Publishing a Secure Azure Storage Module to Terraform Private Registry: Step-by-Step Guide
 Rabiatu Mohammed
Rabiatu Mohammed
Creating reusable Terraform modules is a powerful way to manage infrastructure as code. In this guide, I'll walk through how to build a secure Azure storage account module, publish it to a private registry, and then use it in a Terraform configuration.
Prerequisites
A Terraform Cloud account with access to the private registry.
Basic understanding of Terraform and Azure infrastructure.
Azure account with necessary permissions.
Define the Variables for Your Module
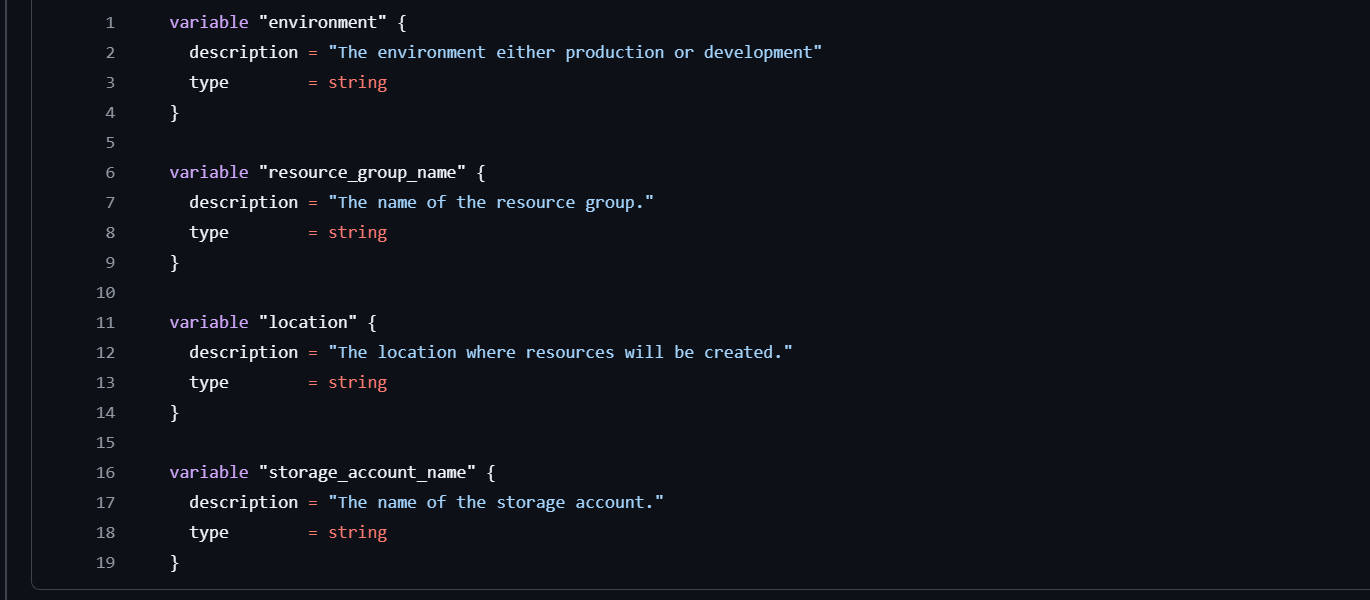
The first step is to create a variables.tf file that defines the parameters your module will accept. By creating variables, we ensure the module is flexible and can be adapted for different environments and configurations. Here’s a basic setup:
Configuring Your Core Infrastructure in Terraform
Let’s get into the heart of the Terraform setup. Our main configuration in main.tf defines the Azure provider, consistent tags, and our secure storage account.
Specifying the Azure Provider
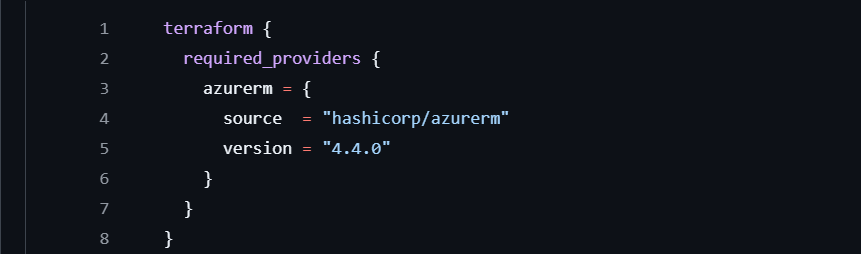
First, we need to tell Terraform which provider we’re using. In this case, it’s Azure (azurerm), and we’re specifying version 4.4.0 to keep things consistent.
Setting Up Consistent Tags
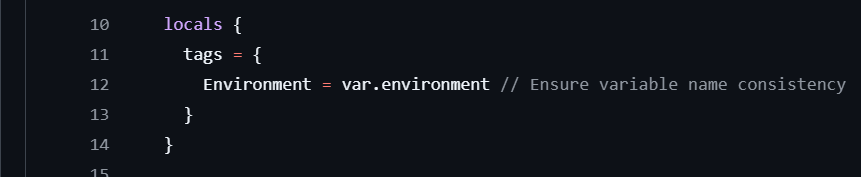
Using locals, we define a reusable set of tags, including Environment, which pulls from the environment variable. This keeps our resources consistently tagged without repetitive typing.
Defining the Storage Account
Here’s the main part: creating an Azure Storage Account. Key variables like resource_group_name, location, and name adapt to what we pass through, making this setup flexible. We also add a conditional for replication type: GRS for production, LRS for other environments.
