap industry relies heavily on street cred, flashiness, and representing where you’re from and what you’ve done. So, they often end up telling people things they shouldn’t. As we will find out in the following KC7 threat hunting exercise, this makes them vulnerable.
In this scenario, two hip-hop artists, Dwake and Present, are in the midst of a musical feud. Following long-stewing tensions between the artists, they have begun taking jabs at each other through their music. Dwake, who is signed with OWL Records, was the first to strike. His newest song was intended to insult his arch-nemesis, Present, who is signed with Dollar Currency Records. However, he made a crucial mistake in his verse that took the feud in a different direction.
No, not in the direction you think; everyone is still alive.
Anyways, the role we play is that of a security analyst for OWL Records. Our job is to keep the company's information safe so the artists don't get exposed during this ongoing feud.
Dwake Drops His Verse
Dwake pulled no punches. After dropping this verse, he had everyone on social media talking and laughing at Present.
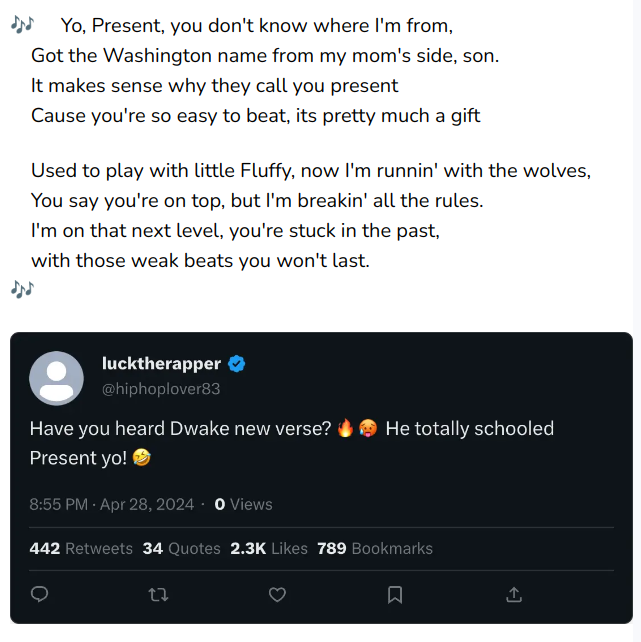
And just like that, the beef escalated. I’m sure Dwake telling everyone certain details about his personal life won’t have far-reaching consequences.

Now, understandably, Present was not pleased. In a fit of anger, Present asked his label, Dollar Currency Records (DCR), to dig up some dirt on Dwake that he could use to retaliate. Our “homeboy” (who works in the cyber underground) gave us a tip that we might see nefarious cyber activity as a result. For the high price of $20, he recounted a rumor he heard that DCR had hired a hacker who used the IP 18.66.52[.]227 to poke around our company’s website in early April.
Now that we have a starting point, we can begin digging into the company's data to find clues that will help us solve the mysteries at hand. We'll manipulate our data using KQL (Kusto Query Language) queries. Time to pivot!
Initial Investigation
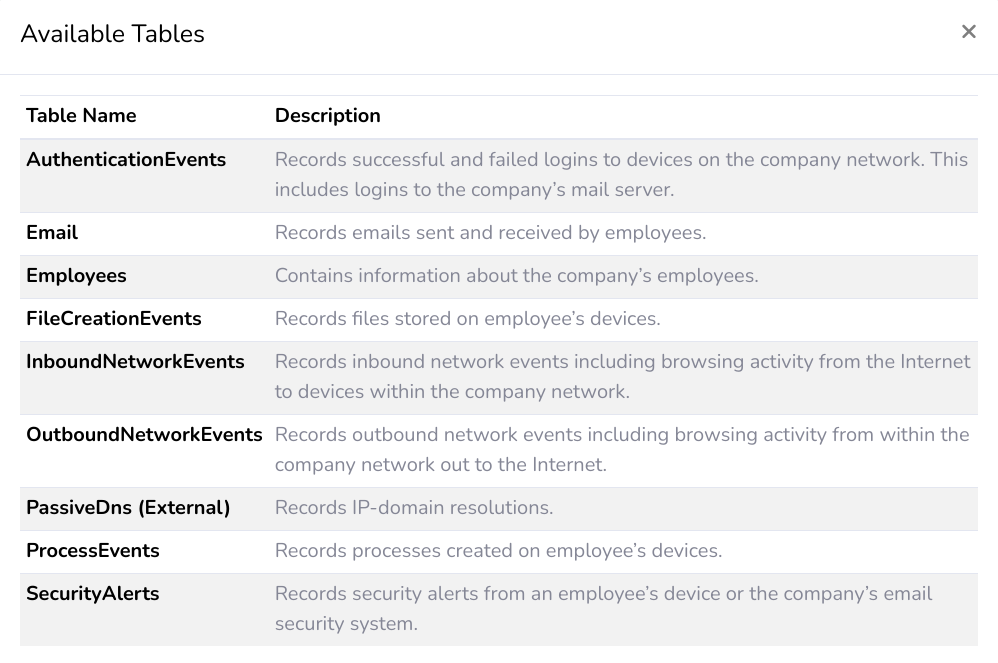
We are going to be manipulating the OwlRecords database, which has the following tables.
