Public Key Cryptography Basics
 Jebitok
Jebitok
In this article, I will write a write-up for Public Key Cryptography Basics that covers the Common Use of Asymmetric Encryption, RSA, Diffie-Hellman Key Exchange, SSH, Digital Signatures and Certificates, as well as PGP and GPG to understand how public key ciphers like RSA work and explore their role in applications such as SSH.
In the analogy presented, what real object is analogous to the public key?
LockKnowing that p = 4391 and q = 6659. What is n?
29239669Knowing that p = 4391 and q = 6659. What is ϕ(n)?
29228620Consider p = 29, g = 5, a = 12. What is A?
7Consider p = 29, g = 5, b = 17. What is B?
9Knowing that p = 29, a = 12, and you have B from the second question, what is the key calculated by Bob? (key = Ba mod p)
24Knowing that p = 29, b = 17, and you have A from the first question, what is the key calculated by Alice? (key = Ab mod p)
24Check the SSH Private Key in
~/Public-Crypto-Basics/Task-5. What algorithm does the key use?RSA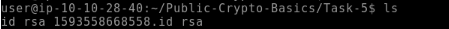
What does a remote web server use to prove itself to the client?
CertificateWhat would you use to get a free TLS certificate for your website?
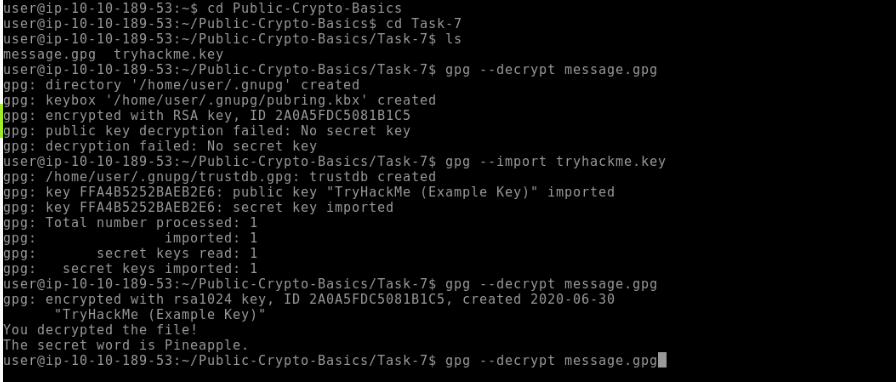
Let's EncryptUse GPG to decrypt the message in
~/Public-Crypto-Basics/Task-7. What secret word does the message hold?Pineapple
You will have to import your key from tryhackme.key then you’ll decrypt your message on message.gpg
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.