Cryptography: Hashing Basics (TryHackMe)
 J3bitok
J3bitok
In this article, I will write a write-up for Hashing Basics that covers Hash Functions, Insecure Password Storage for Authentication, Using Hashing for Secure Password Storage, Recognising Password Hashes, Password Cracking, and Hashing for Integrity Checking.
What is the SHA256 hash of the
passport.jpgfile in~/Hashing-Basics/Task-2?77148c6f605a8df855f2b764bcc3be749d7db814f5f79134d2aa539a64b61f02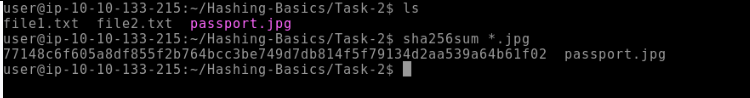
What is the output size in bytes of the MD5 hash function?
16If you have an 8-bit hash output, how many possible hash values are there?
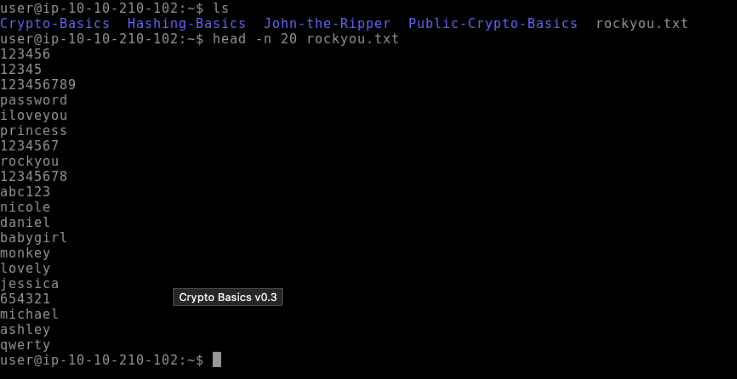
256What is the 20th password in
rockyou.txt?qwerty
there’s a hint to this command head -n 20 rockyou.txt since using without the number only shows the first 10 passwords
Manually check the hash “4c5923b6a6fac7b7355f53bfe2b8f8c1” using the rainbow table above.
inS3CyourP4$$Crack the hash “5b31f93c09ad1d065c0491b764d04933” using an online tool.
tryhackmeShould you encrypt passwords in password-verification systems? Yea/Nay
NayWhat is the hash size in yescrypt?
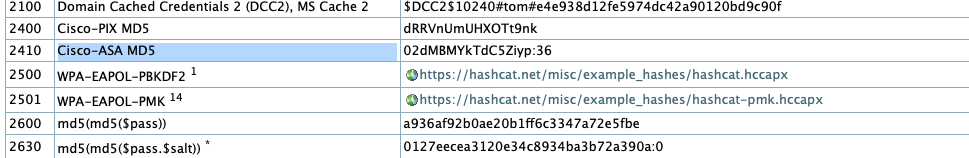
256What’s the Hash-Mode listed for Cisco-ASA MD5?
2410What hashing algorithm is used in Cisco-IOS if it starts with
$9$?scryptUse
hashcatto crack the hash,$2a$06$7yoU3Ng8dHTXphAg913cyO6Bjs3K5lBnwq5FJyA6d01pMSrddr1ZG, saved in~/Hashing-Basics/Task-6/hash1.txt.85208520Use