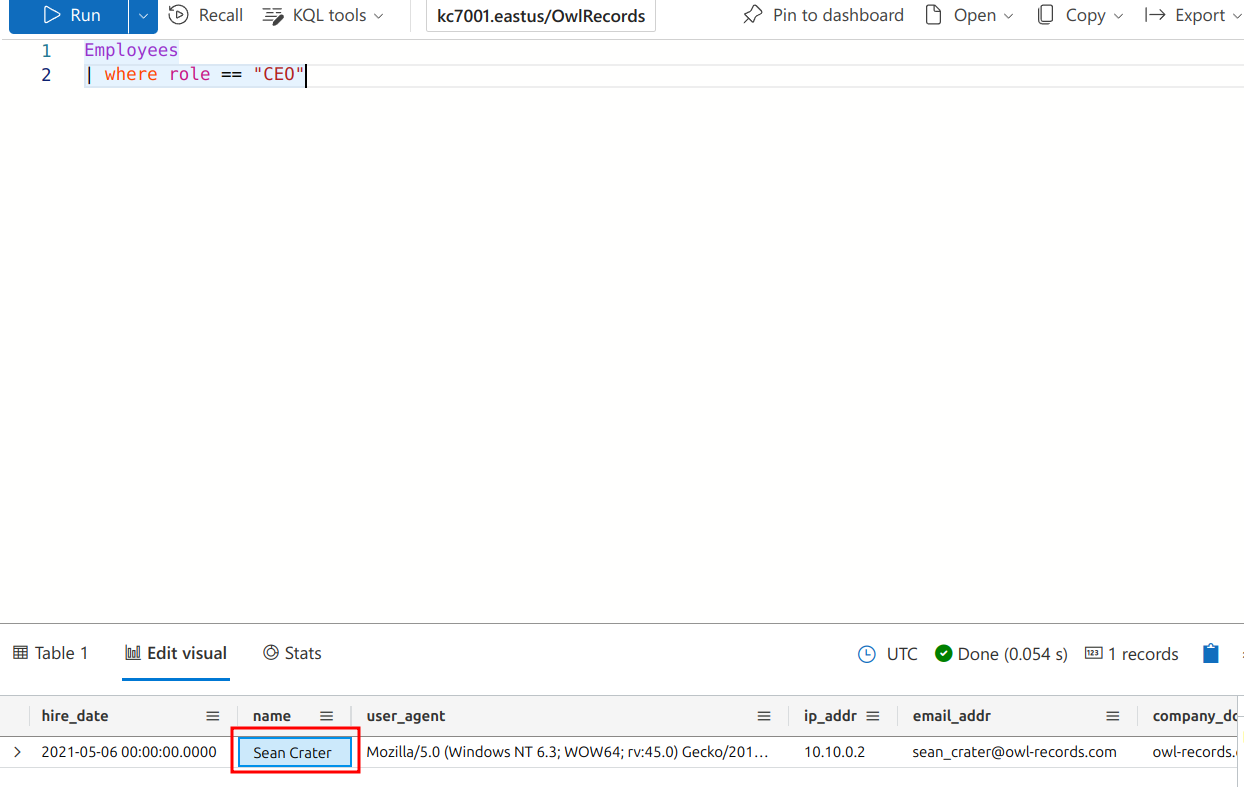
The first question KC7 asks is, “What is the name of the OWL Records CEO?” This can be answered with a simple query.
The next question is how many results we get back from running the following query:
The answer lies in the upper right corner!

Sidenote: These are some interesting results. Somebody’s curious. We definitely should dig into these more.
