The Client-Server Communication - SSL/TLS Handshake Process
 Sai Keerthan Kasula
Sai Keerthan Kasula
Prologue
In this article, we’ll explore the communication process between the client (browser) and server, focusing on how they exchange data and validate each other to ensure that only the intended parties are involved and that the data remains secure.
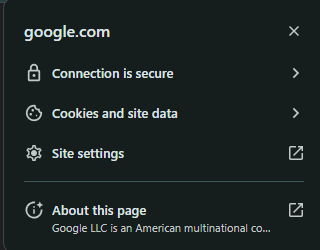
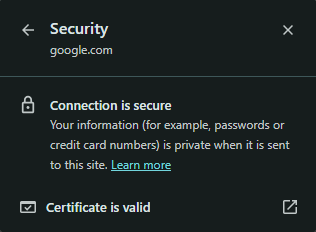
Have you ever noticed, right next to the address bar when you access a site like Google (https://www.google.com), there’s information indicating that the connection is secure?
Why is that? What makes this connection secure? This is because the client (browser) and the server (Google's website) undergo a process to validate each other, establishing a secure connection. Let’s take a brief look at how this process works.
Note: A brief understanding of basic cryptography is required to understand this article’s content. Consider reading my previous blogs about cryptography here →https://keerthankasula.hashnode.dev/
So, What is SSL/TLS (Secure Sockets Layer / Transport Layer Security) handshake? How it makes the client-server connection more secure?
To exchange any kind of confidential information over the internet, it’s essential to verify the identities of all parties involved in the communication. This ensures that only trusted entities can access the information.
In the scenario above, where we are accessing Google’s homepage, there are two critical questions:
The server providing the webpage needs to know that the browser attempting to access its content is legitimate.
Similarly, the browser needs to confirm that the server is authentic and truly who it claims to be.
This process of verifying each other and establishing a secure connection is known as the SSL/TLS handshake.
Let us explore about a brief introduction of SSL handshake below:
Client Hello: The browser (client) initiates communication by sending a “Hello” message to the server, including information about supported encryption algorithms and the client’s random number.
Server Hello: The server responds with its own “Hello” message, selecting an encryption algorithm from the client’s list, and sends its own random number along with its SSL/TLS certificate.
Certificate Verification and Pre-Master Key: The client verifies the server’s certificate (issued by a trusted Certificate Authority, or CA) and then creates a pre-master key. It encrypts this pre-master key with the server's public key (from the certificate) and sends it to the server.
Session Key Creation and Finalization: Both the client and server use the shared pre-master key to generate a session key, used to encrypt the communication that follows. Once verified, both parties send a “Finished” message encrypted with this session key, ensuring a secure channel.
Why This is Secure
Certificate Validation: SSL/TLS certificates are issued by trusted Certificate Authorities (CAs). These CAs authenticate the identity of the server, so the client knows it’s connecting to the correct server.
Encryption: The session key generated in the handshake encrypts all communication between the client and server, making it unreadable to anyone else.
Integrity Checks: SSL/TLS protocols ensure data integrity through hash functions, which detect any tampering with data in transit.
Because SSL/TLS protocols handle encryption, authentication, and integrity checks, this process is considered secure for protecting data between you and Google.
Happy Reading !
Consider following my tech blog for more such content.
Sai Keerthan Kasula, Junior Software Developer.
Subscribe to my newsletter
Read articles from Sai Keerthan Kasula directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sai Keerthan Kasula
Sai Keerthan Kasula
Embracing this journey, eager to confront new challenges daily and strive towards becoming the best version of myself.