hashcatto crack the SHA2-256 hash,9eb7ee7f551d2f0ac684981bd1f1e2fa4a37590199636753efe614d4db30e8e1, saved in saved in~/Hashing-Basics/Task-6/hash2.txt.halloweenUse
hashcatto crack the hash,$6$GQXVvW4EuM$ehD6jWiMsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjycw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0, saved in~/Hashing-Basics/Task-6/hash3.txt.spacemanCrack the hash,
b6b0d451bbf6fed658659a9e7e5598fe, saved in~/Hashing-Basics/Task-6/hash4.txt.funforyouWhat is SHA256 hash of
libgcrypt-1.11.0.tar.bz2found in~/Hashing-Basics/Task-7?09120c9867ce7f2081d6aaa1775386b98c2f2f246135761aae47d81f58685b9c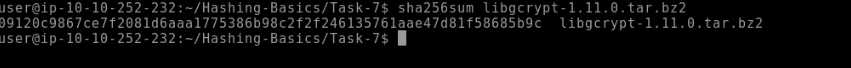
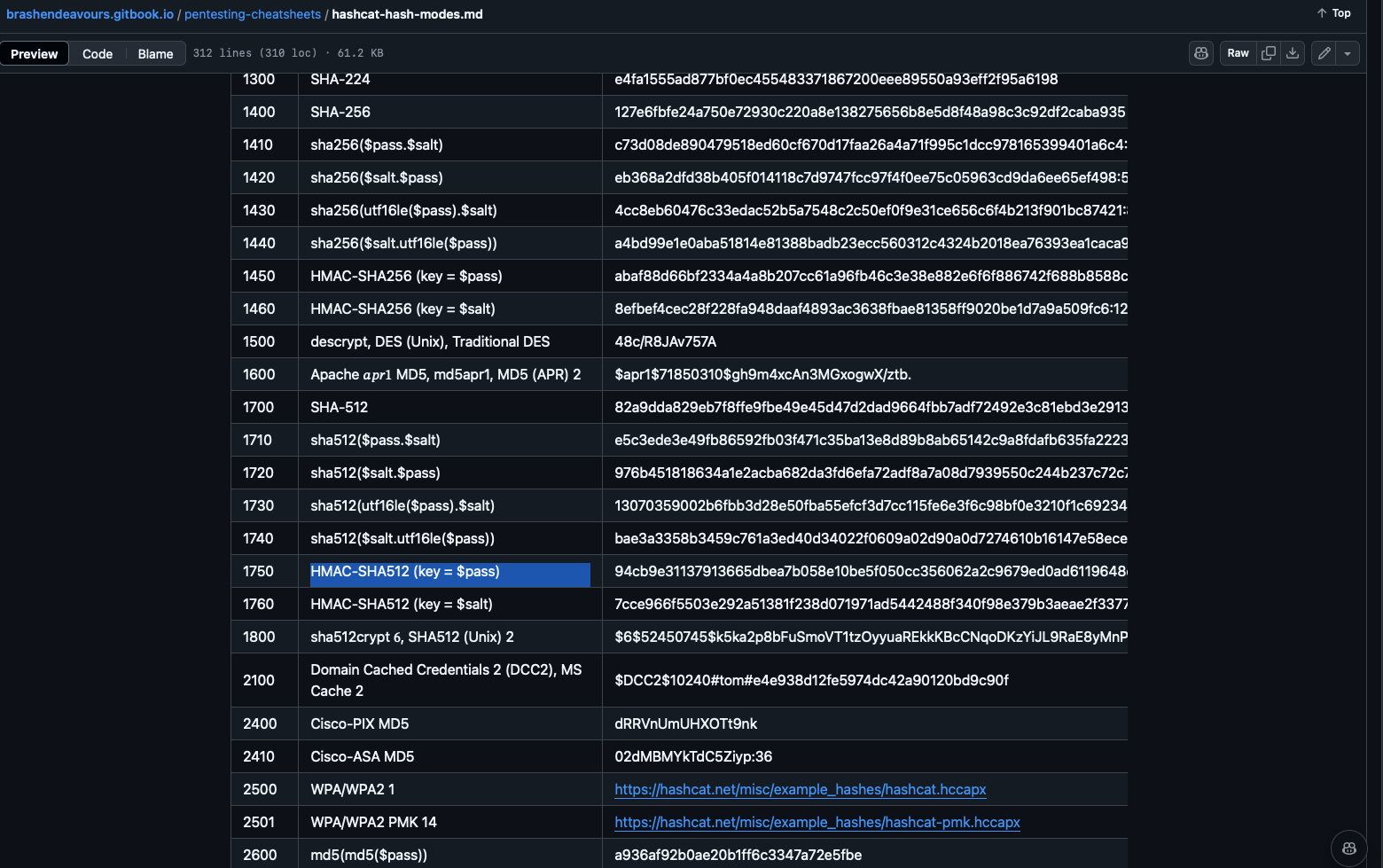
What’s the hashcat mode number for
HMAC-SHA512 (key = $pass)?1750you can check the Hashcat website and GitHub that shows the hash-modes and examples
Use
base64to decodeRU5jb2RlREVjb2RlCg==, saved asdecode-this.txtin~/Hashing-Basics/Task-8. What is the original word?
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges. We can also connect more on LinkedIn or X.
Subscribe to my newsletter
Read articles from J3bitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

J3bitok
J3bitok
Software Developer Learning Cloud and Cybersecurity Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship you can book a session with me on Mentorlst.com.