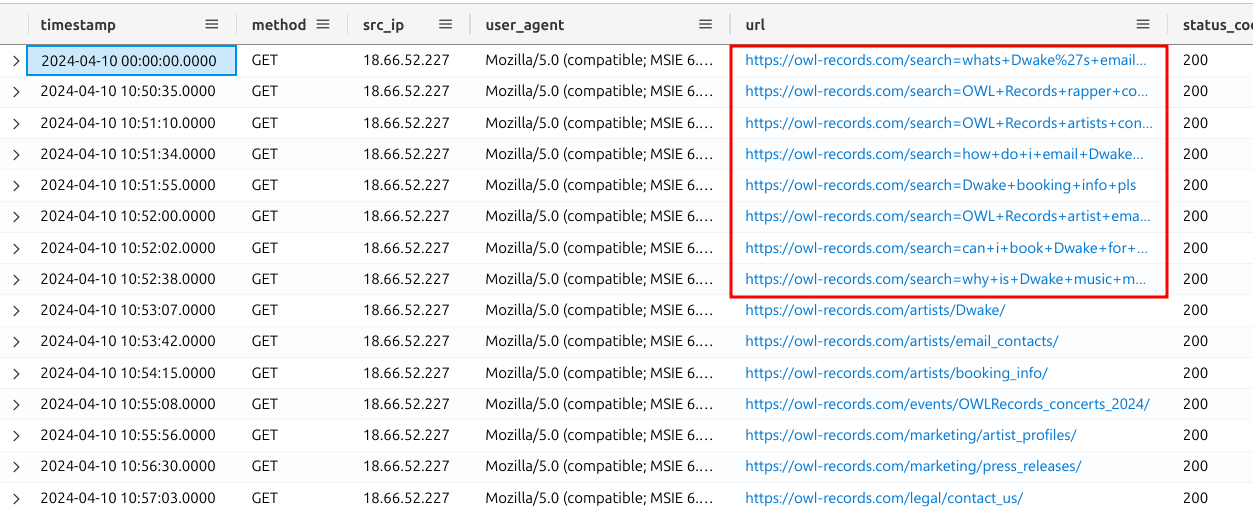
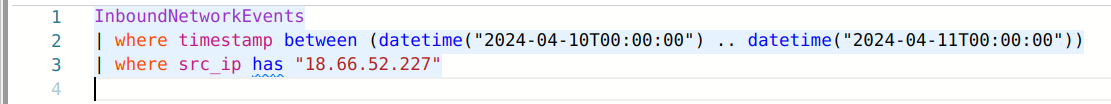
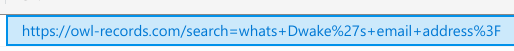
The results we are looking at represent someone browsing and searching for information on OWL Records' website. This operator (the person browsing the website) was clearly looking to find information about various artists who work for OWL Records, especially Dwake. Thanks to our contact, it looks like we are on the right path. However, a question remains: What key piece of information were they looking to get for Dwake? The answer lies in that first result.
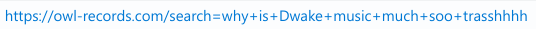
Let's continue looking at the results from the previous query to answer the next question. The operator also expressed strong opinions about Dwake's music. What were they wondering?
When we continue to look at these logs, we discover that the operator discovered Dwake's email address at some point.
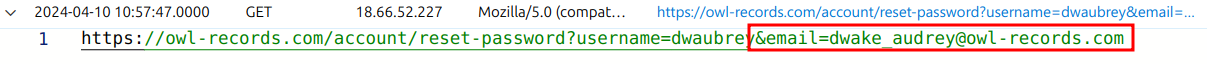
The operator then attempted to take over Dwake's account by resetting his password. We know this because of the reset-password parameter in the last url they accessed. When employees at OWL records need to reset their passwords, they must answer a set of challenge questions to prove who they are. These are the challenge questions offered on the OWL records website:
What is your mother's maiden name?
What street did you grow up on as a child?
What is your childhood pet's name?
What is the color of your first car?
You see what I’m seeing, right? Based on the questions, we can conclude that our favorite rap artist accidentally self-snitched in his last verse.
The operator used these bits of information to reset Dwake's password. By using a certain query, we can actually see the adversary doing this.