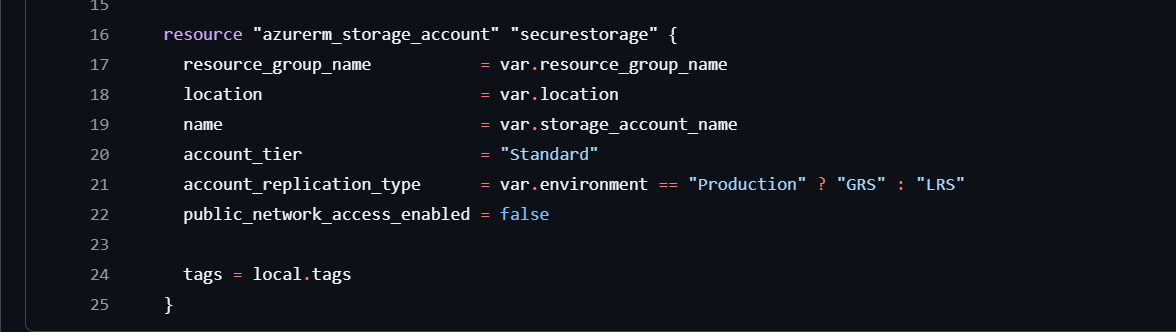
This setup is secure and adaptable. We’re setting public_network_access_enabled to false for extra security, limiting access to trusted networks only.
Defining Outputs
After setting up your resources, it’s a good practice to define outputs for values you might want to reference later. In this case, we're creating an output for the storage account ID. This output block will allow us to see the unique identifier of the storage account after Terraform provisions it.
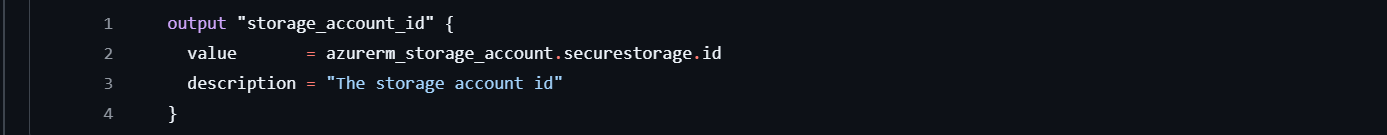
With this output, you can easily access the storage account's ID for use in other configurations or just to verify it’s created as expected.
Push the Module to GitHub
To publish the module, first push the code to a GitHub repository. Ensure the repository is structured correctly with a README file and clear documentation.
You can refer to the complete code on GitHub here.
Publish the Module to Terraform Private Registry
Navigate to Terraform Cloud and select your organization.
Go to Registry > Modules > Publish Module.
Select GitHub as the source, and locate the repository containing your module.
Complete the publishing process by setting up the module version and confirming the release.
Use the Published Module in Your Terraform Configuration
Once published, you can use this module in any Terraform configuration by referencing it in the main.tf file.
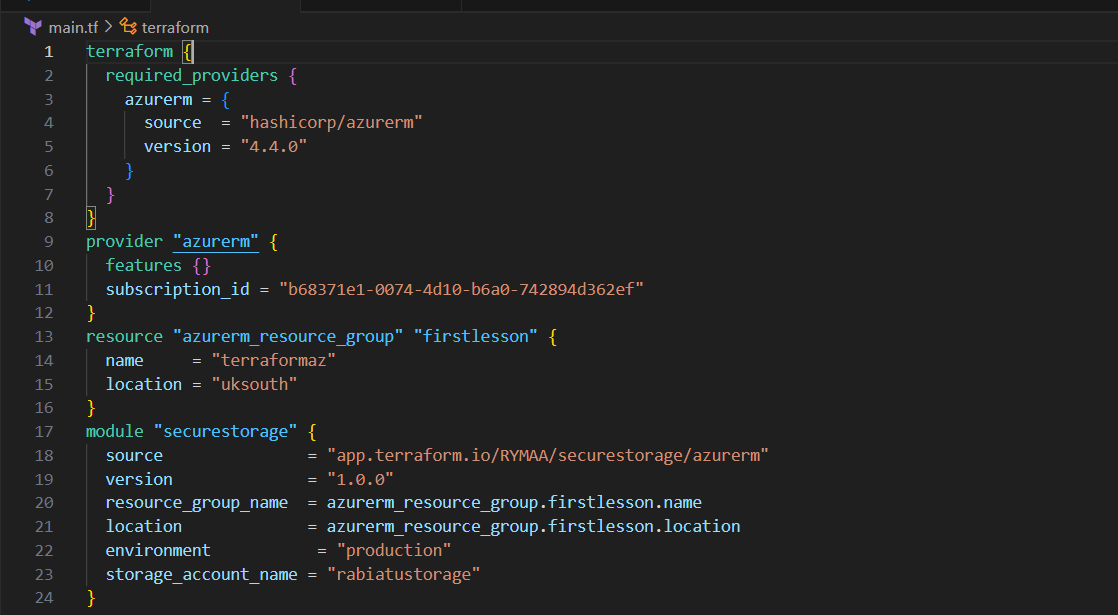
Run Terraform Commands
Initialize Terraform: Run
terraform initto initialize the working directory and install necessary providers and modules.Validate Configuration: Run
terraform validateto ensure your configuration is correct.Plan the Deployment: Use
terraform planto view what changes Terraform will make.Apply the Changes: Run
terraform applyto create the resources.
Verify in Azure
After the apply step completes, log in to your Azure portal and verify that the storage account has been created with the correct settings, replication type, and tags.
By following these steps, you've created a reusable, secure Azure storage module and published it to a private Terraform registry. This setup enables consistent, scalable infrastructure provisioning and allows teams to share and manage resources more efficiently. For the full code, visit GitHub.
Subscribe to my newsletter
Read articles from Rabiatu Mohammed directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rabiatu Mohammed
Rabiatu Mohammed
I work on securing, automating, and improving cloud environments. Always exploring better ways to build reliable, secure infrastructure.