Window and AD Fundamentals: Active Directory Basics (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Windows Fundamentals 3 that covers Windows Domains, Active Directory, Managing Users in AD, Managing Computers in AD, Group Policies, and Authentication Methods, together with Trees, Forests and Trusts.
In a Windows domain, credentials are stored in a centralized repository called...
Active DirectoryThe server in charge of running the Active Directory services is called...
Domain ControllerWhich group normally administrates all computers and resources in a domain?
Domain AdminsWhat would be the name of the machine account associated with a machine named TOM-PC?
TOM-PC$Suppose our company creates a new department for Quality Assurance. What type of containers should we use to group all Quality Assurance users so that policies can be applied consistently to them?
Organizational UnitsWhat was the flag found on Sophie's desktop?
THM{thanks_for_contacting_support}The process of granting privileges to a user over some OU or other AD Object is called...
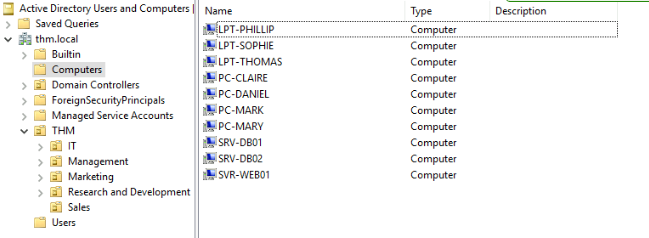
delegationAfter organising the available computers, how many ended up in the Workstations OU?
7
when we remove the SRV (which is 3) we remain with 7
Is it recommendable to create separate OUs for Servers and Workstations? (yay/nay)
yayWhat is the name of the network share used to distribute GPOs to domain machines?
sysvolCan a GPO be used to apply settings to users and computers? (yay/nay)
yayWill a current version of Windows use NetNTLM as the preferred authentication protocol by default? (yay/nay)
nayWhen referring to Kerberos, what type of ticket allows us to request further tickets known as TGS?
Ticket Granting TicketWhen using NetNTLM, is a user's password transmitted over the network at any point? (yay/nay)
nayWhat is a group of Windows domains that share the same namespace called?
TreeWhat should be configured between two domains for a user in Domain A to access a resource in Domain B?
A Trust Relationship
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.