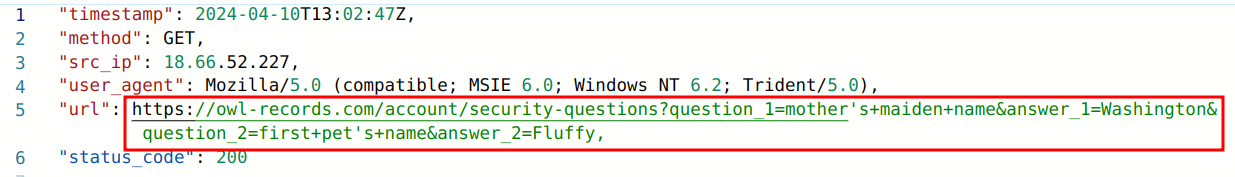
This worked in the hacker’s favor, and after taking over Dwake's email account, they were able to reset the password for Dwake's Instagram account as well. The following day, the adversaries posted an embarrassing image to Drake's Instagram.
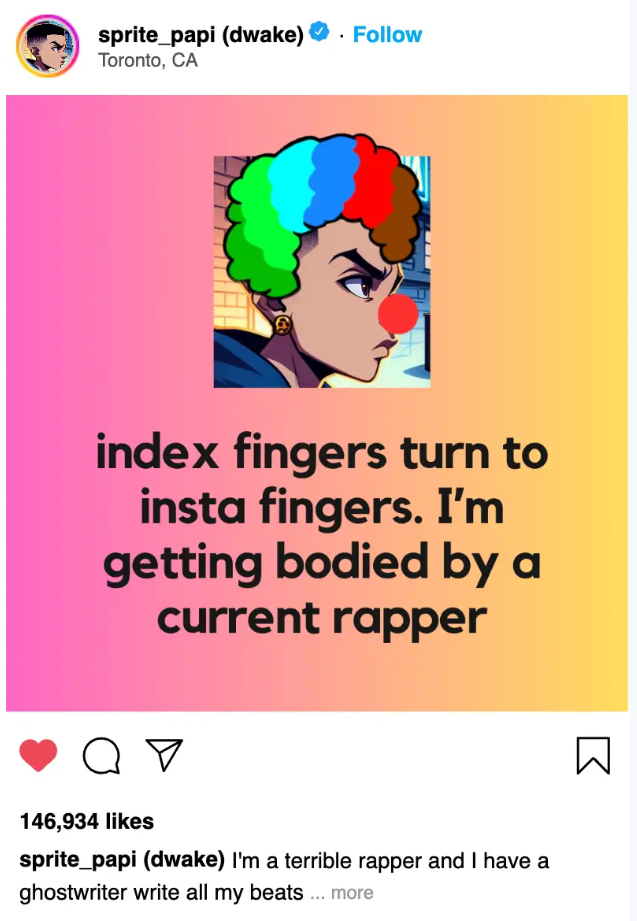
Yikes.
The higher-ups at OWL records deliberated the event in a private meeting. In that meeting was Dwake himself, who was seething about what had taken place. After 6 hours of deliberation, the company declared it a settled issue. However interestingly enough, they never officially specified how they dealt with the situation.

The following day, a random hacker on the dark web threatened to release damaging information on Present the rapper, if he did not announce his retirement in the next 30 days.
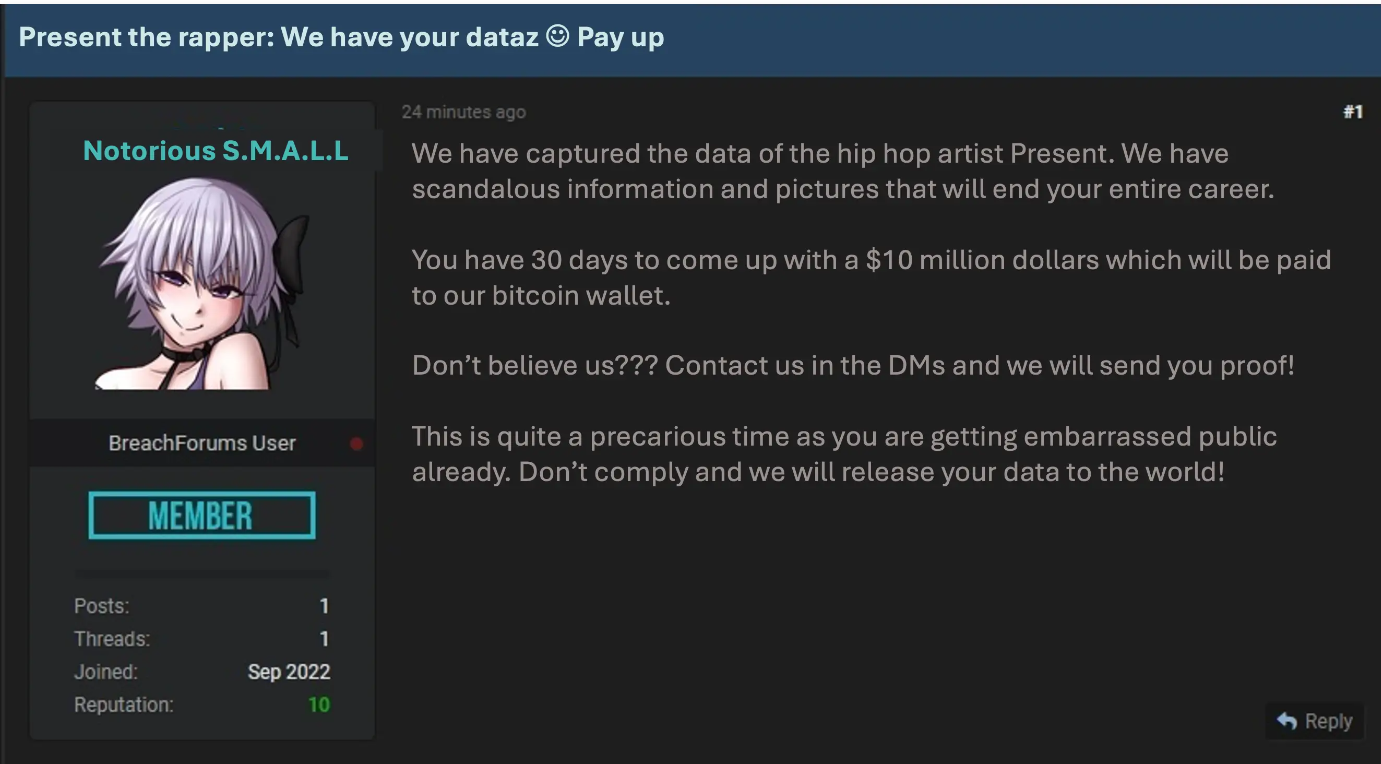
OWL Records is totally not involved. 😃
We can't really prove that OWL Records management had anything to do with the dark web post (and honestly, we don't have any reason to try). But we know this could cause us more headaches if it's not sorted out. So, we hit up our contact in the cyber underground again, and he hinted that any payback might come through phishing. It's a bit of a vague clue, but we're pros, so we can definitely figure something out.
Hunting for Phish
We already know one thing about the bad guys! They used IP 18.66.52[.]227 in their operations. If we can track down a domain name linked to this IP, it might lead us to those phishing emails.
We can look in the PassiveDNS table for ip <-> domain relationships to find the adversary’s domain.
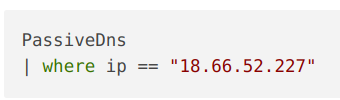
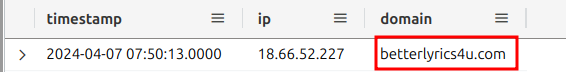
Woohoo! We've got a domain name! Things should be a lot easier now! Let's dive into the email logs to see if this domain was used. Before peering at the logs, we need to inspect the email table.
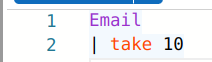
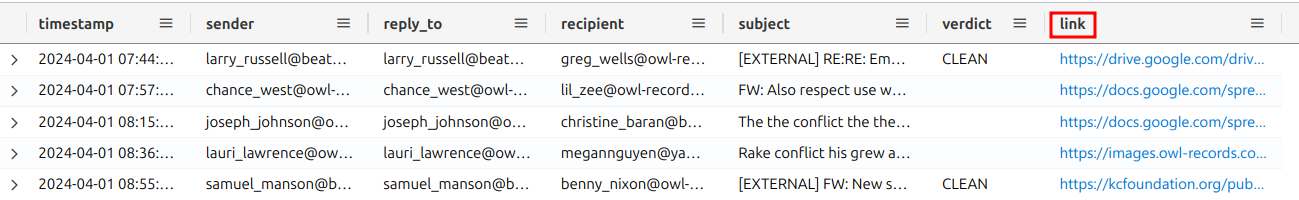
Let's check out the table layout and figure out which column probably has our domain. By using "take 10" to show just the top ten results, we can see that the link column has URLs. That's probably where we'll find our domain.
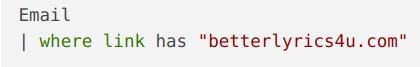
Now, we should look for the “betterlyrics4u[.]com” domain.
The query returns 13 results. Each row represents an email sent to someone at OWL records! We need to find the email address that sent most of the emails. Multiple emails sent from the same external domain to different company email addresses could be a sign of a targeted phishing campaign.
We can easily spot the outlier.
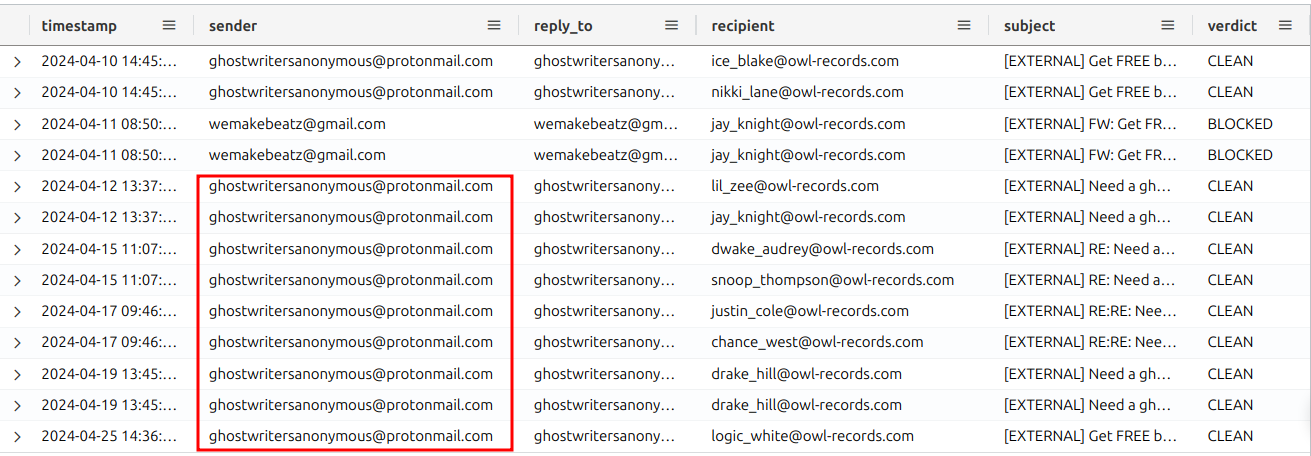
However, we also see a second email address of interest. Luckily emails from this one were blocked.
Okay, we managed to pivot from the domain to find the email addresses for the phishing campaign. To further support our position that this is indeed a targeted effort, we should find out which job role was targeted the most. We need to inspect the email table by assigning it to a variable, filter out unique recipients, and cross-reference the results with the email_addr column in the Employees table.
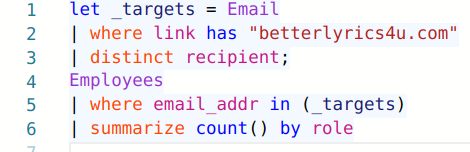
It seems our attacker only wanted to target the rappers.
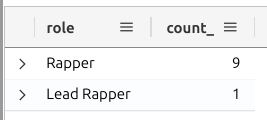
Interesting! There is only one result for the lead rapper. I wonder who it could be.
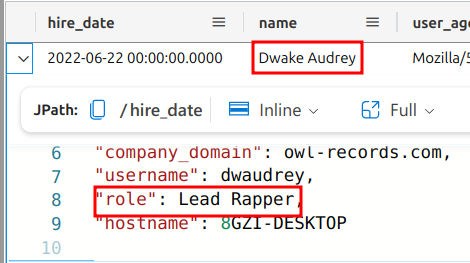
Oh. Yeah, that makes sense, I guess. Personally, I think Snoop is better, but that’s just me. 🤷🏾♂️
Before we pivot off this, we should note Dwake’s IP address. If the phishing attack was successful, this will help later if we need to check the authentication logs.
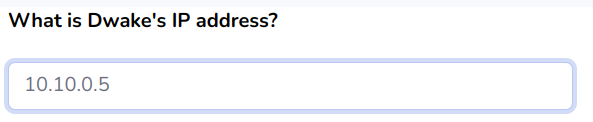
The next question we have to answer is: What is the subject of the email sent to Dwake? Since this is a spear-phishing attack, it has to be interesting enough for him to open.
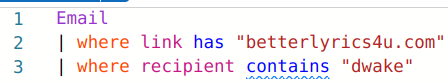
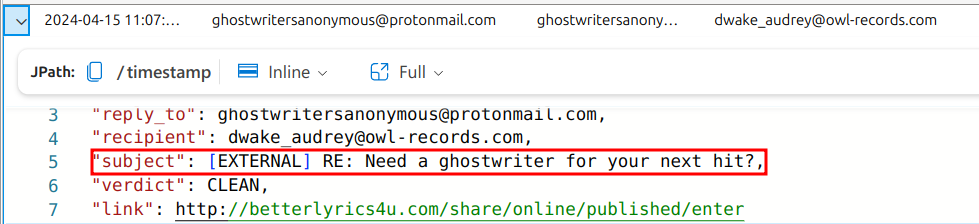
Besides noticing that Dwake probably doesn’t write his own bars, we get quite a bit of information from this result. For one, this email got through the spam filter and was dubbed “CLEAN.” We also see the link the attacker wants him to follow. Let’s inspect the actual contents of the email to get a better idea of what we’re working with.
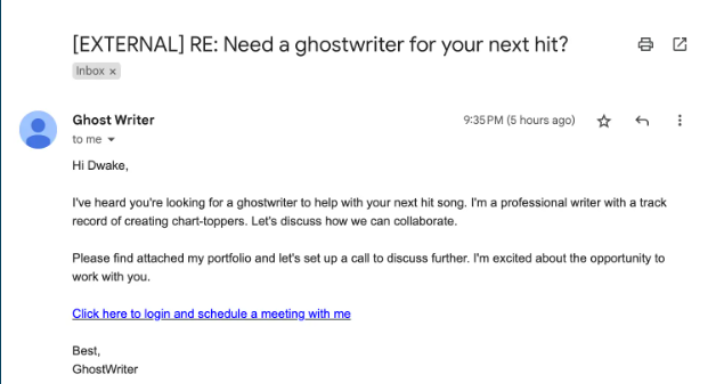
If Dwake clicked the link, we would see the data in the OutboundNetworkEvents table. By examining the data here, we can confirm there was a GET request for the malicious URL and the timeframe in which it happened.
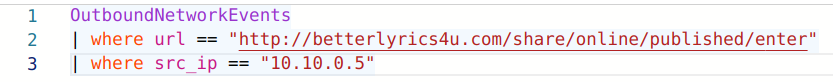
After Dwake clicked on the link in the email, he was presented with this phishing page:
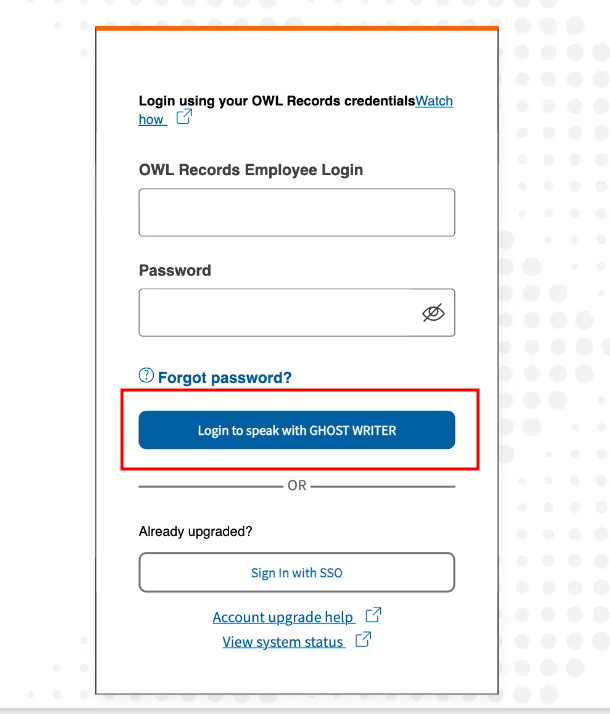
Most likely, he entered his username and password, and the credentials were sent to a remote server controlled by the attacker. Now that they have his credentials, the attackers would need to verify them by logging into Dwake's account. As I mentioned earlier, we can check the AuthenticationEvents table to see if the attackers were able to log in to Dwake's account. We'll need to use the attacker's IP address for this.
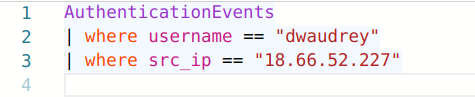
It seems the attacker was able to successfully login.
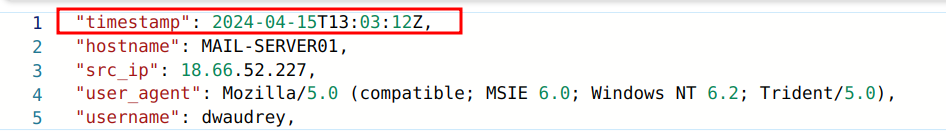
Now that the adversaries have logged into Dwake's account, they will want to look for important information to steal. Since we already know the adversary's IP address, we can check for InboundNetwork events during that timeframe and hunt for activity against Dwake's account.
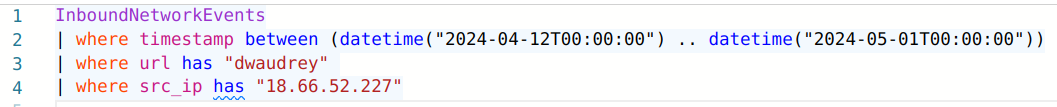
We get ten records with this query and some suspicious URL parameters.
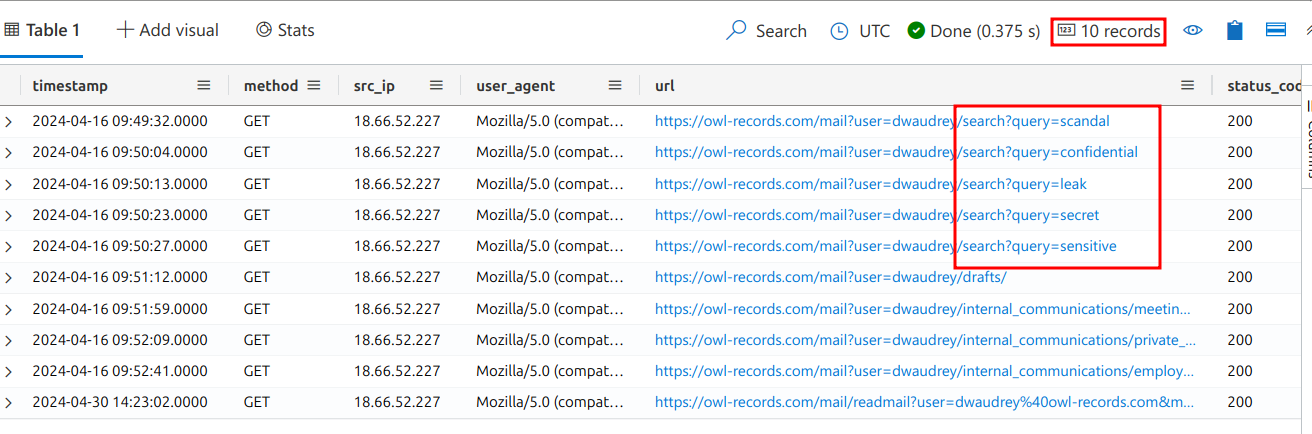
It looks like the attacker accomplished their goal. We see evidence of data exfiltration using a zip file.
Conclusion
Dwake and Present have a lot of dirt on each other now. After some back-and-forth through some middlemen, they decided to call a truce. Luckily, this didn’t escalate beyond cyberspace. Everything's chill in the Rap World for now!
This KC7 exercise demonstrated the entire cyber attack process—from reconnaissance and phishing to account compromise and data theft—in an entertaining way. It highlighted the importance of detailed data analysis, the effectiveness of KQL for threat hunting, and the value of communication in engaging both technical and non-technical audiences. It also showed the importance of training employees on operational security (OPSEC), especially in industries where reputation and persona are public-facing.
If personal info gets leaked or shared too much, it can be used in social engineering attacks. I'm definitely going to keep using KC7 as a hands-on learning tool. This exercise was a big reminder that cybersecurity needs to tackle both the technical and human sides to really work well.
Subscribe to my newsletter
Read articles from Dru Banks directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Dru Banks
Dru Banks
I am a cybersecurity professional with a deep passion for offensive security, threat intelligence, reverse engineering, and malware analysis. I believe that 'knowledge is power,' and that at every opportunity, knowledge should be shared. My blog serves that purpose and will be a public source for my studies, including write-ups on various topics.